RADIUS accounting collects data about user activity and system events and sends it to a RADIUS server when specified events occur on the switch, such as a logoff or a reboot.
The switch supports four types of accounting services:
-
Network accounting: Provides records containing the information listed below on clients directly connected to the switch and operating under Port-Based Access Control (802.1X):
-
Acct-Session-Id
-
Acct-Status-Type
-
Acct-Terminate-Cause
-
Acct-Authentic
-
Acct-Delay-Time
-
Acct-Input-Packets
-
Acct-Output-Packets
-
Acct-Input-Octets
-
Nas-Port
-
Acct-Output-Octets
-
Acct-Session-Time
-
User-Name
-
Service-Type
-
NAS-IP-Address
-
NAS-Identifier
-
Calling-Station-Id
-
HP-acct-terminate-cause
-
MS-RAS-Vendor
-
-
Exec accounting: Provides records holding the information listed below about login sessions (console, Telnet, and SSH) on the switch:
-
Acct-Session-Id
-
Acct-Status-Type
-
Acct-Terminate-Cause
-
Acct-Authentic
-
Acct-Delay-Time
-
Acct-Session-Time
-
User-Name
-
Service-Type
-
NAS-IP-Address
-
NAS-Identifier
-
Calling-Station-Id
-
MS-RAS-Vendor
-
-
System accounting: Provides records containing the information listed below when system events occur on the switch, including system reset, system boot, and enabling or disabling of system accounting.
-
Acct-Session-Id
-
Acct-Status-Type
-
Acct-Terminate-Cause
-
Acct-Authentic
-
Acct-Delay-Time
-
Username
-
Service-Type
-
NAS-IP-Address
-
NAS-Identifier
-
Calling-Station-Id
-
Acct-Session-Time
-
MS-RAS-Vendor
-
-
Commands accounting: Provides records containing information on CLI command execution during user sessions.
-
Acct-Session-Id
-
Acct-Status-Type
-
Service-Type
-
Acct-Authentic
-
User-Name
-
NAS-IP-Address
-
NAS-Identifier
-
NAS-Port-Type
-
Calling-Station-Id
-
HP-Command-String
-
Acct-Delay-Time
-
-
RADIUS accounting with IP attribute: The RADIUS Attribute 8 (Framed-IP-Address) feature provides the RADIUS server with information about the client's IP address after the client is authenticated. DHCP snooping is queried for the IP address of the client, so DHCP snooping must be enabled for the VLAN of which the client is a member.
When the switch begins communications with the RADIUS server it sends the IP address of the client requesting access to the RADIUS server as RADIUS Attribute 8 (Framed-IP-Address) in the RADIUS accounting request. The RADIUS server can use this information to build a map of usernames and addresses.
It may take a minute or longer for the switch to learn the IP address and then send the accounting packet with the Framed-IP-Address attribute to the RADIUS server. If the switch does not learn the IP address after a minute, it sends the accounting request packet to the RADIUS server without the Framed-IP-Address attribute. If the IP address is learned at a later time, it will be included in the next accounting request packet sent.
The switch forwards the accounting information it collects to the designated RADIUS server, where the information is formatted, stored, and managed by the server. For more information on this aspect of RADIUS accounting, see the documentation provided with your RADIUS server.
-
You can configure up to four types of accounting to run simultaneously: exec, system, network, and command.
-
RADIUS servers used for accounting are also used for authentication.
-
The switch must be configured to access at least one RADIUS server.
-
RADIUS servers are accessed in the order in which their IP addresses were configured in the switch. Use
show radiusto view the order. As long as the first server is accessible and responding to authentication requests from the switch, a second or third server will not be accessed. For more on this topic, see Changing RADIUS-server access order. -
If access to a RADIUS server fails during a session, but after the client has been authenticated the switch continues to assume the server is available to receive accounting data. Thus, if server access fails during a session, it will not receive accounting data transmitted from the switch.
The switch can be configured to support either of the following options for the accounting service types used in a management session. (See Accounting service types.)
