Local Area Networks are often deployed in a way that allows unauthorized clients to attach to network devices, or allows unauthorized users to get access to unattended clients on a network. Also, the use of DHCP services and zero configuration make access to networking services easily available. This exposes the network to unauthorized use and malicious attacks. While access to the network should be made easy, uncontrolled and unauthorized access is usually not desirable. 802.1X simplifies security management by providing access control along with the ability to control user profiles from up to three RADIUS servers while allowing a given user to use the same entering valid user credentials for access from multiple points within the network.
The switch offers two methods for using 802.1X access control. Generally, the “Port Based” method supports one 802.1X-authenticated client on a port, which opens the port to an unlimited number of clients. The “User-Based” method supports up to 32 802.1X-authenticated clients on a port. In both cases, there are operating details to be aware of that can influence your choice of methods.
802.1X operation with access control on a per-user basis provides client-level security that allows LAN access to individual 802.1X clients (up to 32 per port), where each client gains access to the LAN by entering valid user credentials. This operation improves security by opening a given port only to individually authenticated clients, while simultaneously blocking access to the same port for clients that cannot be authenticated. All sessions must use the same untagged VLAN (unless MAC-based VLANs are enabled. Please see MAC-based VLANs). Also, an authenticated client can use any tagged VLAN memberships statically configured on the port, provided the client is configured to use the tagged VLAN memberships available on the port. (Note that the session total includes any sessions begun by the Web Authentication or MAC Authentication.) See Option for authenticator ports: configure port-security to allow only 802.1X-authenticated devices.
802.1X port-based access control provides port-level security that allows LAN access only on ports where a single 802.1X-capable client (supplicant) has entered authorized RADIUS user credentials. For reasons outlined below, this option is recommended for applications where only one client at a time can connect to the port. Using this option, the port processes all IP traffic as if it comes from the same client. Thus, in a topology where multiple clients can connect to the same port at the same time:
-
If the first client authenticates and opens the port, and then another client authenticates, the port responds as if the original client has initiated a reauthentication. With multiple clients authenticating on the port, the RADIUS configuration response to the latest client authentication replaces any other configuration from an earlier client authentication. If all clients use the same configuration this should not be a problem. But if the RADIUS server responds with different configurations for different clients, then the last client authenticated will effectively lock out any previously authenticated client. When any client to authenticate closes its session, the port will also close and remain so until another client successfully authenticates.
-
The most recent client authentication determines the untagged VLAN membership for the port. Also, any client able to use the port can access any tagged VLAN memberships statically configured on the port, provided the client is configured to use the available, tagged VLAN memberships.
-
If the first client authenticates and opens the port, and then one or more other clients connect without trying to authenticate, then the port configuration as determined by the original RADIUS response remains unchanged and all such clients will have the same access as the authenticated client. When the authenticated client closes the session, the port will also be closed to any other, unauthenticated clients that may have also been using the port.
This operation unblocks the port while an authenticated client session is in progress. In topologies where simultaneous, multiple client access is possible this can allow unauthorized and unauthenticated access by another client while an authenticated client is using the port. If you want to allow only authenticated clients on the port, then user-based access control should be used instead of port-based access control. Using the user-based method enables you to specify up to 32 authenticated clients.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Port-Based 802.1X can operate concurrently with Web-Authentication or MAC-Authentication on the same port. However, this is not a commonly used application and is not generally recommended. For more information, see Operating Notes. |
|
|
Note that you can also configure 802.1X for authentication through the switch’s local user name and password instead of a RADIUS server, but doing so increases the administrative burden, decentralizes user credential administration, and reduces security by limiting authentication to one Operator password set for all users.
The switches covered in this guide also provide RADIUS Network accounting for 802.1X access. See Radius-administered CoS and rate-limiting.
-
Configure a local user name and password on the switch for both the Operator (login) and Manager (enable) access levels. (While this may or may not be required for your 802.1X configuration, Hewlett Packard Enterprise recommends that you use a local user name and password pair at least until your other security measures are in place.)
-
Enable include-credentials. The port-access option is available only if include-credentials is enabled. See Security settings that can be saved.
For switches covered in this guide, the local operator password configured with the password command is not accepted as an 802.1X authenticator credential. The port-access command is used to configure the operator user name and password that are used as 802.1X credentials for network access to the switch. 802.1X network access is not allowed unless a password has been configured using the password port-access command.
Syntax
Configures the operator user name and password used to access the network through 802.1X authentication.
You can save the port-access password for 802.1X authentication in the configuration file by using the include-credentials command. For more information, see Saving user name and password security.
-
Determine the switch ports that you want to configure as authenticators and supplicants, and disable LACP on these ports. (For more information on disabling LACP, see “Note”).
To display the current configuration of 802.1X, Web-based, and MAC authentication on all switch ports, enter the
show port-access configcommand as shown in the following example:# show port-access config Port Access Status Summary Port-access authenticator activated [No] : No Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No Port 802.1X 802.1X Web Mac LMA Ctrl Mixed Speed Port Supp Auth Auth Auth Auth Dir Mode VSA MBV --- ------ ------ ---- ---- ---- ----- ----- ----- -------- C1 No Yes No No No In No Yes Yes C2 No Yes No No No Both Yes Yes Yes C3 No Yes No No No Both No No Yes C4 No Yes No No Yes Both No Yes Yes -
Determine whether to use user-based access control, see 802.1X User-based access control or portbased access control, see 802.1X Port-based access control.
-
Determine whether to use the optional 802.1X Open VLAN mode for clients that are not 802.1X-aware; that is, for clients that are not running 802.1X supplicant software. (This will require you to provide downloadable software that the client can use to enable an authentication session.) See 802.1X Open VLAN mode.
-
For any port you want to operate as a supplicant, determine the user credentials. You can either use the same credentials for each port or use unique credentials for individual ports or subgroups of ports. (This can also be the same local user name/password pair that you assign to the switch.)
-
Unless you are using only the switch’s local user name and password for 802.1X authentication, configure at least one RADIUS server to authenticate access requests coming through the ports on the switch from external supplicants (including switch ports operating as 802.1X supplicants). You can use up to three RADIUS servers for authentication; one primary and two backups. See the documentation provided with your RADIUS application.
This section outlines the steps for configuring 802.1X on the switch. For detailed information on each step, see the following:
-
Enable 802.1X user-based or port-based authentication on the individual ports you want to serve as authenticators. On the ports you will use as authenticators, either accept the default 802.1X settings or change them, as necessary. Note that, by default, the port-control parameter is set to auto for all ports on the switch. This requires a client to support 802.1X authentication and to provide valid credentials to get network access. See Enabling 802.1X authentication on selected ports.
-
If you want to provide a path for clients without 802.1X supplicant software to download the software so that they can initiate an authentication session, enable the 802.1X Open VLAN mode on the ports you want to support this feature. See 802.1X Open VLAN mode.
-
Configure the 802.1X authentication type. Options include:
-
Local Operator user name and password (using the password port-access command).
-
EAP RADIUS: This option requires your RADIUS server application to support EAP authentication for 802.1X
-
CHAP (MD5) RADIUS: This option requires your RADIUS server application to support CHAP (MD5) authentication. See Configure the 802.1X Authentication Method.
