Before you configure web-based/MAC authentication, follow these guidelines.
-
Configure a local user name and password on the switch for both the operator (login) and manager (enable) access levels. HP recommends that you use a local user name and password pair to protect the switch configuration from unauthorized access.
-
Determine the switch ports that you want to configure as authenticators. Before you configure web-based or MAC authentication on a port operating in an LACP trunk, you must remove the port from the trunk.
To display the current configuration of 802.1X, web-based, and MAC authentication on all switch ports, enter the
show port-access configcommand, as shown in the following example.# show port-access config Port Access Status Summary Port-access authenticator activated [No] : No Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No Port 802.1X 802.1X Web Mac LMA Ctrl Mixed Speed Port Supp Auth Auth Auth Auth Dir Mode VSA MBV --- ------ ------ ---- ---- ---- ----- ----- ----- -------- C1 No Yes No No No In No Yes Yes C2 No Yes No No No Both Yes Yes Yes C3 No Yes No No No Both No No Yes C4 No Yes No No Yes Both No Yes Yes -
Determine whether any VLAN assignments are needed for authenticated clients.
-
If you configure the RADIUS server to assign a VLAN for an authenticated client, this assignment overrides any VLAN assignments configured on the switch while the authenticated client session remains active. The VLAN must be statically configured on the switch.
-
If there is no RADIUS-assigned VLAN, the port can join an “Authorized VLAN” for the duration of the client session. This must be a port-based, statically configured VLAN on the switch.
-
If there is neither a RADIUS-assigned VLAN or an “authorized VLAN” for an authenticated client session on a port, the port’s VLAN membership remains unchanged during authenticated client sessions. Configure the port for the VLAN in which you want it to operate during client sessions.
![[NOTE: ]](images/note.gif)
NOTE: When configuring a RADIUS server to assign a VLAN, you can use either the VLAN’s name or VID. For example, if a VLAN configured in the switch has a VID of 100 and is named vlan100, you could configure the RADIUS server to use either “100” or “vlan100” to specify the VLAN.
-
-
For clients that the RADIUS server does not authenticate, determine whether to use the optional “unauthorized VLAN” mode. This VLAN must be statically configured on the switch. If you do not configure an “unauthorized VLAN”, the switch simply blocks access to unauthenticated clients trying to use the port.
-
Determine the authentication policy you want on the RADIUS server and configure the server. Based on your switches RADIUS application information, include the following in the policy for each client or client device:
-
The CHAP-RADIUS authentication method.
-
An encryption key.
-
One of the following:
-
Include the user name and password for each authorized client if you are configuring web-based authentication.
-
Enter the device MAC address in both the user name and password fields of the RADIUS policy configuration for that device if you are configuring MAC authentication. To allow a particular device to receive authentication only through a designated port and switch, include this in your policy.
-
-
-
Determine the IP address of the RADIUS servers you choose to support web-based or MAC authentication.
Before you configure MAC authentication
-
Ensure that the VLANs are configured on the switch and that the appropriate port assignments have been made if you plan to use multiple VLANs with MAC authentication.
-
Ping the switch console interface to ensure that the switch is able to communicate with the RADIUS server you are configuring to support MAC authentication.
-
Configure the switch with the correct IP address and encryption key to access the RADIUS server.
-
Configure the switch for MAC authentication with the ports you will be using.
-
Test both the authorized and unauthorized access to your system to ensure that MAC authentication works properly on the ports you have chosen to configure for port-access.
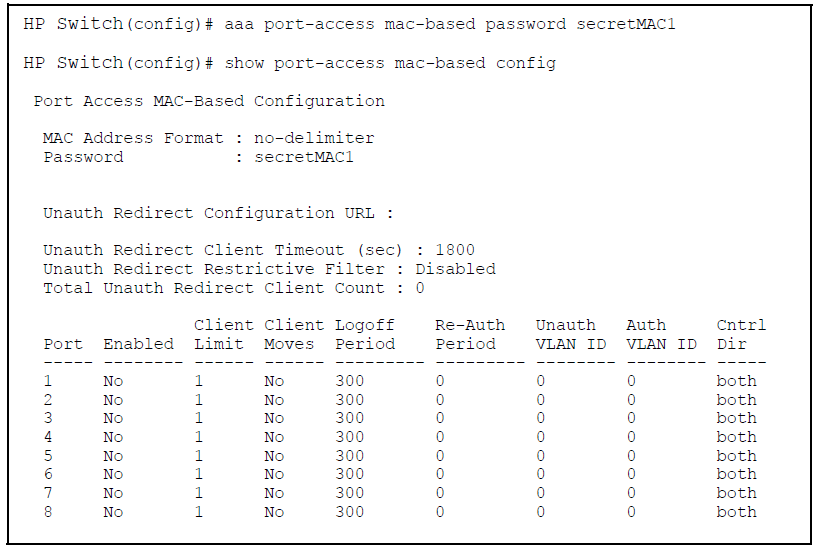
MAC authentication requires that only a single entry containing the user name and password is placed in the user database with the device's MAC address. This creates an opportunity for malicious device spoofing. The global password option configures a common MAC authentication password to use for all MAC authentications sent to the RADIUS server. This makes spoofing more difficult.
