IKE local extended authentication and address pool authorization configuration example
Network requirements
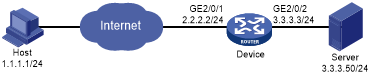
As shown in Figure 145, configure an IPsec tunnel to protect the traffic between the host and the server.
Set up IPsec SAs through IKE negotiations.
Configure the host and the device to use pre-shared key for authentication in the phase-1 IKE negotiation.
Configure the device to use AAA to perform local extended authentication on the host and assign an IPv4 address to the host.
Figure 140: Network diagram
Configuration procedure
Before you configure the device, perform the following tasks:
Make sure the device, host, and server can reach one another.
Configure AAA for authentication. In this example, the authentication account uses username test and password abc.
Configure the device:
# Configure IP addresses for interfaces. (Details not shown.)
# Create an ISP domain named dm.
<Device> system-view [Device] domain dm
# Configure the device to perform IKE local authentication.
[Device-isp-dm] authentication ike local
# Configure the device to perform IKE local authorization.
[Device-isp-dm] authorization ike local [Device-isp-dm] quit
# Create the IKE IPv4 address pool pool with the address range 20.1.1.1 to 20.1.1.20.
[Device] ike address-group pool 20.1.1.1 20.1.1.20
# Add a network user named ike.
[Device] local-user ike class network
# Authorize the user ike to use the IKE service.
[Device-luser-network-ike] service-type ike
# Specify the IPv4 address pool pool as the authorized IPv4 address pool for the user ike.
[Device-luser-network-ike] authorization-attribute ip-pool pool [Device-luser-network-ike] quit
# Add a network user named test.
[Device] local-user test class network
# Authorize the user test to use the IKE service.
[Device-luser-network-test] service-type ike
# Configure a password for the user test.
[Device-luser-network-test] password simple abc [Device-luser-network-test] quit
# Create an IKE keychain named keychain1.
[Device] ike keychain keychain1
# Set the pre-shared key used for IKE negotiation with the remote peer 1.1.1.1.
[Device-ike-keychain-keychain1] pre-shared-key address 1.1.1.1 255.255.255.255 key simple 123456TESTplat&! [Device-ike-keychain-keychain1] quit
# Create an IKE profile named profile1.
[Device] ike profile profile1
# Specify the IKE keychain keychain1 for the IKE profile profile1.
[Device-ike-profile-profile1] keychain keychain1
# Configure the local ID as the IP address 2.2.2.2.
[Device-ike-profile-profile1] local-identity address 2.2.2.2
# Configure the peer ID for IKE profile matching.
[Device-ike-profile-profile1] match remote identity address 1.1.1.1 255.255.255.255
# Enable XAUTH authentication for clients.
[Device-ike-profile-profile1] client-authentication xauth [Device-ike-profile-profile1] quit
# Enable AAA authorization. Specify the ISP domain dm and the username ike.
[Device-ike-profile-profile1] client-authentication xauth [Device-ike-profile-profile1] quit
# Created an IPsec transform set named tran1.
[Device] ipsec transform-set tran1
# Specify the encapsulation mode as transport.
[Device-ipsec-transform-set-tran1] encapsulation-mode transport
# Specify the security protocol as ESP.
[Device-ipsec-transform-set-tran1] protocol esp
# Specify the ESP authentication algorithm and encryption algorithm.
[Device-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-256 [Device-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [Device-ipsec-transform-set-tran1] quit
# Create an IPsec policy template entry. Specify the template name as pt and set the sequence number to 1.
[Device] ipsec policy-template pt 1
# Specify the IPsec transform set tran1.
[Device-ipsec-policy-template-pt-1] transform-set tran1
# Specify the IKE profile profile1.
[Device-ipsec-policy-template-pt-1] ike-profile profile1
# Enable IPsec RRI.
[Device-ipsec-policy-template-pt-1] reverse-route dynamic [Device-ipsec-policy-template-pt-1] quit
# Use IPsec policy template pt to create an IKE-based IPsec policy entry. Specify the policy name as map1 and set the sequence number to 1.
[Device] ipsec policy map1 1 isakmp template pt
# Apply the IPsec policy to GigabitEthernet 2/0/1.
[Device] interface gigabitethernet 2/0/1 [Device-GigabitEthernet2/0/1] ipsec apply policy map1 [Device-GigabitEthernet2/0/1] quit
Configure the host:
Perform the following tasks on the host and make sure the configuration matches that on the device:
Specify the IP address of the remote security gateway.
Set the pre-shared key used for IKE negotiation.
Configure the username and password for IKE client authentication.
Specify the security protocol, encryption algorithm, and authentication algorithm.
Configure IKE negotiation parameters.
Configure the local ID and remote ID.
(Details not shown.)
Verifying the configuration
# Initiate a connection from the host (1.1.1.1) to the server (3.3.3.50) to trigger IKE negotiation. (Details not shown.)
# On the device, verify that an IKE SA to the peer 1.1.1.1 is established and client authentication is enabled.
[Device] display ike sa verbose remote-address 1.1.1.1 ----------------------------------------------- Connection ID: 18 Outside VPN: Inside VPN: Profile: profile1 Transmitting entity: Responder ----------------------------------------------- Local IP: 2.2.2.2 Local ID type: IPV4_ADDR Local ID: 2.2.2.2 Remote IP: 1.1.1.1 Remote ID type: IPV4_ADDR Remote ID: 1.1.1.1 Authentication-method: PRE-SHARED-KEY Authentication-algorithm: SHA1 Encryption-algorithm: 3DES-CBC Life duration(sec): 86400 Remaining key duration(sec): 84565 Exchange-mode: Main Diffie-Hellman group: Group 2 NAT traversal: Detected Extend authentication: Enabled Assigned IP address: 20.1.1.2
# On the host, enter the correct username and password for client authentication. After the authentication succeeds, the IPsec tunnel will be established. (Details not shown.)
# Verify that IPsec SAs are established on the device.
<Device> display ipsec sa
-------------------------------
Interface: GigabitEthernet2/0/1
-------------------------------
-----------------------------
IPsec policy: map1
Sequence number: 1
Mode: Template
-----------------------------
Tunnel id: 2
Encapsulation mode: tunnel
Perfect forward secrecy:
Path MTU: 1427
Tunnel:
local address: 2.2.2.2
remote address: 1.1.1.1
Flow:
sour addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
dest addr: 20.1.1.2/255.255.255.255 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2374047012 (0x8d811524)
Transform set: ESP-ENCRYPT-AES-CBC-256 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843198/3259
Max received sequence-number: 24
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 146589619 (0x08bcc7b3)
Transform set: ESP-ENCRYPT-AES-CBC-256 ESP-AUTH-SHA1
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3259
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1839568/3164
Max sent sequence-number: 2793
UDP encapsulation used for NAT traversal: N
Status: Active