ASPF TCP application inspection configuration example
Network requirements
Local users on the internal network need to access the external network. To protect the internal network against ICMP and SYN packet attacks from the external network, configure an ASPF policy on Router A. Router A can then drop faked ICMP error messages and non-SYN packets that are the first packets over TCP connections.
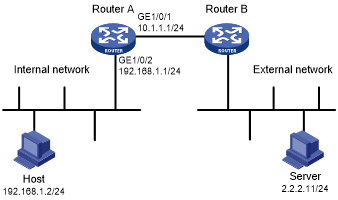
Figure 169: Network diagram
Configuration procedure
# Configure ACL 3111 to deny all IP packets.
<RouterA> system-view [RouterA] acl advanced 3111 [RouterA-acl-ipv4-adv-3111] rule deny ip [RouterA-acl-ipv4-adv-3111] quit
# Create ASPF policy 1.
[RouterA] aspf-policy 1
# Enable ICMP error message check.
[RouterA-aspf-policy-1] icmp-error drop
# Enable TCP SYN check.
[RouterA-aspf-policy-1] tcp syn-check [RouterA-aspf-policy-1] quit
# Enable ASPF policy 1 to inspect FTP packets.
[RouterA-aspf-policy-1] detect ftp
# Apply ACL 3111 to deny all incoming IP packets on GigabitEthernet 1/0/1.
[RouterA] interface gigabitethernet 1/0/1 [RouterA-GigabitEthernet1/0/1] packet-filter 3111 inbound
# Apply ASPF policy 1 to outgoing traffic on interface GigabitEthernet 1/0/1.
[RouterA-GigabitEthernet1/0/1] aspf apply policy 1 outbound
Verifying the configuration
# Display the configuration of ASPF policy 1.
<RouterA> display aspf policy 1
ASPF policy configuration:
Policy number: 1
ICMP error message check: Enabled
TCP SYN packet check: Enabled
Inspected protocol Action
FTP None
Router A can recognize faked ICMP error messages from external networks, and drop the non-SYN packets that are the first packets to establish TCP connections.