As your network expands to include an increasing number of mobile devices, continuous Internet access, and new classes of users (such as partners, temporary employees, and visitors), additional protection from attacks launched from both inside and outside your internal network is often necessary.
Advanced threat protection can detect port scans and hackers who try to access a port or the switch itself. The following software features provide advanced threat protection and are described here:
You can use DHCP snooping to help avoid the Denial of Service attacks that result from unauthorized users adding a DHCP server to the network that then provides invalid configuration data to other DHCP clients on the network. DHCP snooping accomplishes this by allowing you to distinguish between trusted ports connected to a DHCP server or switch and untrusted ports connected to end-users. DHCP packets are forwarded between trusted ports without inspection. DHCP packets received on other switch ports are inspected before being forwarded. Packets from untrusted sources are dropped. Conditions for dropping packets are shown below.
Condition for dropping a packet
| Condition for Dropping a Packet | Packet Type |
|---|---|
| A packet from a DHCP server received on an untrusted port | DHCPOFFER, DHCPACK, DHCPNACK |
| If the switch is configured with a list of authorized DHCP server addresses and a packet is received from a DHCP server on a trusted port with a source IP address that is not in the list of authorized DHCP server addresses. | DHCPOFFER, DHCPACK, DHCPNACK |
| Unless configured to not perform this check, a DHCP packet received on an untrusted port where the DHCP client hardware address field does not match the source MAC address in the packet | N/A |
| Unless configured to not perform this check, a DHCP packet containing DHCP relay information (option 82) received from an untrusted port | N/A |
| A broadcast packet that has a MAC address in the DHCP binding database, but the port in the DHCP binding database is different from the port on which the packet is received | DHCPRELEASE, DHCPDECLINE |
-
DHCP is not configurable from the WebAgent or menu interface.
-
If packets are received at too high a rate, some may be dropped and need to be re-transmitted.
-
HP recommends running a time synchronization protocol such as SNTP in order to track lease times accurately.
-
A remote server must be used to save lease information or there may be a loss of connectivity after a switch reboot.
On the VLAN interfaces of a routing switch, dynamic ARP protection ensures that only valid ARP requests and responses are relayed or used to update the local ARP cache. ARP packets with invalid IP-to-MAC address bindings advertised in the source protocol address and source physical address fields are discarded. For more information about the ARP cache, see “ARP Cache Table” in the Multicast and Routing Guide.
ARP requests are ordinarily broadcast and received by all devices in a broadcast domain. Most ARP devices update their IP-to-MAC address entries each time they receive an ARP packet even if they did not request the information. This behavior makes an ARP cache vulnerable to attacks.
Because ARP allows a node to update its cache entries on other systems by broadcasting or unicasting a gratuitous ARP reply, an attacker can send his own IP-to-MAC address binding in the reply that causes all traffic destined for a VLAN node to be sent to the attacker's MAC address. As a result, the attacker can intercept traffic for other hosts in a classic "man-in-the-middle" attack. The attacker gains access to any traffic sent to the poisoned address and can capture passwords, e-mail, and VoIP calls or even modify traffic before resending it.
Another way in which the ARP cache of known IP addresses and associated MAC addresses can be poisoned is through unsolicited ARP responses. For example, an attacker can associate the IP address of the network gateway with the MAC address of a network node. In this way, all outgoing traffic is prevented from leaving the network because the node does not have access to outside networks. As a result, the node is overwhelmed by outgoing traffic destined to another network.
Dynamic ARP protection is designed to protect your network against ARP poisoning attacks in the following ways:
-
Allows you to differentiate between trusted and untrusted ports.
-
Intercepts all ARP requests and responses on untrusted ports before forwarding them.
-
Verifies IP-to-MAC address bindings on untrusted ports with the information stored in the lease database maintained by DHCP snooping and userconfigured static bindings (in non-DHCP environments):
DHCP snooping intercepts and examines DHCP packets received on switch ports before forwarding the packets. DHCP packets are checked against a database of DHCP binding information. Each binding consists of a client MAC address, port number, VLAN identifier, leased IP address, and lease time. The DHCP binding database is used to validate packets by other security features on the switch. For more information, see DHCP Snooping.
If you have already enabled DHCP snooping on a switch, you may also want to add static IP-to-MAC address bindings to the DHCP snooping database so that ARP packets from devices that have been assigned static IP addresses are also verified.
When dynamic ARP protection is enabled, only ARP request and reply packets with valid IP-to-MAC address bindings in their packet header are relayed and used to update the ARP cache.
Dynamic ARP protection is implemented in the following ways on a switch:
-
You can configure dynamic ARP protection only from the CLI; you cannot configure this feature from the WebAgent or menu interfaces.
-
Line rate—Dynamic ARP protection copies ARP packets to the switch CPU, evaluates the packets, and then re-forwards them through the switch software. During this process, if ARP packets are received at too high a line rate, some ARP packets may be dropped and will need to be retransmitted.
-
The SNMP MIB, HP-ICF-ARP-PROTECT-MIB, is created to configure dynamic ARP protection and to report ARP packet-forwarding status and counters.
The Dynamic IP Lockdown feature is used to prevent IP source address spoofing on a per-port and per-VLAN basis. When dynamic IP lockdown is enabled, IP packets in VLAN traffic received on a port are forwarded only if they contain a known source IP address and MAC address binding for the port. The IP-to-MAC address binding can either be statically configured or learned by the DHCP Snooping feature.
Many network attacks occur when an attacker injects packets with forged IP source addresses into the network. Also, some network services use the IP source address as a component in their authentication schemes. For example, the BSD “r” protocols (rlogin, rcp, rsh) rely on the IP source address for packet authentication. SNMPv1 and SNMPv2c also frequently use authorized IP address lists to limit management access. An attacker that is able to send traffic that appears to originate from an authorized IP source address may gain access to network services for which he is not authorized. Dynamic IP lockdown provides protection against IP source address spoofing by means of IP-level port security. IP packets received on a port enabled for dynamic IP lockdown are only forwarded if they contain a known IP source address and MAC address binding for the port. Dynamic IP lockdown uses information collected in the DHCP Snooping lease database and through statically configured IP source bindings to create internal, per-port lists. The internal lists are dynamically created from known IPto- MAC address bindings to filter VLAN traffic on both the source IP address and source MAC address.
