ASPF application to a zone pair configuration example
Network requirements
Configure an ASPF policy on the router to inspect FTP traffic that passes through the router to implement the following filtering:
Permits only return packets for the FTP connections initiated by users on the internal network to pass through the router.
Blocks all other types of packets from the external network to the internal network.
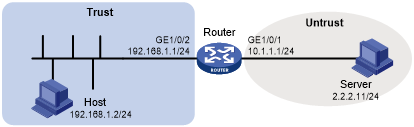
Figure 171: Network diagram
Configuration procedure
# Configure ACL 3500 to permit IP packets.
<Router> system-view [Router] acl advanced 3500 [Router-acl-ipv4-adv-3500] rule permit ip [Router-acl-ipv4-adv-3500] quit
# Add GigabitEthernet 1/0/2 to the security zone Trust.
[Router] security-zone name trust [Router-security-zone-Trust] import interface gigabitethernet 1/0/2 [Router-security-zone-Trust] quit
# Add GigabitEthernet 1/0/1 to the security zone Untrust.
[Router] security-zone name untrust [Router-security-zone-Untrust] import interface gigabitethernet 1/0/1 [Router-security-zone-Untrust] quit
# Create ASPF policy 1 for FTP inspection.
[Router] aspf policy 1 [Router-aspf-policy-1] detect ftp [Router-aspf-policy-1] quit
# Create a zone pair and enter its view.
[Router] zone-pair security source trust destination untrust
# Apply the ACL to filter to permit outgoing packets in the zone pair.
[Router-zone-pair-security-Trust-Untrust] packet-filter 3500
# Apply the ASPF policy to the zone pair.
[Router-zone-pair-security-Trust-Untrust] aspf apply policy 1 [Router-zone-pair-security-Trust-Untrust] quit
Verifying the configuration
# Verify that an ASPF session has been established for the FTP connection between the host and the server.
<Router> display aspf session ipv4 Initiator: Source IP/port: 192.168.1.2/1877 Destination IP/port: 2.2.2.11/21 VPN instance/VLAN ID/Inline ID: -/-/- Protocol: TCP(6) Inbound interface: GigabitEthernet1/0/2 Source security zone: Trust Inbound interface: GigabitEthernet1/0/2 Source security zone: Trust Total sessions found: 1
# Verify that only return packets that match the entries can enter the internal network. (Details not shown.)