In IP networks, ICMP messages are generated in response to either inquiries or requests from routing and diagnostic functions. These messages are directed to the applications originating the inquiries. In unusual situations, if the messages are generated rapidly with the intent of overloading network circuits, they can threaten network availability. This problem is visible in denial-of-service (DoS) attacks or other malicious behaviors where a worm or virus overloads the network with ICMP messages to an extent where no other traffic can get through. (ICMP messages themselves can also be misused as virus carriers). Such malicious misuses of ICMP can include a high number of ping packets that mimic a valid source IP address and an invalid destination IP address (spoofed pings), and a high number of response messages (such as Destination Unreachable error messages) generated by the network.
ICMP rate-limiting provides a method for limiting the amount of bandwidth that may be used for inbound ICMP traffic on a switch port. This feature allows users to restrict ICMP traffic to percentage levels that permit necessary ICMP functions, but throttle additional traffic that may be caused by worms or viruses (reducing their spread and effect). In addition, ICMP rate-limiting preserves inbound port bandwidth for non-ICMP traffic.
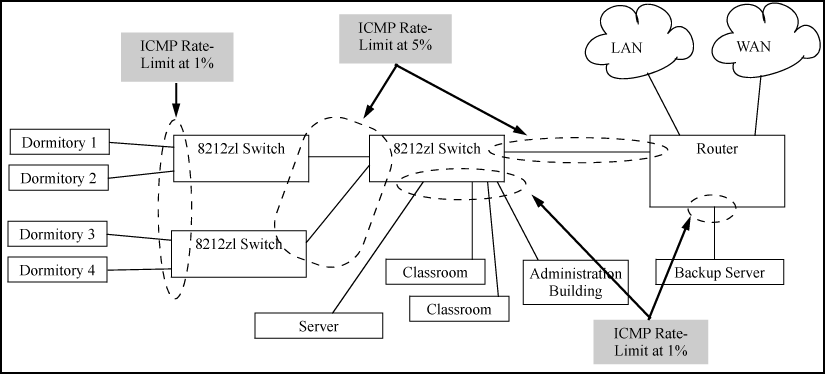
Apply ICMP rate-limiting on all connected interfaces on the switch to effectively throttle excessive ICMP messaging from any source. Example: of ICMP rate-limiting shows an Example: of how to configure this for a small to mid-sized campus though similar rate-limit thresholds are applicable to other network environments. On edge interfaces, where ICMP traffic should be minimal, a threshold of 1% of available bandwidth should be sufficient for most applications. On core interfaces, such as switch-to-switch and switch-to-router, a maximum threshold of 5% should be sufficient for normal ICMP traffic. ("Normal" ICMP traffic levels should be the maximums that occur when the network is rebooting.)
For detailed information about ICMP rate-limiting, see ICMP rate-limiting.
The rate-limit icmp command controls inbound usage of a port by setting a limit on the bandwidth available for inbound ICMP traffic.
Syntax:
Configures inbound ICMP traffic rate-limiting. You can configure a rate limit from either the global configuration level (as shown above) or from the interface context level. The
noform of the command disables ICMP rate-limiting on the specified interfaces.
percent <1-100>Values in this range allow ICMP traffic as a percentage of the bandwidth available on the interface.
kbps <0-10000000>Specifies the rate at which to forward traffic in kilobits per second.
0Causes an interface to drop all incoming ICMP traffic and is not recommended. See the Caution on “Caution”.
trap-clearClears existing ICMP rate limiting trap condition.
Note: ICMP rate-limiting is not supported on meshed ports. (Rate-limiting can reduce the efficiency of paths through a mesh domain).
Example:
Either of the following commands configures an inbound rate limit of 1% on ports A3 to A5, which are used as network edge ports:
HP Switch(config) # int a3-a5 rate-limit icmp 1 HP Switch(eth-A3-A5) # rate-limit icmp 1
For information on using ICMP rate-limiting and all-traffic rate-limiting on the same interface, seeUsing both ICMP rate-limiting and all-traffic rate-limiting on the same interface.