It is important that when implementing the global MAC authentication password option, that the user database on the RADIUS server has this password as the password for each device performing MAC authentication.
To configure the global MAC authentication password:
Syntax
Specifies the global password to be used by all MAC authenticating devices.
The
[no]form of the command disables the feature.For the 3800, 5400zl, and 8200zl switches, when the switch is in enhanced secure mode, commands that take a password as a parameter have the echo of the password typing replaced with asterisks. The input for the password is prompted for interactively. See Secure Mode (3800, 5400zl, and 8200zl Switches).
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The password value is listed in an exported config file when |
|
|
Syntax
aaa port-access mac-based addr-format<no-delimiter|single-dash
|multi-dash|multi-colon|no-delimiter-uppercase|single-dash-uppercase
|multi-dash-uppercase|multi-colon-uppercase>Specifies the MAC address format used in the RADIUS request message. This format must match the format used to store the MAC addresses in the RADIUS server.
no-delimiter: specifies an aabbccddeeff format.
single-dash: specifies an aabbcc-ddeeff format.
multi-dash: specifies an aa-bb-cc-dd-ee-ff format.
multi-colon: specifies an aa:bb:cc:dd:ee:ff format.
no-delimiter-uppercase: specifies an AABBCCDDEEFF format.
single-dash-uppercase: specifies an AABBCC-DDEEFF format
multi-dash-uppercase: specifies an AA-BB-CC-DD-EE-FF format
multi-colon-uppercase: specifies an AA:BB:CC:DD:EE:FF format.
Syntax
Specifies the maximum number of authenticated MACs to allow on the port.
NOTE: On switches where MAC authenticated and 802.1X operate concurrently, this limit includes the total number of clients authenticated through both methods.
The limit of 256 clients only applies when there are fewer than 16,384 authentication clients on the entire switch. After the limit of 16, 384 clients is reached, no additional authentication clients are allowed on any port for any method.
Syntax
Allows client moves between the specified ports under MAC authenticated control. When enabled, the switch allows addresses to move without requiring a re-authentication.
When disabled, the switch does not allow moves and when one occurs, the user is forced to re-authenticate. At least two ports (from ports and to ports) must be specified.
Use the
noform of the command to disable MAC address moves between ports under MAC authenticated control.
Syntax
aaa port-access mac-based[e]port-list[auth-vidvid]
no aaa port-access mac-based[e]port-list[]auth-vidSpecifies the VLAN to use for an authorized client. The RADIUS server can override the value (accept response includes avid).
If
auth-vidis0, no VLAN changes occur unless the RADIUS server supplies one.
Syntax
Syntax
Syntax
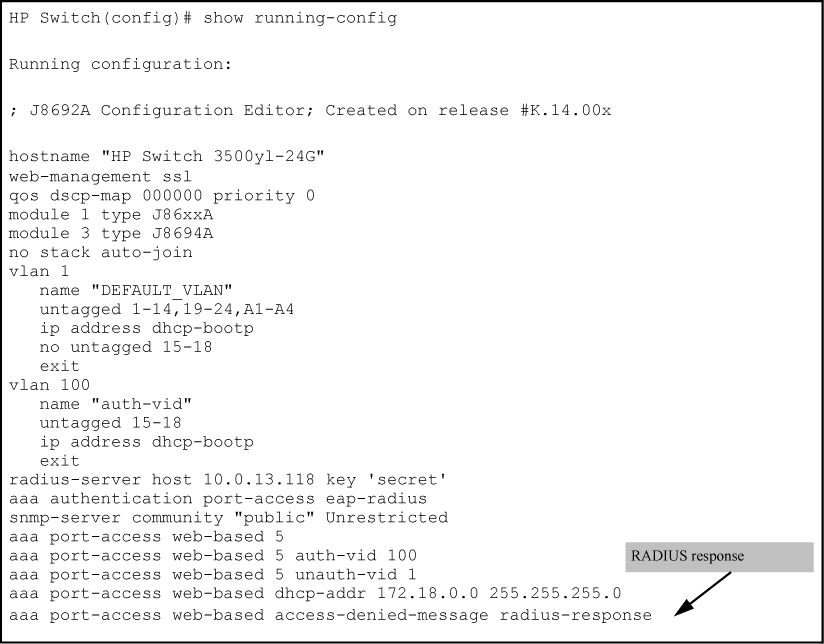
This feature allows administrators to configure custom messages that are displayed when authentication with the RADIUS server fails. The messages are appended to existing internal webpages that display during the authentication process. Messages can be configured using the CLI, or centrally using the RADIUS server, and can provide a description of the reason for a failure as well as possible steps to take to resolve the authentication issue. There is no change to the current web-based authentication functionality.
