Plan your port security configuration and monitoring according to the following:
-
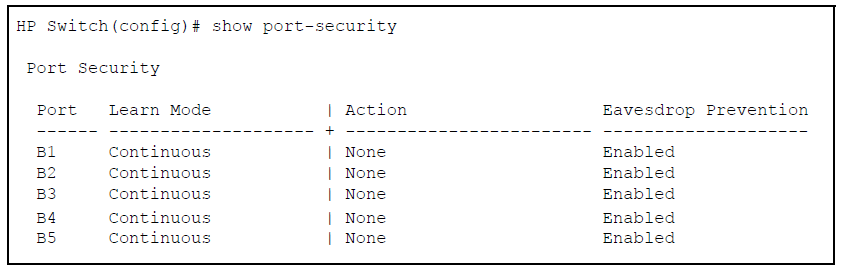
For each port, what security actions do you want? (The switch automatically blocks intruders detected on that port from transmitting to the network.) You can configure the switch to (1) send intrusion alarms to an SNMP management station and to (2) optionally disable the port on which the intrusion was detected.
-
How do you want to learn of the security violation attempts the switch detects? You can use one or more of these methods:
-
Through network management (That is, do you want an SNMP trap sent to a net management station when a port detects a security violation attempt?)
-
Through the switch Intrusion Log, available through the CLI, menu, and WebAgent
-
Through the Event Log (in the menu interface or through the CLI show log command)
-
Use the CLI or WebAgent to configure port security operating and address controls.
Use the global configuration level to execute port-security configuration commands.
-
Configure port security and edit security settings.
-
Add or delete devices from the list of authorized addresses for one or more ports.
-
Clear the Intrusion flag on specific ports.
Syntax
Identifies the method for acquiring authorized addresses.
On switches covered in this guide, automatically invokes eavesdrop protection, see Eavesdrop prevention.
(Default): Appears in the factory-default setting or when you execute no port-security. Allows the port to learn addresses from the devices to which it is connected. In this state, the port accepts traffic from any devices to which it is connected. Addresses learned in the learn continuous mode "age out" and be automatically deleted if they are not used regularly. The default age time is five minutes.
Addresses learned this way appear in the switch and port address tables and age out according to the
MAC Age Intervalin the System Information configuration screen of the Menu interface or theshow system informationlisting. You can set the MAC age out time using the CLI, SNMP, Web, or menu interfaces. For more information on themac-age-timecommand see "Interface Access and System Information" in the Management and Configuration Guide for your switch.Enables you to use the
mac-addressparameter to specify the MAC addresses of the devices authorized for a port, and theaddress-limitparameter (explained below) to specify the number of MAC addresses authorized for the port. You can authorize specific devices for the port, while still allowing the port to accept other, non-specified devices until the device limit has been reached. That is, if you enter fewer MAC addresses than you authorized, the port authorizes the remaining addresses in the order in which it automatically learns them.
For example, if you use address-limit to specify three authorized devices, but use mac-address to specify only one authorized MAC address, the port adds the one specifically authorized MAC address to its authorized-devices list and the first two additional MAC addresses it detects.
You use mac-address to authorize MAC address 0060b0-880a80 for port A4.
You use address-limit to allow three devices on port A4 and the port detects these MAC addresses:
In this example port A4 would assume the following list of authorized addresses:
00f031-423fc1 (the second address the port detected)
0060b0-880a80 (the address you authorized with the mac-address parameter)
The remaining MAC address detected by the port, 080071-0c45a1, is not allowed and is handled as an intruder. Learned addresses that become authorized do not age-out. See also Retention of static addresses.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Using the static parameter with a device limit greater than the number of MAC addresses specified with mac-address can allow an unwanted device to become "authorized". This is because the port, to fulfill the number of devices allowed by the address-limit parameter (se below), automatically adds devices it detects until it reaches the specified limit. |
|
|
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If 802.1X port-access is configured on a given port, then port-security learn-mode must be set to either continuous (the default) or port-access. |
|
|
Syntax
Enables you to use Port Security with (802.1X) Port-Based Access Control.
Specifies which MAC addresses are allowed for this port. Range is 1 (default) to 64 and addresses do not age. Addresses are saved across reboots.
Also known as MAC Secure, or "limited" mode. The limited parameter sets a finite limit to the number of learned addresses allowed per port. (You can set the range from 1, the default, to a maximum of 32 MAC addresses which may be learned by each port.)
All addresses age, meaning they are automatically removed from the authorized address list for that port after a certain amount of time. Limited mode and the address limit are saved across reboots, but addresses which had been learned are lost during the reboot process.
Addresses learned in the limited mode are normal addresses learned from the network until the limit is reached, but they are not configurable. (You cannot enter or remove these addresses manually if you are using learn-mode with the limited-continuous option.)
