-
Configure one to fifteen RADIUS servers to support the switch. See the documentation provided with the RADIUS server application.
-
Before configuring the switch, collect the following information:
-
Determine the access methods (console, Telnet, Port-Access (802.1X), WebAgent and/or SSH) for which you want RADIUS as the primary authentication method. Consider both operator (login) and manager (enable) levels, as well as which secondary authentication methods to use (local or none) if the RADIUS authentication fails or does not respond.
-
Determine the IP addresses of the RADIUS servers to support the switch. You can configure the switch for up to fifteen RADIUS servers. See the documentation provided with the RADIUS server application for more information.
-
If you need to replace the default UDP destination port (1812) the switch uses for authentication requests to a specific RADIUS server, select it before beginning the configuration process.
-
If you need to replace the default UDP destination port (1813) the switch uses for accounting requests to a specific Radius server, select it before beginning the configuration process.
-
Determine whether to use one global encryption key for all RADIUS servers or if unique keys are required for specific servers. With multiple RADIUS servers, if one key applies to two or more of these servers, then you can configure this key as the global encryption key. For any server whose key differs from the global key you are using, you must configure that key in the same command that you use to designate that server's IP address to the switch.
-
Determine an acceptable timeout period for the switch to wait for a server to respond to a request. HP recommends that you begin with the default (five seconds).
-
Determine how many times the switch can contact a RADIUS server before trying another RADIUS server or quitting. This depends on how many RADIUS servers you have configured the switch to access.
-
Determine whether you want to bypass a RADIUS server that fails to respond to requests for service. To shorten authentication time, you can set a bypass period in the range of 1 to 1440 minutes for non-responsive servers. This requires that you have multiple RADIUS servers accessible for service requests.
-
Optional: Determine whether the switch access level (manager or operator) for authenticated clients can be set by a Service Type value the RADIUS server includes in its authentication message to the switch, see Enabling manager access privilege (optional).
-
Configure RADIUS on servers used to support authentication on the switch.
-
Configure RADIUS authentication for controlling access through one or more of the following
-
Serial port
-
Telnet
-
SSH
-
Port-Access (802.1X)
-
WebAgent
-
RADIUS authentication on the switch must be enabled to override the default authentication operation which is to automatically assign an authenticated client to the operator privilege level. This applies the privilege level specified by the service type value received from the RADIUS server, see Configuring authentication for access methods RADIUS is to protect.
-
Configure the switch for accessing one or more RADIUS servers (one primary server and up to two backup servers):
-
Server IP address
-
(Optional) UDP destination port for authentication requests (default: 1812; recommended)
-
(Optional) UDP destination port for accounting requests (default: 1813; recommended)
-
(Optional) Encryption key for use during authentication sessions with a RADIUS server. This key overrides the global encryption key you can also configure on the switch, and must match the encryption key used on the specified RADIUS server. Default: null.
![[NOTE: ]](images/note.gif)
NOTE: Step 2 assumes you have already configured the RADIUS servers to support the switch. See your RADIUS server documentation for details.
-
-
Configure the global RADIUS parameters.
-
This key must match the encryption key used on the RADIUS servers the switch contacts for authentication and accounting services unless you configure one or more per-server keys.
-
The timeout period the switch waits for a RADIUS server to reply.
-
The number of retries when there is no server response to a RADIUS authentication request.
-
The period during which the switch does not send new authentication requests to a RADIUS server that has failed to respond to a previous request. This avoids a wait for a request to time out on a server that is unavailable. If you want to use this feature, select a dead-time period of 1 to 1440 minutes. (Default: 0disabled; range: 1 - 1440 minutes.) If your first-choice server was initially unavailable, but then becomes available before the dead-time expires, you can nullify the dead-time by resetting it to zero and then trying to log on again. As an alternative, you can reboot the switch, (thus resetting the dead-time counter to assume the server is available) and then try to log on again.
-
This is actually an aaa authentication command. It controls how many times per session a RADIUS client (and clients using other forms of access) can try to log in with the correct user name and password.
-
For RADIUS accounting features, see Accounting services.
Configure the switch for RADIUS authentication through the following access methods:
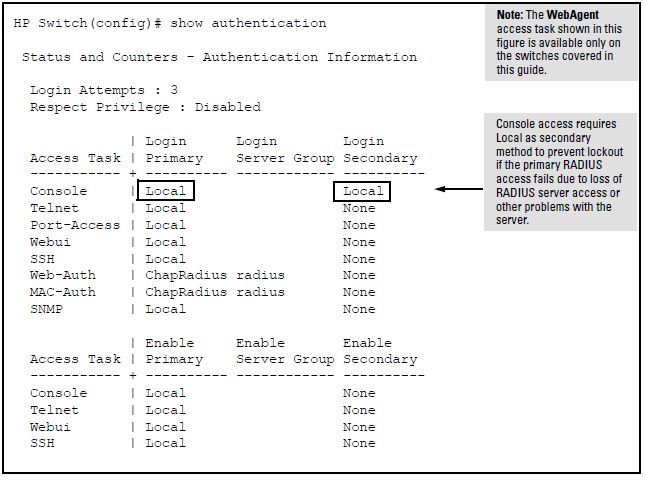
You can configure RADIUS as the primary password authentication method for the above access methods. You also need to select either local, none, or authorized as a secondary, or backup, method. Note that for console access, if you configure RADIUS (or tacacs) for primary authentication, you must configure local for the secondary method. This prevents the possibility of being completely locked out of the switch in the event that all primary access methods fail.
