Before you begin:
If you are new to TACACS+ authentication, HP recommends that you first read the General authentication setup procedure and configure your TACACS+ servers before configuring authentication on the switch.
The switch offers three command areas for TACACS+ operation:
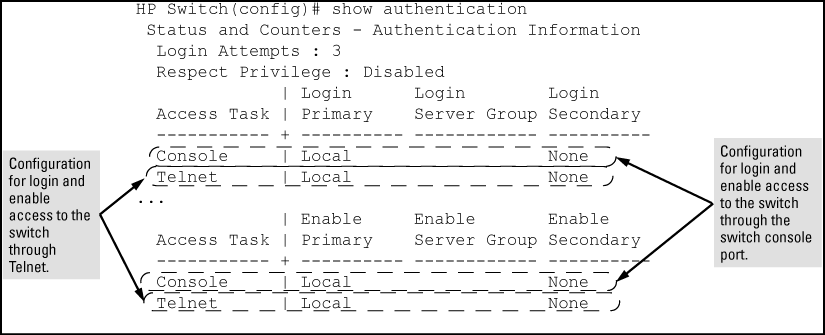
This command lists the number of login attempts the switch allows in a single login session, and the primary/secondary access methods configured for each type of access.
Syntax:
This example shows the default authentication configuration.
Syntax:
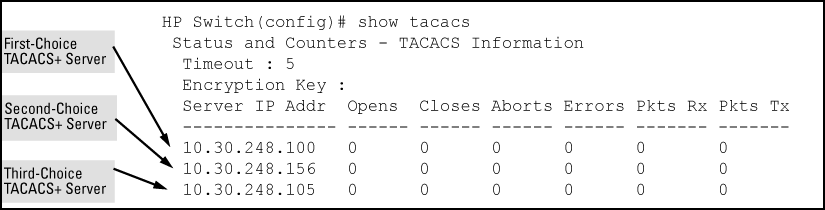
This command lists the timeout period, encryption key, and the IP addresses of the first-choice and backup TACACS+ servers the switch can contact.
Example:
The aaa authentication command configures access control for the following access methods:
-
Console
-
Telnet
-
SSH
-
Web
-
Port-access (802.1X)
However, TACACS+ authentication is only used with the console, Telnet, or SSH access methods. The command specifies whether to use a TACACS+ server or the switch local authentication, or (for some secondary scenarios) no authentication. This means that if the primary method fails, authentication is denied. The command also reconfigures the number of access attempts to allow in a session if the first attempt uses an incorrect username/password pair.
When using TACACS+ to control user access to the switch, first login with your username at the operator privilege level using the password for operator privileges, then login again with the same username but using the Manger password to obtain manager privileges. You can avoid this double login process by entering the privilege-mode option with the aaa authentication login command to enable TACACS+ for a single login. The switch authenticates your username/password, then requests the privilege level (operator or manager) that was configured on the TACACS+ server for this username/password. The TACACS+ server returns the allowed privilege level to the switch. You are placed directly into operator or manager mode, depending on your privilege level.
The no version of the above command disables TACACS+ single login capability.
AAA authentication parameters
Syntax
For the single login feature to work correctly you must check some entries in the User Setup on the TACACS+ server:
-
In the User Setup, scroll to the Advanced TACACS+ Settings section.
-
Make sure the radio button for "Max Privilege for any AAA Client" is checked and the level is set to 15, as shown in Advanced TACACS+ settings section of the TACACS+ server user setup.
-
Privileges are represented by the numbers 0 through 15, with zero allowing only operator privileges (and requiring two logins) and 15 representing root privileges. The root privilege level is the only level that will allow manager level access on the switch.
-
Scroll down to the section that begins with "Shell", see The shell section of the TACACS+ server user setup. Check the Shell box.
-
Check the Privilege level box and set the privilege level to 15 to allow "root" privileges. This allows you to use the single login option.
As shown in Configuring the switch TACACS+ server access, login and enable access is always available locally through a direct terminal connection to the switch console port. However, for Telnet access, you can configure TACACS+ to deny access if a TACACS+ server goes down or otherwise becomes unavailable to the switch.
