While the Event Log records switch-level progress, status, and warning messages on the switch, the debug/system logging (syslog) feature provides a way to record Event Log and debug messages on a remote device. For example, you can send messages about routing misconfigurations and other network protocol details to an external device, and later use them to debug network-level problems.
The debug/syslog feature allows you to specify the types of Event Log and debug messages that you want to send to an external device. You can perform the following operations:
The syslog now messages the sender identified by hostname.
The hostname field identifies the switch that originally sends the syslog message. Configurable through the CLI and SNMP, the format of the hostname field supports the following formats:
-
ip-address: The IP address of the sending interface will be used as the message origin identifier. This is the default format for the origin identifier. The IP address of the sending interface (in dotted decimal notation) is the default format.
-
hostname: The hostname of the sending switch will be used as the message origin identifier.
-
none: No origin identifier will be embedded in the syslog message. Nilvalue is used as defined by “-“.
This configuration is system-wide, not per syslog server.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: There is no support in this feature for menu interface, WebUI or a fully qualified domain name. There are no changes in this feature to PCM or IDM. There are no new log events added in this feature. |
|
|
Use the logging origin-id command to specify the content for the hostname field.
Syntax:
To reset the hostname field content back to default (IP-address), use the
noform of the command.Add an IP address to the list of receiving syslog servers.
Use of
nowithout an IP address specified will remove all IP addresses from the list of syslog receivers. If an IP address is specified, that receiver will be removed. Both link-local with zone ID and global IPv6 addresses are supported.
Specify syslog server facility with the option <
facility>. The commandno logging <facility>sets the facility back to defaults.Specify severity for event messages to be filtered to the syslog server with the option <
severity>. The commandno logging <severity>sets the severity back to default.Event messages of specified system module will be sent to the syslog server. Using
nosends messages from all system modules. Messages are first filtered by selected severity.Specify syslog server transport layer with options
[udp]|[tcp]|[tls].Specify syslog server port number with options
[udp PORT-NUM]|[tcp PORT-NUM]|[tls PORT-NUM].Use the option
transmission-intervalto control the egress rate limit for transmitting notifications, 0 value means there is no rate limit. The values are in seconds. Only one syslog message is allowed for transmission within specified time interval.Specify the origin information for the syslog messages with the option
origin-id.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: When the syslog server receives messages from the switch, the IPv6 address of the switch is partly displayed. Example: |
|
|
Use the command in Setting the origin-id to the hostname to set the origin-id to the hostname.
The following syslog message will occur:
Use the command in Setting the origin-id to none (nilvalue) to set the origin-id to none (nilvalue).
The following syslog message will occur:
Use any of the commands in Setting the origin-id to ip-address (default) to set the origin-id to ip-address (default).
Use the commands show debug or show running-config to display the identification of the syslog message sender. The default option for origin-id is ip-address. The command show running-config will not display the configured option when origin-id is set to the default value of ip address.
When hostname or none is configured using logging origin-id, the same displays as part of the show running-config command.
Syntax:
Output of the show debug command when configured without login origin-id shows the output of the show debug command when configured without loggin origin-id.
Output of the show debug command when configured without login origin-id
Debug Logging Origin identifier: Outgoing Interface IP Destination: None Enabled debug types: None are enabled.
The command logging origin-id hostname will produce the syslog message shown in Syslog message for logging origin-id hostname.
Syslog message for logging origin-id hostname
Debug Logging Origin identifier: Hostname Destination: None Enabled debug types: None are enabled.
The command logging origin-id none will produce the syslog message shown in Syslog message for logging origin-id none.
Syslog message for logging origin-id none
Debug Logging Origin identifier: none Destination: None Enabled debug types: None are enabled.
Syntax:
Output of the show running-config command shows the output of the show running-config command.
Output of the show running-config command
The command logging
origin-id hostname will display the
following:
logging origin-id hostname
The command logging origin-id none will display as the following:
To use debug/syslog messaging, you must configure an external device as the logging destination by using the logging and debug destination commands. For more information, see Debug destinations and Configuring a syslog server.
A debug/syslog destination device can be a syslog server and/or a console session. You can configure debug and logging messages to be sent to:
Using the Debug/Syslog feature, you can perform the following operations:
-
Configure the switch to send Event Log messages to one or more Syslog servers. In addition, you can configure the messages to be sent to the User log facility (default) or to another log facility on configured Syslog servers.
