Aggressive mode with RSA signature authentication configuration example
This configuration example is not available when the device is operating in FIPS mode.
Network requirements
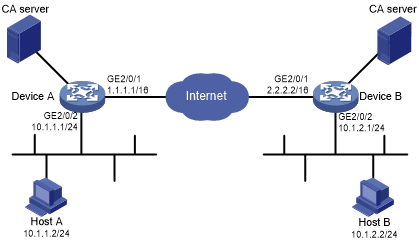
As shown in Figure 142, configure an IKE-based IPsec tunnel between Device A and Deice B to secure the communication between subnet 10.1.1.0/24 and subnet 10.1.2.0/24.
Configure Device A and Device B to use aggressive mode for IKE negotiation phase 1 and use RSA signature authentication. Device A acts as the initiator and the subnet where Device A resides uses IP addresses dynamically allocated.
Figure 137: Network diagram
Configuration procedure
Configure Device A:
# Assign an IP address to each interface. (Details not shown.)
# Configure IPv4 advanced ACL 3101 to identify traffic from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
<DeviceA> system-view [DeviceA] acl advanced 3101 [DeviceA-acl-ipv4-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255 [DeviceA-acl-ipv4-adv-3101] quit
# Create an IPsec transform set named tran1.
[DeviceA] ipsec transform-set tran1
# Set the packet encapsulation mode to tunnel.
[DeviceA-ipsec-transform-set-tran1] encapsulation-mode tunnel
# Use the ESP protocol for the IPsec transform set.
[DeviceA-ipsec-transform-set-tran1] protocol esp
# Specify the encryption and authentication algorithms.
[DeviceA-ipsec-transform-set-tran1] esp encryption-algorithm des-cbc [DeviceA-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [DeviceA-ipsec-transform-set-tran1] quit
# Create a PKI entity named entity1.
[DeviceA] pki entity entity1
# Set the common name as routera for the PKI entity.
[DeviceA-pki-entity-entity1] common-name routera [DeviceA-pki-entity-entity1] quit
# Create a PKI domain named domain1.
[DeviceA] pki domain domain1
# Set the certificate request mode to auto and set the password to 123 for certificate revocation.
[DeviceA-pki-domain-domain1] certificate request mode auto password simple 123
# Set an MD5 fingerprint for verifying the validity of the CA root certificate.
[DeviceA-pki-domain-domain1] root-certificate fingerprint md5 50c7a2d282ea710a449eede6c56b102e
# Specify the trusted CA 8088.
[DeviceA-pki-domain-domain1] ca identifier 8088
# Specify the URL of the registration server for certificate request through the SCEP protocol. This example uses http://192.168.222.1:446/eadbf9af4f2c4641e685f7a6021e7b298373feb7.
[DeviceA-pki-domain-domain1] certificate request url http://192.168.222.1:446/eadbf9af4f2c4641e685f7a6021e7b298373feb7
# Specify the CA to accept certificate requests.
[DeviceA-pki-domain-domain1] certificate request from ca
# Specify the PKI entity for certificate request as entity1.
[DeviceA-pki-domain-domain1] certificate request entity entity1
# Specify the RSA key pair rsa1 with the general purpose for certificate request.
[DeviceA-pki-domain-domain1] public-key rsa general name rsa1 [DeviceA-pki-domain-domain1] quit
# Create an IKE profile named profile1.
[DeviceA] ike profile profile1
# Specify PKI domain domain1 for the IKE profile.
[DeviceA-ike-profile-profile1] certificate domain domain1
# Specify that IKE negotiation operates in aggressive mode.
[DeviceA-ike-profile-profile1] exchange-mode aggressive
# Set the local identity to the FQDN name www.routera.com.
[DeviceA-ike-profile-profile1] local-identity fqdn www.routera.com
# Configure a peer ID with the identity type of FQDN name and the value of www.routerb.com.
[DeviceA-ike-profile-profile1] match remote identity fqdn www.routerb.com [DeviceA-ike-profile-profile1] quit