Addresses learned this way appear in the switch and port address tables and age out according to the MAC Age Interval in the System Information configuration screen of the Menu interface or the show system information listing. You can set the MAC age out time using the CLI, SNMP, Web, or menu interfaces. For more on the mac-age-time command, see "Interface Access and System Information" in the Management and Configuration Guide for your switch. To set the learn-mode to limited use this command syntax:
port-security <port-list> learn-mode limited addresslimit <1..32> action<none|send-alarm|send-disable>The default address-limit is
1but may be set for each port to learn up to 64 addresses.To see the list of learned addresses for a port use the command:
When
learn-modeis set tostatic,configured, orlimited-continuous, theaddress-limitparameter specifies how many authorized devices (MAC addresses) to allow. Range: 1 (the default) to 8 for static and configured modes. Forlearn-modewith thelimited-continuousoption, the range is 1-32 addresses.Available for
learn-modewith the,static,configured, orlimited-continuousoption. Allows up to eight authorized devices (MAC addresses) per port, depending on the value specified in theaddress-limitparameter. Themac-address limited-continuousmode allows up to 32 authorized MAC addresses per port.If you use mac-address with static, but enter fewer devices than you specified in the address-limit field, the port accepts not only your specified devices, but also as many other devices as it takes to reach the device limit. For example, if you specify four devices, but enter only two MAC addresses, the port accepts the first two non-specified devices it detects, along with the two specifically authorized devices. Learned addresses that become authorized do not age-out. See also Retention of static addresses.
Specifies whether an SNMP trap is sent to a network management station when Learn Mode is set to static and the port detects an unauthorized device, or when Learn Mode is set to continuous and there is an address change on a port.
Prevents an SNMP trap from being sent.
noneis the default value.Sends an intrusion alarm. Causes the switch to send an SNMP trap to a network management station.
Sends alarm and disables the port. Available only in the
static,port-access,configured, orlimited learnmodes. Causes the switch to send an SNMP trap to a network management station and disable the port. If you subsequently re-enable the port without clearing the port's intrusion flag, the port blocks further intruders, but the switch does not disable the port again until you reset the intrusion flag. See the Note on Keeping the intrusion log current by resetting alert flags.For information on configuring the switch for SNMP management, see the Management and Configuration Guide for your switch.
Clears the intrusion flag for a specific port, see Reading intrusion alerts and resetting alert flags.
Syntax
Unless you configure the switch to disable a port on which a security violation is detected, the switch security measures block unauthorized traffic without disabling the port. This implementation enables you to apply the security configuration to ports on which hubs, switches, or other devices are connected, and to maintain security while also maintaining network access to authorized users. For example:
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Broadcast and Multicast traffic is always allowed, and can be read by intruders connected to a port on which you have configured port security. |
|
|
Port security does not operate on either a static or dynamic trunk group. If you configure port security on one or more ports that are later added to a trunk group, the switch resets the port security parameters for those ports to the factory-default configuration. (Ports configured for either Active or Passive LACP, and which are not members of a trunk, can be configured for port security.)
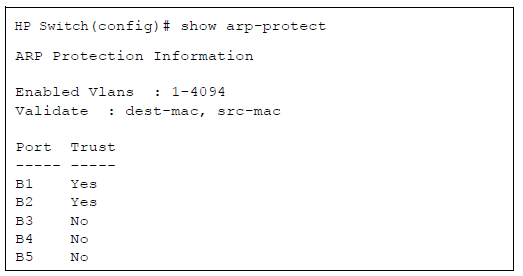
To configure one or more Ethernet interfaces that handle VLAN traffic as trusted ports, enter the arp-protect trust command at the global configuration level. The switch does not check ARP requests and responses received on a trusted port.
Syntax
Dynamic ARP protection can be configured to perform additional validation checks on ARP packets. By default, no additional checks are performed. To configure additional validation checks, enter the arp-protect validate command at the global configuration level.
Syntax
You can configure one or more of the validation checks. The following example of the arp-protect validate command shows how to configure the validation checks for source MAC address and destination AMC address:
HP Switch(config)# arp-protect validate src-mac dest-mac
To display the current configuration of dynamic ARP protection, including the additional validation checks and the trusted ports that are configured, enter the show arp-protect command:
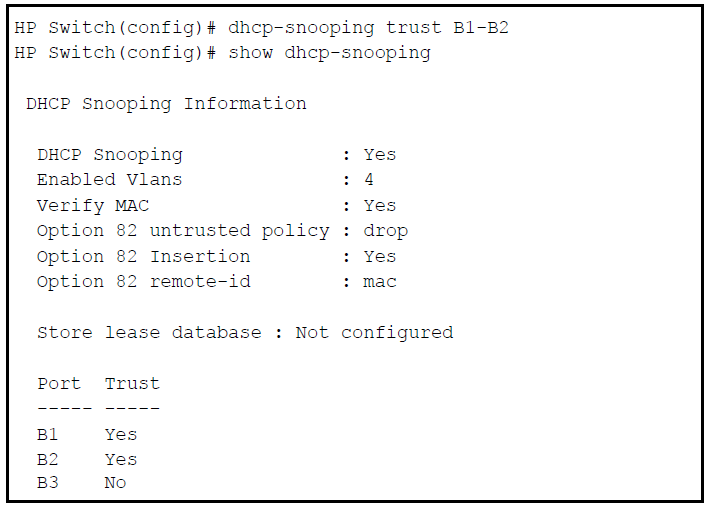
HP Networking switches support DHCPv4 and DHCPv6 snooping. Configuring both versions helps protect your entire network by blocking unintended or rogue DHCPv4 and DHCPv6 servers. By default, all ports are untrusted. Once configured, DHCP server packets are forwarded only if received on a trusted port. DHCP server packets received on an untrusted port are dropped.
To configure a port or range of ports as trusted, enter this command:
HP Switch(config)# dhcp-snooping trust <port-list>
You can also use this command in the interface context, in which case you are not able to enter a list of ports.
Use the no form of the command to remove the trusted configuration from a port.
To configure a port or range of ports as trusted, enter this command:
HP Switch(config)# dhcpv6-snooping trust <port-list>
You can also use this command in the interface context, in which case you are not able to enter a list of ports.
Use the no form of the command to remove the trusted configuration from a port.
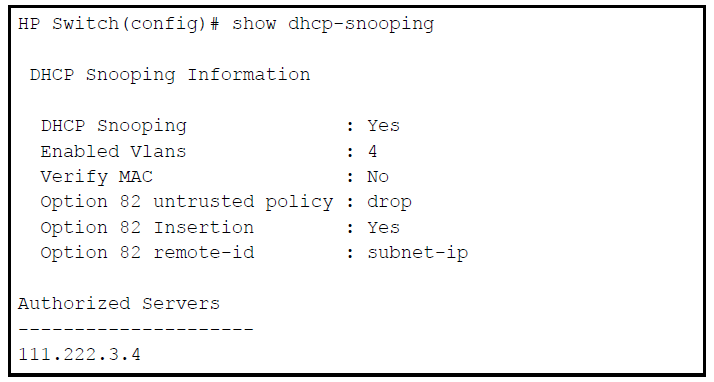
If authorized server addresses are configured, a packet from a DHCP server must be received on a trusted port AND have a source address in the authorized server list in order to be considered valid. If no authorized servers are configured, all servers are considered valid. You can configure a maximum of 20 authorized servers.
To configure a DHCP authorized server address, enter this command in the global configuration context:
HP Switch(config)# dhcp-snooping authorized-server <ip-address>
Syntax
Locks down a given MAC address and VLAN to a specific port.
A separate command is necessary for each MAC/VLAN pair you wish to lock down. If not specifying a VID, the switch inserts "1".
NOTE: A port configured with MAC Lockdown does not accept Multicast MAC addresses; such a port does accept unicast MAC addresses.
MAC Lockdown, also known as "static addressing," is permanently assigned a given MAC address and VLAN to a specific port on the switch. Use MAC Lockdown to prevent station movement and MAC address hijacking and control address learning on the switch.
Locking down a MAC address on a port and a specific VLAN only restricts the MAC address on that VLAN. The client device with that MAC address can to access other VLANs on the same port or through other ports.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Port security and MAC Lockdown are mutually exclusive on a given port. |
|
|
Syntax
MAC Lockout involves configuring a MAC address on all ports and VLANs for a switch, so that any traffic to or from the "locked-out" MAC address is dropped: all data packets addressed to or from the given address are stopped by the switch. MAC Lockout is like a simple blacklist.
MAC Lockout is implemented on a per switch assignment. To use it you must know the MAC Address to block. To fully lock out a MAC address from the network it is necessary to use the MAC Lockout command on all switches.
The following commands and parameters are used to configure the operational thresholds that are monitored on the switch. By default, the instrumentation monitor is disabled.
Syntax
To enable instrumentation monitor using the default parameters and thresholds, enter the general instrumentation monitor command. To adjust specific settings, enter the name of the parameter that you wish to modify, and revise the threshold limits as needed.
Examples
To turn on monitoring and event log messaging with the default medium values:
HP Switch(config)# instrumentation monitor
To turn off monitoring of the system delay parameter:
HP Switch(config)# no instrumentation monitor systemdelay
To adjust the alert threshold for the MAC address count to the low value:
HP Switch(config)# instrumentation monitor mac-addresscount low
To adjust the alert threshold for the MAC address count to a specific value:
HP Switch(config)# instrumentation monitor mac-addresscount 767
To enable monitoring of learn discards with the default medium threshold value:
HP Switch(config)# instrumentation monitor learndiscards