When using enhanced secure mode, several commands have differences from standard secure mode in their options or output. To transition from one security mode to the other, enter this command from a serial terminal connected to the switch.
Syntax
Enables the selected secure mode. This command must be executed from a serial terminal.
Use standard security. This is the default.
HP Switch(config)# secure-mode enhanced Validating software and configurations, this may take a minute... The system will be rebooted and all management module files except software images will be erased and zeroized. This will take up to 60 minutes and the switch will not be usable during that time. A power-cycle will then be required to complete the transition. Continue (y/n)? y (Switch reboots...) . Zeroizing the file system ... 100% Verifying cleanness of the file system... 100% Restoring firmware image and other system files... Zeroization of file system completed Continue initializing... ... HP Switch(config)# show secure-mode Level: EnhancedIf the secure-mode transition fails, this message displays:
Secure-mode transition failed.
For feature-specific show commands, the following prompt appears before the sensitive information is displayed when using enhanced secure mode:
This may show sensitive information. Continue (y/n)?
If “y/Y” is entered, the normal output of the command is displayed. If any other key is pressed, the command is not executed and there is no output. The default is “n/N” when interactive mode is disabled.
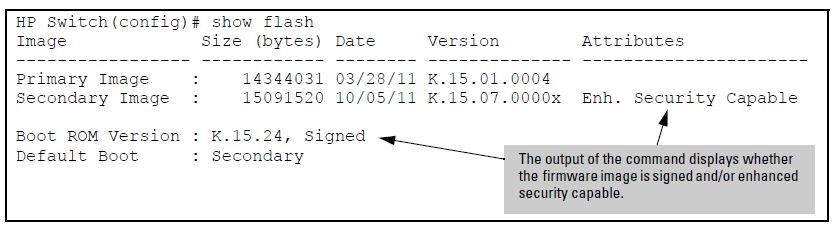
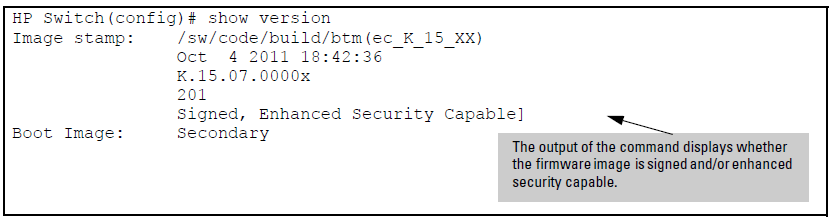
When using enhanced secure mode, the output from the show flash and show version commands is slightly different.
The show config commands that may show sensitive information on the console are:
When one of the above commands is executed in enhanced secure mode, the following prompt displays:
Do you want to show sensitive information (y/n)?
If “Y/y” is entered, the normal command output is displayed on the console. If “N/n” is entered, all the sensitive information is hidden and will be displayed as asterisks (“*****”). The default option is “N/n” when interactive mode is disabled.
When MIB CLI commands are executed in enhanced secure mode, the following prompt appears before the sensitive information for the getmib or walkmib command is displayed:
This may show sensitive information. Continue (y/n)?
If “Y/y” is entered, the sensitive information is displayed in plain text. If ‘N/n’ is entered, the command is not executed and there is no output. The default is “n/N” when interactive mode is disabled.
When using enhanced secure mode, the secret input echo for the setmib command is not replaced with asterisks, however, a warning message displays when this command is executed:
The setmib command should not be used in enhanced secure mode.
When the switch is in enhanced secure mode, a plaintext password cannot be entered inline; it is prompted for interactively twice, for example, for an operator password:
New password for operator: ***** Please retype new password for operator: *****
There is an additional password command option that allows the setting of a password for the ROM console. See Configuring Username and Password Security for more information about setting passwords on the switch.
Syntax
password <manager | operator>[username <ASCII-STR>][sha1<hashed-password>]
password <rom-console> | all
[no]password port-access [username <ASCII-STR>]Sets or clears the local password/user name for a given access level. If no password is entered in the command, you are prompted twice to enter the password. When the switch is in enhanced secure mode, the password for manager, operator, and the ROM console must be at least 8 characters long. The ROM password cannot be set or changed in the Web Agent. When the no form of the command is executed, the command removes specific local password protection. Note: The port-access option is available only if “includecredentials” is enabled.
