Before you configure MAC authentication:
-
Ensure that the VLANs are configured on the switch and that the appropriate port assignments have been made if you plan to use multiple VLANs with MAC authentication.
-
Ping the switch console interface to ensure that the switch is able to communicate with the RADIUS server you are configuring to support MAC authentication.
-
Configure the switch with the correct IP address and encryption key to access the RADIUS server.
-
Configure the switch for MAC authentication with the ports you will be using.
-
Test both the authorized and unauthorized access to your system to ensure that MAC authentication works properly on the ports you have chosen to configure for port-access.
MAC authentication requires that only a single entry containing the username and password is placed in the user database with the device's MAC address. This creates an opportunity for malicious device spoofing. The global password option configures a common MAC authentication password to use for all MAC authentications sent to the RADIUS server. This makes spoofing more difficult.
It is important that when implementing the global MAC authentication password option, that the user database on the RADIUS server has this password as the password for each device performing MAC authentication.
Syntax:
Configuring a global MAC authentication password
HP Switch(config)# aaa port-access mac-based password secretMAC1
HP Switch(config)# show port-access mac-based config
Port Access MAC-Based Configuration
MAC Address Format : no-delimiter
Password : secretMAC1
Unauth Redirect Configuration URL :
Unauth Redirect Client Timeout (sec) : 1800
Unauth Redirect Restrictive Filter : Disabled
Total Unauth Redirect Client Count : 0
Client Client Logoff Re-Auth Unauth Auth Cntrl
Port Enabled Limit Moves Period Period VLAN ID VLAN ID Dir
----- ------- ------ ------ ------- ------- ------- ------- -----
1 No 1 No 300 0 0 0 both
2 No 1 No 300 0 0 0 both
3 No 1 No 300 0 0 0 both
4 No 1 No 300 0 0 0 both
5 No 1 No 300 0 0 0 both
6 No 1 No 300 0 0 0 both
7 No 1 No 300 0 0 0 both
8 No 1 No 300 0 0 0 both
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The password value will display in an exported config file when |
|
|
Syntax:
aaa port-access mac-based addr-format <no-delimiter|single-dash|multi-dash|multi-colon|no-delimiter-uppercase|single-dash-uppercase|multi-dash-uppercase|multi-colon-uppercase>Specifies the MAC address format used in the RADIUS request message. This format must match the format used to store the MAC addresses in the RADIUS server.
no-delimiter: specifies an aabbccddeeff format.
single-dash: specifies an aabbcc-ddeeff format.
multi-dash: specifies an aa-bb-cc-dd-ee-ff format.
multi-colon: specifies an aa:bb:cc:dd:ee:ff format.
no-delimiter-uppercase: specifies an AABBCCDDEEFF format.
single-dash-uppercase: specifies an AABBCC-DDEEFF format
multi-dash-uppercase: specifies an AA-BB-CC-DD-EE-FF format
multi-colon-uppercase: specifies an AA:BB:CC:DD:EE:FF format.
Syntax:
Specifies the maximum number of authenticated MACs to allow on the port.
NOTE: On switches where MAC authenticated and 802.1X operate concurrently, this limit includes the total number of clients authenticated through both methods.
The limit of 256 clients only applies when there are fewer than 16,384 authentication clients on the entire switch. After the limit of 16,384 clients is reached, no additional authentication clients are allowed on any port for any method.
Syntax:
Allows client moves between the specified ports under MAC authenticated control. When enabled, the switch allows addresses to move without requiring a re-authentication.
When disabled, the switch does not allow moves and when one occurs, the user will be forced to re-authenticate. At least two ports (from ports and to ports) must be specified.
Use the
noform of the command to disable MAC address moves between ports under MAC authenticated control.
Syntax:
Syntax:
Syntax:
Syntax:
This feature allows administrators to configure custom messages that are displayed when authentication with the RADIUS server fails. The messages are appended to existing internal web pages that display during the authentication process. Messages can be configured using the CLI, or centrally using the RADIUS server, and can provide a description of the reason for a failure as well as possible steps to take to resolve the authentication issue. There is no change to the current web-based authentication functionality.
Syntax:
Specifies the text message (ASCII string) shown on the web page after an unsuccessful login attempt. The message must be enclosed in quotes.
The
[no]form of the command means that no message is displayed upon failure to authenticate.Default: The internal web page is used. No message will be displayed upon authentication failure.
access-denied-str: The text message that is appended to the end of the web page when there is an unsuccessful authentication request. The string can be up to 250 ASCII characters.
radius-response: Use the text message provided in the RADIUS server response to the authentication request.
Configuring an access denied message on the switch
HP Switch(config)# aaa port-access web-based access-denied-message “Please contact your system administrator to obtain authentication privileges.”
