TACACS AAA systems are used as a single point of management to configuring and store user accounts. They are often coupled with directories and management repositories, simplifying the set upmaintenancenence of the end-user accounts.
In the authorization function of the AAA system, network devices with Authentication Services can provide fine-grained control over user capabilities for the duration of the user’s session, for example setting access control or session duration. Enforcement of restrictions to a user account can limit available commands and levels of access.
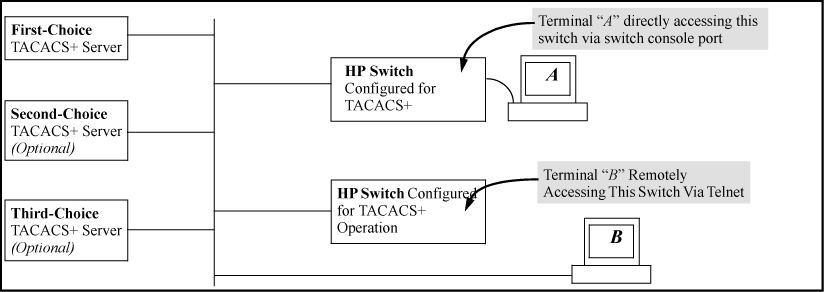
TACACS+ authenticationprovides a central server in which you can allow or deny access to switches and other TACACS-aware devices in your network. TACACS employes a central database which creates multiple unique user name and password sets with their associated privilege levels. This central database can be accessed by individuals via switch from either a console port or via Telnet.
TACACS+ uses an authentication hierarchy consisting of:
-
remote passwords assigned in a TACACS+ server
-
local passwords configured on the switch.
-
WebAgent access. See Controlling webagent access when using TACACS+ authentication.
-
If you configure Authorized IP managers on the switch, it is not necessary to include any devices used as TACACS+ servers in the authorized manager list. That is, authentication traffic between a TACACS+ server and the switch is not subject to Authorized IP manager controls configured on the switch. Also, the switch does not attempt TACACS+ authentication for a management station that the Authorized IP manager list excludes because, independent of TACACS+, the switch already denies access to such stations.
-
When TACACS+ is not enabled on the switch-or when the switch only designated TACACS+ servers are not accessible-setting a local operator password without also setting a local manager password does not protect the switch from manager-level access by unauthorized persons.
-
When using the
copycommand to transfer a configuration to a TFTP server, any optional, server-specific and global encryption keys in the TACACS configuration are not included in the transferred file. Otherwise, a security breach could occur, allowing access to the TACACS+ user name/password information.
It is important to test the TACACS+ service before fully implementing it. Depending on the process and parameter settings you use to set up and test TACACS+ authentication in your network, you could accidentally lock all users, including yourself, out of access to a switch. While recovery is simple, it can pose an inconvenience that can be avoided. To prevent an unintentional lockout on the switch, use a procedure that configures and tests TACACS+ protection for one access type (for example, Telnet access), while keeping the other access type (console, in this case) open in case the Telnet access fails due to a configuration problem. The following procedure outlines a general setup procedure.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If a complete access lockout occurs on the switch as a result of a TACACS+ configuration, see "Troubleshooting TACACS+ Operation" in the Management and Configuration Guide for your switch. |
|
|
-
Familiarize yourself with the requirements for configuring your TACACS+ server application to respond to requests from the switch. (See the documentation provided with the TACACS+ server software.) This includes knowing whether you need to configure an encryption key, see Encryption options in the switch.
-
-
The IP addresses of the TACACS+ servers you want the switch to use for authentication. If you will use more than one server, determine which server is your first-choice for authentication services.
-
The encryption key, if any, for allowing the switch to communicate with the server. You can use either a global key or a server-specific key, depending on the encryption configuration in the TACACS+ servers.
-
The number of log-in attempts you allow before closing a log-in session. ( Default: 3
-
The period you want the switch to wait for a reply to an authentication request before trying another server.