Syntax
aaa authentication<console|telnet|ssh|web|<enable|<login|radius>>
web-based|mac-based|<chap-radius|peap-radius>>Configures RADIUS as the primary password authentication method for console, Telnet, SSH, and/or the WebAgent.
The default primary
<enable|login>authentication is local.
<console|telnet|ssh|web>
Provides options for secondary authentication. For console access, secondary authentication must be local if primary access is not local. This prevents you from being locked out of the switch in the event of a failure in other access methods.
<<
web-based|mac-based> login><chap-radius|peapmschap v2>Password authentication for web-based or MAC-based port access to the switch. Use
peap-mschapv2when you want password verification without requiring access to a plain text password; it is more secure.
[
none|authorized]Provides options for secondary authentication. The
noneoption specifies that a backup authentication method is not used. Theauthorizedoption allows access without authentication.
You can configure RADIUS as the primary password authentication method for all access methods. Select either local, none or authorized as a secondary or backup method. For console access, if you configure RADIUS or TACACS for primary authentication, you must configure local for the secondary method. This prevents the possibility of being completely locked out of the switch in the event all primary access methods fail.
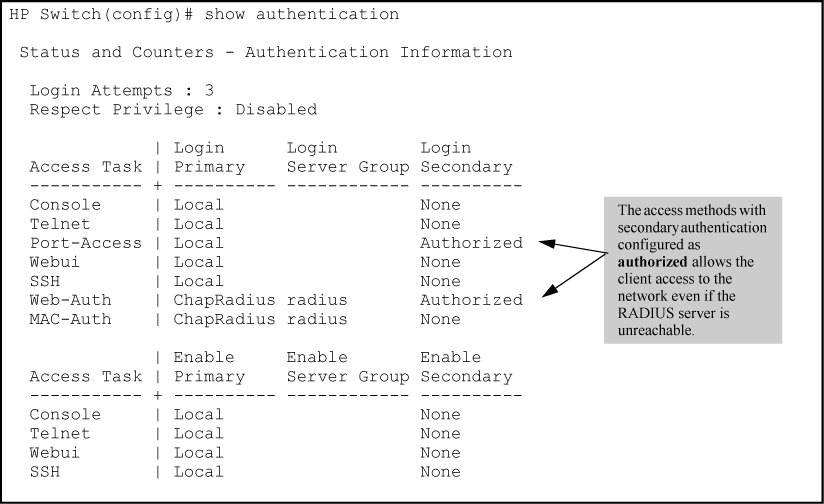
In certain situations, RADIUS servers can become isolated from the network. Users are not able to access the network resources configured with RADIUS access protection and are rejected. To address this situation, configuring the authorized secondary authentication method allows users unconditional access to the network when the primary authentication method fails because the RADIUS servers are unreachable.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Configuring |
|
|
Example of AAA authentication using Authorized for the secondary authentication method shows an example of the show authentication command displaying authorized as the secondary authentication method for port-access, web-based authentication access, and MAC authentication access. Since the configuration of authorized means no authentication is performed and the client has unconditional access to the network, the "Enable Primary" and "Enable Secondary" fields are not applicable (N/A).
Example
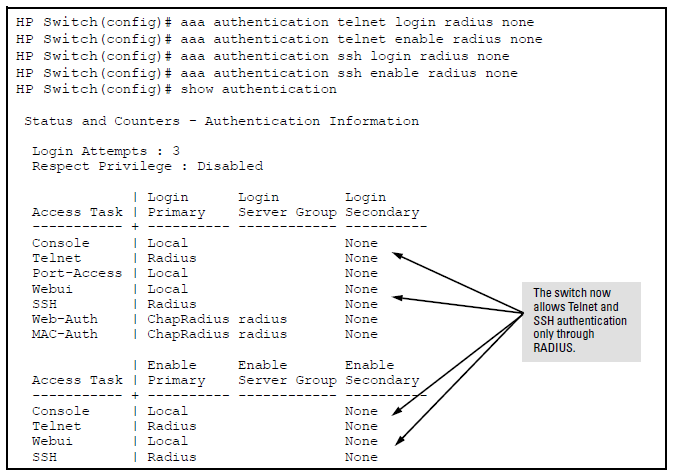
Suppose you already configured local passwords on the switch, but want RADIUS to protect primary Telnet and SSH access without allowing a secondary Telnet or SSH access option (the switch local passwords):
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If you configure the Login Primary method as |
|
|
In the default RADIUS operation, the switch automatically admits any authenticated client to the login (operator) privilege level, even if the RADIUS server specifies enable (manager) access for that client. Thus, an authenticated user authorized for the manager privilege level must authenticate again to change privilege levels. Using the optional login privilege-mode command overrides this default behavior for clients with enable access. That is, with privilege-mode enabled, the switch immediately allows enable (manager) access to a client for whom the RADIUS server specifies this access level.