Dynamic IP lockdown requires that you enable DHCP snooping as a prerequisite for its operation on ports and VLAN traffic:
-
Dynamic IP lockdown only enables traffic for clients whose leased IP addresses are already stored in the lease database created by DHCP snooping or added through a static configuration of an IP-to-MAC binding. Therefore, if you enable DHCP snooping after dynamic IP lockdown is enabled, clients with an existing DHCP-assigned address must either request a new leased IP address or renew their existing DHCP-assigned address. Otherwise, a client’s leased IP address is not contained in the DHCP binding database. As a result, dynamic IP lockdown does not allow inbound traffic from the client.
-
It is recommended that you enable DHCP snooping a week before you enable dynamic IP lockdown to allow the DHCP binding database to learn clients’ leased IP addresses. You must also ensure that the lease time for the information in the DHCP binding database lasts more than a week.
Alternatively, you can configure a DHCP server to re-allocate IP addresses to DHCP clients. In this way, you repopulate the lease database with current IP-to-MAC bindings. 11-25 Configuring Advanced Threat Protection Dynamic IP Lockdown
-
The DHCP binding database allows VLANs enabled for DHCP snooping to be known on ports configured for dynamic IP lockdown. As new IP-to-MAC address and VLAN bindings are learned, a corresponding permit rule is dynamically created and applied to the port (preceding the final deny any vlan <VLAN_IDs> rule. These VLAN_IDs correspond to the subset of configured and enabled VLANS for which DHCP snooping has been configured.
-
For dynamic IP lockdown to work, a port must be a member of at least one VLAN that has DHCP snooping enabled.
-
Disabling DHCP snooping on a VLAN causes Dynamic IP bindings on Dynamic IP Lockdown-enabled ports in this VLAN to be removed. The port reverts back to switching traffic as usual.
This section contains an example that shows the following aspects of the Dynamic IP Lockdown feature:
-
Internal Dynamic IP lockdown bindings dynamically applied on a per-port basis from information in the DHCP Snooping lease database and statically configured IP-to-MAC address bindings
-
Packet filtering using source IP address, source MAC address, and source VLAN as criteria.
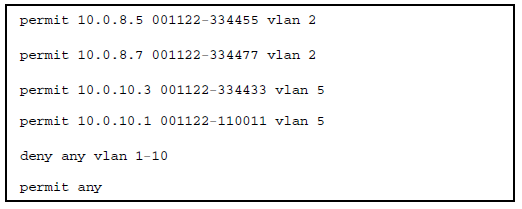
In this example, the following DHCP leases have been learned by DHCP snooping on port 5. VLANs 2 and 5 are enabled for DHCP snooping.
Sample DHCP snooping entries
| IP Address | MAC Address | VLAN ID |
|---|---|---|
| 10.0.8.5 | 001122–334455 | 2 |
| 10.0.8.7 | 001122–334477 | 2 |
| 10.0.10.3 | 001122–334433 | 5 |
The following example shows an IP-to-MAC address and VLAN binding that have been statically configured in the lease database on port 5.
Assuming that DHCP snooping is enabled and that port 5 is untrusted, dynamic IP lockdown applies the following dynamic VLAN filtering on port 5:
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The deny any statement is applied only to VLANs for which DHCP snooping is enabled. The permit any statement is applied only to all other VLANs. |
|
|
-
Dynamic IP lockdown is enabled at the port configuration level and applies to all bridged or routed IP packets entering the switch. The only IP packets that are exempt from dynamic IP lockdown are broadcast DHCP request packets, which are handled by DHCP snooping.
-
DHCP snooping is a prerequisite for Dynamic IP Lockdown operation. The following restrictions apply:
-
DHCP snooping is required for dynamic IP lockdown to operate. To enable DHCP snooping, enter the
dhcp-snoopingcommand at the global configuration level. -
Dynamic IP lockdown only filters packets in VLANs that are enabled for DHCP snooping. In order for Dynamic IP lockdown to work on a port, the port must be configured for at least one VLAN that is enabled for DHCP snooping.
To enable DHCP snooping on a VLAN, enter the
dhcp-snooping vlan [vlan-id-range]command at the global configuration level or thedhcp-snoopingcommand at the VLAN configuration level. -
Dynamic IP lockdown is not supported on a trusted port. (However, note that the DHCP server must be connected to a trusted port when DHCP snooping is enabled.)
By default, all ports are untrusted. To remove the trusted configuration from a port, enter the
no dhcp-snooping trust <port-list>orno dhcp6-snooping trust <port-list>command at the global configuration level.
For more information on how to configure and use DHCP snooping, see DHCP Snooping.
-
-
After you enter the
ip source-lockdowncommand (enabled globally with the desired ports entered in <port-list> the dynamic IP lockdown feature remains disabled on a port if any of the following conditions exist:Dynamic IP lockdown is activated on the port only after you make the following configuration changes:
-
You can configure dynamic IP lockdown only from the CLI; this feature cannot be configured from the WebAgent or menu interface.
-
If you enable dynamic IP lockdown on a port, you cannot add the port to a trunk.
-
Dynamic IP lockdown must be removed from a trunk before the trunk is removed.
There are some differences in the feature set and operation of Dynamic IP Lockdown, depending on the switch on which it is implemented. These are listed below.
-
There is no restriction on GVRP on 3500/5400 switches. On 2600/2800/ 3400 switches, Dynamic IP Lockdown is not supported if GVRP is enabled on the switch.
-
Dynamic IP Lockdown has the host limits shown in the table below. There is a DHCP snooping limit of 8,192 entries.
-
A source is considered “trusted” for all VLANs if it is seen on any VLAN without DHCP snooping enabled.
-
On the HP switch series 5400 and 3500, dynamic IP lockdown is supported on a port configured for statically configured port-based ACLs.
