In the factory default configuration, VLAN support is enabled and all ports on the switch belong to the port-based, default VLAN (named DEFAULT_VLAN). This places all ports in the switch into one physical broadcast domain. In the factory-default state, the default VLAN is also the Primary VLAN.
-
You can partition the switch into multiple virtual broadcast domains by configuring one or more additional VLANs and moving ports from the default VLAN to the new VLANs.
-
The switch supports up to 2048 static and dynamic VLANs, with VIDs numbered up to 4094. You can change the name of the default VLAN, but not its VID, which is always 1.
-
You can remove all ports from the default VLAN by placing them in another port-based VLAN, but this VLAN remains and cannot be deleted from the switch.
For details on port VLAN settings, see Configuring or changing static VLAN per-port settings (CLI).
As certain features and management functions run on only one VLAN in the switch and because DHCP and Bootp can run per-VLAN, there is a need for a dedicated VLAN to manage these features and ensure that multiple instances of DHCP or Bootp on different VLANs do not result in conflicting configuration values for the switch.
The Primary VLAN is the VLAN the switch uses to run and manage these features and data. In the factory-default configuration, the switch designates the default VLAN (DEFAULT_VLAN; VID=1) as the Primary VLAN. However you can designate another static, port-based VLAN as primary.
To summarize, designating a non-default VLAN as primary means that:
-
The switch reads DHCP responses on the Primary VLAN instead of on the default VLAN. This includes such DHCP-resolved parameters as the TimeP server address, Default TTL and IP addressing—including the Gateway IP address—when the switch configuration specifies DHCP as the source for these values.
-
The default VLAN continues to operate as a standard VLAN you cannot delete it or change its VID.
-
Any ports not specifically assigned to another VLAN will remain assigned to the Default VLAN, even if it is the Primary VLAN.
Candidates for Primary VLAN include any static, port-based VLAN currently configured on the switch.
Protocol-Based VLANs and dynamic (GVRP-learned) VLANs that have not been converted to a static VLAN cannot be the Primary VLAN. To display the current Primary VLAN, use the CLI show vlan command.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If you configure a non-default VLAN as the Primary VLAN, you cannot delete that VLAN unless you first select a different VLAN to serve as primary. If you manually configure a gateway on the switch, it ignores any gateway address received via DHCP or Bootp. To change the Primary VLAN configuration, see Changing VLAN support settings (Menu). |
|
|
Configuring a secure Management VLAN creates an isolated network for managing the HP switches that support this feature. Access to a secure Management VLAN and the switch's management functions (Menu and CLI), is available only through ports configured as members.
-
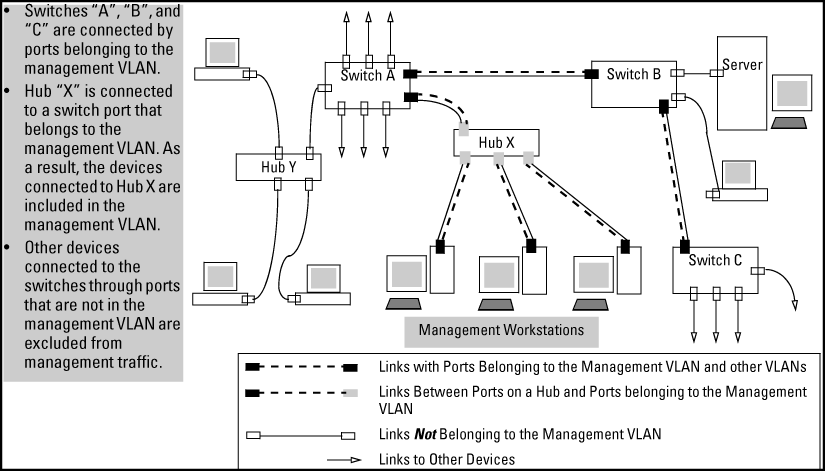
Multiple ports on the switch can belong to the Management VLAN. This allows connections for multiple management stations to the Management VLAN, while allowing Management VLAN links between switches configured for the same Management VLAN.
-
Only traffic from the Management VLAN can manage the switch, which means that only the workstations and PCs connected to ports belonging to the Management VLAN can manage and reconfigure the switch.
Potential security breaches in a network
This illustrates use of the Management VLAN feature to support management access by a group of management workstations.