Syntax
When enabled, the switch reads the Service-Type field in the client authentication received from a RADIUS server. The following table describes the applicableService-Type values and corresponding client access levels the switch allows upon authentication by the server.
This feature applies to console (serial port), Telnet, SSH, and WebAgent access to the switch. It does not apply to 802.1X port-access.
The
noform of the command returns the switch to the default RADIUS authentication operation. The default behavior for most interfaces is that a client authorized by the RADIUS server for Enable (manager) access is prompted twice, once for Login (operator) access and once for Enable access. In the default RADIUS authentication operation, the WebAgent requires only one successful authentication request. For more information on configuring the Service Type in your RADIUS application, see the documentation provided with the application.
This section describes how to configure the switch to interact with a RADIUS server for both authentication and accounting services.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If you want to configure RADIUS accounting on the switch, see Accounting services. |
|
|
Syntax
Adds a server to the RADIUS configuration or (with no) deletes a server from the configuration. You can configure up to three RADIUS servers, and up to 15 RADIUS server addresses. See Using multiple RADIUS server groups for information about grouping multiple RADIUS servers.
The switch uses the first server it successfully accesses, see Changing RADIUS-server access order.
For switches that have a separate out-of-band management port, the
oobmparameter specifies that the RADIUS traffic goes through the out-of-band management (OOBM) port.
[
auth-port|<port-number>]Optional. Changes the UDP destination port for authentication requests to the specified RADIUS server (host). If you do not use this option with the
radius-server hostcommand, the switch automatically assigns the default authentication port number. Theauth-portnumber must match its server counterpart.
[
acct-port|<port-number>]Optional. Changes the UDP destination port for accounting requests to the specified RADIUS server. If you do not use this option with the RADIUS-server host command, the switch automatically assigns the default accounting port number. The
acct-portnumber must match its server counterpart.
Enables or disables the processing of Disconnect and Change of Authorization messages from this host. When enabled, the RADIUS server can dynamically terminate or change the authorization parameters (such as VLAN assignment) used in an active client session on the switch. The UDP port specified in the
radius-server dyn-autz-portcommand (defaults to 3799) is the port used to listen for Change of Authorization messages (CoA) or Disconnect messages (DM). See Change-of-Authorization.
Optional. Specifies an encryption key for use during authentication (or accounting) sessions with the specified server. This key must match the encryption key used on the RADIUS server. Use this command only if the specified server requires a different encryption key than configured for the global encryption key.
NOTE: Formerly, when you saved the configuration file using Xmodem or TFTP, the RADIUS encryption key information was not saved in the file. This caused RADIUS authentication to break when the startup configuration file was loaded back onto the switch. You now can save the configured RADIUS shared secret (encryption) key to a configuration file by entering the commands listed.
Encryption key to use with the RADIUS server, specified using a base64–encoded aes-256 encrypted string.
The time window in seconds within which the received dynamic authorization requests are considered to be current and accepted for processing. A zero value means there is no time limit. A non-zero value indicates that the even-timestamp attribute is expected as part of all Change of Authorization and Disconnect request messages. If the timestamp attribute is not present the message is dropped.
Example
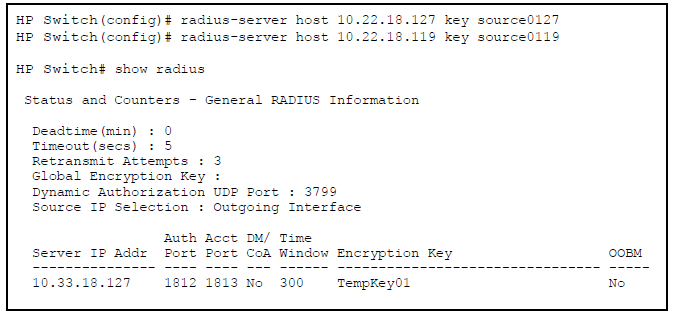
Suppose you have configured the switch as shown in Sample configuration for RADIUS server before changing the key and adding another server and you now need to make the following changes:
To make these changes, perform the following:
To change the order in which the switch accesses RADIUS servers, see Changing RADIUS-server access order.
Configure the switch for the following global RADIUS parameters:
-
Number of login attempts
In a given session, this specifies how many tries at entering the correct user name and password pair are allowed before access is denied and the session terminated. This is a general
aaa authenticationparameter and is not specific to RADIUS. -
Global server key
The server key the switch uses for contacts with all RADIUS servers for which there is not a server-specific key configured by
radius-server host<ip-address>key<key-string>. This key is optional if you configure a server-specific key for each RADIUS server entered in the switch. See Configuring the switch to access a RADIUS server. -
Server timeout
Defines the time period in seconds for authentication attempts. If the timeout period expires before a response is received, the attempt fails.
-
Server dead time
Specifies the time in minutes during which the switch avoids requesting authentication from a server that has not responded to previous requests.
-
Retransmit attempts
If the first attempt to contact a RADIUS server fails, this specifies how many retries to allow the switch to attempt on that server.
-
Change of Authorization port
The dyn-autz-port parameter specifies the UDP port number that listens for the Change of Authorization and Disconnect messages. The UDP port range is 1024-49151. The default port is 3799.
