TCP client verification
The TCP client verification feature protects TCP servers against the following flood attacks:
SYN.
ACK.
SYN-ACK.
FIN.
RST.
The TCP client verification feature enables a TCP proxy on the device.
TCP client verification can operate in the following modes:
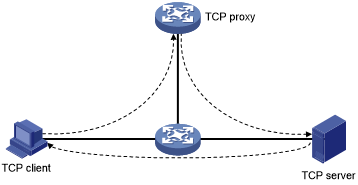
Safe reset—Enables unidirectional TCP proxy for packets only from TCP connection initiators. The unidirectional TCP proxy is sufficient for most scenarios because attacks are often seen from clients.
As shown in Figure 182, if packets from TCP clients pass through the proxy device, but the packets from servers do not, only the safe reset mode can be used.
Figure 177: Safe reset mode application
SYN cookie—Enables bidirectional TCP proxy for TCP clients and servers.
As shown in Figure 183, if packets from clients and servers pass through the TCP proxy device, either safe reset or SYN cookie can be used.
Figure 178: Safe reset/SYN cookie mode application
TCP proxy in safe reset mode
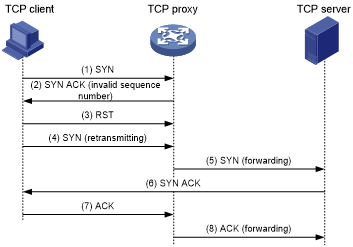
As shown in Figure 184, the safe reset mode functions as follows:
After receiving a SYN packet destined for a protected server, the TCP proxy sends back a SYN ACK packet with an invalid sequence number.
If the TCP proxy receives an RST packet from the client, the client is verified as legitimate.
The TCP proxy adds the client's IP address to the trusted IP list. The client initiates the connection again and the TCP proxy directly forwards the TCP packets to the server.
The safe reset mode requires that TCP clients comply with the TCP protocol suite. The TCP proxy will deny a legitimate client to access the server if the client does not comply with the TCP protocol suite.
With client verification, the TCP connection establishment takes more time than normal TCP connection establishment.
Figure 179: TCP proxy in safe reset mode
TCP proxy in SYN cookie mode
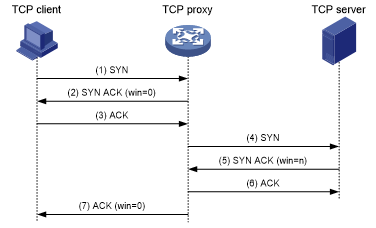
As shown in Figure 185, SYN cookie mode requires two TCP connections to be established as follows:
After receiving a SYN packet from a client to a protected server, the TCP proxy sends back a SYN ACK packet with the window size 0. If the client responds with an ACK packet, the client is verified as legitimate. The proxy device establishes a TCP connection with the client.
The TCP proxy device establishes a connection with the server through a new three-way handshake that has a different window size. This connection uses a different sequence number from the connection between the client and proxy device.
In SYN cookie mode, the TCP proxy is the server proxy that communicates with clients and the client proxy that communicates with server. Choose this mode when the following requirements are met:
The TCP proxy device is deployed on the key path that passes through the ingress and egress of the protected server.
All packets exchanged between clients and server pass through the TCP proxy device.
Figure 180: TCP proxy in SYN cookie mode