-
-
If you select either
eap-radiusorchap-radiusfor step 3, use theradius hostcommand to configure up to three RADIUS server IP addresses on the switch. See Enter the RADIUS Host IP Addresses. -
Enable 802.1X authentication on the switch. See Enabling 802.1X authentication on selected ports.
-
Test both the authorized and unauthorized access to your system to ensure that the 802.1X authentication works properly on the ports you have configured for port-access.
![[NOTE: ]](images/note.gif)
NOTE: If you want to implement the optional port security feature (step 7) on the switch, you should first ensure that the ports you have configured as 802.1X authenticators operate as expected.
-
If you are using Port Security on the switch, configure the switch to allow only 802.1X access on ports configured for 802.1X operation, and (if desired) the action to take if an unauthorized device attempts access through an 802.1X port. See Port-Security.
-
If you want a port on the switch to operate as a supplicant on a port operating as an 802.1X authenticator on another device, then configure the supplicant operation. (See Configuring Switch Ports To Operate As Supplicants for 802.1X Connections to Other Switches.
This task configures the individual ports you want to operate as 802.1X authenticators for point-to-point links to 802.1X-aware clients or switches, and consists of two steps:
(Actual 802.1X operation does not commence until you perform step 5 to activate 802.1X authentication on the switch.)
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If you enable 802.1X authentication on a port, the switch automatically disables LACP on that port. However, if the port is already operating in an LACP trunk, you must remove the port from the trunk before you can configure it for 802.1X authentication. |
|
|
-
Enable the Selected Ports as Authenticators and Enable the (Default) Port-Based Authentication
Syntax
Enables specified ports to operate as 802.1X authenticators and enables port-based authentication. (To enable userbased authentication, execute this command first, and then execute the client-limit <port-list> version of this command described in the next section.) The no form of the command removes 802.1X authentication from <port-list>. To activate configured 802.1X operation, you must enable 802.1X authentication. See Enable 802.1X Authentication on the Switch.
Syntax
Used after executing aaa port-access authenticator <port-list> (above) to convert authentication from port-based to userbased. Specifies user-based 802.1X authentication and the maximum number of 802.1X-authenticated client sessions allowed on each of the ports in <port-list>. If a port currently has no authenticated client sessions, the next authenticated client session the port accepts determines the untagged VLAN membership to which the port is assigned during the session. If another client session begins later on the same port while an earlier session is active, the later session will be on the same untagged VLAN membership as the earlier session.
NOTE: The client limit is 256 clients per-port for MAC-auth and Web-auth; the client limit for 802.1X is 32 clients per port. The MAC-auth and Web-auth limit of 256 clients only applies when there are fewer than 16,384 authentication clients on the entire switch. After the limit of 16, 384 clients is reached, no additional authentication clients are allowed on any port for any method.
Syntax
Used to convert a port from user-based authentication to port-based authentication, which is the default setting for ports on which authentication is enabled. (Executing aaa port-access authenticator <port-list> enables 802.1X authentication on <port-list> and enables port-based authentication.) If a port currently has no authenticated client sessions, the next authenticated client session the port accepts determines the untagged VLAN membership to which the port is assigned during the session. If another authenticated client session begins later on the same port while an earlier session is active, the later session replaces the currently active session and will be on the untagged VLAN membership specified by the RADIUS server for the later session.
The commands in this section are initially set by default and can be reconfigured as needed.
Syntax
Controls authentication mode on the specified port:
authorized: Also termed “Force Authorized”. Gives access to a device connected to the port. In this case, the device does not have to provide 802.1X credentials or support 802.1X authentication. (You can still configure console, Telnet, or SSH security on the port.) auto (the default): The device connected to the port must support 802.1X authentication and provide valid credentials to get network access. (Optional: You can use the Open VLAN mode to provide a path for clients without 802.1X supplicant software to down-load this software and begin the authentication process. See 802.1X Open VLAN mode.) unauthorized: Also termed “Force Unauthorized”. Do not grant access to the network, regardless of whether the device provides the correct credentials and has 802.1X support. In this state, the port blocks access to any connected device.
Sets the period during which the port does not try to acquire a supplicant. The period begins after the last attempt authorized by the max-requests parameter fails). (Default: 60 seconds)
Sets the period the port waits to retransmit the next EAPOL PDU during an authentication session. (Default: 30 seconds)
Sets the period of time the switch waits for a supplicant response to an EAP request. If the supplicant does not respond within the configured time frame, the session times out. (Default: 30 seconds)
Sets the period of time the switch waits for a server response to an authentication request. If there is no response within the configured time frame, the switch assumes that the authentication attempt has timed out. Depending on the current max-requests setting, the switch will either send a new request to the server or end the authentication session. (Default: 30 seconds)
Sets the number of authentication attempts that must time-out before authentication fails and the authentication session ends. If you are using the Local authentication option, or are using RADIUS authentication with only one host server, the switch will not start another session until a client tries a new access attempt. If you are using RADIUS authentication with two or three host servers, the switch will open a session with each server, in turn, until authentication occurs or there are no more servers to try. During the quiet period, if any, you cannot reconfigure this parameter. (Default: 2)
Sets the period of time after which clients connected must be re-authenticated. When the timeout is set to 0 the reauthentication is disabled (Default: 0 second)
Configures an existing static VLAN to be the Unauthorized- Client VLAN. This enables you to provide a path for clients without supplicant software to download the software and begin an authentication session. See 802.1X Open VLAN mode.
Syntax
aaa port-access authenticator <port-list>
Configures the period of time the switch waits for client activity before removing an inactive client from the port. (Default: 300 seconds)
Specifies a delay in seconds for placing a port on the Unauthorized-Client VLAN. This delay allows more time for a client with 802.1X supplicant capability to initiate an authentication session. If a connected client does not initiate a session before the timer expires, the port is assigned to the Unauthenticated-Client VLAN. (Default: 0 seconds)
Configures an existing, static VLAN to be the Authorized- Client VLAN. See 802.1X Open VLAN mode.
This task specifies how the switch authenticates the credentials provided by a supplicant connected to a switch port configured as an 802.1X authenticator
You can configure local, chap-radius or eap-radius as the primary password authentication method for the port-access method. You also need to select none or authorized as a secondary, or backup, method.
Configures local, chap-radius (MD5), or eap-radius as the primary password authentication method for port-access. The default primary authentication is local. (Refer to the documentation for your RADIUS server application.)
For switches covered in this guide, you must use the password port-access command to configure the operator user name and password for 802.1X access. See General Setup Procedure for 802.1X Access Control.
Provides options for secondary authentication. The none option specifies that a backup authentication method is not used. The authorized option allows access without authentication. (default: none).
If you select either eap-radius or chap-radius for the authentication method, configure the switch to use 1, 2, or 3 RADIUS servers for authentication. The following syntax shows the basic commands. For coverage of all commands related to RADIUS server configuration, see RADIUS Authentication, Authorization, and Accounting.
Syntax
Adds a server to the RADIUS configuration. For switches that have a separate out-of-band management port, the oobm parameter specifies that the RADIUS traffic will go through the out-of-band management (OOBM) port.