-
The user name/password pairs you want the TACACS+ server to use for controlling access to the switch.
-
The privilege level you want for each user name/password pair administered by the TACACS+ server for controlling access to the switch.
-
The user name/password pairs you want to use for local authentication (one pair each for operator and manager levels).
-
-
Plan and enter the TACACS+ server configuration needed to support TACACS+ operation for Telnet access (login and enable) to the switch. This includes the user name/password sets for logging in at the operator (read-only) privilege level and the sets for logging in at the manager (read/write) privilege level.
If you are a first-time user of the TACACS+ service, HP recommends that you configure only the minimum feature set required by the TACACS+ application to provide service in your network environment. After you have success with the minimum feature set, you can then want to try additional features that the application offers.
-
Ensure that the switch has the correct local user name and password for manager access. (If the switch cannot find any designated TACACS+ servers, the local manager and operator user name/password pairs are always used as the secondary access control method.)
-
Using a terminal device connected to the switch console port, configure the switch for TACACS+ authentication only for Telnet login access and Telnet enable access. At this stage, do not configure TACACS+ authentication for console access to the switch, as you may need to use the console for access if the configuration for the Telnet method needs debugging.
-
Ensure that the switch is configured to operate on your network and can communicate with your first-choice TACACS+ server. (At a minimum, this requires IP addressing and a successful
pingtest from the switch to the server.) -
On a remote terminal device, use Telnet to attempt to access the switch. If the attempt fails, use the console access to check the TACACS+ configuration on the switch. If you make changes in the switch configuration, check Telnet access again. If Telnet access still fails, check the configuration in your TACACS+ server application for mis-configurations or missing data that could affect the server's interoperation with the switch.
-
After your testing shows that Telnet access using the TACACS+ server is working properly, configure your TACACS+ server application for console access. Then test the console access. If access problems occur, check for and correct any problems in the switch configuration, and then test console access again. If problems persist, check your TACACS+ server application for mis-configurations or missing data that could affect the console access.
-
When you are confident that TACACS+ access through both Telnet and the switch console operates properly, use the
write memorycommand to save the switch running-config file to flash.
Authentication through a TACACS+ server operates generally as described below. For specific operating details, see the documentation you received with your TACACS+ server application.
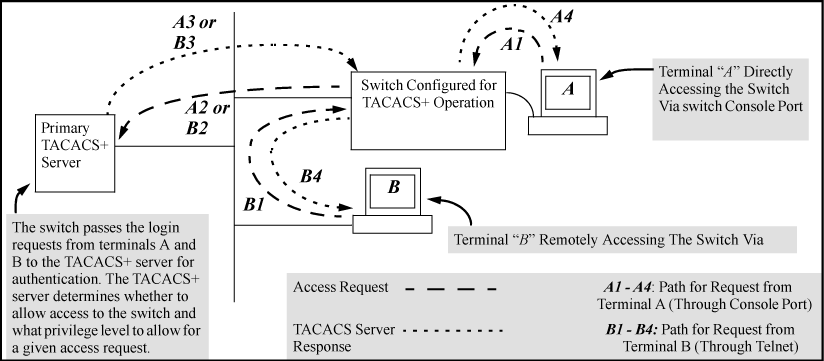
Using Using a TACACS+ Server for Authentication, after either switch detects an operator's logon request from a remote or directly connected terminal, the following events occur:
-
The switch queries the first-choice TACACS+ server for authentication of the request.
-
If the switch does not receive a response from the first-choice TACACS+ server, it attempts to query a secondary server. If the switch does not receive a response from any TACACS+ server, then it uses its own local user name/password pairs to authenticate the logon request, see Local authentication process.
-
If a TACACS+ server recognizes the switch, it forwards a user name prompt to the requesting terminal via the switch.
-
-
When the requesting terminal responds to the prompt with a user name, the switch forwards it to the TACACS+ server.
-
After the server receives the user name input, the requesting terminal receives a password prompt from the server via the switch.
-
When the requesting terminal responds to the prompt with a password, the switch forwards it to the TACACS+ server and one of the following actions occurs:
-
If the user name/password pair received from the requesting terminal matches a user name/password pair previously stored in the server, then the server passes access permission through the switch to the terminal.
-
If the user name/password pair entered at the requesting terminal does not match a user name/password pair previously stored in the server, access is denied. In this case, the terminal is again prompted to enter a user name and repeat steps 2 through 4 In the default configuration, the switch allows up to three attempts to authenticate a login session. If the requesting terminal exhausts the attempt limit without a successful TACACS+ authentication, the login session is terminated and the operator at the requesting terminal must initiate a new session before trying again.
-
When the switch is configured to use TACACS+, it reverts to local authentication only if one of these two conditions exists:
-
"Local" is the authentication option for the access method being used.
-
TACACS+ is the primary authentication mode for the access method being used. Local is the secondary authentication method if the switch is unable to connect to any TACAS+ servers.
For a listing of authentication options, see Configuring the switch TACACS+ server access.
For local authentication, the switch uses the operator-level and manager-level user name/password sets previously configured locally on the switch. (These are the user names and passwords you can configure using the CLI password command, the WebAgent, or the menu interface—which enables only local password configuration).
-
If the operator at the requesting terminal correctly enters the user name/password pair for either access level, access is granted.
-
If the user name/password pair entered at the requesting terminal does not match either user name/password pair previously configured locally in the switch, access is denied. In this case, the terminal is again prompted to enter a user name/password pair. In the default configuration, the switch allows up to three attempts. If the requesting terminal exhausts the attempt limit without a successful authentication, the login session is terminated and the operator at the requesting terminal must initiate a new session before trying again.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The switch menu allows you to configure only the local operator and manager passwords, and not any user names. In this case, all prompts for local authentication requests only a local password. However, if you use the CLI or the WebAgent to configure user names for local access, you see a prompt for both a local user name and a local password during local authentication. |
|
|
AAA Authentication Parameters
| Name | Default | Range | Function |
|---|---|---|---|
| console, Telnet, SSH, web or port-access | n/a | n/a | Specifies the access method used when authenticating. TACACS+ authentication only uses the console, Telnet or SSH access methods. |
| enable | n/a | n/a | Specifies the manager (read/write) privilege level for the access method being configured. |
|
|
privilege-mode disabled | n/a |
login: Specifies the operator (read-only) privilege level for the access method being configured. The privilege-mode option enables TACACS+ for a single login. The authorized privilege level (operator or manager) is returned to the switch by the TACACS+ server. |
|
|
local | n/a | Specifies the primary method of authentication for the access method being configured.
local: Use the user name/password pair configured locally in the switch for the privilege level being configured tacacs: Use a TACACS+ server. |
|
|
none | n/a | Specifies the secondary (backup) type of authentication being configured.
local: The user name/password pair configured locally in the switch for the privilege level being configured. none: No secondary type of authentication for the specified method/privilege path. (Available only if the primary method of authentication for the access being configured is local.) Note: If you do not specify this parameter in the command line, the switch automatically assigns the secondary method as follows:
|
|
|
3 | 1 - 10 | In a given session, specifies how many tries at entering the correct user name/password pair are allowed before access is denied and the session terminated. |
Primary/secondary authentication table
| Access method and privilege level | Authentication options | Effect on access attempts | |
|---|---|---|---|
| Primary | Secondary | ||
| Console — Login | local | none* | Local user name/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local user name/password access. | |
| Console — Enable | local | none | Local user name/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local user name/password access. | |
| Telnet — Login | local | none* | Local user name/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local user name/password access. | |
| tacacs | none | If Tacacs+ server unavailable, denies access. | |
| Telnet — Enable | local | none | Local user name/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local user name/password access. | |
| tacacs | none | If Tacacs+ server unavailable, denies access. | |
Access options
Following is a set of access options and the corresponding commands to configure them
![[CAUTION: ]](images/caution.gif)