Differences in switch platforms
| Switch | Number of Hosts | Comments |
|---|---|---|
| 3500/5400 | 64 bindings per port Up to 4096 manual bindings per switch | This limit is shared with DHCP snooping because they both use the snooping database. |
| 3400/2800 | 32 bindings per port; up to 512 manual bindings Up to 32 VLANs with DHCP snooping enabled | This is not guaranteed as the hardware resources are shared with QoS. |
| 2610 | 8 bindings per port; up to 512 manual bindings Globally 118 to 125 hosts Up to 8 VLANs with DHCP snooping enabled | This is not guaranteed as the hardware resources are shared with IDM ACLs. The number of global bindings available is based on the number o f DHCP snooping-enabled VLANS (1-8). |
| 2600 | 8 bindings per port; up to 512 manual bindings Up to 8 VLANs with DHCP snooping enabled | This is not guaranteed as the hardware resources are shared with QoS. |
A switch maintains a DHCP binding database, which is used for dynamic IP lockdown as well as for DHCP and ARP packet validation. The DHCP snooping feature maintains the lease database by learning the IP-to-MAC bindings of VLAN traffic on untrusted ports. Each binding consists of the client MAC address, port number, VLAN identifier, leased IP address, and lease time.
Dynamic IP lockdown supports a total of 4K static and dynamic bindings with up to 64 bindings per port. When DHCP snooping is enabled globally on a VLAN, dynamic bindings are learned when a client on the VLAN obtains an IP address from a DHCP server. Static bindings are created manually with the CLI or from a downloaded configuration file.
When dynamic IP lockdown is enabled globally or on ports the bindings associated with the ports are written to hardware. This occurs during these events:
-
When dynamic IP lockdown enabled, and a port or switch has the maximum number of bindings configured, the client DHCP request is dropped and the client does not receive an IP address through DHCP.
-
When dynamic IP lockdown is enabled and a port is configured with the maximum number of bindings, adding a static binding to the port fails.
-
When dynamic IP lockdown is enabled globally, the bindings for each port are written to hardware. If global dynamic IP lockdown is enabled and disabled several times, it is possible to run out of buffer space for additional bindings. The software delays adding the bindings to hardware until resources are available.
The instrumentation monitor can be used to detect anomalies caused by security attacks or other irregular operations on the switch. The following table shows the operating parameters that can be monitored at pre-determined intervals, and the possible security attacks that may trigger an alert:
Parameters for monitoring
| Parameter Name | Description |
|---|---|
| pkts-to-closed-ports | The count of packets per minute sent to closed TCP/UDP ports. An excessive amount of packets could indicate a port scan, in which an attacker is attempting to expose a vulnerability in the switch. |
| arp-requests | The count of ARP requests processed per minute. A large amount of ARP request packets could indicate an host infected with a virus that is trying to spread itself. |
| ip-address-count | The number of destination IP addresses learned in the IP forwarding table. Some attacks fill the IP forwarding table causing legitimate traffic to be dropped. |
| system-resource-usage | The percentage of system resources in use. Some Denial-of- Service (DoS) attacks cause excessive system resource usage, resulting in insufficient resources for legitimate traffic.
|
| login-failures/min | The count of failed CLI login attempts or SNMP management authentication failures. This indicates an attempt has been made to manage the switch with an invalid login or password. Also, it might indicate a network management station has not been configured with the correct SNMP authentication parameters for the switch. |
| port-auth-failures/min | The count of times a client has been unsuccessful logging into the network. |
| system-delay | The response time, in seconds, of the CPU to new network events such as BPDU packets or packets for other network protocols. Some DoS attacks can cause the CPU to take too long to respond to new network events, which can lead to a breakdown of Spanning Tree or other features. A delay of several seconds indicates a problem. |
| mac-address-count | The number of MAC addresses learned in the forwarding table. Some attacks fill the forwarding table so that new conversations are flooded to all parts of the network. |
| mac-moves/min | The average number of MAC address moves from one port to another per minute. This usually indicates a network loop, but can also be caused by DoS attacks. |
| learn-discards/min | Number of MAC address learn events per minute discarded to help free CPU resources when busy. |
-
To generate alerts for monitored events, you must enable the instrumentation monitoring log and SNMP trap. The threshold for each monitored parameter can be adjusted to minimize false alarms (see Configuring instrumentation monitor.
-
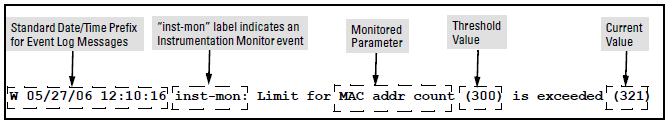
When a parameter exceeds its threshold, an alert (event log message and SNMP trap) is generated to inform network administrators of this condition. The following example shows an event log message that occurs when the number of MAC addresses learned in the forwarding table exceeds the configured threshold:
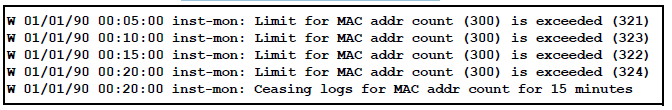
In the preceding example, if a condition is reported 4 times (persists for more than 15 minutes) then alerts cease for 15 minutes. If after 15 minutes the condition still exists, the alerts cease for 30 minutes, then for 1 hour, 2 hours, 4 hours, 8 hours, and after that the persisting condition is reported once a day. As with other event log entries, these alerts can be sent to a server.
-
Known Limitations: The instrumentation monitor runs once every five minutes. The current implementation does not track information such as the port, MAC, and IP address from which an attack is received.
Port security enables you to configure each switch port with a unique list of the MAC addresses of devices that are authorized to access the network through that port. This enables individual ports to detect, prevent, and log attempts by unauthorized devices to communicate through the switch.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Port security does not prevent intruders from receiving broadcast and multicast traffic. Also, Port Security and MAC Lockdown are mutually exclusive on a switch. If one is enabled, then the other cannot be. |
|
|
MAC Lockdown, also known as "Static Addressing", is used to prevent station movement and MAC address "hijacking", by allowing a given MAC address to use only an assigned port on the switch. MAC Lockdown also restricts the client device to a specific VLAN.
MAC Lockout enables blocking a specific MAC address so that the switch drops all traffic to or from the specified address.
The default port security setting for each port is off, or "continuous". That is, any device can access a port without causing a security reaction.
In a similar way to DHCP snooping, dynamic ARP protection allows you to configure VLAN interfaces in two categories: trusted and untrusted ports. ARP packets received on trusted ports are forwarded without validation.
By default, all ports on a switch are untrusted. If a VLAN interface is untrusted:
-
The switch intercepts all ARP requests and responses on the port.
-
Each intercepted packet is checked to see if its IP-to-MAC binding is valid. If a binding is invalid, the switch drops the packet.
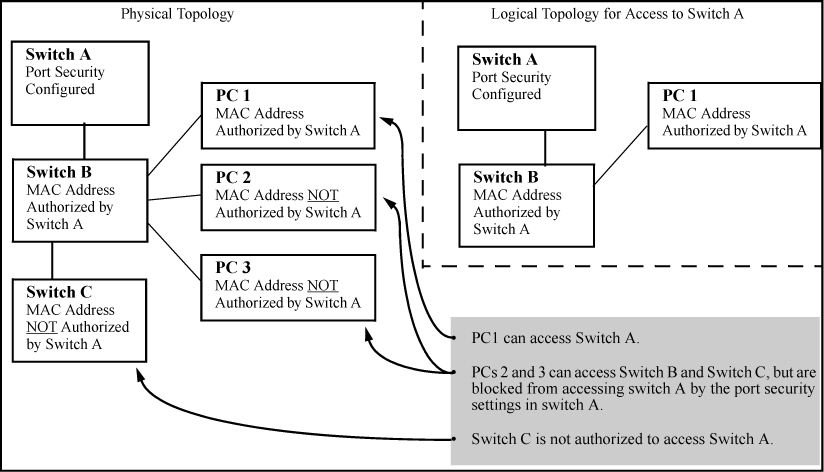
You must configure trusted ports carefully. For example, in the topology in the following figure, Switch B may not see the leased IP address that Host 1 receives from the DHCP server. If the port on Switch B that is connected to Switch A is untrusted and if Switch B has dynamic ARP protection enabled, it sees ARP packets from Host 1 as invalid, resulting in a loss of connectivity.
On the other hand, if Switch A does not support dynamic ARP protection and you configure the port on Switch B connected to Switch A as trusted, Switch B opens itself to possible ARP poisoning from hosts attached to Switch A.
Take into account the following configuration guidelines when you use dynamic ARP protection in your network:
-
You should configure ports connected to other switches in the network as trusted ports. In this way, all network switches can exchange ARP packets and update their ARP caches with valid information.
-
Switches that do not support dynamic ARP protection should be separated by a router in their own Layer 2 domain. Because ARP packets do not cross Layer 2 domains, the unprotected switches cannot unknowingly accept ARP packets from an attacker and forward them to protected switches through trusted ports.
A port that detects an "intruder" blocks the intruding device from transmitting to the network through that port.
Using either the port-security command or the switch WebAgent to enable port security on a given port automatically enables eavesdrop prevention on that port.
On a per-port basis, you can configure security measures to block unauthorized devices, and to send notice of security violations. Once port security is configured, you can then monitor the network for security violations through one or more of the following:
For any port, you can configure the following:
-
Action
Used when a port detects an intruder. Specifies whether to send an SNMP trap to a network management station and whether to disable the port.
-
Address Limit
Sets the number of authorized MAC addresses allowed on the port.
-
Learn-Mode
Specify how the port acquires authorized addresses.
-
Limited-Continuous: Sets a finite limit (1 - 32) to the number of learned addresses allowed per port.
-
Continuous: Allows the port to learn addresses from inbound traffic from any connected device. This is the default setting.
-
-
Static: Enables you to set a fixed limit on the number of MAC addresses authorized for the port and to specify some or all of the authorized addresses. (If you specify only some of the authorized addresses, the port learns the remaining authorized addresses from the traffic it receives from connected devices.)
-
Configured: Requires that you specify all MAC addresses authorized for the port. The port is not allowed to learn addresses from inbound traffic.
-
Specify up to eight devices (MAC addresses) that are allowed to send inbound traffic through the port. This feature:
-
Closes the port to inbound traffic from any unauthorized devices that are connected to the port.
-
Provides the option for sending an SNMP trap notifying of an attempted security violation to a network management station and, optionally, disables the port. (For more on configuring the switch for SNMP management, see "Trap Receivers and Authentication Traps" in the Management and Configuration Guide for your switch.)
-
-
Allows only the MAC address of a device authenticated through the switch 802.1X Port-Based access control.
Configuring port security on a given switch port automatically enables Eavesdrop Prevention for that port. This prevents use of the port to flood unicast packets addressed to MAC addresses unknown to the switch and blocks unauthorized users from eavesdropping on traffic intended for addresses that have aged-out of the switch address table. (Eavesdrop Prevention does not affect multicast and broadcast traffic; the switch floods these two traffic types out a given port regardless of whether port security is enabled on that port.)
Traffic with an unknown destination address is blocked when port security is configured and Eavesdrop Prevention is enabled. You can disable Eavesdrop Prevention on ports where it may cause problems, such as on ports that are configured to use limited-continuous learning mode. See Configuring port security for more information on learning modes.
The following table explains the various interactions between learning modes and Eavesdrop Prevention when Eavesdrop Prevention is disabled.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: When the learning mode is "port-access", Eavesdrop Prevention is not applied to the port. However, it can still be configured or disabled for the port. |
|
|
Learn — Effect
Unless you configure the switch to disable a port on which a security violation is detected, the switch security measures block unauthorized traffic without disabling the port. This implementation enables you to apply the security configuration to ports on which hubs, switches, or other devices are connected, and to maintain security while also maintaining network access to authorized users.
Example
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Broadcast and Multicast traffic is always allowed, and can be read by intruders connected to a port on which you have configured port security. |
|
|
Port security does not operate on either a static or dynamic trunk group. If you configure port security on one or more ports that are later added to a trunk group, the switch resets the port security parameters for those ports to the factory-default configuration. Ports configured for either Active or Passive LACP, and which are not members of a trunk, can be configured for port security.
Static MAC addresses do not age-out. MAC addresses learned by using learn-mode continuous or learn-mode limited-continuous age out according to the currently configured MAC age time. For information on the mac-age-time command, see "Interface Access and System Information" in the Management and Configuration Guide for your switch.