-
Configure the switch to send Event Log messages to the current management- access session (serial-connect CLI, Telnet CLI, or SSH).
-
Disable all Syslog debug logging while retaining the Syslog addresses from the switch configuration. This allows you to configure Syslog messaging and then disable and re-enable it as needed.
-
Display the current debug configuration. If Syslog logging is currently active, the list f configured Syslog servers is displayed.
-
Display the current Syslog server list when Syslog logging is disabled.
-
To use a syslog server as the destination device for debug messaging, follow these steps:
-
Enter the
loggingcommand at the global configuration level to configure the syslog server IP address and enable syslog logging. Optionally, you may also specify the destination subsystem to be used on the syslog server by entering the<syslog-ip-addr>logging facilitycommand.If no other syslog server IP addresses are configured, entering the
loggingcommand enables both debug messaging to a syslog server and the event debug message type. As a result, the switch automatically sends Event Log messages to the syslog server, regardless of other debug types that may be configured. -
Re-enter the
loggingcommand in step "a" to configure additional syslog servers. You can configure up to a total of six servers. (When multiple server IP addresses are configured, the switch sends the debug message types that you configure in step “Step 3” to all IP addresses.)
-
-
To use a CLI session on a destination device for debug messaging:
-
Enable the types of debug messages to be sent to configured syslog servers, the current session device, or both by entering the
debug <command and selecting the desired options.debug-type>Repeat this step if necessary to enable multiple debug message types.
By default, Event Log messages are sent to configured debug destination devices. To block Event Log messages from being sent, enter the
no debug eventcommand. -
If necessary, enable a subset of Event Log messages to be sent to configured syslog servers by specifying a severity level, a system module, or both using the following commands
HP Switch(config)# logging severity <debug | major | error | warning | info> HP Switch(config)# logging system-module
<system-module>To display a list of valid values for each command, enter
logging severityorlogging system-modulefollowed by?or pressing the Tab key.The severity levels in order from the highest to lowest severity are major, error, warning, info, and debug. For a list of valid values for the
logging system-module <command, see Event Log system modules .system-module> -
If you configure system-module, severity-level values, or both to filter Event Log messages, when you finish troubleshooting, you may want to reset these values to their default settings so that the switch sends all Event Log messages to configured debug destinations (syslog servers, CLI session, or both).
To remove a configured setting and restore the default values that send all Event Log messages, enter one or both of the following commands:
HP Switch(config)# no logging severity <debug | major | error | warning | info> HP Switch(config)# no logging system-module
<system-module>
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: If you configure a severity-level, system-module, logging destination, or logging facility value and save the settings to the startup configuration (For example, by entering the |
|
|
Use the show debug command to display the currently configured settings for:
Syntax:
Displays the currently configured debug logging destinations and message types selected for debugging purposes. (If no syslog server address is configured with the
logging <command, nosyslog-ip-addr>show debugcommand output is displayed.)
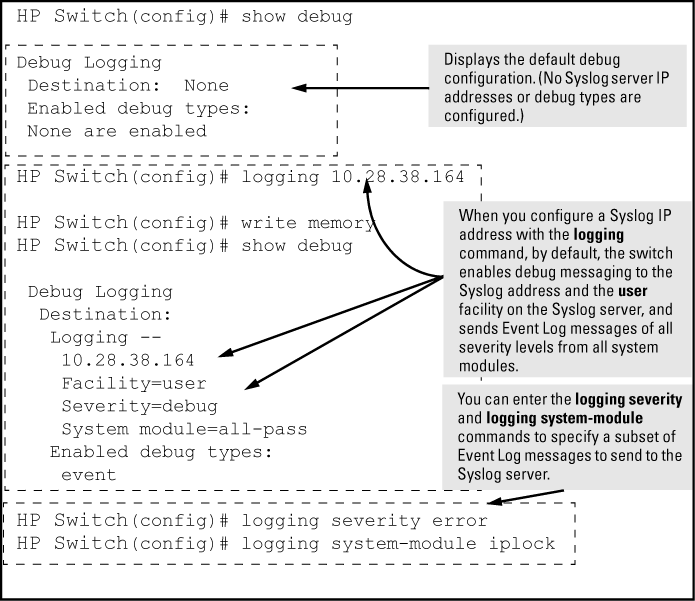
Output of the show debug command
HP Switch(config)# show debug
Debug Logging
Destination:
Logging --
10.28.38.164
Facility=kern
Severity=warning
System module=all-pass
Enabled debug types:
event
Example:
In the following Example:, no syslog servers are configured on the switch (default setting). When you configure a syslog server, debug logging is enabled to send Event Log messages to the server. To limit the Event Log messages sent to the syslog server, specify a set of messages by entering the
logging severityandlogging system-modulecommands.As shown at the top of Syslog configuration to receive event log messages from specified system module and severity levels, if you enter the
show debugcommand when no syslog server IP address is configured, the configuration settings for syslog server facility, Event Log severity level, and system module are not displayed. However, after you configure a syslog server address and enable syslog logging, all debug and logging settings are displayed with theshow debugcommand.If you do not want Event Log messages sent to syslog servers, you can block the messages from being sent by entering the
no debug eventcommand. (There is no effect on the normal logging of messages in the switch's Event Log.)