All user names and passwords should be configured at startup after transitioning to enhanced secure mode, however, the switch will enter enhanced secure mode regardless of the password settings.
After a cold reboot from a console session... ROM console passwords must be set before continuing. New Manager password:****** Retype password:****** New Operator password:****** Retype password:******
Password Commands Affected by Enhanced Secure Mode
| Command in Standard Secure Mode | Command in Enhanced Secure Mode | Location |
|---|---|---|
| snmpv3 user <user-name> auth [md5 | sha] <password> [priv [des | aes] ] | snmpv3 user <user-name> auth [md5 | sha][priv] | Management and Configuration Guide |
| aaa port-access supplicant <port-list> identity <user-name> secret [<port-list>] | aaa port-access supplicant <port-list> identity <user-name> secret <port-list> | Commands to configure the global MAC authentication password |
| aaa port-access mac-based password <password> | aaa port-access mac-based password | |
| stack member <switch-num> mac-address <mac-addr>[password <password>] | stack member <switch-num> mac-address <mac-addr> password] | Advanced Traffic Configuration Guide |
When the switch security is in enhanced secure mode, CLI commands that take a secret key as a parameter have the echo of the secret typing replaced with asterisks, unless the secret is not used for authorizing access to switch access. The input for <key-string> is prompted for interactively:
Enter key-string: ******** Re-enter key-string: ********
Enter authentication-key: ******** Re-enter authentication-key: ********
Secret key commands
| Command in Standard Secure Mode | Command in Enhanced Secure Mode | Location |
|---|---|---|
key-chain <chain-name> key <1-255> key-string <key-str> |
key-chain <chain-name> key <1-255> key-string <key-str> |
|
radius-server [host<ip-addr>] key <key-str> |
radius-server [host <ip-addr>] key |
Configuring the switch global RADIUS parameters |
tacacs-server [host <ip-addr>] key <key-str> |
tacacs-server [host <ip-addr>] key |
Configuring the switch TACACS+ server access |
sntp authentication key-id <1-4294967295> authentication-mode md5 key-value <key-str> [trusted] |
sntp authentication key-id <1-4294967295> authentication-mode md5 key-value [trusted] |
Management and Configuration Guide |
router ospf area <area-id> virtual-link <ip-addr> authentication-key <key-str> |
router ospf area <area-id> virtual-link <ip-addr> authentication-key |
Multicast and Routing Guide |
vlan <vid> ip rip [<ip-addr>] authentication-key |
vlan <vid> ip rip [<ip-addr>] authentication-key |
Multicast and Routing Guide |
vlan <vid> ip ospf [<ip-addr>] authentication-key <key-str> |
vlan <vid> ip ospf [<ip-addr>] authentication-key |
Multicast and Routing Guide |
autorun encryption-key <key-str> |
autorun encryption-key |
Management and Configuration Guide |
encrypt-credentials [pre-shared-key <hex | plaintext> <key-str>] |
encrypt-credentials [pre-shared-key <hex | plaintext>] |
Enabling Encrypt-Credentials |
There are fewer options available for the ip ssh cipher command in enhanced secure mode. The following options are unavailable:
-
3des-cbc
-
rijndael-dbd@lysator.liu.se
The only option available for the ip ssh mac <mac-type>command in enhanced secure mode is hmac-sha1.
When operating in enhanced secure mode, the SSL server will not allow protocol versions lower than TLS 1.0.
See Secure web management for more information about SSL.
For the 8200 switch, when zeroization is triggered by a secure mode transition, HA handles zeroization on the AMM and SMM automatically.
When zeroization is started from the ROM console, there is no synchronization performed between the AMM and SMM, as zeroization from the ROM console is treated as a recovery facility. Each MM has to be zeroized individually.
![[CAUTION: ]](images/caution.gif)