In the following two cases, a port in Static learn mode retains a learned MAC address even if you later reboot the switch or disable port security for that port:
-
The port learns a MAC address after you configure the port for Static learn mode in both the startup-config file and the running-config file (by executing the
write memorycommand). -
The port learns a MAC address after you configure the port for Static learn mode in only the running-config file and, after the address is learned, you execute
write memoryto configure the startup-config file to match the running-config file.
To remove an address learned using either of the preceding methods, do one of the following:
-
Delete the address by using no port-security <port-number> mac-address <mac-addr>.
-
Download a configuration file that does not include the unwanted MAC address assignment.
-
Reset the switch to its factory-default configuration.
If you manually assign a MAC address (using port-security <port-number>address-list <mac-addr>) and then execute write memory, the assigned MAC address remains in memory until you do one of the following:
-
Delete it by using no port-security <port-number> mac-address <mac-addr>
-
Download a configuration file that does not include the unwanted MAC address assignment.
-
Reset the switch to its factory-default configuration.
This example configures port A1 to automatically accept the first device (MAC address) it detects as the only authorized device for that port. (The default device limit is 1.) It also configures the port to send an alarm to a network management station and disable itself if an intruder is detected on the port.
HP Switch(config)# port-security a1 learn-mode static action send-disable
The next example does the same as the preceding example, except that it specifies a MAC address of 0c0090-123456 as the authorized device instead of allowing the port to automatically assign the first device it detects as an authorized device.
HP Switch(config)# port-security a1 learn-mode static mac-address 0c0090-123456 action send-disable
This example configures port A5 to:
-
Allow two MAC addresses, 00c100-7fec00 and 0060b0-889e00, as the authorized devices.
-
Send an alarm to a management station if an intruder is detected on the port, but allow the intruder access to the network.
HP Switch(config)# port-security a5 learn-mode static address-limit 2 mac-address 00c100-7fec00 0060b0-889e00 action send-alarm
If you manually configure authorized devices (MAC addresses) and an alarm action on a port, those settings remain unless you either manually change them or the switch is reset to its factory-default configuration. You can “turn off” authorized devices on a port by configuring the port to continuous Learn Mode, but subsequently reconfiguring the port to static Learn Mode restores those authorized devices.
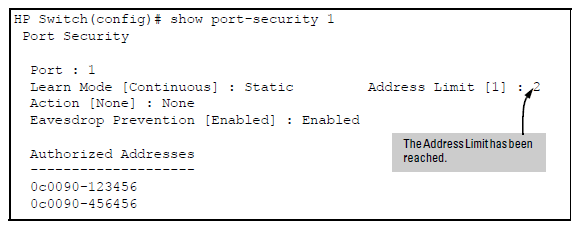
To simply add a device (MAC address) to a port’s existing Authorized Addresses list, enter the port number with the mac-address parameter and the device’s MAC address. This assumes that Learn Mode is set to static and the Authorized Addresses list is not full (as determined by the current Address Limit value). For example, suppose port A1 allows two authorized devices, but has only one device in its Authorized Address list:
With the above configuration for port A1, the following command adds the 0c0090-456456 MAC address as the second authorized address.
HP Switch(config)# port-security a1 mac-address 0c0090- 456456
After executing the above command, the security configuration for port A1 would be:
(The message Inconsistent value appears if the new MAC address exceeds the current Address Limit or specifies a device that is already on the list. Note that if you change a port from static to continuous learn mode, the port retains in memory any authorized addresses it had while in static mode. If you subsequently attempt to convert the port back to static mode with the same authorized addresses, the Inconsistent value message appears because the port already has the addresses in its “Authorized” list.) If you are adding a device (MAC address) to a port on which the Authorized Addresses list is already full (as controlled by the port’s current Address Limit setting), then you must increase the Address Limit in order to add the device, even if you want to replace one device with another. Using the CLI, you can simultaneously increase the limit and add the MAC address with a single command. For example, suppose port A1 allows one authorized device and already has a device listed:
To add a second authorized device to port A1, execute a port-security command for port A1 that raises the address limit to 2 and specifies the additional device’s MAC address. For example:
HP Switch(config)# port-security a1 mac-address 0c0090- 456456 address-limit 2
This command option removes unwanted devices (MAC addresses) from the Authorized Addresses list. (An Authorized Address list is available for each port for which Learn Mode is currently set to “Static”. See the command syntax listing under Configuring port security.
|
|
|
![[CAUTION: ]](images/caution.gif) |
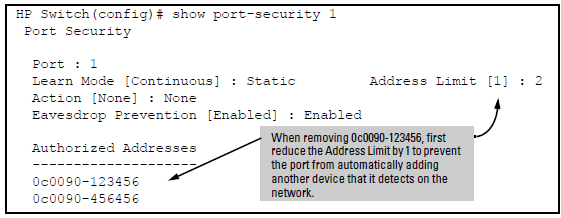
CAUTION: When learn mode is set to static, the Address Limit (address-limit) parameter controls how many devices are allowed in the Authorized Addresses (macaddress) for a given port. If you remove a MAC address from the Authorized Addresses list without also reducing the Address Limit by 1, the port may subsequently detect and accept as authorized a MAC address that you do not intend to include in your Authorized Address list. Thus, if you use the CLI to remove a device that is no longer authorized, it is recommended that you first reduce the Address Limit (address-limit) integer by 1, as shown below. This prevents the possibility of the same device or another unauthorized device on the network from automatically being accepted as “authorized” for that port. |
|
|
To remove a device (MAC address) from the “Authorized” list and when the current number of devices equals the Address Limit value, you should first reduce the Address Limit value by 1, then remove the unwanted device.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: You can reduce the address limit below the number of currently authorized addresses on a port. This enables you to subsequently remove a device from the “Authorized” list without opening the possibility for an unwanted device to automatically become authorized. |
|
|
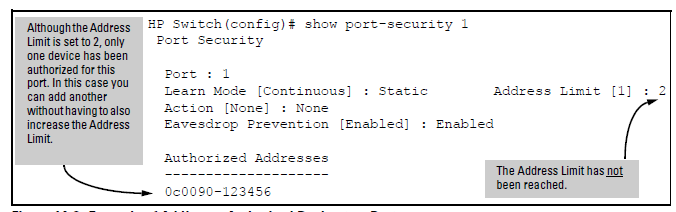
For example, suppose port A1 is configured as shown below and you want to remove 0c0090-123456 from the Authorized Address list:
The following command serves this purpose by removing 0c0090-123456 and reducing the Address Limit to 1:
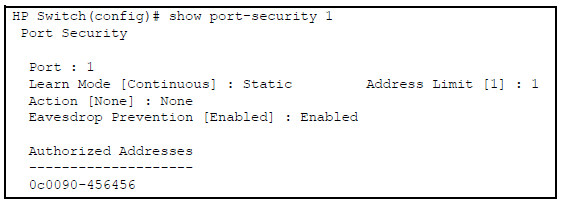
HP Switch(config)# port-security a1 address-limit 1 HP Switch(config)# no port-security a1 mac-address 0c0090-123456
The above command sequence results in the following configuration for port A1:
When a device's MAC address is locked to a port (typically in a pair with a VLAN) all information sent to that MAC address must go through the locked-down port. If the device is moved to another port it cannot receive data. Traffic to the designated MAC address goes only to the allowed port, whether the device is connected to it or not.
MAC Lockdown is useful for preventing an intruder from "hijacking" a MAC address from a known user in order to steal data. Without MAC Lockdown, this causes the switch to learn the address on the malicious user's port, allowing the intruder to steal the traffic meant for the legitimate user.
MAC Lockdown ensures that traffic intended for a specific MAC address can only go through the one port which is supposed to be connected to that MAC address. It does not prevent intruders from transmitting packets with the locked MAC address, but it does prevent responses to those packets from going anywhere other than to the locked-down port. Thus TCP connections cannot be established. Traffic sent to the locked address cannot be hijacked and directed out the port of the intruder.
If the device (computer, PDA, wireless device) is moved to a different port on the switch (by reconnecting the Ethernet cable or by moving the device to an area using a wireless access point connected to a different port on that same switch), the port detects that the MAC Address is not on the appropriate port and continues to send traffic out the port to which the address was locked.
Once a MAC address is configured for one port, you cannot perform port security using the same MAC address on any other port on that same switch.
You cannot lock down a single MAC Address/VLAN pair to more than one port; however you can lock down multiple different MAC Addresses to a single port on the same switch.
Stations can move from the port to which their MAC address is locked to other parts of the network. They can send but not receive data, if that data must go through the locked-down switch.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If the device moves to a distant part of the network where data sent to its MAC address never goes through the locked-down switch, it may be possible for the device to have full two-way communication. For full and complete lockdown network-wide, all switches must be configured appropriately.
|
|
|
There is a limit of 500 MAC Lockdowns that you can safely code per switch. To truly lock down a MAC address it would be necessary to use the MAC Lockdown command for every MAC Address and VLAN ID on every switch. In reality, few network administrators go to this length, but just because you have locked the MAC address and VID for a single switch, the device (or a hacker spoofing the device MAC address) may still be able to use another switch that is not locked.
If someone using a locked MAC address is attempting to communicate using the wrong port the "move attempt" generates messages in the log file such as:
Move attempt
Move attempt (lockdown) logging:
W 10/30/03 21:33:43 maclock: module A: Move 0001e6-1f96c0 to A15 denied
W 10/30/03 21:33:48 maclock: module A: Move 0001e6-1f96c0 to A15 denied
W 10/30/03 21:33:48 maclock: module A: Ceasing move-denied logs for 5m
These messages can be useful for troubleshooting. If you are trying to connect a device that is locked to the wrong port, the device does not work but generates similar error messages.
The purpose of rate-limiting the log messaging is to prevent the log file from becoming too full. When a move attempt (or intrusion) is logged and a message sent to the log file, message throttling is imposed on the logging of subsequent move attempts. The logging system checks move attempts to incorrect ports 5 minutes after the initial attack. If there has been a second attack within the 5 minute interval, the log file registers the most recent attempt and then checks every hour for new attempts If, after an hour, no other attempts have been made, the log resets itself and reverts to checking one time per day.
The switch can also be configured to copy the log messages to a chosen syslog server. See the Management and Configuration Guide for your switch.
Because port-security relies upon MAC addresses, it is often confused with the MAC Lockdown feature. However, MAC Lockdown is a completely different feature and is implemented on a different architecture level.
Port security maintains a list of allowed MAC addresses on a per-port basis. An address can exist on multiple ports of a switch. Port security deals with MAC addresses only while MAC Lockdown specifies both a MAC address and a VLAN for lockdown.
MAC Lockdown, on the other hand, is not a "list." It is a global parameter on the switch that takes precedence over any other security mechanism. The MAC Address is only allowed to communicate using one specific port on the switch.
MAC Lockdown is a good replacement for port security to create tighter control over MAC addresses and which ports they are allowed to use (only one port per MAC Address on the same switch in the case of MAC Lockdown). (You can still use the port for other MAC addresses, but you cannot use the locked MAC address on other ports.)
Using only port security the MAC Address could still be used on another port on the same switch. MAC Lockdown, on the other hand, is a clear one-to-one relationship between the MAC Address and the port. Once a MAC address has been locked to a port it cannot be used on another port on the same switch.
The switch does not allow MAC Lockdown and port security on the same port.
When you deploy MAC Lockdown you need to consider how you use it within your network topology to ensure security. In some cases where you are using techniques such as "meshing" or Spanning Tree Protocol (STP) to speed up network performance by providing multiple paths for devices, using MAC Lockdown either does not work or else it defeats the purpose of having multiple data paths.
The purpose of using MAC Lockdown is to prevent a malicious user from "hijacking" an approved MAC address so they can steal data traffic being sent to that address.
As we have seen, MAC Lockdown can help prevent this type of hijacking by making sure that all traffic to a specific MAC address goes only to the proper port on a switch which is supposed to be connected to the real device bearing that MAC address.
However, you can run into trouble if you incorrectly try to deploy MAC Lockdown in a network that uses multiple path technology, like Spanning Tree or "mesh networks."
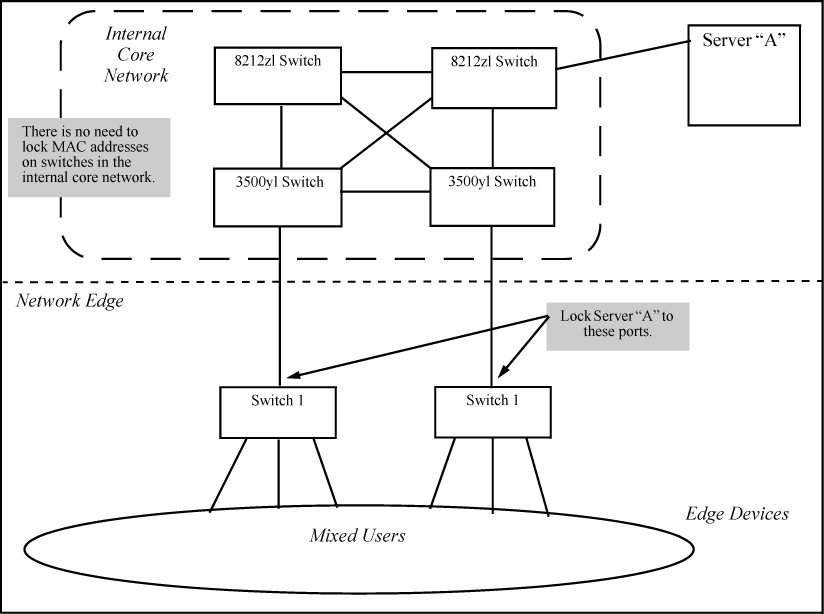
Let's examine a good use of MAC Lockdown within a network to ensure security first.
Example
In the Model Network Topology shown above, the switches that are connected to the edge of the network each have one and only one connection to the core network. This means each switch has only one path by which data can travel to Server A. You can use MAC Lockdown to specify that all traffic intended for Server A's MAC Address must go through the one port on the edge switches. That way, users on the edge can still use other network resources, but they cannot "spoof" Server A and hijack data traffic which is intended for that server alone.
The key points for this Model Topology are:
-
The Core Network is separated from the edge by the use of switches which have been locked for security.
-
All switches connected to the edge (outside users) each have only one port they can use to connect to the Core Network and then to Server A.
-
Each switch has been configured with MAC Lockdown so that the MAC Address for Server A has been locked to one port per switch that can connect to the Core and Server A.
Using this setup, Server A can be moved around within the core network, and yet MAC Lockdown still prevents a user at the edge from hijacking its address and stealing data.
Please note that in this scenario a user with bad intentions at the edge can still "spoof" the address for Server A and send out data packets that look as though they came from Server A. The good news is that because MAC Lockdown has been used on the switches on the edge, any traffic that is sent back to Server A is be sent to the proper MAC Address because MAC Lockdown has been used. The switches at the edge do not send Server A's data packets anywhere but the port connected to Server A. (Data would not be allowed to go beyond the edge switches.)
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Using MAC Lockdown still does not protect against a hijacker within the core! In order to protect against someone spoofing the MAC Address for Server A inside the Core Network, you would have to lock down each and every switch inside the Core Network as well, not just on the edge. |
|
|
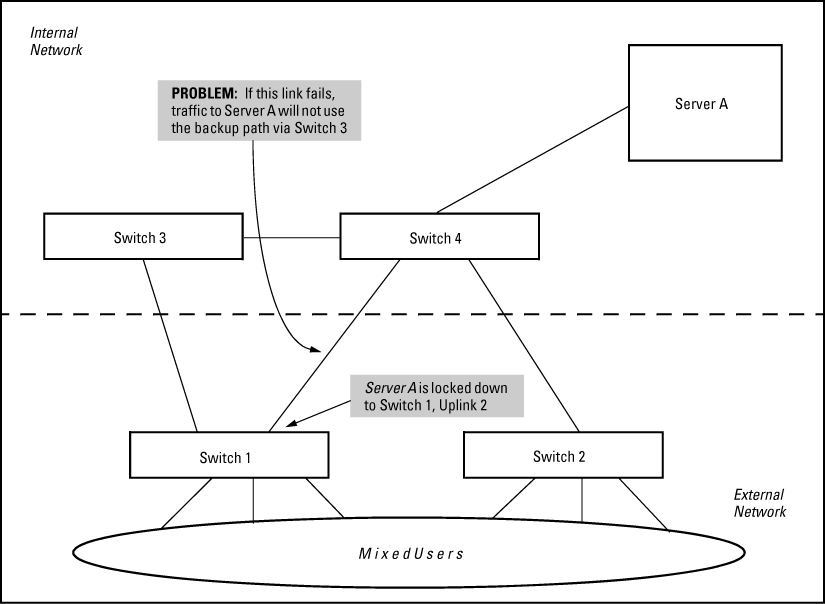
Now let's take a look at a network topology in which the use of MAC Lockdown presents a problem. In the following figure, Switch 1 (on the bottom-left) is located at the edge of the network where there is a mixed audience that might contain hackers or other malicious users. Switch 1 has two paths it could use to connect to Server A. If you try to use MAC Lockdown here to make sure that all data to Server A is locked to one path, connectivity problems would be the result since both paths need to be usable in case one of them fails.
The resultant connectivity issues would prevent you from locking down Server A to Switch 1. And when you remove the MAC Lockdown from Switch 1 (to prevent broadcast storms or other connectivity issues), you then open the network to security problems. The use of MAC Lockdown as shown in the above figure would defeat the purpose of using MSTP or having an alternate path.
Technologies such as MSTP or "meshing" are primarily intended for an internal campus network environment in which all users are trusted. MSTP and "meshing" do not work well with MAC Lockdown.
If you deploy MAC Lockdown as shown in the Model Topology in MAC lockdown deployed at the network edge provides security, you should have no problems with either security or connectivity.
Let's say a customer knows there are unauthorized wireless clients who should not have access to the network. The network administrator "locks out" the MAC addresses for the wireless clients by using the MAC Lockout command (lockout-mac ). When the wireless clients then attempt to use the network, the switch recognizes the intruding MAC addresses and prevents them from sending or receiving data on that network.mac-address
If a particular MAC address can be identified as unwanted on the switch then that MAC Address can be disallowed on all ports on that switch with a single command. You don't have to configure every single port—just perform the command on the switch and it is effective for all ports.
MAC Lockout overrides MAC Lockdown, port security, and 802.1X authentication.
