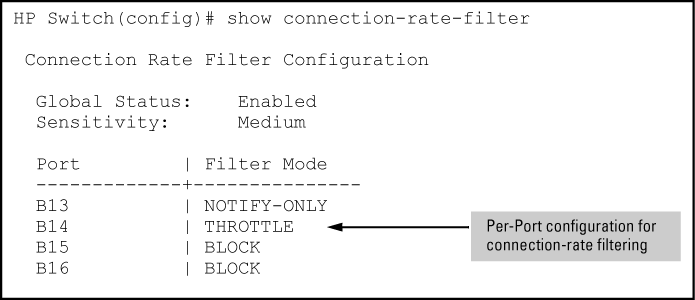
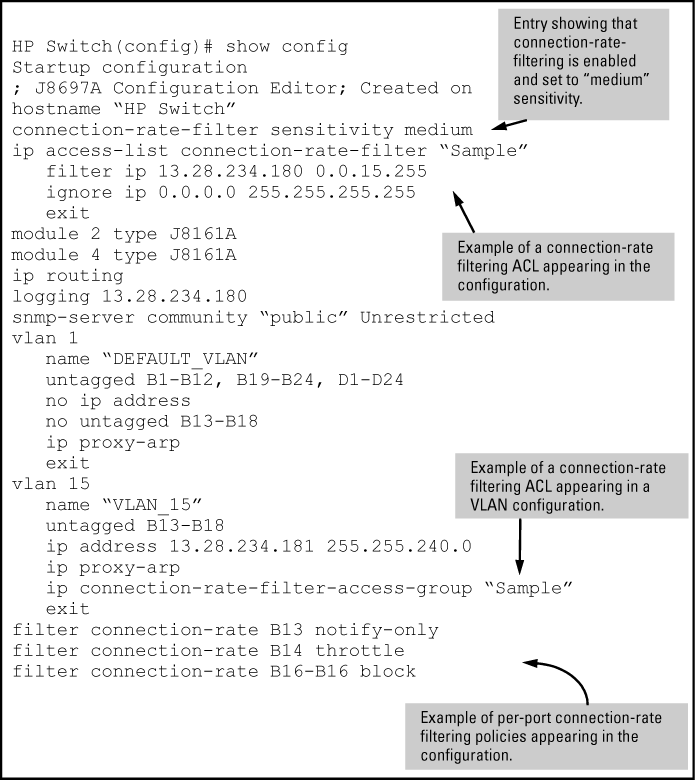
Use the following command to view the basic connection-rate configuration. If you need to view connection-rate ACLs and/or any other switch configuration details, use show config or show running. See Displaying the connection-rate status, sensitivity, and per-port configuration.
Syntax
Displays the current global connection-rate status (enabled/disabled) and sensitivity setting, and the current per-port configuration. This command does not display the current (optional) connection-rate ACL configuration.
To view the complete connection-rate configuration, including any ACLs, use show config (for the startup-config file) or show running (for the running-config file). See Applying connection-rate ACLs.
Use the commands in this section to enable connection-rate filtering on the switch and to apply the filtering on a per-port basis.
Syntax
[no]
connection-rate-filter
Enables connection-rate filtering.
Sets the global sensitivity level at which the switch interprets a given host attempt to connect to a series of different devices as a possible attack by a malicious agent residing in the host.
Options for configuring sensitivity include:
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The sensitivity settings configured on the switch determine the Trottle mode penalty periods as shown in Throttle mode penalty periods. |
|
|
Syntax
Configures the per-port policy for responding to detection of a relatively high number of inbound IP connection attempts from a given source. The level at which the switch detects such traffic depends on the sensitivity setting configured by the
connection-rate-filter sensitivitycommand. See Enabling global connection-rate filtering and sensitivity.
NOTE: You can use connection-rate ACLs to create exceptions to the configured filtering policy. See Applying connection-rate ACLs.