# Create an IKE proposal named 10.
[DeviceA] ike proposal 10
# Specify the authentication algorithm as HMAC-MD5.
[DeviceA-ike-proposal-10] authentication-algorithm md5
# Specify the RSA authentication method.
[DeviceA-ike-proposal-10] authentication-method rsa-signature [DeviceA-ike-proposal-10] quit
# Create an IKE-based IPsec policy entry. Specify the policy name as map1 and set the sequence number to 10.
[DeviceA] ipsec policy map1 10 isakmp
# Specify the remote IP address 2.2.2.2 for the IPsec tunnel.
[DeviceA-ipsec-policy-isakmp-map1-10] remote-address 2.2.2.2
# Specify the IPsec transform set tran1 for the IPsec policy.
[DeviceA-ipsec-policy-isakmp-map1-10] transform-set tran1
# Specify ACL 3101 to identify the traffic to be protected.
[DeviceA-ipsec-policy-isakmp-map1-10] security acl 3101
# Specify IKE profile profile1 for the IPsec policy.
[DeviceA-ipsec-policy-isakmp-map1-10] ike-profile profile1 [DeviceA-ipsec-policy-isakmp-map1-10] quit
# Apply the IPsec policy map1 to interface GigabitEthernet 2/0/1.
[DeviceA] interface gigabitethernet 2/0/1 [DeviceA-GigabitEthernet2/0/1] ipsec apply policy map1 [DeviceA-GigabitEthernet2/0/1] quit
# Configure a static route to the subnet where Host B resides. The command uses the direct next hop address (1.1.1.2) as an example.
[DeviceA] ip route-static 10.1.2.0 255.255.255.0 1.1.1.2
Configure Device B:
# Assign an IP address to each interface. (Details not shown.)
# Create an IPsec transform set named tran1.
<DeviceB> system-view [DeviceB] ipsec transform-set tran1
# Set the packet encapsulation mode to tunnel.
[DeviceB-ipsec-transform-set-tran1] encapsulation-mode tunnel
# Use the ESP protocol for the IPsec transform set.
[DeviceB-ipsec-transform-set-tran1] protocol esp
# Specify the encryption and authentication algorithms.
[DeviceB-ipsec-transform-set-tran1] esp encryption-algorithm des-cbc [DeviceB-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [DeviceB-ipsec-transform-set-tran1] quit
# Create a PKI entity named entity2.
[DeviceB] pki entity entity2
# Set the common name as routerb for the PKI entity.
[DeviceB-pki-entity-entity2] common-name routerb [DeviceB-pki-entity-entity2] quit
# Create a PKI domain named domain2.
[DeviceB] pki domain domain2
# Set the certificate request mode to auto and set the password to 123 for certificate revocation.
[DeviceB-pki-domain-domain2] certificate request mode auto password simple 123
# Set an MD5 fingerprint for verifying the validity of the CA root certificate.
[DeviceB-pki-domain-domain2] root-certificate fingerprint md5 50c7a2d282ea710a449eede6c56b102e
# Specify the trusted CA 8088.
[DeviceB-pki-domain-domain2] ca identifier 8088
# Specify the URL of the registration server for certificate request through the SCEP protocol. This example uses http://192.168.222.1:446/eadbf9af4f2c4641e685f7a6021e7b298373feb7.
[DeviceB-pki-domain-domain2] certificate request url http://192.168.222.1:446/eadbf9af4f2c4641e685f7a6021e7b298373feb7
# Specify the CA to accept certificate requests.
[DeviceB-pki-domain-domain2] certificate request from ca
# Specify the PKI entity for certificate request as entity2.
[DeviceB-pki-domain-domain2] certificate request entity entity2
# Specify the RSA key pair rsa1 with the general purpose for certificate request.
[DeviceB-pki-domain-domain2] public-key rsa general name rsa1 [DeviceB-pki-domain-domain2] quit
# Create an IKE profile named profile2.
[DeviceB] ike profile profile2
# Specify PKI domain domain2 for the IKE profile.
[DeviceB-ike-profile-profile2] certificate domain domain2
# Set the local identity to the FQDN name www.routerb.com.
[DeviceB-ike-profile-profile2] local-identity fqdn www.routerb.com
# Configure a peer ID with the identity type of FQDN name and the value of www.routera.com.
[DeviceB-ike-profile-profile2] match remote identity fqdn www.routera.com [DeviceB-ike-profile-profile2] quit