ICMP and all-traffic rate-limiting can be configured on the same interface. All-traffic rate-limiting applies to all inbound or outbound traffic (including ICMP traffic), while ICMP rate-limiting applies only to inbound ICMP traffic.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If the all-traffic load on an interface meets or exceeds the currently configured all-traffic inbound rate-limit while the ICMP traffic rate-limit on the same interface has not been reached, all excess traffic is dropped, including any inbound ICMP traffic above the all-traffic limit (regardless of whether the ICMP rate-limit has been reached). |
|
|
Example:
all inbound traffic above 55% of the port's bandwidth, including any additional ICMP traffic, is dropped as long as all inbound traffic combined on the port demands 55% or more of the port's bandwidth.
The show rate-limit icmp command displays the per-interface ICMP rate-limit configuration in the running-config file.
Syntax:
Without [
port-list], this command lists the ICMP rate-limit configuration for all ports on the switch.With [
port-list], this command lists the rate-limit configuration for the specified interfaces. This command operates the same way in any CLI context
If you want to view the rate-limiting configuration on ports 1–6:
Listing the rate-limit configuration
HP Switch(config)# show rate-limit icmp 1-6
Inbound ICMP Rate Limit Maximum Percentage
| Rate
Port | Mode Limit
----- + -------- --------
1 | Disabled Disabled
2 | kbps 100
3 | % 5
4 | % 1
5 | % 1
6 | Disabled Disable
The show running command displays the currently applied setting for any interfaces in the switch configured for all traffic rate-limiting and ICMP rate-limiting.
The show config command displays this information for the configuration currently stored in the startup-config file. (Note that configuration changes performed with the CLI, but not followed by a write mem command, do not appear in the startup-config file.)
For more information on ICMP rate-limiting, see Operating notes for ICMP rate-limiting.
ICMP rate-limiting operates on an interface (per-port) basis to allow, on average, the highest expected amount of legitimate, inbound ICMP traffic.
-
Interface support: ICMP rate-limiting is available on all types of ports (other than trunk ports or mesh ports), and at all port speeds configurable for the switch.
-
Rate-limiting is not permitted on mesh ports: Either type of rate-limiting (all-traffic or ICMP) can reduce the efficiency of paths through a mesh domain.
-
Rate-limiting is not supported on port trunks: Neither all-traffic nor ICMP rate-limiting are supported on ports configured in a trunk group.
-
ICMP percentage-based rate-limits are calculated as a percentage of the negotiated link speed: For example, if a 100 Mbps port negotiates a link to another switch at 100 Mbps and is ICMP rate-limit configured at 5%, the inbound ICMP traffic flow through that port is limited to 5 Mbps. Similarly, if the same port negotiates a 10 Mbps link, it allows 0.5 Mbps of inbound traffic. If an interface experiences an inbound flow of ICMP traffic in excess of its configured limit, the switch generates a log message and an SNMP trap (if an SNMP trap receiver is configured).
-
ICMP rate-limiting is port-based: ICMP rate-limiting reflects the available percentage of an interface's entire inbound bandwidth. The rate of inbound flow for traffic of a given priority and the rate of flow from an ICMP rate-limited interface to a particular queue of an outbound interface are not measures of the actual ICMP rate limit enforced on an interface.