Primary/secondary authentication table
| Access method and privilege level | Authentication options | Effect on access attempts | |
|---|---|---|---|
| Primary | Secondary | ||
| Console — Login | local | none* | Local username/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local username/password access. | |
| Console — Enable | local | none | Local username/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local username/password access. | |
| Telnet — Login | local | none* | Local username/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local username/password access. | |
| tacacs | none | If Tacacs+ server unavailable, denies access. | |
| Telnet — Enable | local | none | Local username/password access only. |
| tacacs | local | If Tacacs+ server unavailable, uses local username/password access. | |
| tacacs | none | If Tacacs+ server unavailable, denies access. | |
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: Regarding the use of local for login primary access: During local authentication (which uses passwords configured in the switch instead of in a TACACS+ server), the switch grants read-only access if you enter the operator password, and read-write access if you enter the manager password. For example, if you configure authentication on the switch with Telnet Login Primary as Local and Telnet Enable Primary as Tacacs, when you attempt to Telnet to the switch, you will be prompted for a local password. If you enter the switch local manager password (or, if there is no local manager password configured in the switch) you can bypass the TACACS+ server authentication for Telnet Enable Primary and go directly to read-write (manager) access. Thus, for either the Telnet or console access method, configuring Login Primary for Local authentication while configuring Enable Primary for TACACS+ authentication is not recommended, as it defeats the purpose of using the TACACS+ authentication. If you want Enable Primary log-in attempts to go to a TACACS+ server, then you should configure both Login Primary and Enable Primary for Tacacs authentication instead of configuring Login Primary to Local authentication. |
|
|
Access options
The following is a set of access options and the corresponding commands to configure them:
-
Console login (operator or read-only) access, primary using TACACS+ server and secondary using local
-
Console enable (manager or read/write) access, primary using TACACS+ server and secondary using local
-
Telnet login (operator or read-only) access, primary using TACACS+ server and secondary using local
-
Telnet enable (manager or read/write) access, primary using TACACS+ server and secondary using local
-
Deny access and close the session after failure of two consecutive username/password pairs
The tacacs-server command configures these parameters:
-
The host IP address(es) for up to three TACACS+ servers; one first-choice and up to two backups. Designating backup servers provides for a continuation of authentication services in case the switch is unable to contact the first-choice server.
-
An optional encryption key. This key helps to improve security, and must match the encryption key used in your TACACS+ server application. In some applications, the term "secret key" or "secret" may be used instead of "encryption key". If you need only one encryption key for the switch to use in all attempts to authenticate through a TACACS+ server, configure a global key. However, if the switch is configured to access multiple TACACS+ servers having different encryption keys, you can configure the switch to use different encryption keys for different TACACS+ servers.
-
The timeout value in seconds for attempts to contact a TACACS+ server. If the switch sends an authentication request, but does not receive a response within the period specified by the timeout value, the switch resends the request to the next server in its Server IP Addr list, if any. If the switch still fails to receive a response from any TACACS+ server, it reverts to whatever secondary authentication method was configured using the
aaa authenticationcommand (local or none), see Configuring the switch authentication methods.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: As described in General authentication setup procedure, HP recommends that youconfigure, test, and troubleshoot authentication via Telnet access before you configure authentication via console port access. This helps to prevent accidentally locking yourself out of switch access due to errors or problems in setting up authentication in either the switch or your TACACS+ server. |
|
|
Syntax:
Adds a TACACS+ server and optionally assigns a server-specific encryption key. If the switch is configured to access multiple TACACS+ servers having different encryption keys, you can configure the switch to use different encryption keys for different TACACS+ servers.
Configures an optional global encryption key. Keys configured in the switch must exactly match the encryption keys configured in the TACACS+ servers that the switch will attempt to use for authentication.
Syntax:
These commands are used to enable TACACS+ authorization.
Brief description of TACACS authorization options:
Local
Locally authenticated clients goes through local authorization. No authentication is performed for RADIUS/TACACS+ authenticate clients.
RADIUS
Locally authenticated clients go through local authorization. RADIUS authenticated clients go through RADIUS authorization. No authorization is performed for TACACS+ authenticated clients.
TACACS
TACACS authenticated clients go through TACACS authorization. No authorization is performed for RADIUS/locally authenticated users.
Auto
Uses the same method as Authentication and Authorization. For example local/radius/tacacs authenticated clients will go through local/radius/tacacs authorization respectively.
Authorization method:
Syntax:
Configures the dead time for unavailable TACACS+ servers. When a server stops responding, the switch ignores this for a given amount of time and proceeds immediately to the next backup. Configuring the dead time improves server response time as the switch no longer has to wait for connections to time out before contacting the next backup server. The default value of zero disables skipping unavailable servers.
