The HP switches covered in this guide use Secure Shell version 2 (SSHv2) to provide remote access to management functions on the switches via encrypted paths between the switch and management station clients capable of SSH operation.
SSH provides Telnet-like functions but, unlike Telnet, SSH provides encrypted, authenticated transactions. The authentication types include:
-
Client public-key authentication
-
Switch SSH and user password authentication
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: SSH in HP switches is based on the OpenSSH software toolkit. For more information on OpenSSH, visit www.openssh.com. |
|
|
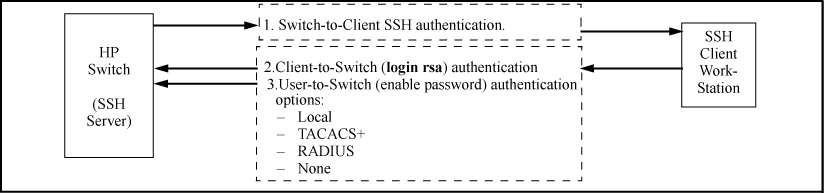
This option uses one or more public keys (from clients) that must be stored on the switch. Only a client with a private key that matches a stored public key can gain access to the switch, and the same private key can be stored on one or more clients.
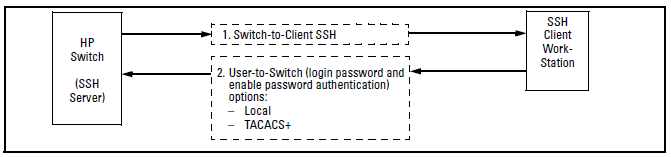
This option is a subset of full certificate authentication of the client public-key authentication shown in Client public-key authentication model. It occurs if the switch has SSH enabled but does not have login access (login public-key) configured to authenticate the client’s key. As in Client public-key authentication model, the switch authenticates itself to SSH clients. Users on SSH browser then authenticate themselves to the switch (login and/or enable levels) by providing passwords stored locally on the switch or on a TACACS+ or RADIUS server. However, the client does not use a certificate to authenticate itself to the switch.