Optional. Specifies an encryption key for use during authentication (or accounting) sessions with the specified server. This key must match the key used on the RADIUS server. Use this option only if the specified server requires a different key than configured for the global encryption key. The tilde (~) character is allowed in the string. It is not backward compatible; the “~” character is lost if you use a software version that does not support the “~” character.
Syntax
Specifies the global encryption key the switch uses for sessions with servers for which the switch does not have a server-specific key. This key is optional if all RADIUS server addresses configured in the switch include a server- specific encryption key. The tilde (~) character is allowed in the string, for example, radius-server key hp~switch. It is not backward compatible; the “~” character is lost if you use a software version that does not support the “~” character. Default: Null
The no form of the command removes the global encryption key.
After configuring 802.1X authentication as described in the preceding four sections, activate it with this command:
Syntax
While 802.1X authentication is operating, you can use the following aaa portaccess authenticator commands to reset 802.1X authentication and statistics on specified ports.
Syntax
On the specified ports, blocks inbound and outbound traffic and restarts the 802.1X authentication process. This happens only on ports configured with control auto and actively operating as 802.1X authenticators.
On the specified ports, forces reauthentication (unless the authenticator is in “HELD” state).
On the specified ports, clears authenticator statistics counters.
After you enable 802.1X authentication on specified ports, you can use the aaa port-access controlled-direction command to configure how a port transmits traffic before it successfully authenticates a client and enters the authenticated state.
As documented in the IEEE 802.1X standard, an 802.1X-aware port that is unauthenticated can control traffic in either of the following ways:
Prerequisite
As documented in the IEEE 802.1X standard, the disabling of incoming traffic and transmission of outgoing traffic on an 802.1X-aware egress port in an unauthenticated state (using the aaa port-access controlleddirection in command) is supported only if:
For information on how to configure the prerequisites for using the aaa portaccess controlled-direction in command, see “Multiple Instance Spanning-Tree Operation” in the Advanced Traffic Management Guide.
The Wake-on-LAN feature is used by network administrators to remotely power on a sleeping workstation (for example, during early morning hours to perform routine maintenance operations, such as patch management and software updates).
The aaa port-access controlled-direction incommand allows Wake-on-LAN traffic to be transmitted on an 802.1X-aware egress port that has not yet transitioned to the 802.1X authenticated state; the controlled-direction both setting prevents Wake-on-LAN traffic to be transmitted on an 802.1X-aware egress port until authentication occurs.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Although the controlled-direction in setting allows Wake-on-LAN traffic to traverse the switch through unauthenticated 802.1X-aware egress ports, it does not guarantee that the Wake-on-LAN packets will arrive at their destination. For example, firewall rules on other network devices and VLAN rules may prevent these packets from traversing the network. |
|
|
Preparation
This section assumes use of both the Unauthorized-Client and Authorized-Client VLANs.
Before you configure the 802.1X Open VLAN mode on a port:
-
Statically configure an “Unauthorized-Client VLAN” in the switch. The only ports that should belong to this VLAN are ports offering services and access you want available to unauthenticated clients. (802.1X authenticator ports do not have to be members of this VLAN.)
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Do not allow any port memberships or network services on this VLAN that would pose a security risk if exposed to an unauthorized client. |
|
|
-
Statically configure an Authorized-Client VLAN in the switch. The only ports that should belong to this VLAN are ports offering services and access you want available to authenticated clients. 802.1X authenticator ports do not have to be members of this VLAN.
Note that if an 802.1X authenticator port is an untagged member of another VLAN, the port’s access to that other VLAN will be temporarily removed while an authenticated client is connected to the port.
For example, if:
-
Port A5 is an untagged member of VLAN 1 (the default VLAN).
-
You configure port A5 as an 802.1X authenticator port.
-
You configure port A5 to use an Authorized-Client VLAN.
Then, if a client connects to port A5 and is authenticated, port A5 becomes an untagged member of the Authorized-Client VLAN and is temporarily suspended from membership in the default VLAN
-
-
If you expect friendly clients to connect without having 802.1X supplicant software running, provide a server on the Unauthorized-Client VLAN for downloading 802.1X supplicant software to the client, and a procedure by which the client initiates the download.
-
A client must either have a valid IP address configured before connecting to the switch, or download one through the Unauthorized-Client VLAN from a DHCP server. In the latter case, you will need to provide DHCP services on the Unauthorized-Client VLAN.
-
Ensure that the switch is connected to a RADIUS server configured to support authentication requests from clients using ports configured as 802.1X authenticators. (The RADIUS server should not be on the Unauthorized- Client VLAN.)
![[NOTE: ]](images/note.gif)
NOTE: As an alternative, you can configure the switch to use local password authentication instead of RADIUS authentication. However, this is less desirable because it means that all clients use the same passwords and have the same access privileges. Also, you must use 802.1X supplicant software that supports the use of local switch passwords.
![[CAUTION: ]](images/caution.gif)
CAUTION: Ensure that you do not introduce a security risk by allowing Unauthorized- Client VLAN access to network services or resources that could be compromised by an unauthorized client.
These steps enable 802.1X authentication, and must be done before configuring 802.1X VLAN operation.
-
Enable 802.1X authentication on the individual ports you want to serve as authenticators. (The switch automatically disables LACP on the ports on which you enable 802.1X.) On the ports you will use as authenticators with VLAN operation, ensure that the port-control parameter is set to auto (the default). (See Enabling 802.1X authentication on selected ports.) This setting requires a client to support 802.1X authentication (with 802.1X supplicant operation) and to provide valid credentials to get network access.
Syntax
-
Configure the 802.1X authentication type. Options include
Syntax
-
If you selected either eap-radius or chap-radius for step 2, use the radius host command to configure up to three RADIUS server IP addresses on the switch.
Syntax
Adds a server to the RADIUS configuration. For switches that have a separate out-of-band management port, the oobm parameter specifies that the RADIUS traffic will go through the out-of-band management (OOBM) port.
Optional. Specifies an encryption key for use with the specified server. This key must match the key used on the RADIUS server. Use this option only if the specified server requires a different key than configured for the global encryption key The tilde (~) character is allowed in the string. It is not backward compatible; the “~” character is lost if you use a software version that does not support the “~” character.
Syntax
Specifies the global encryption key the switch uses for sessions with servers for which the switch does not have a server-specific key. This key is optional if all RADIUS server addresses configured in the switch include a server- specific encryption key. The tilde (~) character is allowed in the string, for example, radiusserver key hp~switch. It is not backward compatible; the “~” character is lost if you use a software version that does not support the “~” character.
The no form of the command removes the global encryption key.
-
Activate authentication on the switch.
Syntax
-
Test both the authorized and unauthorized access to your system to ensure that the 802.1X authentication works properly on the ports you have configured for port-access.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If you want to implement the optional port-security feature on the switch, you should first ensure that the ports you have configured as 802.1X authenticators operate as expected. Then see Option For Authenticator Ports: Configure Port-Security To Allow Only 802.1X-Authenticated Devices. |
|
|
After you complete steps 1 and 2, the configured ports are enabled for 802.1X authentication (without VLAN operation), and you are ready to configure VLAN Operation.