Syntax
Specifies the text message (ASCII string) shown on the webpage after an unsuccessful login attempt. The message must be enclosed in quotes.
The
[no]form of the command means that no message is displayed upon failure to authenticate.Default: The internal webpage is used. No message appears upon authentication failure.
The text message that is appended to the end of the webpage when there is an unsuccessful authentication request. The string can be up to 250 ASCII characters.
Use the text message provided in the RADIUS server response to the authentication request.
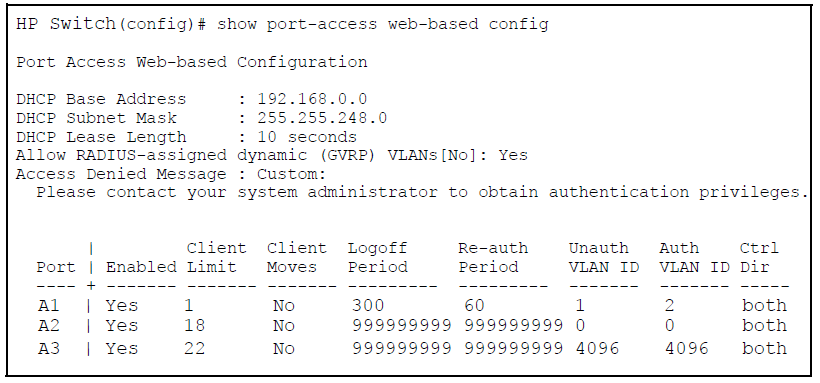
Unauthenticated clients can be assigned to a specific static, untagged VLAN (unauth-vid), to provide access to specific (guest) network resources. If no VLAN is assigned to unauthenticated clients, the port is blocked and no network access is available.
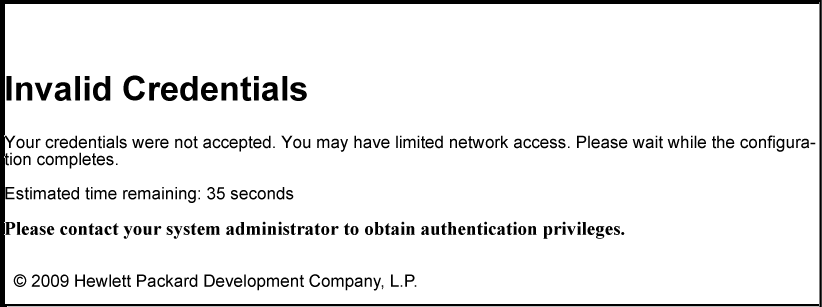
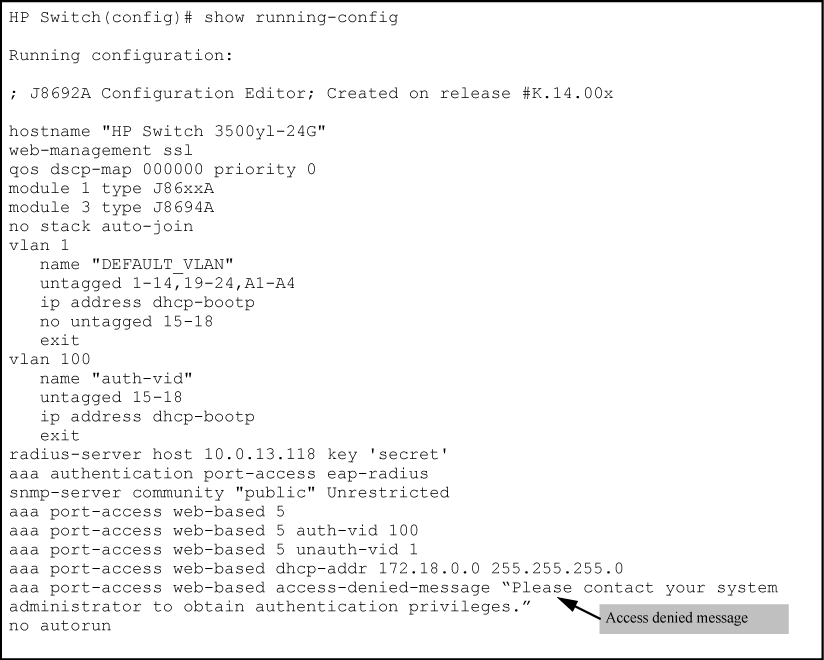
The following figure shows an example of the denied access message that appears when unauth-vod is configured.
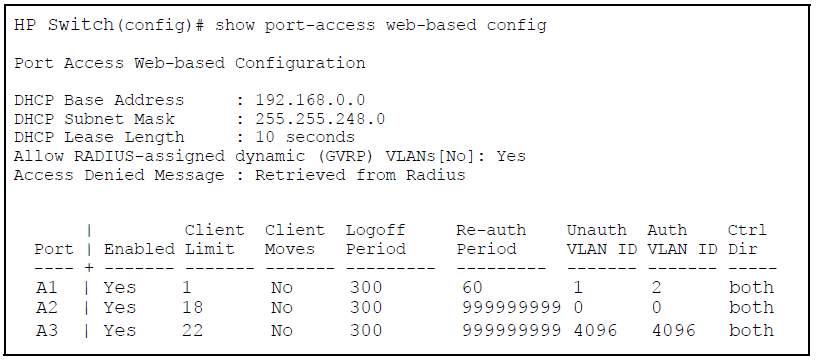
The show running-config command displays the client’s information, including the configured access denied message.
When a client’s MAC address is checked by the RADIUS server against the known list of MAC addresses, and the MAC address is not found, the client needs a way to quickly become registered through a web registration process. The HTTP Redirect feature provides a way for a client who has failed MAC authentication to become registered through a web/registration server. Only a web browser is required for this authentication process.
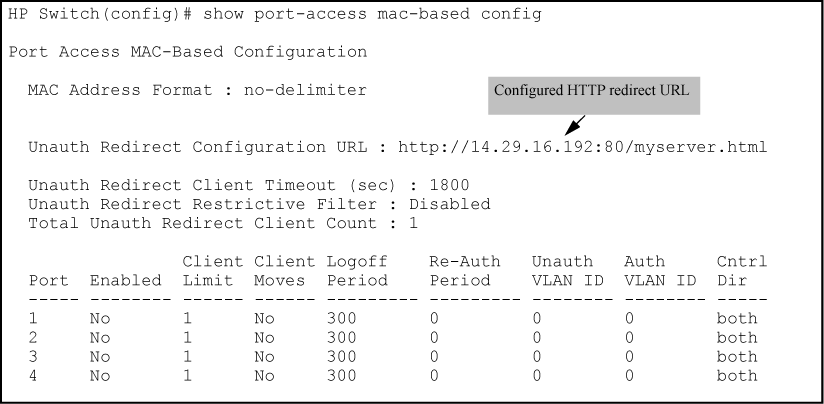
The unauth-redirect option must be configured with the registration server’s URL as a parameter before HTTP redirect operations can begin. The full URL must be used.
Syntax
Enables the HTTP redirect registration server feature by configuring the URL of the registration page. An entry can have either an IP address or a DNS name. Only one server can be configured.
NOTE: The entire URL must be used, including the “http://” or “https://” portion.
The time (in seconds) before a client in an unauthorized redirection state is removed from the state tables.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Rogue clients can attempt to access any webpages on the web/registration server via interface ports configured for MAC authentication. |
|
|
-
If the configured URL contains a domain name (as opposed to an IP address) the switch’s DNS resolver must be configured:
HP Switch(config)# ip dns server-address priority 1 <ipv4=address>
-
The NAT does an IP route lookup before it sends the packet to the destination registration server. A VLAN must have been configured that allows the switch to access the registration server.
-
The initial page, redirect server, and filter path configuration is per-switch.
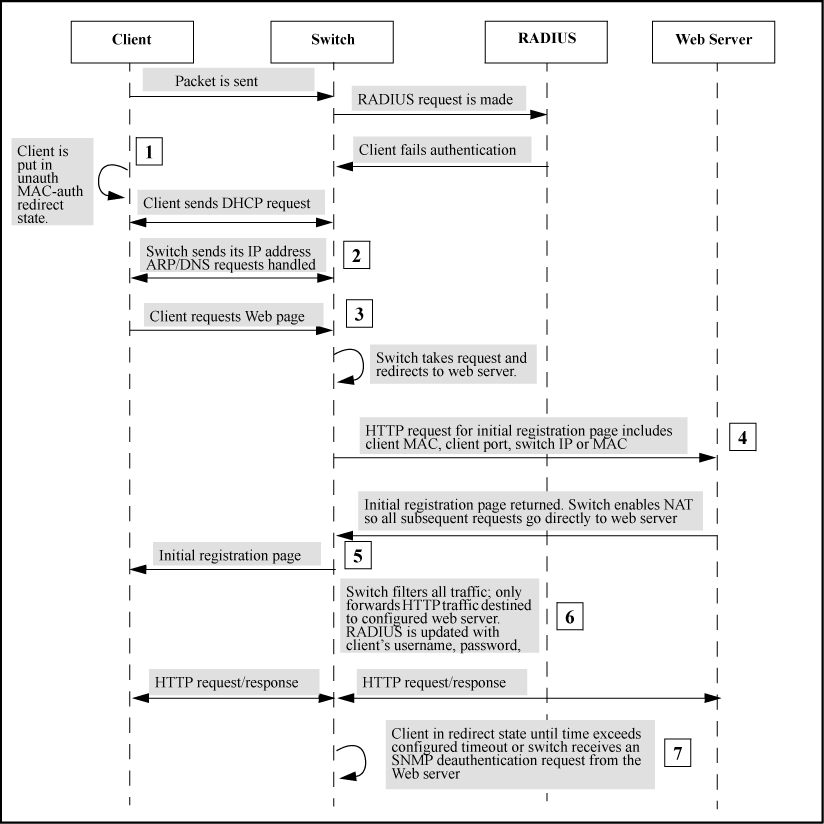
Following are the steps involved in HTTP registration.
-
When the redirect feature is enabled, a client that fails MAC authentication is moved into the unauthorized MAC authentication redirection state.
-
A client in the redirect state (having failed MAC authentication) with a web browser open sends a DHCP request. The switch responds with a DHCP lease for an address in the switch configurable DHCP address range. Additionally, the switch IP address becomes the client’s default gateway. All ARP/DNS requests are handled by the switch and all requests are directed to the switch.The switch replies to these requests with its own address.
-
The client requests a webpage. The switch takes this request and responds to the client browser with an HTTP redirect to the configured URL. The client MAC address and interface port are appended as HTTP parameters.
-
Before returning the initial registration page to the client, the switch enables NAT so that all subsequent requests go to the web server directly. The initial HTML page is returned to the switch and then by proxy to the client.
-
After the registration process completes, the registration server updates the RADIUS server with the client’s user name, password, and profile.
-
The client remains in the redirect state until the client’s time exceeds the configured timeout or the switch receives an SNMP deauthentication request from the registration server.
-
The registration server sends an SNMP request to the switch with the MAC identification and interface port to reauthenticate or deauthenticate the client.
-
The switch moves the client out of the special web-based/MAC authentication redirect state and the client becomes unknown to the switch again. This sets the stage for a new MAC authentication cycle.
The restrictive-filter option allows the switch to reply to all HTTP requests to the switch IP address with an HTTP-redirect containing the URL of the registration server. It is used when there is no registration process and only a warning or informational page is displayed to the client.
If SSL is not configured, the switch verifies that the MAC address and interface port parameters are present. If SSL is enabled, the switch ensures that the HTTP request is to the registration server’s destination IP address.
The MIB variable hpicfUsrAuthMacAuthClientReauthenticateEntry in the hpicfUsrAuthMIB provides the capability to reauthenticate a specific MAC client on a port. The MAC address and port are required for SNMP reauthentication.
To reauthenticate a client using the CLI, use this command:
HP Switch(config)# aaa port-access mac-based <single-port> reauthenticate mac-addr<MAC address>
The keyword mac-addr specifies single client reauthentication. If the reauthenticate parameter is entered without the mac-addr keyword and MAC address, the command is executed as port reauthentication — all clients on a port are reauthenticated.