The security settings that can be saved to a configuration file are:
The benefits of including and saving security credentials in a configuration file are:
-
After making changes to security replaceables in the running configuration, you can experiment with the new configuration and, if necessary, view the new security settings during the session. After verifying the configuration, you can then save it permanently by writing the settings to the startup-config file.
-
By permanently saving a switch security credentials in a configuration file, you can upload the file to a TFTP server or Xmodem host, and later download the file to the switches on which you want to use the same security settings without having to manually configure the settings (except for SNMPv3 user replaceables) on each switch.
-
By storing different security settings in different files, you can test different security configurations when you first download a new software version that supports multiple configuration files, by changing the configuration file used when you reboot the switch.
For more information about how to experiment with, upload, download, and use configuration files with different software versions, see:
-
"Switch Memory and Configuration" in the management and configuration guide.
The information saved to the running-config file when the include-credentials command is entered includes:
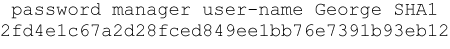
password manager [user-name <name>] <hash-type> <pass-hash> password operator [user-name <name>] <hash-type> <pass-hash>
<name>is an alphanumeric string for the user name assigned to the manager or operator.
<hash-type>indicates the type of hash algorithm used: SHA-1 or plain text.
<pass-hash>is the SHA-1 authentication protocol's hash of the password or clear ASCII text.
For example, a manager user name and password can be stored in a running-config file as follows:
Use the write memory command to save the password configurations in the startup-config file. The passwords take effect when the switch boots with the software version associated with that configuration file.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: If a |
|
|
SNMPv1 community names and write access settings, and SNMPv3 user names, continue to be saved in the startup-config file even when entering the include-credentials command.
In addition, the following SNMPv3 security replaceables are saved:
where: <name> is the name of an SNMPv3 management station.
[ auth <md5 | sha> ]
is the optional authentication method used for the management station.
auth-pass is the hashed authentication password used with the configured authentication method.
[ privpriv-pass ]
is the optional hashed privacy password used by a privacy protocol to encrypt SNMPv3 messages between the switch and the station.
The following example shows the additional security credentials for SNMPv3 users that can be saved in a running-config file:
Although you can enter a SNMPv3 authentication or privacy password in either clear ASCII text or the SHA-1 hash of the password, the password is displayed and saved in a configuration file only in hashed format, as shown in Example of security credentials saved in the running-config.
For more information about the configuration of SNMP security replaceables, see "Configuring for Network Management Applications" in management and configuration guide for your switch.
802.1X authenticator (port-access) credentials can be stored in a configuration file.
-
802.1X authenticator credentials are used by a port to authenticate supplicants requesting a point-to-point connection to the switch.
-
802.1X supplicant credentials are used by the switch to establish a point-to-point connection to a port on another 802.1X-aware switch.
Only 802.1X authenticator credentials are stored in a configuration file. For information about how to use 802.1X on the switch both as an authenticator and a supplicant, see Storing 802.1X port-access credentials.
The local password configured with the password command is no longer accepted as an 802.1X authenticator credential. A new configuration command password port-access is introduced to configure the local operator user name and password used as 802.1X authentication credentials for access to the switch.
The password port-access values are now configured separately from the manager and operator passwords configured with the password manager and password operator commands and used for management access to the switch. For information on the new password command syntax, see Setting a new console password
After entering the complete password port-access command, the password is set. You are not prompted to enter the password a second time.
The following table shows the states of several access types when the factory default settings are in effect or when include-credentials is enabled or not enabled.
| Type | Factory default | include-credentials enabled |
include-credentials disabled but active |
[no]include-credentials executed |
||||||
|---|---|---|---|---|---|---|---|---|---|---|
| manager/operator passwords & port access |
Single set for switch. Stored outside config. Not displayed in config file. |
One set per stored config. Stored in config. Displayed in config. |
Same as Not displayed in config |
One set for switch No credentials displayed in config |
||||||
| SSH Public Key |
One set for switch Stored in flash Not displayed in config |
One set per stored config Stored in flash Displayed in config |
Same as Not displayed in config |
One set for switch No credentials displayed in config |
||||||
| SNMPv3 auth and priv |
Stored in flash Not displayed in config |
Stored in flash Displayed in config |
Same as Not displayed in config |
No credentials displayed in config |
||||||
| RADIUS & TACACS keystrings | Not displayed in config |
Stored in flash Displayed in config |
Same as Not displayed in config |
No credentials displayed in config |
||||||
|
||||||||||
![[no]front-panel-security password-clear](images/Graphics/figure_2-20.png)

![[NOTE: ]](images/note.gif)