Use these commands to actually configure Open VLAN mode. For a listing of the steps needed to prepare the switch for using Open VLAN mode, see Setting Up and Configuring 802.1X Open VLAN Mode.
Syntax
Configures an existing, static VLAN to be the Authorized- Client VLAN.
Configures an existing, static VLAN to be the Unauthorized- Client VLAN.
For example, suppose you want to configure 802.1X port-access with Open VLAN mode on ports A10 - A20 and
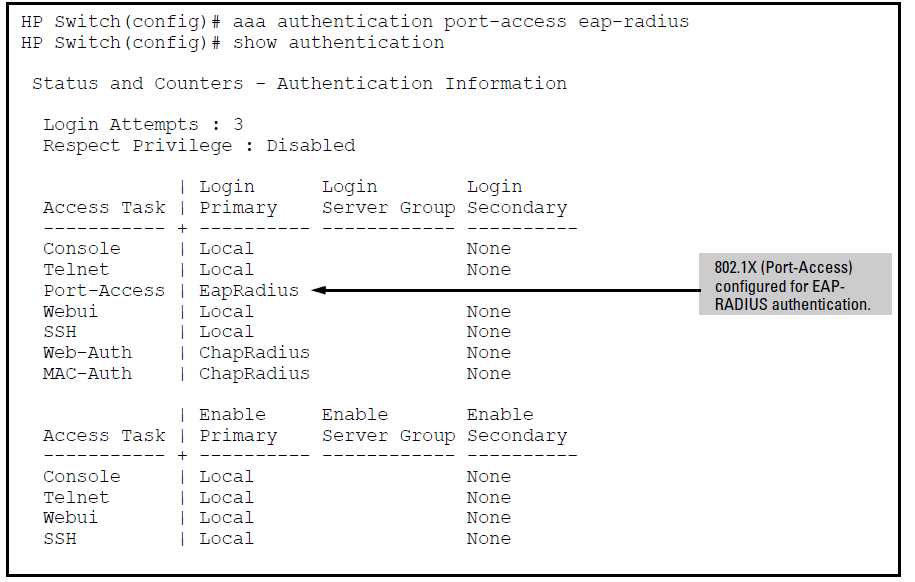
switch(config)# aaa authentication port-access eap-radius
Configures the switch for 802.1X authentication using an EAP-RADIUS server.
switch(config)# aaa port-access authenticator a10-a20
Configures ports A10 - A20 as 802.1 authenticator ports.
switch(config)# radius host 10.28.127.101 key rad4all
Configures the switch to look for a RADIUS server with an IP address of 10.28.127.101 and an encryption key of rad4all.
switch(config)# aaa port-access authenticator e a10-a20 unauth-vid 80
Configures ports A10 - A20 to use VLAN 80 as the Unauthorized-Client VLAN.
switch(config)# aaa port-access authenticator e a10-a20 auth-vid 81
Configures ports A10 - A20 to use VLAN 81 as the Authorized-Client VLAN.
switch(config)# aaa port-access authenticator active
Activates 802.1X port-access on ports you have configured as authenticators.
For information and an example on viewing current Open VLAN mode operation, see Viewing 802.1X Open VLAN Mode Status.
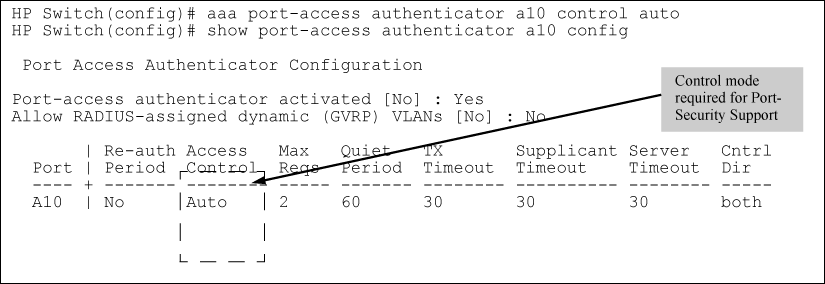
If 802.1X authentication is disabled on a port or set to authorized (Force Authorize), the port can allow access to a non-authenticated client. Port- Security operates with 802.1X authentication only if the selected ports are configured as 802.1X with the control mode in the port-access authenticator command set to auto (the default setting). For example, if port A10 was at a non-default 802.1X setting and you wanted to configure it to support the portsecurity option, you would use the following aaa port-access command:
Field table
| Field | Description |
|---|---|
| Port-access authenticator activated | Whether 802.1X authentication is enabled or disabled on specified ports. |
| Port | Port number on switch. |
| Re-auth Period | Period of time (in seconds) after which clients connected to the port need to be reauthenticated. |
| Access Control | Port’s authentication mode:Auto: Network access is allowed to any connected device that supports 802.1X authentication and provides valid 802.1X credentials.Authorized: Network access is allowed to any device connected to the port, regardless of whether it meets 802.1X criteria.Unauthorized: Network access is blocked to any device connected to the port, regardless of whether the device meets 802.1X criteria. |
| Max reqs | Number of authentication attempts that must time-out before authentication fails and the authentication session ends. |
| Quiet Period | Period of time (in seconds) during which the port does not try to acquire a supplicant. |
| TX Timeout | Period of time (in seconds) that the port waits to retransmit the next EAPOL PDU during an authentication session. |
| Supplicant Timeout | Period of time (in seconds) that the switch waits for a supplicant response to an EAP request. |
| Server Timeout | Period of time (in seconds) that the switch waits for a server response to an authentication request. |
| Cntrl Dir | Direction in which flow of incoming and outgoing traffic is blocked on 802.1X-aware port that has not yet entered the authenticated state: Both: Incoming and outgoing traffic is blocked on port until authentication occurs. In: Only incoming traffic is blocked on port before authentication occurs. Outgoing traffic with unknown destination addresses is flooded on the unauthenticated 802.1X-aware port. |
Syntax
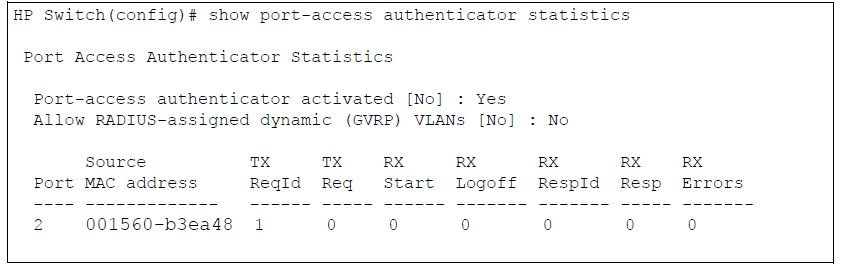
Displays statistical information for all switch ports or specified ports that are enabled as 802.1X authenticators, including:
Whether port-access authentication is enabled
Whether RADIUS-assigned dynamic VLANs are supported
802.1X supplicant’s MAC address as determined by the content of the last EAPOL frame received on the port
802.1X traffic statistics from received and transmitted packets
802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed
Syntax
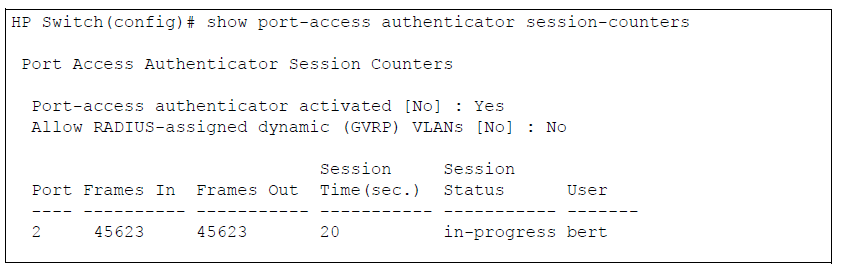
Displays information for active 802.1X authentication sessions on all switch ports or specified ports that are enabled as 802.1X authenticators, including:
802.1X frames received and transmitted on each port
Duration and status of active 802.1X authentication sessions (in-progress or terminated)
User name of 802.1X supplicant included in 802.1X response packets, configured with the aaa port-access supplicant identity
<username>command.802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed.