You cannot use MAC Lockout to lock:
-
Broadcast or Multicast Addresses (Switches do not learn these)
-
Switch Agents (The switch own MAC Address)
A MAC address can exist on many different VLANs, so a lockout MAC address must be added to the MAC table as a drop. As this can quickly fill the MAC table, restrictions are placed on the number of lockout MAC addresses based on the number of VLANs configured.
| VLANs configured | Number of MAC lockout addresses | Total number of MAC addresses |
|---|---|---|
| 1-8 | 200 | 1,600 |
| 9-16 | 100 | 1,600 |
| 17-256 | 64 | 16,384 |
| 257-1024 | 16 | 16,384 |
| 1025-2048 | 8 | 16,384 |
There are l imits for the number of VLANs, Multicast Filters, and Lockout MACs that can be configured concurrently as all use MAC table entries. The limits are shown below.
If someone using a locked out MAC address tries to send data through the switch a message is generated in the log file:
Lockout logging format:
W 10/30/03 21:35:15 maclock: module A: 0001e6-1f96c0 detected on port A15
W 10/30/03 21:35:18 maclock: module A: 0001e6-1f96c0 detected on port A15
W 10/30/03 21:35:18 maclock: module A: Ceasing lock-out logs for 5m
As with MAC Lockdown a rate limiting algorithm is used on the log file so that it does not become overclogged with error messages. See Limiting the frequency of log messages.
MAC Lockout is independent of port-security and in fact overrides it. MAC Lockout is preferable to port-security to stop access from known devices because it can be configured for all ports on the switch with one command.
It is possible to use MAC Lockout in conjunction with port-security. You can use MAC Lockout to lock out a single address—deny access to a specific device—but still allow the switch some flexibility in learning other MAC Addresses. Be careful if you use both together, however:
-
If a MAC Address is locked out and appears in a static learn table in port-security, the apparently "authorized" address is still locked out anyway.
-
MAC entry configurations set by port security are kept even if MAC Lockout is configured and the original port security settings are honored once the Lockout is removed.
-
A port security static address is permitted to be a lockout address. In that case (MAC Lockout), the address is locked out (SA/DA drop) even though it's an "authorized" address from the perspective of port security.
-
When MAC Lockout entries are deleted, port security then re-learns the address as needed later on.
When the switch detects an intrusion on a port, it sets an "alert flag" for that port and makes the intrusion information available as described below. While the switch can detect additional intrusions for the same port, it does not list the next chronological intrusion for that port in the Intrusion Log until the alert flag for that port has been reset.
When a security violation occurs on a port configured for Port Security, the switch responds in the following ways to notify you:
-
The switch sets an alert flag for that port. This flag remains set until:
-
You use either the CLI, menu interface, or WebAgent to reset the flag.
-
The switch is reset to its factory default configuration.
-
-
The switch enables notification of the intrusion through the following means:
-
In the CLI:
-
The
show port-security intrusion-logcommand displays the Intrusion Log -
The
logcommand displays the Event Log
-
-
In the menu interface:
-
The Port Status screen includes a per-port intrusion alert
-
The Event Log includes per-port entries for security violations
-
-
In the WebAgent:
-
The Alert Log includes entries for per-port security violations
-
The Intrusion Log lists per-port security violation entries
-
-
In network management applications such as HP PCM+ via an SNMP trap sent to a network management station
-
When the switch detects an intrusion attempt on a port, it enters a record of this event in the Intrusion Log. No further intrusion attempts on that port appear in the Log until you acknowledge the earlier intrusion event by resetting the alert flag.
The Intrusion Log lists the 20 most recently detected security violation attempts, regardless of whether the alert flags for these attempts have been reset. This gives you a history of past intrusion attempts. Thus, for example, if there is an intrusion alert for port A1 and the Intrusion Log shows two or more entries for port 1, only the most recent entry has not been acknowledged (by resetting the alert flag). The other entries give you a history of past intrusions detected on port A1.
The log shows the most recent intrusion at the top of the listing. You cannot delete Intrusion Log entries (unless you reset the switch to its factory-default configuration). Instead, if the log is filled when the switch detects a new intrusion, the oldest entry is dropped off the listing and the newest entry appears at the top of the listing.
When a violation occurs on a port, an alert flag is set for that port and the violation is entered in the Intrusion Log. The switch can detect and handle subsequent intrusions on that port, but does not log another intrusion on the port until you reset the alert flag for either all ports or for the individual port.
The Intrusion Log lists detected intruders by MAC address. If you are using HP PCM+ to manage your network, you can use the device properties page to link MAC addresses to their corresponding IP addresses.
If you are using the WebAgent through a switch port configured for Static port security, and your browser access is through a proxy web server, then it is necessary to do the following:
-
Enter your PC or workstation MAC address in the port's Authorized Addresses list.
-
Enter your PC or workstation's IP address in the switch IP Authorized Managers list. See "Using Authorized IP Managers" in the Management and Configuration Guide for your switch.
Without both of the above configured, the switch detects only the proxy server's MAC address, and not your PC or workstation MAC address, and interprets your connection as unauthorized.
If you reset the switch (using the Reset button, Device Reset, or Reboot Switch), the Intrusion Log lists the time of all currently logged intrusions as "prior to" the time of the reset.
If the Intrusion Log is full of entries for which the alert flags have not been reset, a new intrusion will cause the oldest entry to drop off the list, but will not change the alert flag status for the port referenced in the dropped entry. This means that, even if an entry is forced off of the Intrusion Log, no new intrusions can be logged on the port referenced in that entry until you reset the alert flags.
To maintain security, LACP is not allowed on ports configured for port security. If you configure port security on a port on which either active or passive LACP is configured, the switch removes the LACP configuration, displays a notice that LACP is disabled on the ports, and enables port security. For example:
HP Switch(config)# port-security e a17 learn-mode static address-limit 2
LACP has been disabled on secured port(s).
HP Switch(config)#
The switch does not allow you to configure LACP when port security is enabled. For example:
HP Switch(config)# int e a17 lacp passive
Error configuring port A17: LACP and port security cannot be run together.
HP Switch(config)#
To restore LACP to the port, you must remove port security and re-enable LACP active or passive.