Aggressive mode with NAT traversal configuration example
This configuration example is not available when the device is operating in FIPS mode.
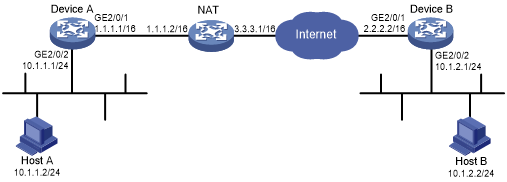
Network requirements
Device A is behind the NAT device. Hosts behind Device A use public IP address 3.3.3.1 to access the external network.
Configure an IKE-based IPsec tunnel between Device A and Deice B to secure the communication between subnet 10.1.1.0/24 and subnet 10.1.2.0/24.
Configure Device A and Device B to use the default IKE proposal for the aggressive IKE negotiation to set up the IPsec SAs.
Configure the two devices to use the pre-shared key authentication method for the IKE negotiation phase 1.
Figure 138: Network diagram
Configuration procedure
Configure Device A:
# Assign an IP address to each interface. (Details not shown.)
# Configure IPv4 advanced ACL 3000 to identify traffic from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
<DeviceA> system-view [DeviceA] acl advanced 3000 [DeviceA-acl-ipv4-adv-3000] rule 0 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 [DeviceA-acl-ipv4-adv-3000] quit
# Create an IPsec transform set named transform1.
[DeviceA] ipsec transform-set transform1
# Use the ESP protocol for the IPsec transform set.
[DeviceA-ipsec-transform-set-transform1] protocol esp
# Specify the encryption and authentication algorithms.
[DeviceA-ipsec-transform-set-transform1] esp encryption-algorithm 3des-cbc [DeviceA-ipsec-transform-set-transform1] esp authentication-algorithm md5 [DeviceA-ipsec-transform-set-transform1] quit
# Create an IKE keychain named keychain1.
[DeviceA] ike keychain keychain1
# Specify 12345zxcvb!@#$%ZXCVB in plain text as the pre-shared key to be used with the remote peer at 2.2.2.2.
[DeviceA-ike-keychain-keychain1] pre-shared-key address 2.2.2.2 255.255.0.0 key simple 12345zxcvb!@#$%ZXCVB [DeviceA-ike-keychain-keychain1] quit
# Create an IKE profile named profile1.
[DeviceA] ike profile profile1
# Specify IKE keychain keychain1.
[DeviceA-ike-profile-profile1] keychain keychain1
# Specify that IKE negotiation operates in aggressive mode.
[DeviceA-ike-profile-profile1] exchange-mode aggressive
# Set the local identity to the FQDN name www.devicea.com.
[DeviceA-ike-profile-profile1] local-identity fqdn www.devicea.com
# Configure a peer ID with the identity type as IP address and the value as 2.2.2.2/16.
[DeviceA-ike-profile-profile1] match remote identity address 2.2.2.2 255.255.0.0 [DeviceA-ike-profile-profile1] quit
# Create an IKE-based IPsec policy entry. Specify the policy name as policy1 and set the sequence number to 1.
[DeviceA] ipsec policy policy1 1 isakmp
# Specify the remote IP address 2.2.2.2 for the IPsec tunnel.
[DeviceA-ipsec-policy-isakmp-policy1-1] remote-address 2.2.2.2
# Specify the IPsec transform set transform1 for the IPsec policy.
[DeviceA-ipsec-policy-isakmp-policy1-1] transform-set transform1
# Specify ACL 3000 to identify the traffic to be protected.
[DeviceA-ipsec-policy-isakmp-policy1-1] security acl 3000
# Specify IKE profile profile1 for the IPsec policy.
[DeviceA-ipsec-policy-isakmp-policy1-1] ike-profile profile1 [DeviceA-ipsec-policy-isakmp-policy1-1] quit
# Apply IPsec policy policy1 to interface GigabitEthernet 2/0/1.
[DeviceA] interface gigabitethernet 2/0/1 [DeviceA-GigabitEthernet2/0/1] ipsec apply policy policy1 [DeviceA-GigabitEthernet2/0/1] quit
# Configure a static route to the subnet where Host B resides. The command uses the direct next hop address (2.2.2.1) as an example.
