ACL logging enables the switch to generate a message when IP traffic meets the criteria for a match with an ACE that results in an explicit “deny” or “permit” action. You can use ACL logging to help:
-
Test your network to ensure that your ACL configuration is detecting and denying or “permitting” the IPv4 traffic you do not want forwarded.
-
Receive notification when the switch detects attempts to forward IPv4 traffic you have designed your ACLs to reject (deny) or allow (permit).
The switch sends ACL messages to and optionally to the current console, Telnet, or SSH session. You can use logging < > to configure up to six server destinations.
These requirements are described in more detail in Enabling ACL logging on the switch.
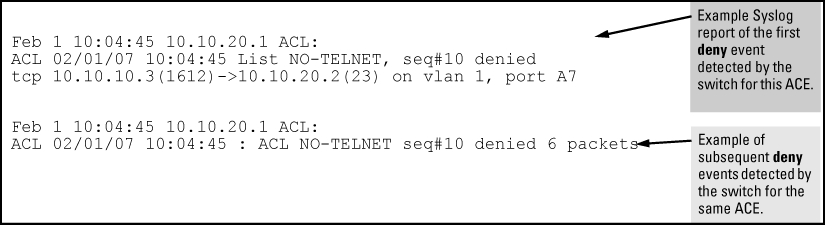
When the switch detects a packet match with an ACE and the ACE includes either the deny or permit action and the optional log parameter, an ACL log message is sent to the designated debug destination.
The first time a packet matches an ACE with deny or permit and log configured, the message is sent immediately to the destination and the switch starts a wait-period of approximately five minutes. (The exact duration of the period depends on how the packets are internally routed.) At the end of the collection period, the switch sends a single-line summary of any additional “deny” or “permit” matches for that ACE (and any other “deny” or “permit” ACEs for which the switch detected a match).
If no further log messages are generated in the wait-period, the switch suspends the timer and resets itself to send a message as soon as a new “deny” or “permit” match occurs. If subsequent packets matching the already logged ACL entries are detected, then a new logged event will be generated that summarizes the number of packets that matched each specific entry (with the time period). The data in the message includes the information illustrated in Content of a message generated by an ACL-deny action.
-
If you are using a Syslog server, use the
logging <command to configure the Syslog server IPv4 address. Ensure that the switch can access any Syslog server you specify.ip-addr> -
Use
logging facility syslogto enable the logging for Syslog operation. -
Use the
debugdestinationcommand to configure one or more log destinations. Destination options includeloggingandsession. For more information on debug, see the “Troubleshooting” section of the Management and Configuration Guide for your switch. -
Use
debug aclordebug allto configure the debug operation to include ACL messages. -
Configure one or more ACLs with the
denyorpermitaction and thelogoption.
HP Switch(config)# ip access-list extended NO-TELNET
HP Switch(config-ext-nacl)# remark "DENY 10.10.10.3 TELNET TRAFFIC IN"
HP Switch(config-ext-nacl)# deny tcp host 10.10.10.3 any eq telnet log
HP Switch(config-ext-nacl)# permit ip any any
HP Switch(config-ext-nacl)# exit
HP Switch(config)# logging 10.10.20.3
HP Switch(config)# logging facility syslog
HP Switch(config)# debug destination logging
HP Switch(config)# debug destination session
HP Switch(config)# debug acl
HP Switch(config)# write mem
HP Switch(config)# show debug
Debug Logging
Destination:
Logging --
10.10.20.3
Facility = syslog
Session
Enabled debug types:
event
acl log
HP Switch(config)# show access-list config
ip access-list extended "NO-TELNET"
10 remark "DENY 10.10.10.3 TELNET TRAFFIC"
10 deny tcp 10.10.10.5 0.0.0.0 0.0.0.0 255.255.255.255 eq 23 log
20 permit ip 0.0.0.0 255.255.255.255 0.0.0.0 255.255.255.255
exit
By default, the wait period for logging "deny" matches (described above in "ACL Logging Operation") is approximately five minutes (300 seconds). You can manually set the wait period timer to an interval between 30 and 300 seconds, using the access-list command from the config context. This setting is stored in the switch configuration.
Syntax:
access-list logtimer <default<30-300>>This command sets the wait period timer for logging "deny" or “permit“ messages to the SYSLOG server or other destination device. The first time a packet matches an ACE with deny and
logconfigured, the message is sent immediately to the destination and the switch starts a wait period of approximately five minutes (default value). The exact duration of the period depends on how the packets are internally routed. At the end of the wait period, the switch sends a single-line summary of any additional “deny“ or “permit” matches for that ACE, and any other “deny“ or “permit” ACEs for which the switch detected a match. If no further log messages are generated in the wait period, the switch suspends the timer and resets itself to send a message as soon as a new “deny“ or “permit” match occurs.
ACL statistics counters provide a means for monitoring ACL performance by using counters to display the current number of matches the switch has detected for each ACE in an ACL assigned to a switch interface. This can help in determining whether a particular traffic type is being filtered by the intended ACE in an assigned list, or if traffic from a particular device or network is being filtered as intended.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This section describes the command for monitoring static ACL performance. To monitor RADIUS-assigned ACL performance, use either of the following commands: |
|
|