Output showing the custom access denied message
HP Switch(config)# show port-access web-based config
Port Access Web-based Configuration
DHCP Base Address : 192.168.0.0
DHCP Subnet Mask : 255.255.248.0
DHCP Lease Length : 10 seconds
Allow RADIUS-assigned dynamic (GVRP) VLANs[No]: Yes
Access Denied Message : Custom:
Please contact your system administrator to obtain authentication
privileges.
| Client Client Logoff Re-auth Unauth Auth Ctrl
Port | Enabled Limit Moves Period Period VLAN ID VLAN ID Dir
---- + ------- ------- ------- --------- --------- ------- ------- -----
1 | Yes 1 No 300 60 1 2 both
2 | Yes 18 No 999999999 999999999 0 0 both
3 | Yes 22 No 999999999 999999999 4096 4096 both
Access denied message when radius-response is configured
HP Switch(config)# show port-access web-based config
Port Access Web-based Configuration
DHCP Base Address : 192.168.0.0
DHCP Subnet Mask : 255.255.248.0
DHCP Lease Length : 10 seconds
Allow RADIUS-assigned dynamic (GVRP) VLANs[No]: Yes
Access Denied Message : Retrieved from Radius
| Client Client Logoff Re-auth Unauth Auth Ctrl
Port | Enabled Limit Moves Period Period VLAN ID VLAN ID Dir
---- + ------- ------- ------- --------- --------- ------- ------- -----
1 | Yes 1 No 300 60 1 2 both
2 | Yes 18 No 300 999999999 0 0 both
3 | Yes 22 No 300 999999999 4096 4096 both
Unauthenticated clients can be assigned to a specific static, untagged VLAN (unauth-vid), to provide access to specific (guest) network resources. If no VLAN is assigned to unauthenticated clients, the port is blocked and no network access is available.
The show running-config command displays the client’s information, including the configured access denied message.
Running configuration output displaying access denied message
HP Switch(config)# show running-config Running configuration: ; J9627A Configuration Editor; Created on release #XX.15.XX hostname "Switch" web-management ssl qos dscp-map 000000 priority 0 no stack auto-join vlan 1 name "DEFAULT_VLAN" untagged 1-14,19-24 ip address dhcp-bootp no untagged 15-18 exit vlan 100 name "auth-vid" untagged 15-18 ip address dhcp-bootp exit radius-server host 10.0.13.118 key 'secret' aaa authentication port-access eap-radius snmp-server community "public" Unrestricted aaa port-access web-based 5 aaa port-access web-based 5 auth-vid 100 aaa port-access web-based 5 unauth-vid 1 aaa port-access web-based dhcp-addr 172.18.0.0 255.255.255.0 aaa port-access web-based access-denied-message “Please contact your system administrator to obtain authentication privileges.”no autorun
Running configuration output when RADIUS response is configured
HP Switch(config)# show running-config Running configuration: ; J9627A Configuration Editor; Created on release #XX.15.XX hostname "Switch" web-management ssl qos dscp-map 000000 priority 0 no stack auto-join vlan 1 name "DEFAULT_VLAN" untagged 1-14,19-24 ip address dhcp-bootp no untagged 15-18 exit vlan 100 name "auth-vid" untagged 15-18 ip address dhcp-bootp exit radius-server host 10.0.13.118 key 'secret' aaa authentication port-access eap-radius snmp-server community "public" Unrestricted aaa port-access web-based 5 aaa port-access web-based 5 auth-vid 100 aaa port-access web-based 5 unauth-vid 1 aaa port-access web-based dhcp-addr 172.18.0.0 255.255.255.0 aaa port-access web-based access-denied-message radius-response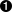
Syntax:
Displays the status of all ports or specified ports that are enabled for MAC authentication. The information displayed for each port includes:
Number of authorized and unauthorized clients.
VLAN ID number of the untagged VLAN used. If the switch supports MAC (untagged) VLANs,
MACbasedis displayed to show that multiple untagged VLANs are configured for authentication sessions.If tagged VLANs (statically configured or RADIUS-assigned) are used (
YesorNo.)If client-specific per-port CoS (Class of Service) values are configured (
YesorNo) or the numerical value of the CoS (802.1p priority) applied to all inbound traffic. For client-specific per-port CoS values, enter theshow port-access web-based clients detailedcommand.If per-port rate-limiting for inbound traffic is applied (
YesorNo) or the percentage value of the port's available bandwidth applied as a rate-limit value.If RADIUS-assigned ACLs are applied.
Information on ports not enabled for MAC authentication is not displayed.
Output for the show port-access mac-based command
HP Switch(config)# show port-access mac-based
Port Access MAC-Based Status
Auth Unauth Untagged Tagged Port % In RADIUS Cntl
Port Clients Clients VLAN VLANs COS Limit ACL Dir
---- ------- ------- -------- ------ -------- ------ ------ ------
1 1 1 2003 Yes 70000000 100 Yes both
2 2 0 MACbased No Yes Yes Yes both
3 4 0 1 Yes No No No both
Syntax:
Displays the session status, name, and address for each MAC authenticated client on the switch. The IP address displayed is taken from the DHCP binding table (learned through the DHCP Snooping feature).
If DHCP snooping is not enabled on the switch,
n/a(not available) is displayed for a client's IP address.If a MAC-authenticated client uses an IPv6 address,
n/a - IPv6is displayed.If DHCP snooping is enabled but no MAC-to-IP address binding for a client is found in the DHCP binding table,
n/a- no infois displayed.