Management VLAN control in a LAN
In this example, Workstation 1 has management access to all three switches through the Management VLAN, while the PCs do not. This is because configuring a switch to recognize a Management VLAN automatically excludes attempts to send management traffic from any other VLAN.
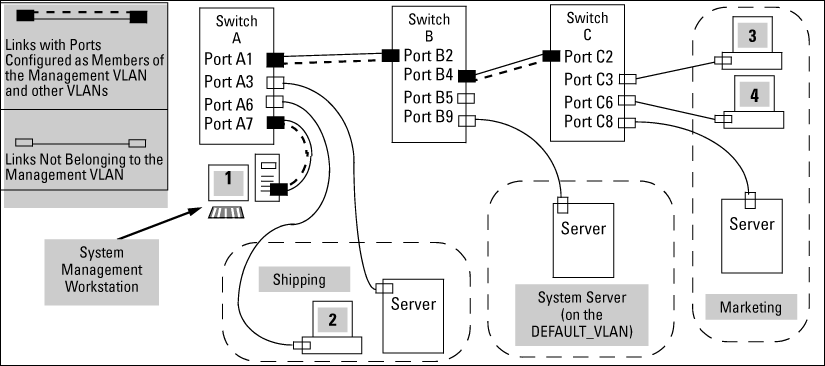
VLAN membership in Management VLAN control in a LAN
| Switch | A1 | A3 | A6 | A7 | B2 | B4 | B5 | B9 | C2 | C3 | C6 | C8 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Management VLAN (VID = 7) | Y | N | N | Y | Y | Y | N | N | Y | N | N | N |
| Marketing VLAN (VID = 12) | N | N | N | N | N | N | N | N | N | Y | Y | Y |
| Shipping Dept. VLAN (VID = 20) | N | Y | Y | N | N | N | N | N | N | N | N | N |
| DEFAULT-VLAN (VID = 1) | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y | Y |
See Configuring a secure Management VLAN (CLI) for configuration details.
-
The Management VLAN feature applies to both IPv4 and IPv6 traffic.
-
Routing between the Management VLAN and other VLANs is not allowed.
-
If there are more than 25 VLANs configured on the switch, reboot the switch after configuring the Management VLAN.
-
If you implement a Management VLAN in a switch mesh environment, all meshed ports on the switch will be members of the Management VLAN.
-
Only one Management VLAN can be active in the switch. If one Management VLAN VID is saved in the startup-config file and you configure a different VID in the running-config file, the switch uses the running-config version until you either use the
write-memorycommand or reboot the switch. -
During a Telnet session to the switch, if you configure the Management VLAN to a VID that excludes the port through which you are connected to the switch, you will continue to have access only until you terminate the session by logging out or rebooting the switch.
![[NOTE: ]](images/note.gif)
NOTE: The Management VLAN feature does not control management access through a direct connection to the switch's serial port.
-
During a WebAgent session, if you configure the Management VLAN to a VID that excludes the port through which you are connected to the switch, you will continue to have access only until you close the browser session or reboot the switch.
-
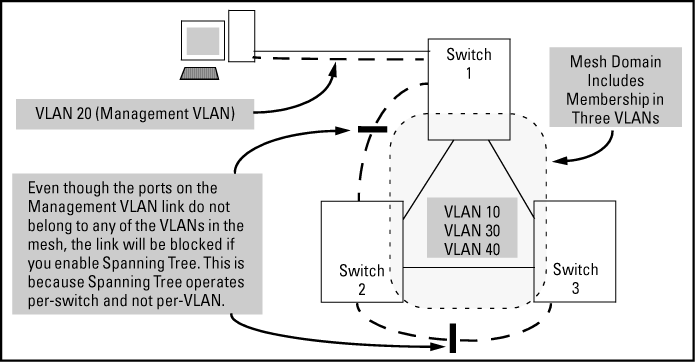
Enabling Spanning Tree between a pair of switches where there are multiple links using separate VLANs, including the Management VLAN, will force the blocking of one or more links. This may include the link carrying the Management VLAN, which will cause loss of management access to some devices. This can also occur where meshing is configured and the Management VLAN is configured on a separate link.
-
Monitoring Shared Resources: The Management VLAN feature shares internal switch resources with several other features. The switch provides ample resources for all features. However, if the internal resources become fully subscribed, the Management VLAN feature cannot be configured until the necessary resources are released from other uses. For information on determining the current resource availability and usage, see the appendix titled "Monitoring Resources" in the Management and Configuration Guide for your switch.