-
Below-maximum rates: ICMP rate-limiting operates on a per-interface basis, regardless of traffic priority. Configuring ICMP rate-limiting on an interface where other features affect inbound port queue behavior (such as flow control) can result in the interface not achieving its configured ICMP rate-limiting maximum. For example, in some situations with flow control configured on an ICMP rate-limited interface, there can be enough "back pressure" to hold high-priority inbound traffic from the upstream device or application to a rate that does not allow bandwidth for lower-priority ICMP traffic. In this case, the inbound traffic flow may not permit the forwarding of ICMP traffic into the switch fabric from the rate-limited interface. (This behavior is termed "head-of-line blocking" and is a well-known problem with flow-control.) In cases where both types of rate-limiting (
rate-limit allandrate-limit icmp) are configured on the same interface, this situation is more likely to occur.In another type of situation, an outbound interface can become oversubscribed by traffic received from multiple ICMP rate-limited interfaces. In this case, the actual rate for traffic on the rate-limited interfaces may be lower than configured because the total traffic load requested to the outbound interface exceeds the interface's bandwidth, and thus some requested traffic may be held off on inbound.
-
Monitoring (mirroring) ICMP rate-limited interfaces: If monitoring is configured, packets dropped by ICMP rate-limiting on a monitored interface are still forwarded to the designated monitor port. (Monitoring shows what traffic is inbound on an interface, and is not affected by "drop" or "forward" decisions.)
-
Optimum rate-limiting operation: Optimum rate-limiting occurs with 64-byte packet sizes. Traffic with larger packet sizes can result in performance somewhat below the configured inbound bandwidth. This is to ensure the strictest possible rate-limiting of all sizes of packets.
-
Outbound traffic flow: Configuring ICMP rate-limiting on an interface does not control the rate of outbound traffic flow on the interface.
ICMP rate-limiting is applied to the available bandwidth on an interface. If the total bandwidth requested by all ICMP traffic is less than the available, configured maximum rate, no ICMP rate-limit can be applied. That is, an interface must be receiving more inbound ICMP traffic than the configured bandwidth limit allows. If the interface is configured with both rate-limit all and rate-limit icmp, the ICMP limit can be met or exceeded only if the rate limit for all types of inbound traffic has not already been met or exceeded. Also, to test the ICMP limit you need to generate ICMP traffic that exceeds the configured ICMP rate limit. Using the recommended settings—1% for edge interfaces and 5% maximum for core interfaces—it is easy to generate sufficient traffic. However, if you are testing with higher maximums, you need to ensure that the ICMP traffic volume exceeds the configured maximum.
When testing ICMP rate-limiting where inbound ICMP traffic on a given interface has destinations on multiple outbound interfaces, the test results must be based on the received outbound ICMP traffic.
ICMP rate-limiting is not reflected in counters monitoring inbound traffic because inbound packets are counted before the ICMP rate-limiting drop action occurs.
If the switch detects a volume of inbound ICMP traffic on a port that exceeds the ICMP rate-limit configured for that port, it generates one SNMP trap and one informational Event Log message to notify the system operator of the condition. (The trap and Event Log message are sent within two minutes of when the event occurred on the port.) For Example:
These trap and Event Log messages provide an advisory that inbound ICMP traffic on a given interface has exceeded the configured maximum. The additional ICMP traffic is dropped, but the excess condition may indicate an infected host (or other traffic threat or network problem) on that interface. The system operator should investigate the attached devices or network conditions further; the switch does not send more traps or Event Log messages for excess ICMP traffic on the affected port until the system operator resets the port's ICMP trap function.
The switch does not send more traps or Event Log messages for excess ICMP traffic on the affected port until the system operator resets the port’s ICMP trap function. The reset can be done through SNMP from a network management station or through the CLI with the trap-clear command option or the setmib command.
Syntax:
On a port configured with ICMP rate-limiting, this command resets the ICMP trap function, which allows the switch to generate a new SNMP trap and an Event Log message if ICMP traffic in excess of the configured limit is detected on the port.
Example:
An operator noticing an ICMP rate-limiting trap or Event Log message originating with port 1 on a switch would use the following setmib command to reset the port to send a new message if the condition occurs again:
HP Switch(config)# interface 1 rate-limit icmp trap-clear
HP Switch(config)# setmib hpicmpratelimitportalarmflag. 1 -i 1
To enable excess ICMP traffic notification traps and Event Log messages, use the setmib command described on ICMP rate-limiting trap and Event Log messages. The port number included in the command corresponds to the internal number the switch maintains for the designated port and not the port's external identity.