-
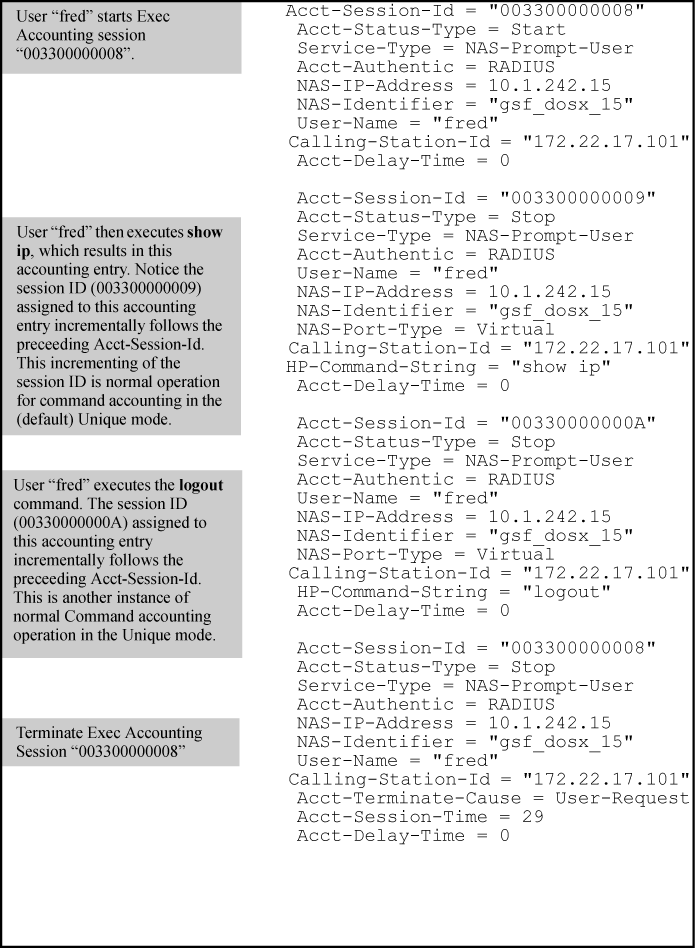
Unique Acct-Session-ID for each accounting service type used in the same management session (the default)
-
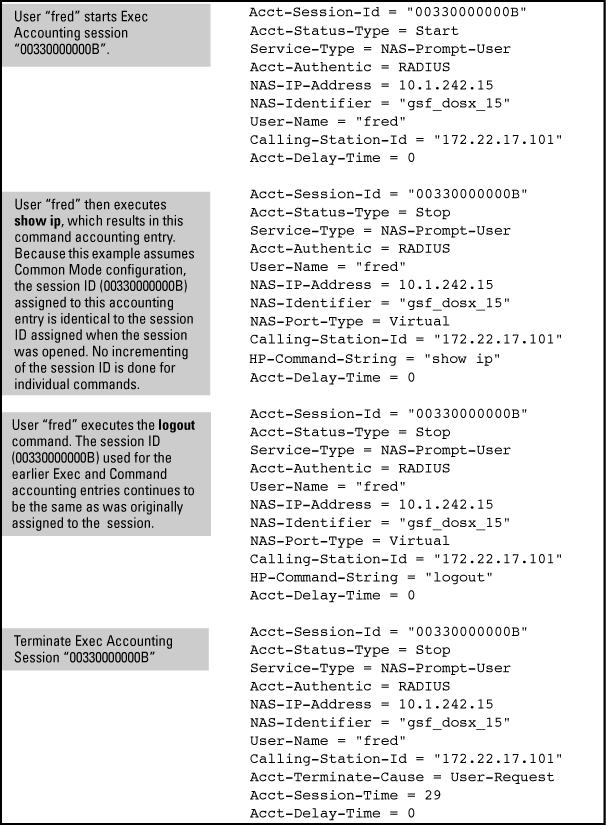
Same Acct-Session-ID for all accounting service types used in the same management session
In the Unique mode (the default), the various service types running in a management session operate as parallel, independent processes. Thus, during a specific management session, a given service type has the same Acct-Session-ID for all accounting actions for that service type. However, the Acct- Session-ID for each service type differs from the ID for the other types.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: In Unique Acct-Session-ID operation, the Command service type is a special case in which the Acct-Session-ID for each executed CLI command in the session is different from the IDs for other service types used in the session and also different for each CLI command executed during the session. That is, the ID for each successive CLI command in the session is sequentially incremented from the ID value assigned to the immediately preceding CLI command in that session. |
|
|
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This procedure assumes: |
|
|
-
Configure the switch for accessing a RADIUS server.