Syntax:
Configure command authorization. For each command issued by the user, an authorization request is sent to the server. Command authorization can be applied to all commands or only manager-level commands
Syntax:
[no]
aaa accounting < exec | network | system | commands | start-stop | stop-only | intermim-update radius | syslog | tacacs>Configures the accounting service on the device. Accounting can be configured for EXEC sessions, network connection, commands and system. The accounting data is collected by a RADIUS, SYSLOG, or TACACS+ server.
NOTE: Network accounting is not supported through TACACS+ and SYSLOG.
session-idaccounting is not supported for TACACS+.
Syntax:
Shows accounting configuration parameters. If
sessionsis specified, the command will show accounting data for all active sessions.
Show authorization
HP Switch(config)# show accounting
Status and Counters - Accounting Information
Interval(min) : 0
Suppress Empty User : No
Sessions Identification : Common
Type | Method Mode Server Group
-------- + ------ -------------- ------------
Network | None
Exec | None
System | tacacs Start-Stop tacacs
Commands | None
Syntax:
Example:
HP Switch# show tacacs TACACS+ Information Timeout : 5 Source IP Selection : Outgoing Interface Encryption Key : Server Addr Opens Closes Aborts Errors Pkts Rx Pkts Tx OOBM ------------ ------ ------ ------ ------ ------- ------- ----
Syntax:
show tacacs
HP Switch# show tacacs TACACS+ Information Timeout : 5 Source IP Selection : Outgoing Interface Encryption Key : Server Addr Opens Closes Aborts Errors Pkts Rx Pkts Tx OOBM ------------ ------ ------ ------ ------ ------- ------- ----
show tacacs host
HP Switch(config)# show tacacs host <IP> TACACS+ Server Information Server Addr : 10.0.0.3 OOBM : Enabled Sessions Opened : Sessions Closed : Sessions Aborted : Sessions Error : Authentication : Packets Tx : 0 Packets Rx : 0 Timeouts : 0 Authorization : Packets Tx : 0 Packets Rx : 0 Timeouts : 0 Accounting : Packets Tx : 0 Packets Rx : 0 Timeouts : 0
Syntax:
Example:
HP Switch(config)# Active Accounted actions on SWITCH, User (n/a) Priv (n/a), Acct-Session-Id 0x013E00000006, System Accounting record, 1:45:34 Elapsed, system event ‘Accounting On’, method ‘radius’ Active Accounted actions on SWITCH, User (n/a) Priv (n/a), Task-id 0x013E00000006, Command Accounting record, 1:45:34 Elapsed, method ‘tacacs’.
Syntax:
Specifies the IP address of a device running a TACACS+ server application. Optionally, can also specify the unique, per-server encryption key to use when each assigned server has its own, unique key. For more on the encryption key, see Using the encryption key and the documentation provided with your TACACS+ server application.
The
oobmoption specifies that the TACACS+ traffic will go through the out-of-band management (OOBM) port.You can enter up to three IP addresses; one first-choice and two (optional) backups (one second-choice and one third-choice).
Use
show tacacsto view the current IP address list.If the first-choice TACACS+ server fails to respond to a request, the switch tries the second address, if any, in the show tacacs list. If the second address also fails, then the switch tries the third address, if any.
See Example of the switch TACACS+ configuration listing, the priority (first-choice, second-choice, and third-choice) of a TACACS+ server in the switch TACACS+ configuration depends on the order in which you enter the server IP addresses:
When there are no TACACS+ servers configured, entering a server IP address makes that server the first-choice TACACS+ server.
When there is one TACACS+ serves already configured, entering another server IP address makes that server the second-choice (backup) TACACS+ server.
When there are two TACACS+ servers already configured, entering another server IP address makes that server the third-choice (backup) TACACS+ server.
The above position assignments are fixed. If you remove one server and replace it with another, the new server assumes the priority position that the removed server had. For example, suppose you configured three servers, A, B, and C, configured in order:
If you removed server B and then entered server X, the TACACS+ server order of priority would be:
If there are two or more vacant slots in the TACACS+ server priority list and you enter a new IP address, the new address will take the vacant slot with the highest priority. Thus, if A, B, and C are configured as above and you (1) remove A and B, and (2) enter X and Y (in that order), then the new TACACS+ server priority list would be X, Y, and C.