Example:
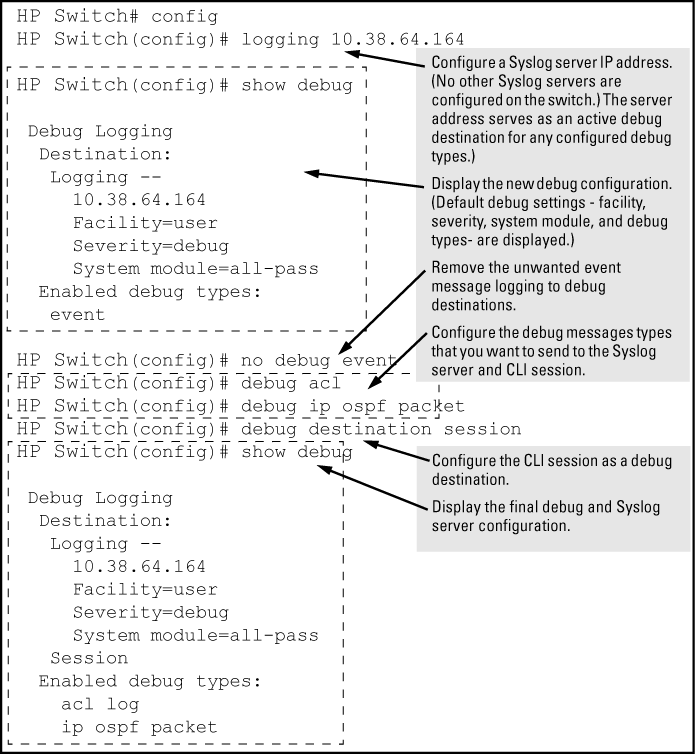
The next Example: shows how to configure:
Debug logging of ACL and IP-OSPF packet messages on a syslog server at 18.38.64.164 (with user as the default logging facility).
Display of these messages in the CLI session of your terminal device's management access to the switch.
Blocking Event Log messages from being sent from the switch to the syslog server and a CLI session.
To configure syslog operation in these ways with the debug/syslog feature disabled on the switch, enter the commands shown in Debug/syslog configuration for multiple debug types and multiple destinations.
At the manager level, use the debug command to perform two main functions:
By default, no debug destination is enabled and only Event Log messages are enabled to be sent.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: To configure a syslog server, use the |
|
|
Syntax:
Debug message filtering provides the ability to filter debug messages by debug type. Multiple debug filters can be applied to a debug type.
Syntax:
[no]
debug <[debug type> includeip ip-addr list|port <|port-list>vlan <]vid-list>
Enables or disables debug message filtering for a debug type. The filter types are:
IPv4 or IPv6 address list Port list VLAN list
Setting an SNMP event filter for an IP address
HP Switch(config)# debug snmp event include ip 10.10.10.1 HP Switch(config)# show debug Debug Logging Destination: Session Enabled debug types: snmp trap include ip 10.10.10.1
Use the debug destination command to enable (and disable)syslog messaging on a syslog server or to a CLI session for specified types of debug and Event Log messages.
Syntax:
loggingEnables syslog logging to configured syslog servers so that the debug message types specified by the
debug <command (see Debug messages) are sent.debug-type>(Default: Logging disabled)
To configure a syslog server IP address, see Configuring a syslog server.
NOTE: Debug messages from the switches covered in this guide have a debug severity level. Because the default configuration of some syslog servers ignores syslog messages with the debug severity level, ensure that the syslog servers you want to use to receive debug messages are configured to accept the debug level. For more information, see Operating notes for debug and Syslog.
sessionEnables transmission of event notification messages to the CLI session that most recently executed this command. The session can be on any one terminal emulation device with serial, Telnet, or SSH access to the CLI at the Manager level prompt (
HP Switch#_).If more than one terminal device has a console session with the CLI, you can redirect the destination from the current device to another device. Do so by executing
debug destination sessionin the CLI on the terminal device on which you now want to display event messages.Event message types received on the selected CLI session are configured with the
debug <command.debug-type>bufferEnables syslog logging to send the debug message types specified by the
debug <command to a buffer in switch memory.debug-type>To view the debug messages stored in the switch buffer, enter the
show debug buffercommand.
At the global configuration level, the loggingcommand allows you to enable debug logging on specified syslog servers and select a subset of Event Log messages to send for debugging purposes according to:
By specifying both a severity level and system module, you can use both configured settings to filter the Event Log messages you want to use to troubleshoot switch or network error conditions.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: After you configure a syslog server and a severity level and/or system module to filter the Event Log messages that are sent, if you save these settings to the startup configuration file by entering the After a reboot, messages remain in the Event Log and are not deleted. However, after a power recycle, all Event Log messages are deleted. If you configure a severity level, system module, or both to temporarily filter Event Log messages, be sure to reset the values to their default settings by entering the
HP Switch(config)# no logging severity <debug | major | error | warning | info>
HP Switch(config)# no logging system-module <
|
|
|
Syslog is a client-server logging tool that allows a client switch to send event notification messages to a networked device operating with syslog server software. Messages sent to a syslog server can be stored to a file for later debugging analysis.
To use the syslog feature, you must install and configure a syslog server application on a networked host accessible to the switch. For instructions, see the documentation for the syslog server application.
To configure a syslog service, use the logging < command as shown below.syslog-ip-addr>
When you configure a syslog server, Event Log messages are automatically enabled to be sent to the server. To reconfigure this setting, use the following commands:
-
Specifies additional debug message types (see Debug messages).
-
Configures the system module or severity level used to filter the Event Log messages sent to configured syslog servers. (See Configuring the severity level for Event Log messages sent to a syslog server and Configuring the system module used to select the Event Log messages sent to a syslog server.)
To display the currently configured syslog servers as well as the types of debug messages and the severity-level and system-module filters used to specify the Event Log messages that are sent, enter the show debug command (See Debug/syslog configuration commands).
Syntax:
Enables or disables syslog messaging to the specified IP address. You can configure up to six addresses. If you configure an address when none are already configured, this command enables destination logging (syslog) and the Event debug type. Therefore, at a minimum, the switch begins sending Event Log messages to configured syslog servers. The ACL, IP-OSPF, and/or IP-RIP message types are also sent to the syslog servers if they are currently enabled as debug types. (See Debug messages.)
no loggingRemoves all currently configured syslog logging destinations from the running configuration.
Using this form of the command to delete the only remaining syslog server address disables debug destination logging on the switch, but the default Event debug type does not change.
no logging <syslog-ip-address>Removes only the specified syslog logging destination from the running configuration.
Removing all configured syslog destinations with the
no loggingcommand (or a specified syslog server destination with theno logging <command) does not delete the syslog server IP addresses stored in the startup configuration.syslog-ip-address>
Enter the no debug < command. (See Debug messages.)debug-type>
Enter the no debug destination logging command. Note that, unlike the case in which no syslog servers are configured, if one or more syslog servers are already configured and syslog messaging is disabled, configuring a new server address does not re-enable syslog messaging. To re-enable syslog messaging, you must enter the debug destination logging command.
Syntax:
Allows the configuration of the UDP or TCP transport protocol for the transmission of logging messages to a syslog server.
Specifying a destination port with UDP or TCP is optional.
Default ports: UDP port is 514
Default Transport Protocol: UDP
Because TCP is a connection-oriented protocol, a connection must be present before the logging information is sent. This helps ensure that the logging message will reach the syslog server. Each configured syslog server needs its own connection. You can configure the destination port that is used for the transmission of the logging messages.