You can configure up to three RADIUS servers (one primary, two backup). The switch operates on the assumption that a server can operate in both accounting and authentication mode. See the documentation for your RADIUS server application for additional information.
-
Use the same
radius-server hostcommand that you would use to configure RADIUS authentication. See Configuring a switch to access a RADIUS server. -
Provide the following:
-
A RADIUS server IP address.
-
Optional — UDP destination port for authentication requests. Otherwise the switch assigns the default UDP port (1812; recommended).
-
Optional — if you are also configuring the switch for RADIUS authentication, and need a unique encryption key for use during authentication sessions with the RADIUS server you are designating, configure a server-specific key. This key overrides the global encryption key you can also configure on the switch, and must match the encryption key used on the specified RADIUS server. For more information, see the
key <parameter in Configuring a switch to access a RADIUS server. Default: nullkey-string>
-
-
-
(Optional) Reconfigure the desired Acct-Session-ID operation.
-
Unique (the default setting): Establishes a different Acct-Session-ID value for each service type, and incrementing of this ID per CLI command for the Command service type. See Unique Acct-Session-ID operation.
-
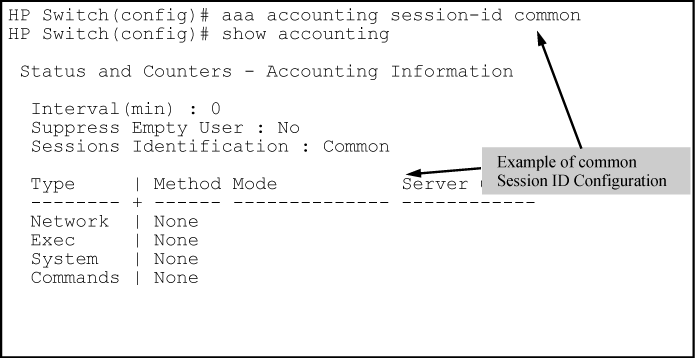
Common: Establishes the same Acct-Session-ID value for all service types, including successive CLI commands in the same management session.
-
-
Configure accounting types and the controls for sending reports to the RADIUS server.
-
(Optional) Configure session blocking and interim updating options
Before you configure the actual accounting parameters, configure the switch to use a RADIUS server. This process is outlined in Configuring the switch to access a RADIUS server. Repeat this now only if one of the following applies:
-
The switch is not yet configured to use a RADIUS server
-
Your server data has changed
-
You need to specify a non-default UDP destination port for accounting requests
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Switch operation expects a RADIUS server to accommodate both authentication and accounting. |
|
|
Syntax:
[key <
key-string>]Optional. Specifies an encryption key for use during accounting or authentication sessions with the specified server. This key must match the encryption key used on the RADIUS server. Use this command only if the specified server requires a different encryption key than configured for the global encryption key.
NOTE: If you save the config file using Xmodem or TFTP, the key information is not saved in the file. This causes RADIUS authentication to fail when the config file is loaded back onto the switch.
Example:
Suppose you want the switch to use the RADIUS server described below for both authentication and accounting purposes.
-
IP address: 10.33.18.151
-
A non-default UDP port number of 1750 for accounting.
For this example, assume that all other RADIUS authentication parameters for accessing this server are acceptable at their default settings, and RADIUS is already configured as an authentication method for one or more types of access to the switch (Telnet, Console, etc.).
Because the radius-server command includes an acct-port keyword with a non-default UDP port number of 1750, the switch assigns this value as the UDP accounting port.
Configuring for a RADIUS server with a non-default accounting UDP port number
HP Switch(config)# radius-server host 10.33.18.151
acct-port 1750 key source0151
HP Switch(config)# write mem
HP Switch(config)# show radius
Status and Counters - General RADIUS Information
Deadtime(min) : 0
Timeout(secs) : 5
Retransmit Attempts : 3
Global Encryption Key :
Dynamic Authorization UDP Port : 3799
Auth Acct DM/ Time
Server IP Addr Port Port CoA Window Encryption Key
--------------- ---- ---- --- ------ -------------------
10.33.18.151 1812 1750 No 10 source0151
The radius-server command as shown in Configuring for a RADIUS server with a non-default accounting UDP port number above, configures the switch to use a RADIUS server at IP address 10.33.18.151, with a non-default UDP accounting port of 1750, and a server-specific key of "source0151".
Syntax:
Optional command to reconfigure the Acct-Session-ID mode to apply to the accounting service type records for a given management session.
unique: Configures the switch to use a different Acct-Session-ID for each accounting service type. (Default setting)
common: Configures the switch to apply the same Acct-Session-ID to all accounting service types in the same management session.
For more on these options, see Acct-Session-ID options in a management session.
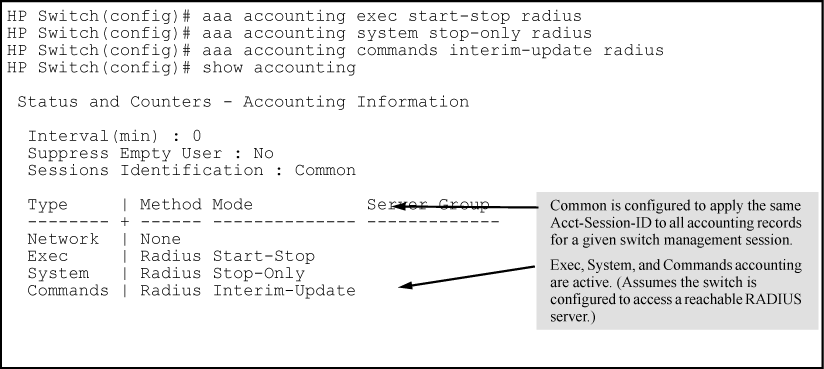
Configure one or more accounting service types to track:
-
Exec: Use
execif you want to collect accounting information on login sessions on the switch via the console, Telnet, or SSH. See Accounting services. -
System: Use
systemif you want to collect accounting data when:-
A system boot or reload occurs
-
System accounting is turned on or off
![[NOTE: ]](images/note.gif)
NOTE: There is no time span associated with using the
systemoption. It simply causes the switch to transmit whatever accounting data it currently has when one of the above events occurs.
-
-
Network: Use
networkif you want to collect accounting information on 802.1X port-based-access to the network by users connected to the physical ports on the switch. See Accounting services. -
Commands: When commands accounting is enabled, an accounting notice record is sent after the execution of each command.
These options are enabled separately, and define how the switch will send accounting data to a RADIUS server:
-
Start-Stop: Applies to the
exec,network, andsystemaccounting service types:-
Send a "start record accounting" notice at the beginning of the accounting session and a "stop record notice" at the end of the session. Both notices include the latest data the switch has collected for the requested accounting type.
-
Do not wait for an acknowledgement.
-
-
Stop-Only: Applies to the
network,exec,system, andcommandservice types, as described below:-
Send a stop record accounting notice at the end of the accounting session. The notice includes the latest data the switch has collected for the requested accounting type (
network,exec, orsystemservice types). For thecommandsservice type, sends the "Stop" accounting notice after execution of each CLI command. -
Do not wait for an acknowledgment.
-
-
Interim-Update: Applies only to the
commandservice type, and is intended for use when the optionalcommonsession ID is configured. Enablinginterim-updatein this case results in the command accounting records appearing as enclosed sub-parts of theexecservice type record for a given management session. Using interim-update when theuniquesession ID is configured has no effect because in this case, the different service types appear as separate accounting processes with separate Acct-Session-ID values.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Configuring |
|
|
Configures RADIUS accounting service type and how data will be sent to the RADIUS server.
Specifies an accounting service type to configure. See Accounting service types.
To configure RADIUS accounting on the switch with start-stop for Exec functions, stop-only for system functions, and interim-update for commands functions.
This example continues from Example of configuring accounting types and controls, where the session ID was configured as common.
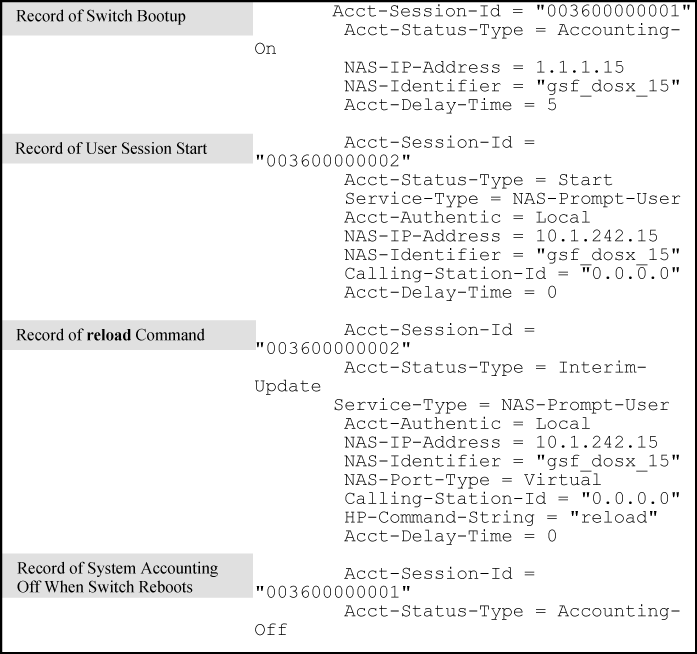
If the switch is configured with RADIUS accounting on the switch to use start-stop for Exec, System, and Command functions, as shown in Example of accounting session operation with "start-stop" enabled, there will be an "Accounting-On" record when the switch boots up and an "Accounting-Off" record when the switch reboots or reloads. (Assume that Acct-Session-Id is configured for common.)
These optional parameters give you additional control over accounting data.
-
Updates: In addition to using a
Start-StoporStop-Onlytrigger, you can optionally configure the switch to send periodic accounting record updates to a RADIUS server. -
Suppress: The switch can suppress accounting for an unknown user having no user name.
Syntax:
Syntax:
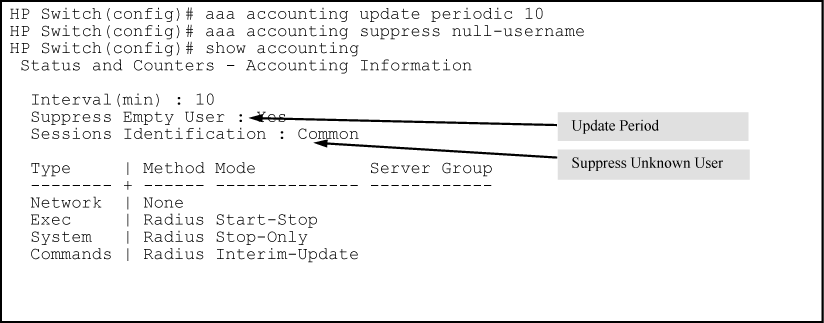
To continue the example in Example of configuring accounting types and controls, suppose you want the switch to:
-
Send updates every 10 minutes on in-progress accounting sessions.
-
Block accounting for unknown users (no username).