Syntax
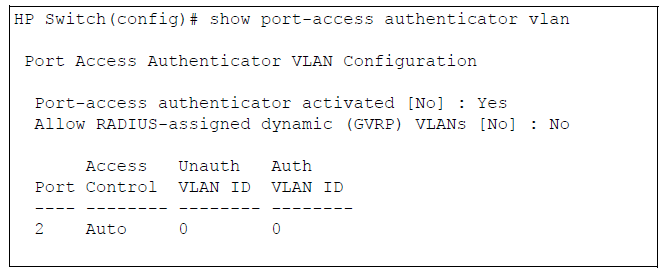
Displays the following information on the VLANs configured for use in 802.1X port-access authentication on all switch ports, or specified ports, that are enabled as 802.1X authenticator:
802.1X configuration information for ports that are not enabled as an 802.1X authenticators is not displayed.
Syntax
Displays the session status, name, and address for each 802.1X port-access-authenticated client on the switch. Multiple authenticated clients may be displayed for the same port. The IP address displayed is taken from the DHCP binding table (learned through the DHCP Snooping feature).
If DHCP snooping is not enabled on the switch, n/a (not available) is displayed for a client’s IP address.
If an 802.1X-authenticated client uses an IPv6 address, n/a - IPv6 is displayed.
If DHCP snooping is enabled but no MAC-to-IP address binding for a client is found in the DHCP binding table, n/a - no info is displayed.
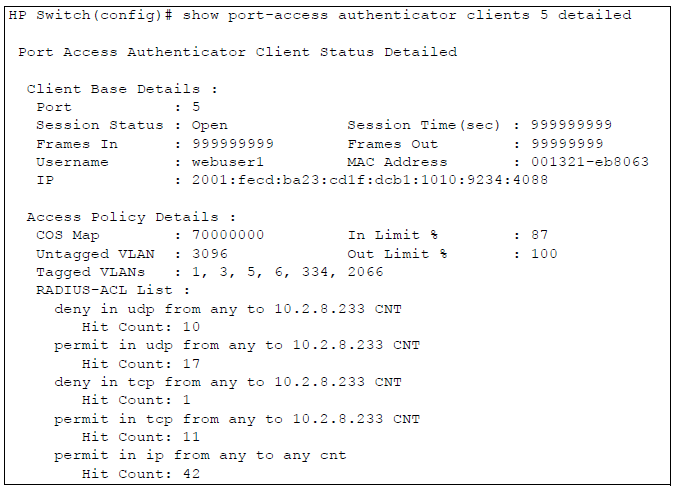
Syntax
Displays detailed information on the status of 802.1Xauthenticated client sessions on specified ports, including the matches the switch detects for individual ACEs configured with the cnt (counter) option in an ACL assigned to the port by a RADIUS server.
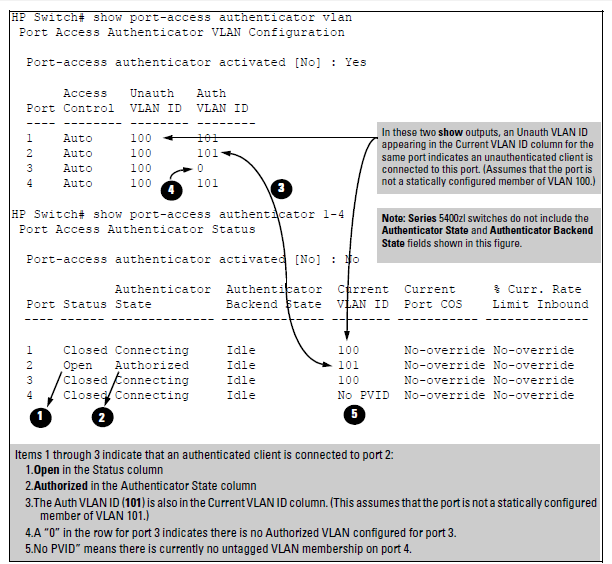
You can examine the switch’s current VLAN status by using the show port-access authenticator vlan and show port-access authenticator <port-list> commands as shown in the following figure and described in the following table.
-
When the Auth VLAN ID is configured and matches the Current VLAN ID, an authenticated client is connected to the port. (This assumes the port is not a statically configured member of the VLAN you are using for Auth VLAN.)
-
When the Unauth VLAN ID is configured and matches the Current VLAN ID, an unauthenticated client is connected to the port. (This assumes the port is not a statically configured member of the VLAN you are using for Unauth VLAN.)
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: That because a temporary Open VLAN port assignment to either an authorized or unauthorized VLAN is an untagged VLAN membership, these assignments temporarily replace any other untagged VLAN membership that is statically configured on the port. For example, if port 12 is statically configured as an untagged member of VLAN 1, but is configured to use VLAN 25 as an authorized VLAN, then the port’s membership in VLAN 1 will be temporarily suspended whenever an authenticated 802.1X client is attached to the port. |
|
|
Output for Determining Open VLAN Mode Status
| Status Indicator | Meaning |
|---|---|
| Access Control | This state is controlled by the following port-access command syntax:\
switch(config)# aaa port-access authenticator <port-list> control <authorized | auto | unauthorized>Auto: Configures the port to allow network access to any connected device that supports 802.1X authentication and provides valid 802.1X credentials. (This is the default authenticator setting.) Authorized: Configures the port for “Force Authorized”, which allows access to any device connected to the port, regardless of whether it meets 802.1X criteria. (You can still configure console, Telnet, or SSH security on the port.)Unauthorized: Configures the port for “Force Unauthorized”, which blocks access to any device connected to the port, regardless of whether the device meets 802.1X criteria. |
| Unauthorized VLAN ID | <vlan-id>: Lists the VID of the static VLAN configured as the unauthorized VLAN for the indicated port.0: No unauthorized VLAN has been configured for the indicated port. |
| Authorized VLAN ID | <vlan-id>: Lists the VID of the static VLAN configured as the authorized VLAN for the indicated port.0: No authorized VLAN has been configured for the indicated port. |
| Status | Closed: Either no client is connected or the connected client has not received authorization through 802.1X authentication.Open: An authorized 802.1X supplicant is connected to the port. |
| Current VLAN ID | <vlan-id>: Lists the VID of the static, untagged VLAN to which the port currently belongs.No PVID: The port is not an untagged member of any VLAN. |
| Current Port CoS | See RADIUS Authentication, Authorization, and Accounting. |
| % Curr. Rate Limit Inbound |
Syntax
Syntax
Shows the port-access supplicant configuration (excluding the secret parameter) for all ports or <portlist> ports configured on the switch as supplicants. The Supplicant State can include the following:
Connecting
Starting authentication. Authenticated - Authentication completed (regardless of whether the attempt was successful).
