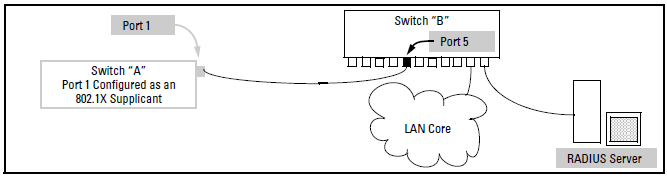
A switch port can operate as a supplicant in a connection to a port on another 802.1X-aware switch to provide security on links between 802.1X-aware switches. (A port can operate as both an authenticator and a supplicant.)
Example:
Suppose that you want to connect two switches, where:
-
When port 1 on switch “A” is first connected to a port on switch “B”, or if the ports are already connected and either switch reboots, port 1 begins sending start packets to port 5 on switch “B”.
-
If, after the supplicant port sends the configured number of start packets, it does not receive a response, it assumes that switch “B” is not 802.1X-aware, and transitions to the authenticated state. If switch “B” is operating properly and is not 802.1X-aware, then the link should begin functioning normally, but without 802.1X security. and password.
-
If, after sending one or more start request packets, port 1 receives a request packet from port 5, then switch “B” is operating as an 802.1X authenticator. The supplicant port then sends a response/ID packet. If switch “B” is configured for RADIUS authentication, it forwards this request to a RADIUS server. If switch “B” is configured for Local 802.1X authentication, the authenticator compares the switch “A” response to its local username
-
-
The RADIUS server then responds with an MD5 access challenge that switch “B” forwards to port 1 on switch “A”.
-
Port 1 replies with an MD5 hash response based on its username and password or other unique credentials. Switch “B” forwards this response to the RADIUS server.
-
The RADIUS server then analyzes the response and sends either a “success” or “failure” packet back through switch “B” to port 1.
You can configure a switch port as a supplicant for a point-to-point link to an 802.1X-aware port on another switch. Configure the port as a supplicant before configuring any supplicant-related parameters.
Syntax:
You must enable supplicant operation on a port before changing the supplicant configuration. This means you must execute the supplicant command once without any other parameters, then execute it again with a supplicant parameter you want to configure. If the intended authenticator port uses RADIUS authentication, then use the identity and secret options to configure the RADIUS-expected credentials on the supplicant port. If the intended authenticator port uses Local 802.1X authentication, then use the identity and secret options to configure the authenticator switch’s local username and password on the supplicant port.
Syntax:
To enable supplicant operation on the designated ports, execute this command without any other parameters. After doing this, you can use the command again with the following parameters to configure supplicant operation. (Use one instance of the command for each parameter you want to configure The
noform disables supplicant operation on the designated port(s).Sets the username and password to pass to the authenticator port when a challenge-request packet is received from the authenticator port due to an authentication request. If the intended authenticator port is configured for RADIUS authentication, then <
> and <username> must be the username and password expected by the RADIUS server. If the intended authenticator port is configured for Local authentication, then <password> and <username> must be the username and password configured on the Authenticator switch. (Default: Null.)passwordSets the secret password to be used by the port supplicant when an MD5 authentication request is received from an authenticator. The switch prompts you to enter the secret password after the command is invoked.
Sets the delay period the port waits to receive a challenge from the authenticator. If the request times out, the port sends another request, up to the number of attempts specified by the
max-startparameter. (Default: 30 seconds).Defines the maximum number of times the supplicant port requests authentication. See step 1 in Configuring switch ports to operate as supplicants for 802.1X connections to other switches for a description of how the port reacts to the authenticator response. (Default: 3).
Sets the time period the supplicant port waits after an active 802.1X session fails before trying to re- acquire the authenticator port. (Default: 60 seconds)
Sets the delay between Start packet retransmissions. That is, after a supplicant sends a start packet, it waits during the
start-periodfor a response. If no response comes during thestart-period, the supplicant sends a new start packet. Themax-startsetting (above) specifies how many start attempts are allowed in the session. (Default: 30 seconds)