Configuring TCP for logging message transmission using the default port
HP Switch(config)# logging 192.123.4.5 tcpConfiguring TCP for logging message transmission using a specified port
HP Switch(config)# logging 192.123.4.5 9514
Syntax:
The logging facility specifies the destination subsystem used in a configured syslog server. (All configured syslog servers must use the same subsystem.) HP recommends the default (user) subsystem unless your application specifically requires another subsystem. Options include:
user(default) Random user-level messages
kernKernel messages
Mail system
daemonSystem daemons
authSecurity/authorization messages
syslogMessages generated internally by syslog
lprLine-printer subsystem
newsNetnews subsystem
uucpuucp subsystem
croncron/at subsystem
sys9cron/at subsystem
sys10 - sys14Reserved for system use
local10 - local17Reserved for system use
Use the
noform of the command to remove the configured facility and reconfigure the default (user) value.
This feature provides a per-port basis filter that can restrict the logging of events that are associated with a link status change. Unimportant linkup/linkdown events can be filtered out, avoiding unwanted messages in the event log and reducing troubleshooting time.
The specific port-based events to be controlled are:
RMON_PMGR_PORT_UP—Indicates that the port has changed from and off-line to an on-line state. To be online the port must be both connected to the LAN and enabled through configuration.
RMON_PMGR_PORT_DOWN—Indicates that the port has changed from an on-line state to an offline state. For this state to occur, the port is physically disconnected from the LAN, disabled through the configuration, or both.
-
A filter is identified by a unique name of up to 16 printable ASCII characters.
-
Filters can be dynamically replaced; the newly enabled filter automatically disables the previous filter.
-
A filter always contains a default sub-filter that functions as the filtering rules terminator.
-
To apply filtering to an event logging process, the filter must be explicitly enabled from the CLI.
-
Enabled filter modules can be dynamically modified; the changes will take effect immediately.
A filter module may include up to 19 option sub-filters and a default sub-filter. The sub-filter types are:
A sub-filter has a sequence number, criteria to be matched, and a resulting action when a match occurs. All of the parameters must be specified in order to create the sub-filter.
The following sub-filter rules apply:
-
Up to 19 optional sub-filters and a default sub-filter are allowed in a filter module.
-
Sub-filters in the filter module can be of the same or different types.
-
Sub-filter entries can be modified with new criteria and action definitions.
-
Sub-filters are executed from the lowest sequence number to the highest. As soon as a match is found the log event is immediately accepted or rejected and no further matching operation is performed.
-
The default sub-filter must always be the last entry in a filter module. It functions as the rules terminator when the criteria matching performed by the prior sub-filters in a filter does not produce an action.
-
The default sub-filter cannot be deleted, re-ordered, or changed. The only parameter that can be modified is the action parameter of permit or deny. The default is permit.
Creates a logging filter to restrict which events are logged. The no form of the command removes the logging filter.
<name>: The name that identifies the filter.
severity <severity>: Specifies the severity of an event—major, warning, error, info, or debug.
event-num <num>: Specifies an event number to match.
deny: If the log entry matches the specified criteria, do not log the event message. No further criteria are evaluated for a match.
permit: If the log entry matches the specified criteria, log the event message. No further criteria are evaluated for a match.
Enables a log filter. Only one filter can be enabled at a time. An enabled filter automatically disables a previously enabled filter.
Displays the logging filter’s configuration information. The Matches column indicates the number of times that criteria has matched.
Specifying the criteria for a filter and then enabling the filter
HP Switch(config)# logging filter SevWarnFatal 10 severity warning permit HP Switch(config)# logging filter SevWarnFatal 20 severity major permit HP Switch(config)# logging filter SevWarnFatal default deny HP Switch(config)# logging filter SevWarnFatal enable
-
The filter named SevWarnFatal adds a sub-filter of the severity type, with a sequence number of 10. The sub-filter specifies that a match for an event log message with a severity of “warning” will be logged.
-
The second sub-filter has a sequence number of 20 and a severity type of major. The sub-filter specifies that a match for an event log message with a severity of “major” will be logged.
-
The default sub-filter, which is created automatically at the time of filter creation, is always the last entry in the filter module. It matches “anything” and cannot be changed. You can change the actions to either permitor deny. This example specifies that any message that did not meet the prior matching criteria will not be logged.
-
The last command enables the filter named SevWarnFatal. If there was another filter enabled, this filter automatically replaces it and the other filter is disabled.
Specifying the criteria for a filter named noUpDownEvents and then enabling the filter
HP Switch(config)# logging filter noUpDownEvent 10 event-num 76 deny HP Switch(config)# logging filter noUpDownEvent 20 event-num 77 deny HP Switch(config)# logging filter noUpDownEvent default permit HP Switch(config)# logging filter noUpDownEvent enable
-
The filter named noUpDownEvents adds a sub-filter with a type of event-num, and a sequence number of 10. The sub-filter specifies that a match for an event log message with an event number of “76” will not be logged.