# Create an IKE proposal named 10.
[DeviceB] ike proposal 10
# Specify the authentication algorithm as HMAC-MD5.
[DeviceB-ike-proposal-10] authentication-algorithm md5
# Specify the RSA authentication method.
[DeviceB-ike-proposal-10] authentication-method rsa-signature [DeviceB-ike-proposal-10] quit
# Create an IPsec policy template entry. Specify the template name as template1 and set the sequence number to 1.
[DeviceB] ipsec policy-template template1 1
# Specify the IPsec transform set tran1 for the IPsec policy template.
[DeviceB-ipsec-policy-template-template1-1] transform-set tran1
# Specify the IKE profile profile2 for the IPsec policy template.
[DeviceB-ipsec-policy-template-template1-1] ike-profile profile2 [DeviceB-ipsec-policy-template-template1-1] quit
# Create an IKE-based IPsec policy entry by using IPsec policy template template1. Specify the policy name as use1 and set the sequence number to 1.
[DeviceB] ipsec policy use1 1 isakmp template template1
# Apply IPsec policy use1 to interface GigabitEthernet 2/0/1.
[DeviceB] interface gigabitethernet 2/0/1 [DeviceB-GigabitEthernet2/0/1] ipsec apply policy use1 [DeviceB-GigabitEthernet2/0/1] quit
# Configure a static route to the subnet where Host A resides. The command uses the direct next hop address (2.2.2.1) as an example.
[DeviceB] ip route-static 10.1.1.0 255.255.255.0 2.2.2.1
Verifying the configuration
# Initiate a connection from subnet 10.1.1.0/24 to subnet 10.1.2.0/24 to trigger IKE negotiation. After IPsec SAs are successfully negotiated by IKE, traffic between the two subnets is IPsec protected.
# Display the IKE proposal configuration on Device A and Device B.
[DeviceA] display ike proposal
Priority Authentication Authentication Encryption Diffie-Hellman Duration
method algorithm algorithm group (seconds)
----------------------------------------------------------------------------
10 RSA-SIG MD5 AES-CBC-128 Group 1 86400
default PRE-SHARED-KEY SHA1 AES-CBC-128 Group 1 86400
[DeviceB] display ike proposal
Priority Authentication Authentication Encryption Diffie-Hellman Duration
method algorithm algorithm group (seconds)
----------------------------------------------------------------------------
10 RSA-SIG MD5 AES-CBC-128 Group 1 86400
default PRE-SHARED-KEY SHA1 AES-CBC-128 Group 1 86400
# Display the IKE SA on Device A.
[DeviceA] display ike sa
Connection-ID Remote Flag DOI
------------------------------------------------------------------
1 2.2.2.2 RD IPSEC
Flags:
RD--READY RL--REPLACED FD-FADING
# Display information about the CA certificate on Device A.
[DeviceA] display pki certificate domain domain1 ca
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
b9:14:fb:25:c9:08:2c:9d:f6:94:20:30:37:4e:00:00
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=cn, O=rnd, OU=sec, CN=8088
Validity
Not Before: Sep 6 01:53:58 2012 GMT
Not After : Sep 8 01:50:58 2015 GMT
Subject: C=cn, O=rnd, OU=sec, CN=8088
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:de:81:f4:42:c6:9f:c2:37:7b:21:84:57:d6:42:
00:69:1c:4c:34:a4:5e:bb:30:97:45:2b:5e:52:43:
c0:49:1f:e1:d8:0f:5c:48:c2:39:69:d1:84:e4:14:
70:3d:98:41:28:1c:20:a1:9a:3f:91:67:78:77:27:
d9:08:5f:7a:c4:36:45:8b:f9:7b:e7:7d:6a:98:bb:
4e:a1:cb:2c:3d:92:66:bd:fb:80:35:16:c6:35:f0:
ff:0b:b9:3c:f3:09:94:b7:d3:6f:50:8d:83:f1:66:
2f:91:0b:77:a5:98:22:b4:77:ac:84:1d:03:8e:33:
1b:31:03:78:4f:77:a0:db:af
Exponent: 65537 (0x10001)
Signature Algorithm: sha1WithRSAEncryption
9a:6d:8c:46:d3:18:8a:00:ce:12:ee:2b:b0:aa:39:5d:3f:90:
08:49:b9:a9:8f:0d:6e:7b:e1:00:fb:41:f5:d4:0c:e4:56:d8:
7a:a7:61:1d:2b:b6:72:e3:09:0b:13:9d:fa:c8:fc:c4:65:a7:
f9:45:21:05:75:2c:bf:36:7b:48:b4:4a:b9:fe:87:b9:d8:cf:
55:16:87:ec:07:1d:55:5a:89:74:73:68:5e:f9:1d:30:55:d9:
8a:8f:c5:d4:20:7e:41:a9:37:57:ed:8e:83:a7:80:2f:b8:31:
57:3a:f2:1a:28:32:ea:ea:c5:9a:55:61:6a:bc:e5:6b:59:0d:
82:16
# Display the local certificate on Device A.
[DeviceA] display pki certificate domain domain1 local
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
a1:f4:d4:fd:cc:54:c3:07:c4:9e:15:2d:5f:64:57:77
Signature Algorithm: sha1WithRSAEncryption
Issuer: C=cn, O=rnd, OU=sec, CN=8088
Validity
Not Before: Sep 26 02:06:43 2012 GMT
Not After : Sep 26 02:06:43 2013 GMT
Subject: CN=devicea
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:b0:a1:cd:24:6e:1a:1d:51:79:f0:2a:3e:9f:e9:
84:07:16:78:49:1b:7d:0b:22:f0:0a:ed:75:91:a4:
17:fd:c7:ef:d0:66:5c:aa:e3:2a:d9:71:12:e4:c6:
25:77:f0:1d:97:bb:92:a8:bd:66:f8:f8:e8:d5:0d:
d2:c8:01:dd:ea:e6:e0:80:ad:db:9d:c8:d9:5f:03:
2d:22:07:e3:ed:cc:88:1e:3f:0c:5e:b3:d8:0e:2d:
ea:d6:c6:47:23:6a:11:ef:3c:0f:6b:61:f0:ca:a1:
79:a0:b1:02:1a:ae:8c:c9:44:e0:cf:d1:30:de:4c:
f0:e5:62:e7:d0:81:5d:de:d3
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 CRL Distribution Points:
Full Name:
URI:http://xx.rsa.com:447/8088.crl
Signature Algorithm: sha1WithRSAEncryption
73:ac:66:f9:b8:b5:39:e1:6a:17:e4:d0:72:3e:26:9e:12:61:
9e:c9:7a:86:6f:27:b0:b9:a3:5d:02:d9:5a:cb:79:0a:12:2e:
cb:e7:24:57:e6:d9:77:12:6b:7a:cf:ee:d6:17:c5:5f:d2:98:
30:e0:ef:00:39:4a:da:ff:1c:29:bb:2a:5b:60:e9:33:8f:78:
f9:15:dc:a5:a3:09:66:32:ce:36:cd:f0:fe:2f:67:e5:72:e5:
21:62:85:c4:07:92:c8:f1:d3:13:9c:2e:42:c1:5f:0e:8f:ff:
65:fb:de:7c:ed:53:ab:14:7a:cf:69:f2:42:a4:44:7c:6e:90:
7e:cd
# Display the IPsec SA information on Device A.
[DeviceA] display ipsec sa
-------------------------------
Interface: GigabitEthernet2/0/1
-------------------------------
-----------------------------
IPsec policy: map1
Sequence number: 10
Mode: ISAKMP
Flow table status: Active
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect forward secrecy:
Inside VRF:
Extended Sequence Number enable: N
Traffic Flow Confidentiality enable: N
Path MTU: 1456
Tunnel:
local address: 1.1.1.1
remote address: 2.2.2.2
Flow:
sour addr: 10.1.1.0/255.255.255.0 port: 0 protocol: ip
dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3264152513 (0xc28f03c1)
Connection ID: 1
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3484
Max received sequence-number:
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 738451674 (0x2c03e0da)
Connection ID: 2
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3484
Max received sequence-number:
UDP encapsulation used for NAT traversal: N
Status: Active
# Display the information about the CA certificate, local certificate, IKE SA, and IPsec SA on Device B.
[DeviceB] display ike sa [DeviceB] display pki certificate domain domain2 ca [DeviceB] display pki certificate domain domain2 local [DeviceB] display ipsec sa