Acquired
The port received a request for identification from an authenticator.
Authenticating
Authentication is in progress.
Held
Authenticator sent notice of failure. The supplicant port is waiting for the authenticator’s held-period.
For descriptions of the supplicant parameters, see Configuring a Supplicant Switch Port.
Shows the port-access statistics and source MAC addresses for all ports or <port-list> ports configured on the switch as supplicants. See the “Note on Supplicant Statistics”, below.
For each port configured as a supplicant, show port-access supplicant statistics <port-list>] displays the source MAC address and statistics for transactions with the authenticator device most recently detected on the port. If the link between the supplicant port and the authenticator device fails, the supplicant port continues to show data received from the connection to the most recent authenticator device until one of the following occurs:
-
The supplicant port detects a different authenticator device.
-
You use the aaa port-access supplicant <port-list> clear-statistics command to clear the statistics for the supplicant port.
-
The switch reboots.
Thus, if the supplicant’s link to the authenticator fails, the supplicant retains the transaction statistics it most recently received until one of the above events occurs. Also, if you move a link with an authenticator from one supplicant port to another without clearing the statistics data from the first port, the authenticator’s MAC address will appear in the supplicant statistics for both ports.
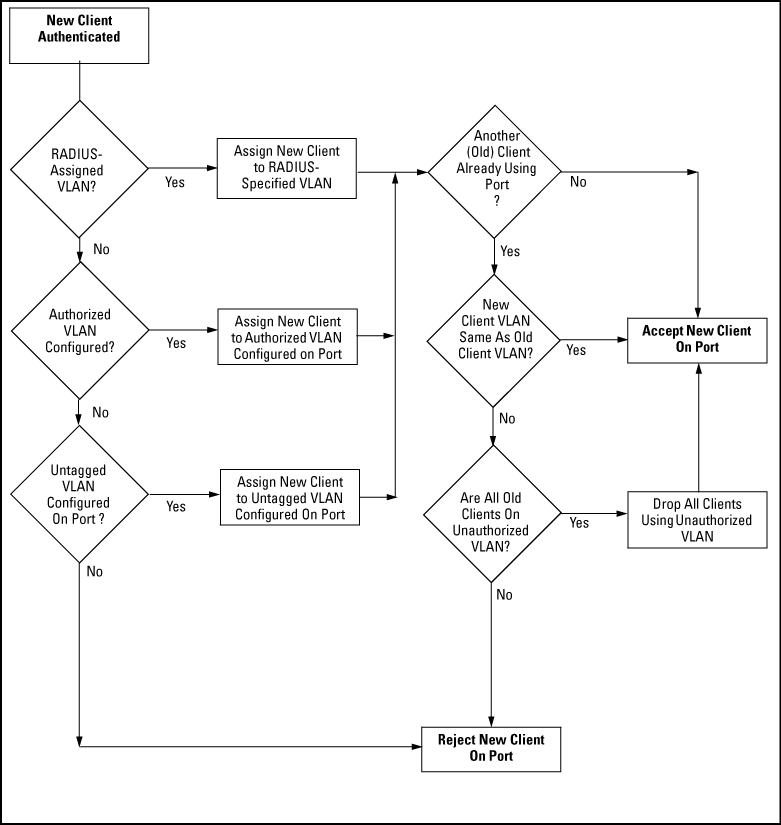
Static VLAN Requirement. RADIUS authentication for an 802.1X client on a given port can include a (static) VLAN requirement. (Refer to the documentation provided with your RADIUS application.) The static VLAN to which a RADIUS server assigns a client must already exist on the switch. If it does not exist or is a dynamic VLAN (created by GVRP), authentication fails. Also, for the session to proceed, the port must be an untagged member of the required VLAN. If it is not, the switch temporarily reassigns the port as described below.
If the Port Used by the Client Is Not Configured as an Untagged Member of the Required Static VLAN: When a client is authenticated on port “N”, if port “N” is not already configured as an untagged member of the static VLAN specified by the RADIUS server, then the switch temporarily assigns port “N” as an untagged member of the required VLAN (for the duration of the 802.1X session). At the same time, if port “N” is already configured as an untagged member of another VLAN, port “N” loses access to that other VLAN for the duration of the session. (This is because a port can be an untagged member of only one VLAN at a time.) Using a RADIUS server to authenticate clients, you can provide port-level security protection from unauthorized network access for the following authentication methods:
-
802.1X: Port-based or client-based access control to open a port for client access after authenticating valid user credentials.
-
MAC address: Authenticates a device’s MAC address to grant access to the network
-
WebAgent: Authenticates clients for network access using a webpage for user login.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: You can use 802.1X (port-based or client-based) authentication and either Web or MAC authentication at the same time on a port, with a maximum of 32 clients allowed on the port. (The default is one client.) Web authentication and MAC authentication are mutually exclusive on the same port. Also, you must disable LACP on ports configured for any of these authentication methods. For more information, see About web and MAC authentication. |
|
|
Following client authentication, VLAN configurations on a port are managed as follows when you use 802.1X, MAC, or Web authentication:
-
The port resumes membership in any tagged VLANs for which it is already assigned in the switch configuration. Tagged VLAN membership allows a port to be a member of multiple VLANs simultaneously.
-
The port is temporarily assigned as a member of an untagged (static or dynamic) VLAN for use during the client session according to the following order of options.
-
The port joins the VLAN to which it has been assigned by a RADIUS server during client authentication.
-
If RADIUS authentication does not include assigning the port to a VLAN, then the switch assigns the port to the authorized-client VLAN configured for the authentication method.
-
If the port does not have an authorized-client VLAN configured, but is configured for membership in an untagged VLAN, the switch assigns the port to this untagged VLAN.