-
The second sub-filter has a sequence number of 20 and a type of event-num. The sub-filter specifies that a match for an event log message with an event number of “77” will not be logged.
-
The default sub-filter, which is created automatically at the time of filter creation, is always the last entry in the filter module. It matches “anything” and cannot be changed. You can change the actions to either permit or deny. This example specifies that any message that did not meet the prior matching criteria will be logged.
-
The last command enables the filternamednoUpDownEvents. If there was another filter enabled, this filter automatically replaces it and the other filter is disabled.
Specifying the criteria for a match using a regular expression and then enabling the filter
HP Switch(config)# logging filter noUpPorts 10 "(A10|A22|B5) is now on-line" deny HP Switch(config)# logging filter noUpPorts default permit HP Switch(config)# logging filter noUpPorts enable
This example denies logging of the matching regular expression “port <port-num> is now on-line” for ports A10, A22, and B5.
-
The filter named noUpPorts adds a sub-filter with a type of regular expression for ports A10, A22, and B5. The sub-filter specifies the matching criteria for the regular expression and if there is a match, the event log message is not logged.
-
The default sub-filter specifies that any message that did not meet the prior matching criteria will be logged.
Specifying the criteria for a match using a regular expression for specific ports
HP Switch(config)# logging filter noStpBlockPorts 10 "(A[1-9]|A10|B[1-4]) .*Blocked by STP" permit HP Switch(config)# logging filter noStpBlockPorts 20 " .*Blocked by STP" deny HP Switch(config)# logging filter noStpBlockPorts default permit HP Switch(config)# logging filter noStpBlockPorts enable
-
The filter named noStpBlockPorts adds a sub-filter with a type of regular expression with a sequence number of 10. This rule specifies that event messages from ports A1-A10, and B1-B4 with the “.*Blocked by STP” expression pattern in the message body are logged.
-
The second command adds a sub-filter with a type of regular expression and a sequence number of 20. This rule specifies that event messages generated from any ports with the “.*Blocked by STP” expression pattern in the message body are not logged.
-
The default sub-filter specifies that any message that did not meet the prior matching criteria will be logged.
The configured logging filters
HP Switch# show logging filter Status and Counters - Log Filters Information Name Enabled --------------- ------- noUpPorts No SevWarnFatal No noUpDownEvents No noStpBlockPorts Yes
Output for specified logging filters
HP Switch# show logging filter sevWarnFatal Status and Counters - Log Filters Information Name : Enabled Enabled : Yes Messages Dropped : 0 Seq Type Value Action Matches --- -------- ---------------------------------- ------ ------- 10 Severity warning Permit 2 20 Severity major Permit 2 def (any) Deny 0 HP Switch(config)# show logging filter noStpBlockPorts Status and Counters - Log Filters Information Name : noStpBlockPorts Enabled : Yes Messages Dropped : 0 Seq Type Value Action Matches --- -------- ----------------------------------- ------ ------- 10 RegExp (A[1-9]|A10|B[1-4]).*Blocked by STP Permit 2 20 RegExp .*Blocked by STP Deny 2 def (any) Permit 0
Output of running-config file
HP Switch# show running-config Running configuration: ; J9470A Configuration Editor; Created on release #XX.15.13.0000x ; Ver #04:0f.ff.3f.ef:24 hostname "HP Switch" module 1 type j94dda logging filter "noUpPorts" 10 "(A10|A22|B5) is now on-line" deny logging filter "noUpPorts" default permit logging filter "SevWarnFatal" 10 severity warning permit logging filter "SevWarnFatal" 20 severity major permit logging filter "SevWarnFatal" default deny logging filter "noUpDownEvent" 10 event-num 76 deny logging filter "noUpDownEvent" 20 event-num 77 deny logging filter "noUpDownEvent" default permit logging filter "noStpBlockPorts" 10 "(A[1-9]|A10|B[1-4]) .*Blocked by STP" permit logging filter "noStpBlockPorts" 20 " .*Blocked by STP" deny logging filter "noStpBlockPorts" default permit logging filter "noStpBlockPorts" enable snmp-server community "public" unrestricted snmp-server host 15.255.133.156 community "public" snmp-server host 15.255.133.146 community "public" vlan 1 . . .
You can associate a user-friendly description with each of the IP addresses (IPv4 only) configured for syslog using the CLI or SNMP.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The HP enterprise MIB hpicfSyslog.mib allows the configuration and monitoring of syslog for SNMP (RFC 3164 supported). |
|
|
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Entering the |
|
|
Syntax:
An optional user-friendly description that can be associated with a server IP address. If no description is entered, this is blank. If <
text_string> contains white space, use quotes around the string. IPv4 addresses only.Use the
noform of the command to remove the description. Limit: 255 characters
NOTE: To remove the description using SNMP, set the description to an empty string.
This description can be added with the CLI or SNMP. The CLI command is:
Syntax:
Provides a user-friendly description for the combined filter values of
severityandsystem module. If no description is entered, this is blank.If
text_stringcontains white space, use quotes around the string.
The logging command with a priority description
HP Switch(config)# logging priority-descr severe-pri
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: A notification is sent to the SNMP agent if there are any changes to the syslog parameters, either through the CLI or with SNMP. |
|
|
Event Log messages are entered with one of the following severity levels (from highest to lowest):
|
|
A fatal error condition has occurred on the switch. |
|
|
An error condition has occurred on the switch. |
|
|
A switch service has behaved unexpectedly. |
|
|
Information on a normal switch event. |
|
|
Reserved for HP switch internal diagnostic information. |
Using the logging severity command, you can select a set of Event Log messages according to their severity level and send them to a syslog server. Messages of the selected and higher severity will be sent. To configure a syslog server, see Configuring a syslog server.
Syntax:
[no]
logging severity<major|error|warning|info|debug>
Configures the switch to send all Event Log messages with a severity level equal to or higher than the specified value to all configured Syslog servers.
Default:
debug(Reports messages of all severity levels.)Use the
noform of the command to remove the configured severity level and reconfigure the default value, which sends Event Log messages of all severity levels to syslog servers.
NOTE: The severity setting does not affect event notification messages that the switch normally sends to the Event Log. All messages remain recorded in the Event Log.
Event Log messages contain the name of the system module that reported the event. Using the logging system-module command, you can select a set of Event Log messages according to the originating system module and send them to a syslog server.
Syntax:
Configures the switch to send all Event Log messages being logged from the specified system module to configured syslog servers. (To configure a syslog server, see Configuring a syslog server.)
See Event Log system modules for the correct value to enter for each system module.
Default:
all-pass(Reports all Event Log messages.)Use the
noform of the command to remove the configured system module value and reconfigure the default value, which sends Event Log messages from all system modules to syslog servers.You can select messages from only one system module to be sent to a syslog server; you cannot configure messages from multiple system modules to be sent. If you re-enter the command with a different system module name, the currently configured value is replaced with the new one.
NOTE: This setting has no effect on event notification messages that the switch normally sends to the Event Log.
-
Rebooting the switch or pressing the
Resetbutton resets the debug configuration.Debug option
Effect of a reboot or reset
logging (debug destination)
If syslog server IP addresses are stored in the startup-config file, they are saved across a reboot and the logging destination option remains enabled. Otherwise, the logging destination is disabled.
session (debug destination)
Disabled.
ACL (debug type)
Disabled.
All (debug type)
Disabled.
event (debug type)
If a syslog server IP address is configured in the startup-config file, the sending of Event Log messages is reset to
enabled, regardless of the last active setting.If no syslog server is configured, the sending of Event Log messages is
disabled.IP (debug type)
Disabled.
-
Debugcommands do not affect normal message output to the Event Log.
Using the
debug eventcommand, you can specify that Event Log messages are sent to the debug destinations you configure (CLI session, syslog servers, or both) in addition to the Event Log. -
Ensure that your syslog servers accept debug messages.
All syslog messages resulting from a debug operation have a "debug" severity level. If you configure the switch to send debug messages to a syslog server, ensure that the server's syslog application is configured to accept the "debug" severity level. (The default configuration for some syslog applications ignores the "debug" severity level.)
-
Duplicate IP addresses are not stored in the list of syslog servers.
-
If the default severity value is in effect, all messages that have severities greater than the default value are passed to syslog. For example, if the default severity is "debug," all messages that have severities greater than debug are passed to syslog.
-
There is a limit of six syslog servers. All syslog servers are sent the same messages using the same filter parameters. An error is generated for an attempt to add more than six syslog servers.