[DeviceA] ip route-static 10.1.2.0 255.255.255.0 2.2.2.1
Configure Device B:
# Assign an IP address to each interface. (Details not shown.)
# Create IPsec transform set transform1.
<DeviceB> system-view [DeviceB] ipsec transform-set transform1
# Use the ESP protocol for the IPsec transform set.
[DeviceB-ipsec-transform-set-transform1] protocol esp
# Specify the encryption and authentication algorithms.
[DeviceB-ipsec-transform-set-transform1] esp encryption-algorithm 3des-cbc [DeviceB-ipsec-transform-set-transform1] esp authentication-algorithm md5 [DeviceB-ipsec-transform-set-transform1] quit
# Create IKE keychain keychain1.
[DeviceB]ike keychain keychain1
# Specify 12345zxcvb!@#$%ZXCVB in plain text as the pre-shared key to be used with the remote peer at 1.1.1.1. The source address of packets from 1.1.1.1 is translated into 3.3.3.1 by the NAT device, so specify the IP address of the remote peer as 3.3.3.1.
[DeviceB-ike-keychain-keychain1] pre-shared-key address 3.3.3.1 255.255.255.0 key simple 12345zxcvb!@#$%ZXCVB [DeviceB-ike-keychain-keychain1] quit
# Create an IKE profile named profile1.
[DeviceB] ike profile profile1
# Specify the IKE keychain keychain1.
[DeviceB-ike-profile-profile1] keychain keychain1
# Specify that IKE negotiation operates in aggressive mode.
[DeviceB-ike-profile-profile1] exchange-mode aggressive
# Configure a peer ID with the identity type of FQDN name and the value of www.devicea.com.
[DeviceB-ike-profile-profile1] match remote identity fqdn www.devicea.com [DeviceB-ike-profile-profile1] quit
# Create an IPsec policy template entry. Specify the template name as template1 and set the sequence number to 1.
[DeviceB] ipsec policy-template template1 1
# Specify the IPsec transform set transform1 for the IPsec policy template.
[DeviceB-ipsec-policy-template-template1-1] transform-set transform1
# Specify 2.2.2.2 as the local address of the IPsec tunnel.
[DeviceB-ipsec-policy-template-template1-1] local-address 2.2.2.2
# Specify IKE profile profile1 for the IPsec policy.
[DeviceB-ipsec-policy-template-template1-1] ike-profile profile1 [DeviceB-ipsec-policy-template-template1-1] quit
# Create an IKE-based IPsec policy entry by using IPsec policy template template1. Specify the policy name as policy1 and set the sequence number to 1.
[DeviceB] ipsec policy policy1 1 isakmp template template1
# Apply IPsec policy policy1 to interface GigabitEthernet 2/0/1.
[DeviceB] interface gigabitethernet 2/0/1 [DeviceB-GigabitEthernet2/0/1] ipsec apply policy policy1 [DeviceB-GigabitEthernet2/0/1] quit
# Configure a static route to the subnet where Host A resides. The command uses the direct next hop address (3.3.3.1) as an example.
[DeviceB] ip route-static 10.1.1.0 255.255.255.0 3.3.3.1
Verifying the configuration
# Initiate a connection from subnet 10.1.1.0/24 to subnet 10.1.2.0/24 to trigger IKE negotiation. After IPsec SAs are successfully negotiated by IKE, traffic between the two subnets is IPsec protected.
# Display the IKE SA on Device A.
[DeviceA] display ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
13 2.2.2.2 RD IPSEC
Flags:
RD--READY RL--REPLACED FD-FADING
[DeviceA] display ike sa verbose
-----------------------------------------------
Connection ID: 13
Outside VPN:
Inside VPN:
Profile: profile1
Transmitting entity: Initiator
-----------------------------------------------
Local IP: 1.1.1.1
Local ID type: FQDN
Local ID: www.devicea.com
Remote IP: 2.2.2.2
Remote ID type: IPV4_ADDR
Remote ID: 2.2.2.2
Authentication-method: PRE-SHARED-KEY
Authentication-algorithm: MD5
Encryption-algorithm: 3DES-CBC
Life duration(sec): 86400
Remaining key duration(sec): 84565
Exchange-mode: Aggressive
Diffie-Hellman group: Group 1
NAT traversal: Detected
# Display the IPsec SAs generated on Device A.
[DeviceA] display ipsec sa
-------------------------------
Interface: GigabitEthernet2/0/1
-------------------------------
-----------------------------
IPsec policy: policy1
Sequence number: 1
Mode: ISAKMP
Flow table status: Active
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect forward secrecy:
Inside VRF:
Extended Sequence Number enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1435
Tunnel:
local address: 1.1.1.1
remote address: 2.2.2.2
Flow:
sour addr: 10.1.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.2.1.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 830667426 (0x3182faa2)
Connection ID: 1
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/2313
Max received sequence-number:
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for nat traversal: Y
Status: Active
[Outbound ESP SAs]
SPI: 3516214669 (0xd1952d8d)
Connection ID: 2
Transform set: ESP-ENCRYPT-3DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/2313
Max received sequence-number:
UDP encapsulation used for nat traversal: Y
Status: Active