-
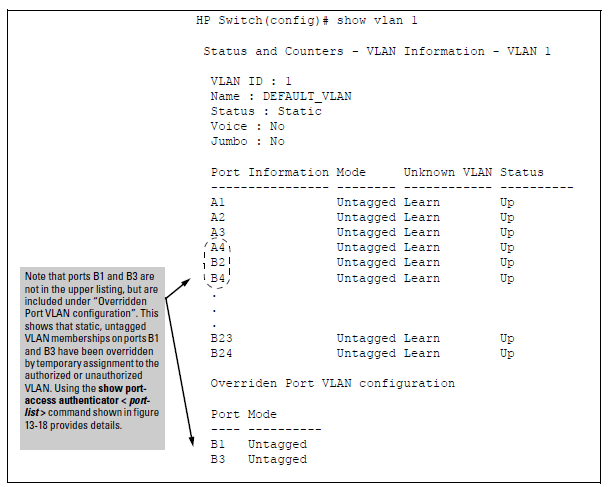
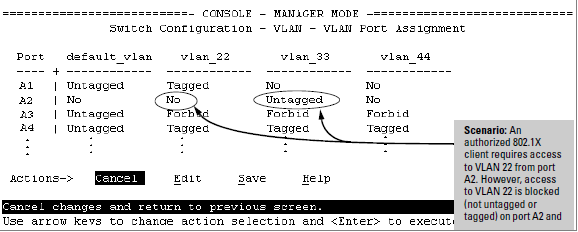
The following example shows how an untagged static VLAN is temporarily assigned to a port for use during an 802.1X authentication session. In the example, an 802.1X-aware client on port A2 has been authenticated by a RADIUS server for access to VLAN 22. However, port A2 is not configured as a member of VLAN 22 but as a member of untagged VLAN 33 as shown in Active VLAN Configuration.
For example, suppose that a RADIUS-authenticated, 802.1X-aware client on port A2 requires access to VLAN 22, but VLAN 22 is configured for no access on port A2, and VLAN 33 is configured as untagged on port A2:
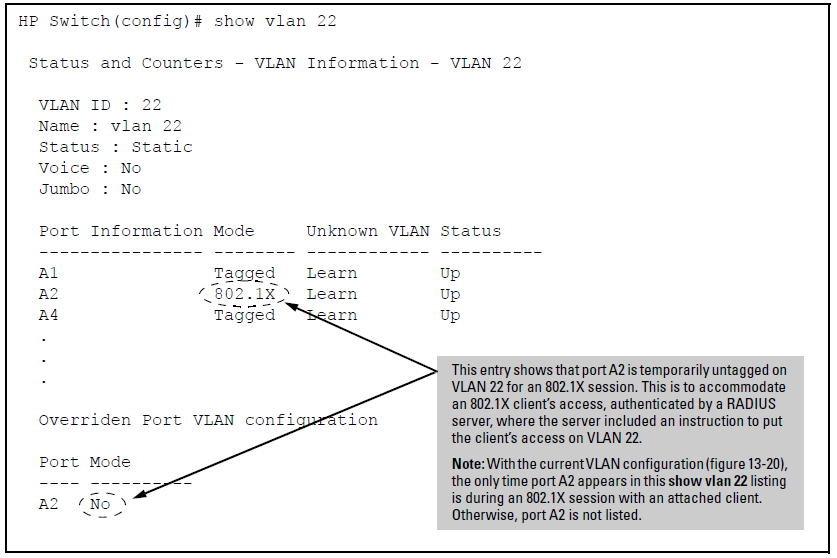
In Active VLAN Configuration, if RADIUS authorizes an 802.1X client on port A2 with the requirement that the client use VLAN 22, then: VLAN 22 becomes available as Untagged on port A2 for the duration of the session. VLAN 33 becomes unavailable to port A2 for the duration of the session (because there can be only one untagged VLAN on any port). To view the temporary VLAN assignment as a change in the active configuration, use the show vlan <vlan-id> command as shown in The Active Configuration for VLAN 22 Temporarily Changes for the 802.1X Session where <vlan-id> is the (static or dynamic) VLAN used in the authenticated client session.
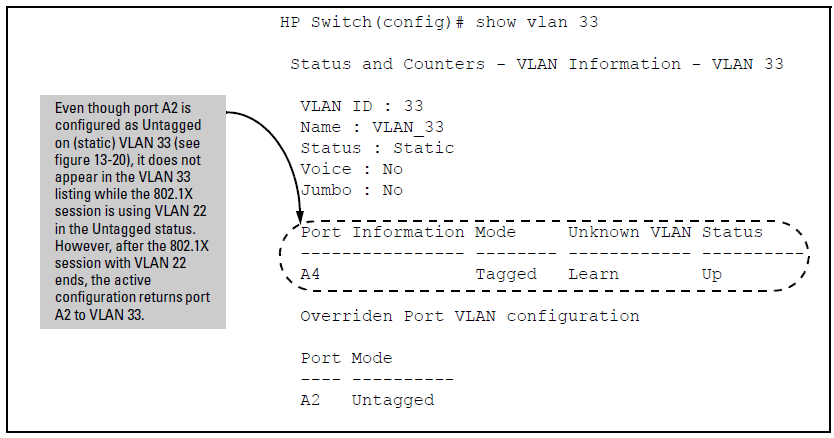
However, as shown in Active VLAN Configuration, because VLAN 33 is configured as untagged on port A2 and because a port can be untagged on only one VLAN, port A2 loses access to VLAN 33 for the duration of the 802.1X session on VLAN 22. You can verify the temporary loss of access to VLAN 33 by entering the show vlan 33 command as shown in The Active Configuration for VLAN 33 Temporarily Drops Port 22 for the 802.1X Session.
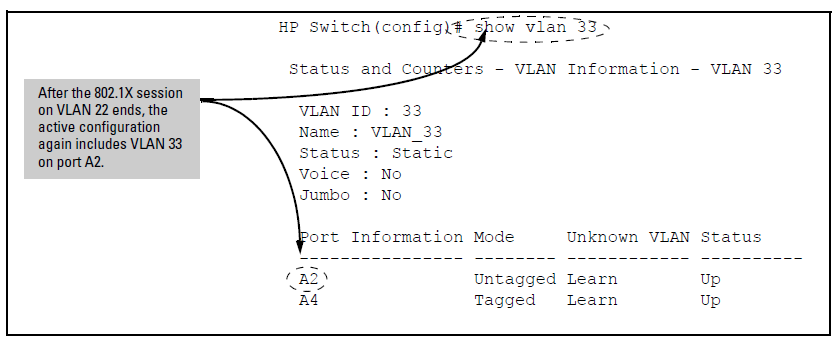
When the 802.1X client’s session on port A2 ends, the port removes the temporary untagged VLAN membership. The static VLAN (VLAN 33) that is “permanently” configured as untagged on the port becomes available again. Therefore, when the RADIUS-authenticated 802.1X session on port A2 ends, VLAN 22 access on port A2 also ends, and the untagged VLAN 33 access on port A2 is restored as shown in The Active Configuration for VLAN 33 Restores Port A2 After the 802.1X Session Ends.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If 802.1X port-access is configured on a given port, then port-security learnmode for that port must be set to either continuous (the default) or port-access. |
|
|
In addition to the above, to use port-security on an authenticator port, use the per-port client-limit option to control how many MAC addresses of 802.1X-authenticated devices the port is allowed to learn. (Using client-limit sets 802.1X to user-based operation on the specified ports.) When this limit is reached, no further devices can be authenticated until a currently authenticated device disconnects and the current delay period or logoff period has expired.
Syntax
Configures user-based 802.1X authentication on the specified ports and sets the number of authenticated devices the port is allowed to learn. For more on this command, see Configuring switch ports as 802.1X authenticators.
Alternative
Syntax
Configures port-based 802.1X authentication on the specified ports, which opens the port. (See User Authentication Methods.)
A switch port can operate as a supplicant in a connection to a port on another 802.1X-aware switch to provide security on links between 802.1X-aware switches. (A port can operate as both an authenticator and a supplicant.)
Example
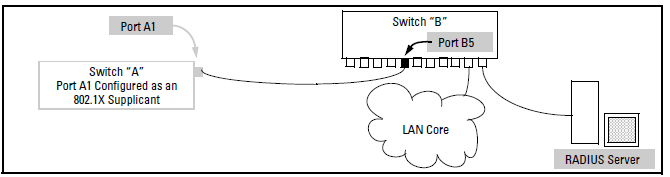
Suppose that you want to connect two switches, where:
-
When port A1 on switch “A” is first connected to a port on switch “B”, or if the ports are already connected and either switch reboots, port A1 begins sending start packets to port B5 on switch “B”.
-
If, after the supplicant port sends the configured number of start packets, it does not receive a response, it assumes that switch “B” is not 802.1X-aware, and transitions to the authenticated state. If switch “B” is operating properly and is not 802.1X-aware, then the link should begin functioning normally, but without 802.1X security. and password.
-
If, after sending one or more start request packets, port A1 receives a request packet from port B5, then switch “B” is operating as an 802.1X authenticator. The supplicant port then sends a response/ID packet. If switch “B” is configured for RADIUS authentication, it forwards this request to a RADIUS server. If switch “B” is configured for Local 802.1X authentication, the authenticator compares the switch “A” response to its local user name
-
-
The RADIUS server then responds with an MD5 access challenge that switch “B” forwards to port A1 on switch “A”.
-
Port A1 replies with an MD5 hash response based on its user name and password or other unique credentials. Switch “B” forwards this response to the RADIUS server.
-
The RADIUS server then analyzes the response and sends either a “success” or “failure” packet back through switch “B” to port A1.
You can configure a switch port as a supplicant for a point-to-point link to an 802.1X-aware port on another switch. Configure the port as a supplicant before configuring any supplicant- related parameters.
Syntax
You must enable supplicant operation on a port before changing the supplicant configuration. This means you must execute the supplicant command once without any other parameters, then execute it again with a supplicant parameter you want to configure. If the intended authenticator port uses RADIUS authentication, then use the identity and secret options to configure the RADIUS-expected credentials on the supplicant port. If the intended authenticator port uses Local 802.1X authentication, then use the identity and secret options to configure the authenticator switch’s local user name and password on the supplicant port.
Syntax
To enable supplicant operation on the designated ports, execute this command without any other parameters. After doing this, you can use the command again with the following parameters to configure supplicant operation. (Use one instance of the command for each parameter you want to configure The no form disables supplicant operation on the designated ports.
Sets the user name and password to pass to the authenticator port when a challenge-request packet is received from the authenticator port due to an authentication request. If the intended authenticator port is configured for RADIUS authentication, then <username> and <password> must be the username and password expected by the RADIUS server. If the intended authenticator port is configured for Local authentication, then <username> and <password> must be the user name and password configured on the Authenticator switch. (Default: Null.)
Sets the secret password to be used by the port supplicant when an MD5 authentication request is received from an authenticator. The switch prompts you to enter the secret password after the command is invoked.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: For the 3800, 5400zl, and 8200zl switches, when the switch is in enhanced secure mode, commands that take a password as a parameter have the echo of the password typing replaced with asterisks. The input for the password is prompted for interactively. For more information, see Secure Mode (3800, 5400zl, and 8200zl Switches). |
|
|
Specify secret as a base64-encoded aes-256 encrypted string.
Sets the delay period the port waits to receive a challenge from the authenticator. If the request times out, the port sends another request, up to the number of attempts specified by the max-start parameter. (Default: 30 seconds).
Defines the maximum number of times the supplicant port requests authentication. (Default: 3).
Sets the time period the supplicant port waits after an active 802.1X session fails before trying to re- acquire the authenticator port. (Default: 60 seconds)
Sets the delay between Start packet retransmissions. That is, after a supplicant sends a start packet, it waits during the start-period for a response. If no response comes during the start- period, the supplicant sends a new start packet. The max-start setting (above) specifies how many start attempts are allowed in the session. (Default: 30 seconds)
On the specified ports, blocks inbound and outbound traffic and restarts the 802.1X authentication process. Affects only ports configured as 802.1X supplicants.
Clears and restarts the 802.1X supplicant statistics counters.
This operation provides security on a point-to-point link between a client and the switch, where both devices are 802.1X-aware. (If you expect desirable clients that do not have the necessary 802.1X supplicant software, you can provide a path for downloading such software by using the 802.1X Open VLAN mode—see 802.1X Open VLAN mode.)
Suppose that you have configured a port on the switch for 802.1X authentication operation, which blocks access to the LAN through that port. If you then connect an 802.1X-aware client (supplicant) to the port and attempt to log on:
-
The client responds with a user name that uniquely defines this request for the client.
-
The switch responds in one of the following ways:
-
If 802.1X on the switch is configured for RADIUS authentication, the switch then forwards the request to a RADIUS server.
-
The server responds with an access challenge which the switch forwards to the client.
-
The client then provides identifying credentials (such as a user certificate), which the switch forwards to the RADIUS server.
-
The RADIUS server then checks the credentials provided by the client. iv. If the client is successfully authenticated and authorized to connect to the network, then the server notifies the switch to allow access to the client. Otherwise, access is denied and the port remains blocked.
-
-
If 802.1X on the switch is configured for local authentication, then
-
The switch compares the client’s credentials to the user name and password configured in the switch (Operator level).
-
If the client is successfully authenticated and authorized to connect to the network, then the switch allows access to the client. Otherwise, access is denied and the port remains blocked for that client.
-
![[NOTE: ]](images/note.gif)
NOTE: The switches covered in this guide can use either 802.1X port-based authentication or 802.1X user-based authentication. See User Authentication Methods.
-
Following client authentication, an 802.1X port resumes membership in any tagged VLANs for which it is already assigned in the switch configuration. The port also becomes an untagged member of one VLAN according to the following order of options:
-
1st Priority: The port joins a VLAN to which it has been assigned by a RADIUS server during client authentication.
-
2nd Priority: If RADIUS authentication does not include assigning the port to a VLAN, then the switch assigns the port to the VLAN entered in the port’s 802.1X configuration as an Authorized-Client VLAN, if configured
-
3rd Priority: If the port does not have an Authorized-Client VLAN configured, but does have a static, untagged VLAN membership in its configuration, then the switch assigns the port to this VLAN.
A port assigned to a VLAN by an Authorized-Client VLAN configuration (or a RADIUS server) will be an untagged member of the VLAN for the duration of the authenticated session. This applies even if the port is also configured in the switch as a tagged member of the same VLAN.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: On the switches covered in this guide, using the same port for both RADIUS-assigned clients and clients using a configured, Authorized-Client VLAN is not recommended. This is because doing so can result in authenticated clients with mutually exclusive VLAN priorities, which means that some authenticated clients can be denied access to the port. See Priority of VLAN Assignment for an Authenticated Client. |
|
|