The easiest way to change the order of the TACACS+ servers in the priority list is to remove all server addresses in the list and then re-enter them in order, with the new first-choice server address first, and so on.
To add a new address to the list when there are already three addresses present, you must first remove one of the currently listed addresses.
See also General authentication process using a TACACS+ server.
Syntax:
Specifies the optional, global "encryption key" that is also assigned in the TACACS+ servers that the switch will access for authentication. This option is subordinate to any "per-server" encryption keys you assign, and applies only to accessing TACACS+ servers for which you have not given the switch a "per-server" key. (See the
host <entry above.)ip-addr> [key <key-string>]You can configure a TACACS+ encryption key that includes a tilde (~) as part of the key, for example, "hp~switch". It is not backward compatible; the "~" character is lost if you use a software version that does not support the "~" character
For more on the encryption key, see Using the encryption key and the documentation provided with your TACACS+ server application.
Use the show running-config command to display the key information.
The running config file showing the host-specific key for TACACS+ with the “~” included
HP Switch(config)# show running-config Running configuration: ; J9627A Configuration Editor; Created on release #XX.15.XX hostname "Switch" vlan 1 name "DEFAULT_VLAN" untagged 1-24 ip address dhcp-bootp exit banner motd "good morning tacacs-server host 10.10.10.2 key "hp~networking" snmp-server community "public" unrestricted
Syntax:
Specifies how long the switch waits for a TACACS+ server to respond to an authentication request. If the switch does not detect a response within the timeout period, it initiates a new request to the next TACACS+ server in the list. If all TACACS+ servers in the list fail to respond within the timeout period, the switch uses either local authentication (if configured) or denies access (if
noneconfigured for local authentication).
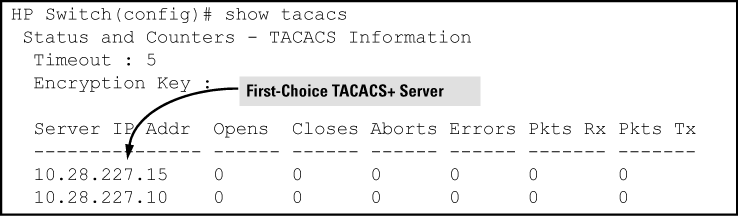
Suppose the switch is configured to use TACACS+ servers at 10.28.227.10 and 10.28.227.15. 10.28.227.15 was entered first and so is listed as the first-choice server:
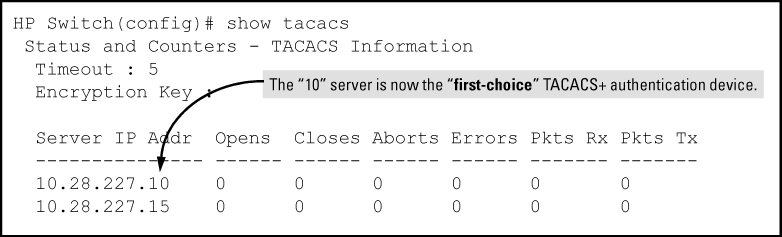
To move the "first-choice" status from the "15" server to the "10" server, use the no tacacs-server host < command to delete both servers, then use ip-addr>tacacs-server host < to re-enter the "10" server first, then the "15" server.ip-addr>
The servers would then be listed with the new "first-choice" server, that is:
To remove the 10.28.227.15 device as a TACACS+ server, you would use this command:
Use an encryption key in the switch if the switch will be requesting authentication from a TACACS+ server that also uses an encryption key. (If the server expects a key, but the switch either does not provide one, or provides an incorrect key, then the authentication attempt will fail.)
-
Use a global encryption key if the same key applies to all TACACS+ servers the switch may use for authentication attempts.
-
Use a per-server encryption key if different servers the switch may use will have different keys.(For more details on encryption keys, see Using the encryption key.
To configure north01 as a per-server encryption key:
An encryption key can contain up to 100 characters, without spaces, and is likely to be case-sensitive in most TACACS+ server applications.
To delete a per-server encryption key in the switch, re-enter the tacacs-server host command without the key parameter. For example, if you have north01 configured as the encryption key for a TACACS+ server with an IP address of 10.28.227.104 and you want to eliminate the key, you would use this command:
The timeout period specifies how long the switch waits for a response to an authentication request from a TACACS+ server before either sending a new request to the next server in the switch Server IP Address list or using the local authentication option. For example, to change the timeout period from 5 seconds (the default) to 3 seconds: