A standard ACL uses only source IPv4 addresses in its ACEs. This type of ACE is useful when you need to:
-
Permit or deny any IPv4 traffic based on source address only.
-
Quickly control the IPv4 traffic from a specific address. This allows you to isolate IPv4 traffic problems generated by a specific device, group of devices, or a subnet threatening to degrade network performance. This gives you an opportunity to troubleshoot without sacrificing performance for users outside of the problem area.
A named, standard ACL is identified by an alphanumeric string of up to 64 characters and is created by entering the Named ACL (nacl) context. A numbered, standard ACL is identified by a number in the range of 1-99 and is created without having to leave the global config context. Note that the CLI Command syntax for creating a named ACL differs from the Command syntax for creating a numbered ACL. For example, the first pair of entries below illustrate how to create (or enter) a named, standard ACL and enter an ACE. The next entry illustrates creating a numbered, standard ACL with the same ACE.
HP Switch(config)# ip access-list standard Test-List HP Switch(config-std-nacl)# permit host 10.10.10.147HP Switch(config)# access-list 1 permit host 10.10.10.147
Note that once a numbered ACL has been created, it can be accessed using the named ACL method. This is useful if it becomes necessary to edit a numbered ACL by inserting or removing individual ACEs. Inserting or deleting an ACE is done by sequence number, and requires the Named ACL (nacl) context. The switch allows a maximum of 2048 unique ACL identities (IPv4 and IPv6 combined).
This section describes the commands for performing the following:
This command is a prerequisite to entering or editing ACEs in a named ACL.
Syntax:
Places the CLI in the "Named ACL" (
nacl) context specified by the <name-str> alphanumeric identifier. This enables entry of individual ACEs in the specified ACL. If the ACL does not already exist, this command creates it.
<name–str>: Specifies an identifier for the ACL. Consists of an alphanumeric string of up to 64 case-sensitive characters. Including spaces in the string requires that you enclose the string in single or double quotes.
Configuring ACEs is done after using the ip access-list standard < command described above to enter the "Named ACL" ( name-str>nacl) context of an access list. See Configuring ACEs in a named, standard ACL.
Syntax:
Executing this command appends the ACE to the end of the list of ACEs in the current ACL. In the default ACL configuration, ACEs are automatically assigned consecutive sequence numbers in increments of 10 and can be renumbered using
resequence(See Resequencing the ACEs in an ACL.)
NOTE: To insert a new ACE between two existing ACEs, precede
denyorpermitwith an appropriate sequence number. See Inserting an ACE in an existing ACL.
For named ACLs, used in the "Named ACL" (
nacl) context to configure an ACE. Specifies whether the ACE denies or permits a packet matching the criteria in the ACE, as described below.
Defines the source IPv4 address (SA) a packet must carry for a match with the ACE.
host <SA>: Specifies only packets having <SA> as the source. Use this criterion when you want to match the IPv4 packets from a single source address.
SA <mask>orSA/mask–length: Specifies packets received from either a subnet or a group of IPv4 addresses. The mask format can be in either dotted-decimal format or CIDR format (number of significant bits).Mask Application: The mask is applied to the IPv4 address in the ACE to define which bits in a packet's SA must exactly match the SA configured in the ACE and which bits need not match. For example:
10.10.10.1/24and10.10.10.1 0.0.0.255both define any address in the range of 10.10.10.(1-255).
NOTE: Specifying a group of contiguous addresses may require more than one ACE.
[log]: This option generates an ACL log message if:
The action is deny or permit. (*Applicable only to the HP Switch 2620 series.)
The action is deny. (*Applicable only to the HP Switch 2910al and 2920 series.)
Use the debug command to direct ACL logging output to the current console session and/or to a Syslog server. Note that you must also use the
logging <command to specify the addresses of Syslog servers to which you want log messages sent.ip-addr>
Example:
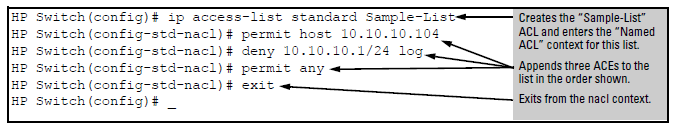
This example creates an ACL that:
Screen output listing the sample-list ACL content
HP Switch(config)# show access-list Sample-List
Access Control Lists
Name: Sample-List
Type: Standard
Applied: No
SEQ Entry
--------------------------------------------------------
10 Action: permit
IP : 10.10.10.104 Mask: 0.0.0.0
20 Action: deny (log)
IP : 10.10.10.1 Mask: 0.0.0.255
30 Action: permit
IP : 0.0.0.0 Mask: 255.255.255.255
Note that each ACE is automatically assigned a sequence number.
Use the following steps when creating or adding to a numbered, standard ACL:
The following describes the commands for performing these steps.
This command is an alternative to using ip access-list standard <name-str> and does not use the "Named ACL"(nacl) context.
Syntax:
Appends an ACE to the end of the list of ACEs in the current IPv4 standard, numbered ACL. If the ACL does not already exist, creates both the ACL and its first ACE. In the default configuration, ACEs are automatically assigned consecutive sequence numbers in increments of 10 and can be renumbered using
resequence, see Resequencing the ACEs in an ACL.
Specifies the ACL identifier as a number. The switch interprets an ACL with a value in this range as a standard ACL (which filters all IPv4 traffic on the basis of SA). To create a standard access list with an alphanumeric name (
name-str) instead of a number, see Configuring named, standard ACLs.
Specifies whether the ACE denies or permits a packet matching the criteria in the ACE, as described next.
Defines the source IPv4 address (SA) a packet must carry for a match with the ACE.
SA <mask> or SA/mask–length– Specifies packets received from an SA, where the SA is either a subnet or a group of IPv4 addresses. The mask format can be in either dotted-decimal format or CIDR format (number of significant bits).
SA Maskapplication: The mask is applied to the SA in the ACE to define which bits in a packet's SA must exactly match the SA configured in the ACL and which bits need not match.Example:
10.10.10.1/24 and 10.10.10.1 0.0.0.255 both define any address in the range of 10.10.10.(1–255).
NOTE: Specifying a group of contiguous addresses may require more than one ACE.
This option can be used after the SA to generate an Event Log message if:
The action is deny or permit.
There is a match.
ACL logging is enabled.
This example creates a standard, numbered ACL with the same ACE content as show in Commands used to create a standard, named ACL.
Standard, numbered ACL with the same ACEs as the standard, named ACL in Commands used to create a standard, named ACL
HP Switch(config)# access-list 17 permit host 10.10.10.104
HP Switch(config)# access-list 17 deny 10.10.10.1/24 log
HP Switch(config)# access-list 17 permit any
HP Switch(config)# show access-list 17
Access Control Lists
Name: 17
Type: Standard
Applied: No
SEQ Entry
-------------------------------------------------------
10 Action: permit
IP : 10.10.10.104 Mask: 0.0.0.0
20 Action: deny (log)
IP : 10.10.10.1 Mask: 0.0.0.255
30 Action: permit
IP : 0.0.0.0 Mask: 255.255.255.255
Note that each ACE is automatically assigned a sequence number.
![[NOTE: ]](images/note.gif)