To match the port's external slot/number to the internal port number, use the walkmib ifDescr command, as shown in the following example:
Matching internal port numbers to external port numbers
HP Switch# walkmib ifDescr ifDescr.1 = 1 ifDescr.2 = 2 ifDescr.3 = 3 ifDescr.4 = 4 ifDescr.5 = 5 ifDescr.6 = 6 ifDescr.7 = 7 ifDescr.8 = 8 ifDescr.9 = 9 ifDescr.10 = 10 ifDescr.11 = 11 ifDescr.12 = 12 ifDescr.13 = 13 ifDescr.14 = 14 ifDescr.15 = 15 ifDescr.16 = 16 ifDescr.17 = 17 ifDescr.18 = 18 ifDescr.19 = 19 ifDescr.20 = 20 ifDescr.21 = 21 ifDescr.22 = 22 ifDescr.23 = 23 ifDescr.24 = 24 ifDescr.210 = Trk1 ifDescr.211 = Trk2 ifDescr.330 = DEFAULT_VLAN ifDescr.4425 = HP Switch software loopback interface ifDescr.4426 = HP Switch software loopback interface . . .
You can configure rate-limiting (throttling) of inbound broadcast and multicast traffic on the switch, which helps prevent the switch from being disrupted by traffic storms if they occur on the rate-limited port. The rate-limiting is implemented as a percentage of the total available bandwidth on the port.
The rate-limit command can be executed from the global or interface context, for Example:
HP Switch(config)# interface 3 rate-limit bcast in percent 10HP Switch(config)# interface 3 HP Switch(eth-3)# rate-limit bcast in percent 10
Syntax:
Enables rate-limiting and sets limits for the specified inbound broadcast or multicast traffic. Only the amount of traffic specified by the percent is forwarded.
If you want to set a limit of 50% on inbound broadcast traffic for port 3, you can first enter interface context for port 3 and then execute the rate-limit command, as shown in Inbound broadcast rate-limiting of 50% on port 3. Only 50% of the inbound broadcast traffic will be forwarded.
Inbound broadcast rate-limiting of 50% on port 3
HP Switch(config)# int 3 HP Switch(eth-3)# rate-limit bcast in percent 50 HP Switch(eth-3)# show rate-limit bcast Broadcast-Traffic Rate Limit Maximum % Port | Inbound Limit Mode Radius Override ----- + ------------- --------- --------------- 1 | Disabled Disabled No-override 2 | Disabled Disabled No-override 3 | Disabled % No-override 4 | Disabled Disabled No-override 5 | Disabled Disabled No-override
If you rate-limit multicast traffic on the same port, the multicast limit is also in effect for that port, as shown in Inbound multicast rate-limiting of 20% on port 3. Only 20% of the multicast traffic will be forwarded.
Inbound multicast rate-limiting of 20% on port 3
HP Switch(eth-3)# rate-limit mcast in percent 20 HP Switch(eth-3)# show rate-limit mcast Multicast-Traffic Rate Limit Maximum % Port | Inbound Limit Mode Radius Override ----- + ------------- --------- --------------- 1 | Disabled Disabled No-override 2 | Disabled Disabled No-override 3 | 20 % No-override 4 | Disabled Disabled No-override
To disable rate-limiting for a port enter the no form of the command, as shown in Disabling inbound multicast rate-limiting for port 3.
Disabling inbound multicast rate-limiting for port 3
HP Switch(eth-3)# no rate-limit mcast in HP Switch(eth-3)# show rate-limit mcast Multicast-Traffic Rate Limit Maximum % Port | Inbound Limit Mode Radius Override ----- + ------------- --------- --------------- 1 | Disabled Disabled No-override 2 | Disabled Disabled No-override 3 | Disabled Disabled No-override 4 | Disabled Disabled No-override
![[CAUTION: ]](images/caution.gif)