Before gaining access to the network, a client first presents authentication credentials to the switch. The switch then verifies the credentials with a RADIUS authentication server. Successfully authenticated clients receive access to the network, as defined by the System Administrator. Clients who fail to authenticate successfully receive no network access or limited network access as defined by the System Administrator.
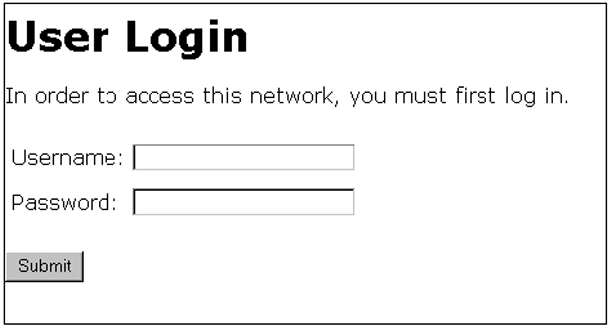
When a client connects to a web-based authentication enabled port, communication is redirected to the switch. A temporary IP address is assigned by the switch and a login screen is presented for the client to enter their username and password.
The default User Login screen is shown in Default user login screen.
When a client connects to the switch, it sends a DHCP request to receive an IP address to connect to the network. To avoid address conflicts in a secure network, you can specify a temporary IP address pool to be used by DHCP by configuring the dhcp-addr and dhcp-lease options when you enable web-based authentication with the aaa port-access web-based command.
The Secure Socket Layer (SSLv3/TLSv1) feature provides remote web-based access to the network via authenticated transactions and encrypted paths between the switch and management station clients capable of SSL/TLS. If you have enabled SSL on the switch, you can specify the ssl-login option when you configure web-based authentication so that clients who log in to specified ports are redirected to a secure login page (https://...) to enter their credentials.
The switch passes the supplied username and password to the RADIUS server for authentication and displays the following progress message:
If the client is authenticated and the maximum number of clients allowed on the port (client-limit) has not been reached, the port is assigned to a static, untagged VLAN for network access. After a successful login, a client can be redirected to a URL if you specify a URL value (redirect-url) when you configure web-based authentication.
The assigned VLAN is determined, in order of priority, as follows:
-
If there is a RADIUS-assigned VLAN, then, for the duration of the client session, the port belongs to this VLAN and temporarily drops all other VLAN memberships.
-
If there is no RADIUS-assigned VLAN, then, for the duration of the client session, the port belongs to the authorized VLAN (
auth-vidif configured) and temporarily drops all other VLAN memberships. -
If neither 1 or 2, above, apply, but the port is an untagged member of a statically configured, port-based VLAN, then the port remains in this VLAN.
-
If neither 1, 2, or 3, above, apply, then the client session does not have access to any statically configured, untagged VLANs and client access is blocked.
The assigned port VLAN remains in place until the session ends. Clients can be forced to reauthenticate after a fixed period of time (reauth-period) or at any time during a session (reauthenticate). An implicit logoff period can be set if there is no activity from the client after a given amount of time (logoff-period). In addition, a session ends if the link on the port is lost, requiring reauthentication of all clients. Also, if a client moves from one port to another and client moves have not been enabled (client-moves) on the ports, the session ends and the client must reauthenticate for network access. At the end of the session the port returns to its pre-authentication state. Any changes to the port's VLAN memberships made while it is an authorized port take affect at the end of the session.
A client can not be authenticated due to invalid credentials or a RADIUS server timeout. The max-retries parameter specifies how many times a client can enter their credentials before authentication fails. The server-timeout parameter sets how long the switch waits to receive a response from the RADIUS server before timing out. The max-requests parameter specifies how many authentication attempts can result in a RADIUS server timeout before authentication fails. The switch waits a specified amount of time (quiet-period) before processing any new authentication requests from the client.
Network administrators can assign unauthenticated clients to a specific static, untagged VLAN (unauth-vid), to provide access to specific (guest) network resources. If no VLAN is assigned to unauthenticated clients the port is blocked and no network access is available. Should another client successfully authenticate through that port any unauthenticated clients on the unauth-vid are dropped from the port.
When a client connects to a MAC authentication enabled port traffic is blocked. The switch immediately submits the client's MAC address (in the format specified by the addr-format) as its certification credentials to the RADIUS server for authentication.
If the client is authenticated and the maximum number of MAC addresses allowed on the port (addr-limit) has not been reached, the port is assigned to a static, untagged VLAN for network access.
The assigned VLAN is determined, in order of priority, as follows:
-
If there is a RADIUS-assigned VLAN, then, for the duration of the client session, the port belongs to this VLAN and temporarily drops all other VLAN memberships.
-
If there is no RADIUS-assigned VLAN, then, for the duration of the client session, the port belongs to the authorized VLAN (if configured) and temporarily drops all other VLAN memberships.
-
If neither 1 or 2, above, apply, but the port is an untagged member of a statically configured, port-based VLAN, then the port remains in this VLAN.
-
If neither 1, 2, or 3, above, apply, then the client session does not have access to any statically configured, untagged VLANs and client access is blocked.
The assigned port VLAN remains in place until the session ends. Clients may be forced to reauthenticate after a fixed period of time (reauth-period) or at any time during a session (reauthenticate). An implicit logoff period can be set if there is no activity from the client after a given amount of time (logoff-period). In addition, a session ends if the link on the port is lost, requiring reauthentication of all clients. Also, if a client moves from one port to another and client moves have not been enabled (addr-moves) on the ports, the session ends and the client must reauthenticate for network access. At the end of the session the port returns to its pre-authentication state. Any changes to the port’s VLAN memberships made while it is an authenticated port take affect at the end of the session.
A client may not be authenticated due to invalid credentials or a RADIUS server timeout. The server-timeout parameter sets how long the switch waits to receive a response from the RADIUS server before timing out. The maxrequests parameter specifies how many authentication attempts may result in a RADIUS server timeout before authentication fails. The switch waits a specified amount of time (quiet-period) before processing any new authentication requests from the client.
Network administrators may assign unauthenticated clients to a specific static, untagged VLAN (unauth-vid), to provide access to specific (guest) network resources. If no VLAN is assigned to unauthenticated clients the port remains in its original VLAN configuration. Should another client successfully authenticate through that port any unauthenticated clients are dropped from the port.