The
noform of the command disables connection-rate filtering on the ports in #<port-list>.The
notify-onlyoption can be used if the switch detects a relatively high number of IP connection attempts from a specific host,notify-onlygenerates an Event Log message and sends a similar message to any SNMP trap receivers configured on the switch.The
trottlecommand can be used if the switch detects a relatively high number of IP connection attempts from a specific host, this option generates thenotify-onlymessaging and blocks all inbound traffic from the offending host for a penalty period. After the penalty period, the switch allows traffic from the offending host to resume, and re-examines the traffic. If the suspect behavior continues, the switch again blocks the traffic from the offending host and repeats the cycle. For the penalty periods, see Throttle mode penalty periods.The
blockcommand can be used if the switch detects a relatively high number of IP connection attempts from a specific host, this option generates thenotify-onlymessaging and also blocks all inbound traffic from the offending host.
Throttle mode penalty periods
| Throttle mode (sensitivity) | Frequency of IP connection requests from the same source | Mean number of new destination hosts in the frequency period | Penalty period |
|---|---|---|---|
| Low | <0.1 second | 54 | <30 seconds |
| Medium | <1.0 second | 37 | 30 - 60 seconds |
| High | <1.0 second | 22 | 60 - 90 seconds |
| Aggressive | <1.0 second | 15 | 90 - 120 seconds |
Example of a Basic Connection-Rate Filtering Configuration
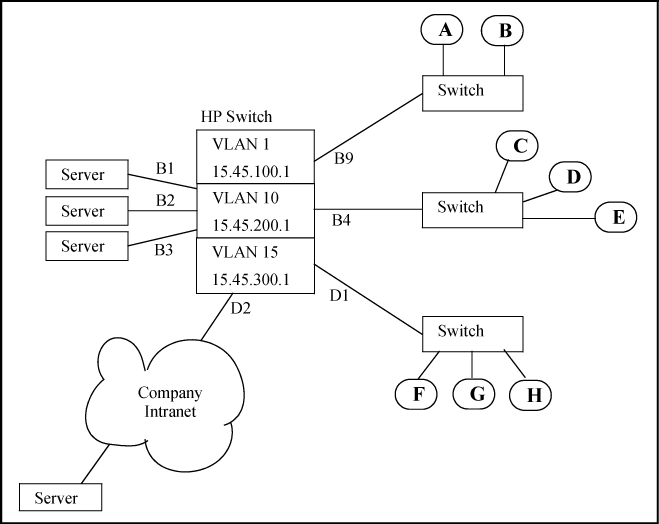
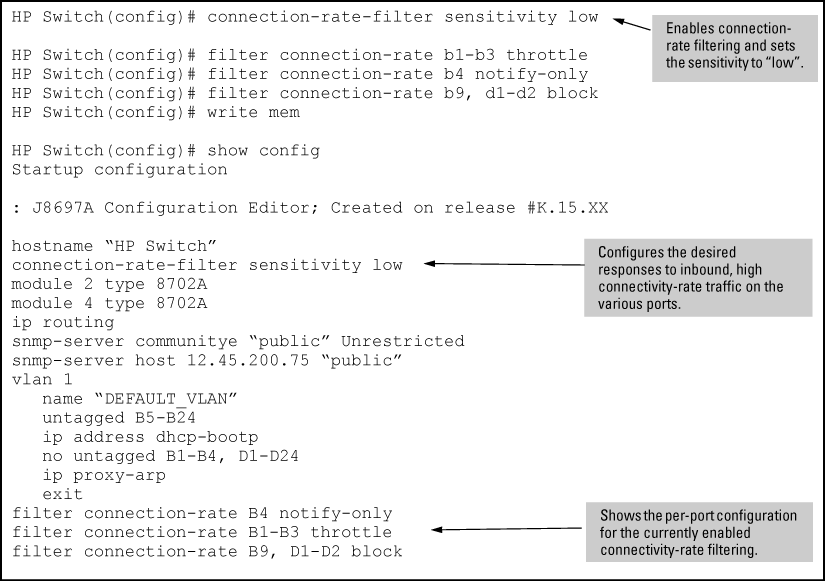
Suppose that in the sample network, the administrator wanted to enable connection-rate filtering and configure the following response to high connection-rate traffic on the switch:
-
Ports B1 — B3: Throttle traffic from the transmitting hosts.
-
Port B4: Respond with notify-only to identify the transmitting hosts.
-
Ports B9, D1, and D2: Block traffic from the transmitting hosts.
This example illustrates the configuration steps and resulting startup-config file: