The show commands in this section apply to both IPv4 and IPv6 ACLs. For information on IPv6 ACL operation, see the chapter titled “IPv6 Access Control Lists” in the IPv6 Configuration Guide for your switch.
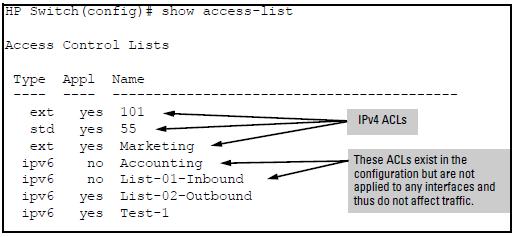
This command lists the configured IPv4 and IPv6 ACLs, regardless of whether they are assigned to any VLANs.
Syntax:
This command lists the configuration details for the IPv4 and IPv6 ACLs in the running-config file, regardless of whether any are actually assigned to filter IPv4 traffic on specific VLANs.
Syntax:
For example, with two ACLs configured in the switch, you will see results similar to the following:
An ACL configured syntax listing
HP Switch(config)# show access-list config ip access-list standard "List-43" 10 deny 10.28.236.77 0.0.0.0 20 deny 10.29.140.107 0.0.0.0 30 permit 0.0.0.0 255.255.255.255 exit ip access-list extended "111" 10 permit tcp 10.30.133.27 0.0.0.0 0.0.0.0 255.255.255.255 20 permit tcp 10.30.155.101 0.0.0.0 0.0.0.0 255.255.255.255 30 deny ip 10.30.133.1 0.0.0.0 0.0.0.0 255.255.255.255 log 40 deny ip 10.30.155.1 0.0.0.255 0.0.0.0 255.255.255.255 exit
This command briefly lists the identification andtypes of IPv4 and IPv6 VACLs currently assigned to a particular VLAN in the running-config file. For IPv6, the switch supports, per-VLAN, one VACL assignment.
Syntax:
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This information also appears in the |
|
|
This command lists the identification and types of current static port ACL assignments to individual switch ports and trunks, as configured in the running-config file. The switch allows one static port ACL assignment per port.
Syntax:
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This information also appears in the |
|
|
For example, if you assigned a standard ACL with an ACL-ID of “Port-10” to filter inbound IP traffic on switch ports B10-B11 and trunk trk1, you could verify these assignments as shown in Listing the ACL assignments for ports and trunks.
This command displays a specific ACL configured in the running config file in an easy-to-read tabular format.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This information also appears in the |
|
|
Syntax:
Displays detailed information on the content of a specific ACL configured in the running-config file.
For example, suppose you configured the following two ACLs in the switch:
| ACL ID | Type | Desired Action |
|---|---|---|
| 1 | Standard |
|
| 105 | Extended |
|
Descriptions of data types included in show access-list <acl-id> output
| Field | Description |
|---|---|
| Name | The ACL identifier. Can be a number from 1 to 199, or a name. |
| Type | Standard or Extended. The former uses only source IPv4 addressing. The latter uses both source and destination IPv4 addressing and also allows TCP or UDP port specifiers. |
| Applied | "Yes" means the ACL has been applied to a port or VLAN interface. "No" means the ACL exists in the switch configuration, but has not been applied to any interface, and is therefore not in use. |
| SEQ | The sequential number of the Access Control Entry (ACE) in the specified ACL. |
| Entry | Lists the content of the ACEs in the selected ACL. |
| Action | Permit (forward) or deny (drop) a packet when it is compared to the criteria in the applicable ACE and found to match. Includes the optional log option, if used, in deny actions. |
| Remark | Displays any optional remark text configured for the selected ACE. |
| IP |
Used for Standard ACLs: The source IPv4 address to which the configured mask is applied to determine whether there is a match with a packet. |
| Src IP |
Used for Extended ACLs: Same as above. |
| Dst IP |
Used for Extended ACLs: The source and destination IPv4 addresses to which the corresponding configured masks are applied to determine whether there is a match with a packet. |
| Mask | The mask configured in an ACE and applied to the corresponding IPv4 address in the ACE to determine whether a packet matches the filtering criteria. |
| Proto | Used only in extended ACLs to specify the packet protocol type to filter. Must be either IPv4, TCP, or UDP. For TCP protocol selections, includes the established option, if configured. |
| Port(s) | Used only in extended ACLs to show any TCP or UDP operator and port number(s) included in the ACE. |
| TOS | Used only in extended ACLs to indicate Type-of-Service setting, if any. |
| Precedence | Used only in extended ACLs to indicate the IP precedence setting, if any. |
The show config and show running commands include in their listings any configured ACLs and any ACL assignments to VLANs. See ACL configuration factors. Remember that show config lists the startup-config file and show running lists the running-config file.