Syntax
Specifies how many tries for entering the correct user name and password are allowed before shutting down the session due to input errors.
Specifies the global encryption key the switch uses with servers for which the switch does not have a server-specific key assignment. This key is optional if all RADIUS server addresses configured in the switch include a server-specific encryption key.
Optional. Specifies the time in minutes during which the switch does not attempt to use a RADIUS server that has not responded to an earlier authentication attempt.
Specifies the UDP port number that listens for Change of Authorization or Disconnect messages. The range of ports is 1024-49151.
Specifies the maximum time the switch waits for a response to an authentication request before counting the attempt as a failure.
If a RADIUS server fails to respond to an authentication request, specifies how many retries to attempt before closing the session.
Example
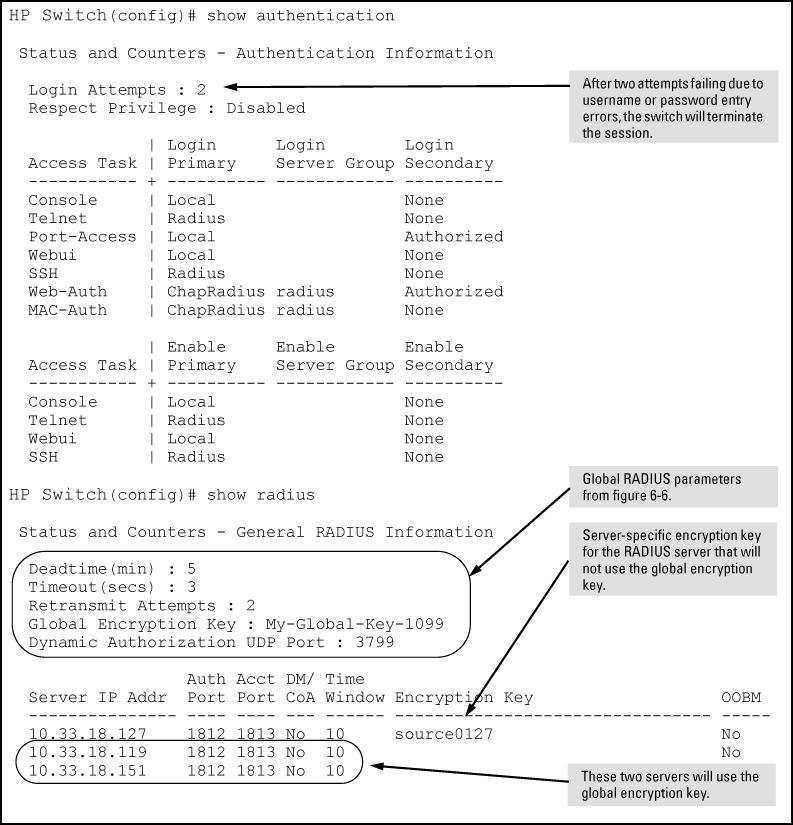
Suppose your switch is configured to use three RADIUS servers for authenticating access through Telnet and SSH. Two of these servers use the same encryption key. In this case the plan is to configure the switch with the following global authentication parameters:
-
Allow only two tries to correctly enter user name and password.
-
Use the global encryption key to support the two servers that use the same key. (For this example, assume that you did not configure these two servers with a server-specific key.)
-
Use a dead-time of five minutes for a server that fails to respond to an authentication request.
-
Allow two retries following a request that did not receive a response.
Listings of global RADIUS parameters configured in Example of global configuration exercise for RADIUS authentication
Syntax
Adds a server to the RADIUS configuration or (with no) deletes a server from the configuration. You can configure up to fifteen RADIUS server addresses. The switch uses the first server it successfully accesses.
Syntax
Associates a RADIUS server with a server group. Each group can contain up to 3 RADIUS servers. The default group (called RADIUS'), can only contain the first three RADIUS servers. The default group cannot be edited. The
noform of the command removes the RADIUS server with the indicated IP address from the server group. If that server was the last entry in the group, the group is removed.The group name of the RADIUS server group. The name has a maximum length of 12 characters. Up to five groups can be configured with a a maximum of three RADIUS servers in each group. The first group slot is used by the default group.
The following commands have the server-group option. If no server-group is specified, the default RADIUS group is used. The server group must already be configured.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The last RADIUS server in a server group cannot be deleted if any authentication or accounting method is using the server group. |
|
|
Syntax
aaa authentication[<console|telnet|ssh|web>|<enable|login>|local
|radius] [server-group||group-namelocal|none|authorized]Configures the primary password authentication method for console,Telnet, SSH, and the WebAgent.
<local|radius>
[<local]
radius>Use either the local switch user/password database or a RADIUS server for authentication.
Specifies the server group to use.
[
local|none|authorized]Provides options for secondary authentication.
Note that for console access, secondary authentication must be local if primary access is not local. This prevents being locked out of the switch in the event of a failure in other access methods.
Syntax
aaa authentication[<port-access>|<local|eap-radius|chap-radius>|<macbased|web-based|<chap-radius|peap-mschapv2>] [none|authorized|server-group|<group-name>]>>Configures the primary authentication method for port-access, MAC-based, or web-based access.
mac-based|web-based<chap-radius|peap-mschapv2>Password authentication for web-based or MAC-based port access to the switch. Use
peap-mschapv2for password verification without requiring access to a plain text password; it is more secure.Configures
local,chap-radius (MD5), oreap-radiusas the primary password authentication method for port-access.
[
none|authorized|server-group<group-name>]
none: No backup authentication method is used.
authorized: Allow access without authentication
server-group <group-name>: Specifies the server group to use with RADIUS.
-
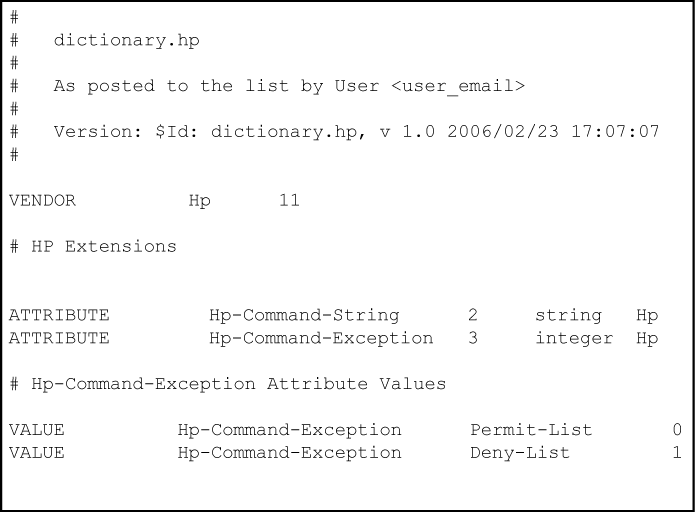
Create a dictionary file (for example, dictionary.hp) containing HP VSA definitions. An example file is:
-
Find the location of the dictionary files used by FreeRADIUS (try
/usr/local/share/freeradius). -
Copy dictionary.hp to that location. Open the existing dictionary file and add this entry:
-
You can now use HP VSAs with other attributes when configuring user entries.
Configuring a Cisco secure ACS for MS Windows
It is necessary to create a dictionary file that defines the VSAs so that the RADIUS server application can determine which VSAs to add to its user interface. The VSAs appear below the standard attributes that can be configured in the application.
The dictionary file must be placed in the proper directory on the RADIUS server. Follow these steps.
Create a dictionary file (for example, hp.ini) containing the HP VSA definitions, as shown in the example below.
;[User Defined Vendor] ; ; The Name and IETF vendor code and any VSAs MUST be unique. ; ; One or more VSAs named (max 255) ; ; Each named VSA requires a definition section ; ; Types are STRING, INTEGER, IPADDR ; ; The profile specifies usage, IN for accounting, OUT for authorization, ; MULTI if more than a single instance is allowed per RADIUS message. ; Combinations are allowed, e.g. "IN", "MULTI OUT", "MULT IN OUT" ; ; Enumerations are optional for INTEGER attribute types [User Defined Vendor] Name=HP IETF Code=11 VSA 2=Hp-Command-String VSA 3=Hp-Command-Exception Hp-Command-String] Type=STRING Profile=IN OUT Hp-Command-Exception] Type=INTEGER Profile=IN OUT Enums=Hp-Command-Exception-Types Hp-Command-Exception-Types] 0=PermitList 1=DenyListCopy the hp.ini dictionary file to c:\program files\cisco acs 3.2\utils (or the \utils directory wherever acs is installed).
From the command prompt execute the following command:
c:\Program files\CiscoSecure ACS v3.2\utils> csutil -addudv 0 hp.iniThe zero is the slot number. You see some processing messages:
Adding or removing vendors requires ACS services to be re-started. Please make sure regedit is not running as it can prevent registry backup/restore operations. Are you sure you want to proceed? (Y or N) yParsing [.\hp.ini] for addition at UDV slot
Creating backup of current config
Start the registry editor (regedit) and browse to HKEY_LOCAL_MACHINE\software\cisco\CiscoAAA v3.2\NAS Vendors tree.
Cisco adds the entry into this tree for each custom vendor. The id is 100 + the slot number used in the previous command (100 + 0, as it was added in slot 0). Look in the key to verify the vendor name and id.
Go to:HKEY_LOCAL_MACHINE\software\cisco\CiscoAAAv3.2\CSRadius\ExtensionPoints\002\AssociatedWithVendors
Right click and then select New> key. Add the vendor Id number that you determined in step 4 (100 in the example).
The newly created HP RADIUS VSA appears only when you configure an AAA client (NAS) to use the HP VSA RADIUS attributes. Select Network Configuration and add (or modify) an AAA entry. In the Authenticate Using field choose RADIUS(HP) as an option for the type of security control protocol.
Select
Submit + Restartto effect the change. The HP RADIUS VSA attributes appears in Cisco ACS configurations, for example, "Interface Configuration", "Group Setup", "User Setup".
To enable the processing of the HP-Command-String VSA for RADIUS accounting:
Below are the procedures for processing the HP-Command-String VSA.
-
Select CSV RADIUS Accounting. In the Select Columns to Log section, add the HP-Command-String attribute to the Logged Attributes list.
-
Select Network Configuration. In the AAA Clients section, select an entry in the AAA Client Hostname column. This opens the AAA Client Setup screen.
-
Check the box for Log Update/Watchdog Packets from this AAA Client.
-
Click Submit + Restart. You should be able to see the HP-Command-String attribute in the RADIUS accounting reports.
-
Enter the commands you wish to allow or deny with the special characters used in standard regular expressions (c, ., \, list], ^list], *, ^, $). Commands must be between 1-249 characters in length.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This procedure assumes:
If you have not already done so, see RADIUS Authentication, Authorization, and Accounting.
|
|
|
Before you configure the actual accounting parameters, configure the switch to use a RADIUS server. This process is outlined in Configuring the switch to access a RADIUS server. Repeat this now only if one of the following applies:tt
-
The switch is not yet configured to use a RADIUS server
-
Your server data has changed
-
You need to specify a non-default UDP destination port for accounting requests
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Switch operation expects a RADIUS server to accommodate both authentication and accounting. |
|
|
Syntax
Optional. Changes the UDP destination port for accounting requests to the specified RADIUS server. If you do not use this option, the switch automatically assigns the default accounting port number. (Default: 1813)
Optional. Specifies an encryption key for use during accounting or authentication sessions with the specified server. This key must match the encryption key used on the RADIUS server. Use this command only if the specified server requires a different encryption key than configured for the global encryption key.
Note: If you save the config file using Xmodem or TFTP, the key information is not saved in the file. This causes RADIUS authentication to fail when the config file is loaded back onto the switch.
Encryption key to use with the RADIUS server, specified using a base64-encoded aes-256 encrypted string.
Example
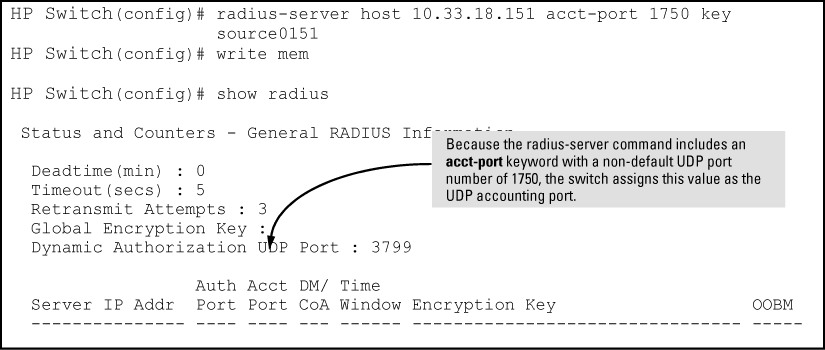
Suppose you want the switch to use the RADIUS server described below for both authentication and accounting purposes.
-
IP address: 10.33.18.151
-
A non-default UDP port number of 1750 for accounting
-
An encryption key of "source0151" for accounting sessions
For this example, assume that all other RADIUS authentication parameters for accessing this server are acceptable at their default settings, and RADIUS is already configured as an authentication method for one or more types of access to the switch (Telnet, Console, etc.).
The RADIUS-server command as shown in Example of configuring for a RADIUS Server with a non-default accounting UDP port number above, configures the switch to use a RADIUS server at IP address 10.33.18.151, with a non-default UDP accounting port of 1750, and a server-specific key of "source0151".
Syntax
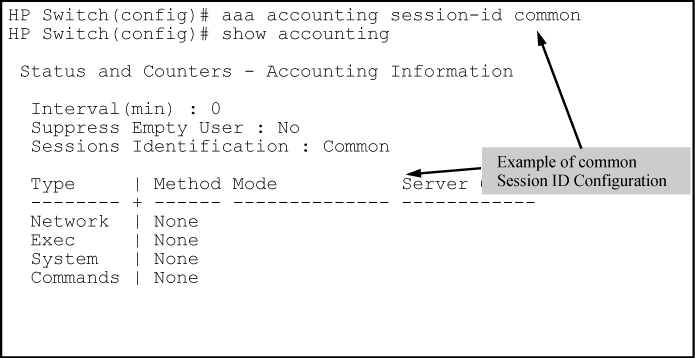
Optional command to reconfigure the Acct-Session-ID mode to apply to the accounting service type records for a given management session.
Configures the switch to use a different Acct-Session-ID for each accounting service type. (Default setting)
Configures the switch to apply the same Acct-Session-ID to all accounting service types in the same management session.
For more on these options, see Acct-Session-ID options in a management session.
Syntax
Configures RADIUS accounting service type and how data is sent to the RADIUS server.
<exec|network|system|command>Specifies an accounting service type to configure. See Accounting service types.
-
Use
execif you want to collect accounting information on login sessions on the switch via the console, Telnet, or SSH. See Accounting services -
Use
systemif you want to collect accounting data when:-
A system boot or reload occurs
-
System accounting is turned on or off
![[NOTE: ]](images/note.gif)
NOTE: There is no time span associated with using the system option. It simply causes the switch to transmit whatever accounting data it currently has when one of the above events occurs.
-
-
Use
networkif you want to collect accounting information on 802.1X port-based-access to the network by users connected to the physical ports on the switch. See Accounting services. -
Commands: When commands accounting is enabled, an accounting notice record is sent after the execution of each command.
These options are enabled separately, and define how the switch sends accounting data to a RADIUS server:
-
Applies to the
exec,network, andsystemaccounting service types:-
Send a "start record accounting" notice at the beginning of the accounting session and a "stop record notice" at the end of the session. Both notices include the latest data the switch has collected for the requested accounting type.
-
Do not wait for an acknowledgement.
-
-
Applies to the
network,exec,system, andcommandservice types, as described below:-
Send a stop record accounting notice at the end of the accounting session. The notice includes the latest data the switch has collected for the requested accounting type (
network,exec, orsystemservice types). For thecommandsservice type, sends the "Stop" accounting notice after execution of each CLI command. -
Do not wait for an acknowledgment.
-
-
Interim-Update
Applies only to the
commandservice type, and is intended for use when the optionalcommonsession ID is configured. Enablinginterim-updatein this case results in the command accounting records appearing as enclosed sub-parts of theexecservice type record for a given management session. Using interim-update when theuniquesession ID is configured has no effect because in this case, the different service types appear as separate accounting processes with separate Acct-Session-ID values.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Configuring |
|
|
Example
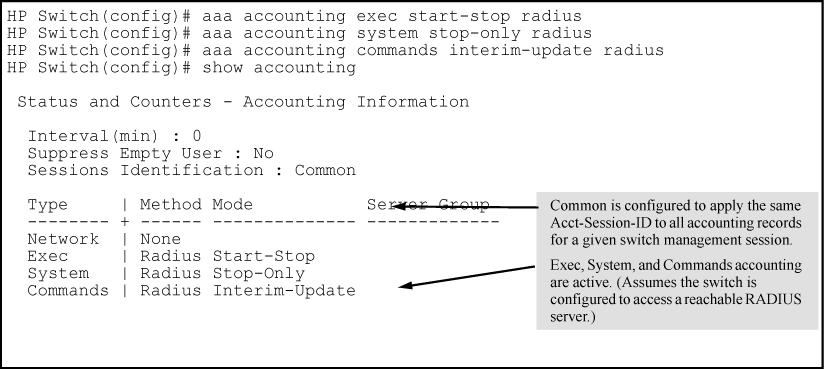
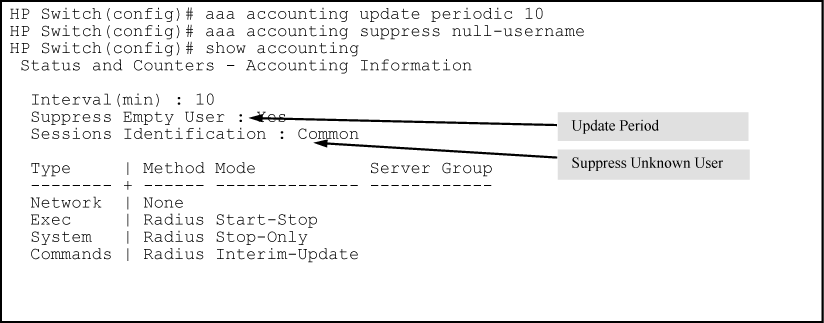
To configure RADIUS accounting on the switch with start-stop for Exec functions, stop-only for system functions, and interim-update for commands functions.
This example continues from Example of configuring accounting types and controls, where the session ID was configured as common.
Example
If the switch is configured with RADIUS accounting on the switch to use start-stop for Exec, System, and Command functions, as shown in Example of accounting session operation with "start-stop" enabled, there is an "Accounting-On" record when the switch boots up and an "Accounting-Off" record when the switch reboots or reloads. (Assume that Acct-Session-Id is configured for common.)
These optional parameters give you additional control over accounting data.
-
Updates: In addition to using a
Start-StoporStop-Onlytrigger, you can optionally configure the switch to send periodic accounting record updates to a RADIUS server. -
Suppress: The switch can suppress accounting for an unknown user having no user name.
Syntax
Sets the accounting update period for all accounting sessions on the switch.
The
noform disables the update function and resets the value to zero.
Syntax
To continue the example in Example of configuring accounting types and controls, suppose you want the switch to:
-
Send updates every 10 minutes on in-progress accounting sessions.
-
Block accounting for unknown users (no user name).
Some RADIUS-based features implemented on HP switches use HP VSAs for information exchange with the RADIUS server. RADIUS Access-Accept packets sent to the switch may contain the vendor-specific information.
The list of commands that are permitted (or denied) execution by the user are called regular expressions. The system compares those regular expressions against the full command name to determine whether the user is allowed to execute the command. For example, assume a RADIUS user is defined as follows:
User1 is blocked from executing all commands that contain “config” in the name, which includes the following commands:
To block User 1 from executing only the “configure” command, the regular expression would be:
The ^ metacharacter defines the start of the string and the $ character defines the end of the string. Do not leave a space between the semi-colon and the start of the next regular expression. So the HP-Command-String with more than one regular expression defined may look as follows:
HP-Command-String = “^configure$;^show running-config$”.
In this case, User1 is blocked from executing the commands “configure” and “show running-config” but is able to execute the “show config” command.
The attributes supported with commands authorization are:
-
HP-Command-String: List of commands (regular expressions) that are permitted (or denied) execution by the user. The commands are delimited by semi-colons and must be between 1 and 249 characters in length. Multiple instances of this attribute may be present in Access-Accept packets. (A single instance may be present in Accounting-Request packets.)
-
HP-Command-Exception: A flag that specifies whether the commands indicated by the HP-Command-String attribute are permitted or denied to the user. A zero (0) means permit all listed commands and deny all others; a one (1) means deny all listed commands and permit all others.
The following table shows the results of using the HP-Command-String and HP-Command-Exception attributes in various combinations.
HP command string and exception
| HP-command-string | HP-command-exception | Description |
|---|---|---|
| Not present | Not present | If command authorization is enabled and the RADIUS server does not provide any authorization attributes in an Access-Accept packet, the user is denied access to the server. This message appears: "Access denied: no user's authorization info supplied by the RADIUS server." |
| Not present | DenyList-PermitOthers(1) | Authenticated user is allowed to execute all commands available on the switch. |
| Not present | PermitList-DenyOthers(0) | Authenticated user can only execute a minimal set of commands (those that are available by default to any user). |
| Commands List | DenyList-PermitOthers(1) | Authenticated user may execute all commands except those in the Commands list. |
| Commands List | PermitList-DenyOthers(0) | Authenticated user can execute only those commands provided in the Commands List, plus the default commands. |
| Commands List | Not present | Authenticated user can only execute commands from the Commands List, plus the default commands. |
| Empty Commands List | Not present | Authenticate user can only execute a minimal set of commands (those that are available by default to any user). |
| Empty Commands List | DenyList-PermitOthers(1) | Authenticated user is allowed to execute all commands available on the switch. |
| Empty Commands List | PermitList-DenyOthers(0) | Authenticate user can only execute a minimal set of commands (those that are available by default to any user). |
You must configure the RADIUS server to provide support for the HP VSAs. There are multiple RADIUS server applications; the two examples below show how a dictionary file can be created to define the VSAs for that RADIUS server application.
Only RADIUS-authenticated port-access clients are able to dynamically change the port access settings using the new proprietary RADIUS VSAs. The settings that can be overridden are:
-
Client limit (address limit with mac-based port access)
-
Disabling the port-access types
-
Setting the port mode in which 802.1X is operating
If the VSA client limit decreases the switch configured client limit, all clients except the client that is overriding the settings is deauthenticated. Only one client session at a time can override the port-access settings on a port. When the client session is deauthenticated, the port resets itself to the configured settings. This port reset causes the deauthentication of all clients for the port-access authentication types that had their settings changed dynamically.
-
HP-Port-Client-Limit-Dot1x
This VSA temporarily alters the 802.1X authentication client limit to the value contained in the VSA. Values range from 0 to 32 clients. A zero client limit means this VSA is disabled. This is an HP proprietary VSA with a value of 10.
-
HP-Port-Client-Limit-MA
This VSA temporarily alters the MAC authentication client limit to the value contained in the VSA. Values range from 0 to 256 clients. A zero client limit means this VSA is disabled. This is an HP proprietary VSA with a value of 11.
-
HP-Port-Client-Limit-WA
This VSA temporarily alters the web-based authentication client limit to the value contained in the VSA. Values range from 0 to 256 clients. A zero client limit means this VSA is disabled. This is an HP proprietary VSA with a value of 12.
-
HP-Port-Auth-Mode-Dot1x
This VSA temporarily alters the 802.1X authentication mode to be either port-based or user-based depending on the value in the VSA. A port-based VSA is set with a value of 1; a user-based VSA is set with a value of 2. This is an HP proprietary VSA with a value of 13.
If an 802.1X port is operating in port-based mode, it is invalid to set the 802.1X client limit using the HP-Port-Client-Limit VSA.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The changing of the client limits for a port using VSAs is temporary. The running configuration file is not changed and still displays the client limit and address limit settings. |
|
|
Each authentication type may have a unique value for the client limit. If the value of the VSA is zero, the authentication type corresponding to that VSA is disabled.
Settings for these VSAs are in effect for the duration of the authenticated session of the downstream supplicant switch. If for any reason there is a loss of the session (link loss between authenticator switch and supplicant switch, or authentication failure during reauthentication), the originally configured 802.1X and MAC authentication limits are restored.
The following commands have the server-group option. If no server-group is specified, the default RADIUS group is used. The server group must have already been configured.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The last RADIUS server in a server group cannot be deleted if an authentication or accounting method is using the server group. |
|
|
Syntax
aaa authentication <console | telenet | ssh | web><enable | login| local |radius {server-group<group-name> | local | none | authorized}>Configures the primary password authentication method for console, Telnet, SSH, and/or the WebAgent.
Syntax
aaa authentication <port-access <local | eap-radius | <mac-based | web-based <chap-radius | peap-mschapv2> [none | authorized | server-group <group-name>]>>Configures the primary authentication method for portaccess, MAC-based, or web-based access.