Output for the show port-access mac-based clients command
HP Switch(config)# show port-access mac-based clients Port Access MAC-Based Client Status Port MAC Address IP Address Session Status ---- ------------- --------------------------------------- ------------- 1 001321-eb8063 2001:fecd:ba23:cd1f:dcb1:1010:9234:4088 unauthenticated 1 000000-111112 192.192.192.192 authenticated 2 000000-111111 n/a authenticating
Syntax:
Displays detailed information on the status of MAC authenticated client sessions on specified ports.
For HP Switch 2620, 2910al, and 2920-series:
This syntax shows session status, name, and address for each web-based authenticated client on the switch. The IP address displayed is taken from the DHCP binding table, learned through DHCP snooping.The following can appear if the client's IP address is not available:
n/a— DHCP snooping is not enabled on the switch;n/ais displayed for a client's IP address.
n/a-IPv6— a web-based authenticated client uses an IPv6 address.
n/a-no info— DHCP snooping is enabled but no MAC-to-IP address binding for a client is found in the DHCP binding table.
Output for the show port-access mac-based clients detailed command
HP Switch(config)# show port-access mac-based clients 1 detailed
Port Access MAC-Based Client Status Detailed
Client Base Details :
Port : 1
Session Status : authenticated Session Time(sec) : 6
Username : client1 MAC Address : 0010b5-891a9e
IP : n/a
Access Policy Details :
COS Map : 12345678 In Limit % : 98
Untagged VLAN : 4006 Out Limit % : 100
Tagged VLANs : 1, 3, 5, 6, 334, 4001
RADIUS-ACL List :
deny in udp from any to 10.2.8.233 CNT
Hit Count: 0
permit in udp from any to 10.2.8.233 CNT
Hit Count: 0
deny in tcp from any to 10.2.8.233 CNT
Hit Count: 0
permit in tcp from any to 10.2.8.233 CNT
Hit Count: 0
permit in tcp from
Syntax:
Displays the currently configured MAC authentication settings for all switch ports or specified ports, including:
MAC address format
Support for RADIUS-assigned dynamic VLANs (
YesorNo)Controlled direction setting for transmitting Wake-on-LAN traffic on egress ports
Authorized and unauthorized VLAN IDs
If the authorized or unauthorized VLAN ID value is
0, the default VLAN ID is used unless overridden by a RADIUS-assigned value.
Output for the show port-access mac-based config command
HP Switch(config)# show port-access mac-based config
Port Access MAC-Based Configuration
MAC Address Format : no-delimiter
Allow RADIUS-assigned dynamic (GVRP) VLANs [No] : No
Client Client Logoff Re-Auth Unauth Auth Cntrl
Port Enabled Limit Moves Period Period VLAN ID VLAN ID Dir
----- -------- ------ ------ ------ ------- -------- ------- ----
1 No 1 No 300 0 0 0 both
2 Yes 1 No 300 0 0 0 in
Syntax:
Displays more detailed information on the currently configured MAC authentication settings for specified ports.
Output for the show port-access mac-based config detail command
HP Switch(config)# show port-access mac-based config 1 detailed Port Access MAC-Based Detailed Configuration Port : 1 Web-based enabled : Yes Client Limit : 1 Client Moves : No Logoff Period : 300 Re-Auth Period : 0 Unauth VLAN ID : 0 Auth VLAN ID : 0 Max Requests : 3 Quiet Period : 60 Server Timeout : 30
Syntax:
Displays the currently configured web authentication settings for all switch ports or specified ports and includes RADIUS server-specific settings, such as:
Timeout waiting period.
Number of timeouts supported before authentication login fails.
Length of time (quiet period) supported between authentication login attempts.
Output for the show port-access mac-based config auth-server command
HP Switch(config)# show port-access mac-based config auth-server
Port Access MAC-Based Configuration
Client Client Logoff Re-Auth Max Quiet Server
Port Enabled Limit Moves Period Period Req Period Timeout
----- ------- ------ ------ ------- -------- ---- ------- --------
1 No 1 No 300 0 3 60 30
2 No 1 No 300 0 3 60 30
3 Yes 1 No 300 0 3 60 30
...
The table below shows the possible client status information that can be reported by a web-based or MAC-based ‘show... clients’ command.
| Reported status | Available network connection | Possible explanations |
|---|---|---|
| authenticated | Authorized VLAN | Client authenticated. Remains connected until logoff-period or reauth-period expires. |
| authenticating | Switch only | Pending RADIUS request. |
| rejected-no vlan | No network access |
|
| rejected-unauth vlan | Unauthorized VLAN only |
|
| timed out-no vlan | No network access | RADIUS request timed out. If unauth-vid is specified it cannot be successfully applied to the port. An authorized client on the port has precedence. Credentials resubmitted after quiet-period expires. |
| timed out-unauth vlan | Unauthorized VLAN only | RADIUS request timed out. After the quiet-period expires credentials are resubmitted when client generates traffic. |
| unauthenticated | Switch only | Waiting for user credentials. |