ASPF H.323 application inspection configuration example
Network requirements
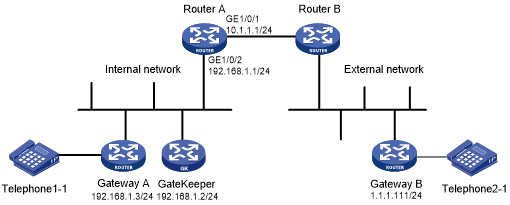
Figure 175 displays a typical H.323 application network. Gateway B on the external network needs to access the H.323 Gatekeeper, and with the assistance of Gatekeeper, to establish a connection with the H.323 Gateway A. Other protocol packets from the external network are dropped.
Configure a packet filter on Router A to permit only packets destined to the Gatekeeper. Configure an ASPF policy on Router A to detect H.323 protocol packets so that return packets to the external network can be passed through interface GigabitEthernet 1/0/1.
Figure 170: Network diagram
Configuration procedure
# Create ACL 3200 and configure two rules in the ACL: one to permit packets destined to Gatekeeper to pass, and one to deny all IP packets.
<RouterA> system-view [RouterA] acl advanced 3200 [RouterA-acl-ipv4-adv-3200] rule 0 permit ip destination 192.168.1.2 0 [RouterA-acl-ipv4-adv-3200] rule 5 deny ip [RouterA-acl-ipv4-adv-3200] quit
# Create ASPF policy 1 for H.323 inspection.
[RouterA] aspf policy 1 [RouterA-aspf-policy-1] detect h323 [RouterA-aspf-policy-1] quit
# Apply ACL 3200 to filter incoming packets on interface GigabitEthernet 1/0/1.
[RouterA] interface gigabitethernet 1/0/1 [RouterA-GigabitEthernet1/0/1] packet-filter 3200 inbound
# Apply ASPF policy 1 to incoming traffic on GigabitEthernet 1/0/1.
[RouterA-GigabitEthernet1/0/1] aspf apply policy 1 inbound [RouterA-GigabitEthernet1/0/1] quit
Verifying the configuration
# Verify that ASPF sessions have been created between Gateway B and Gatekeeper/Gateway A.
[RouterA] display aspf session ipv4 Initiator: Source IP/port: 1.1.1.111/33184 Destination IP/port: 192.168.1.3/32828 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: UDP(17) Inbound interface: GigabitEthernet1/0/1 Initiator: Source IP/port: 1.1.1.111/1719 Destination IP/port: 192.168.1.2/1719 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: UDP(17) Inbound interface: GigabitEthernet1/0/1 Initiator: Source IP/port: 1.1.1.111/3521 Destination IP/port: 192.168.1.2/20155 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: TCP(6) Inbound interface: GigabitEthernet1/0/1 Initiator: Source IP/port: 1.1.1.111/33185 Destination IP/port: 192.168.1.3/32829 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: UDP(17) Inbound interface: GigabitEthernet1/0/1 Initiator: Source IP/port: 1.1.1.111/3688 Destination IP/port: 192.168.1.2/1720 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: TCP(6) Inbound interface: GigabitEthernet1/0/1 Total sessions found: 5
# Verify that only return packets that match the entries can pass through GigabitEthernet 1/0/1. (Details not shown.)