A RADIUS-assigned ACL is configured on a RADIUS server and dynamically assigned by the server to filter IP traffic from a specific client after the client is authenticated by the server.
The information in this section describes how to apply RADIUS-assigned ACLs on the switch, and assumes a general understanding of ACL structure and operation. If you need information on ACL filtering criteria, design, and operation, see the following:
RADIUS-assigned ACLs enhance network and switch management access security and traffic control by permitting or denying authenticated client access to specific network resources and to the switch management interface. This includes preventing clients from using TCP or UDP applications, ICMP packet types, and IGMP (IPv4 only) if you do not want their access privileges to include these capabilities.
The switch supports RADIUS-assigned ACLs for the following traffic applications:
-
Inbound IPv4 traffic only
-
Inbound IPv4 and IPv6 traffic
This feature is designed for use on the network edge to accept RADIUS-assigned ACLs for Layer-3 filtering of IP traffic entering the switch from authenticated clients. A given RADIUS-assigned ACL is identified by a unique username/password pair or client MAC address, and applies only to IP traffic entering the switch from clients that authenticate with the required, unique credentials. The switch allows multiple RADIUS-assigned ACLs on a given port, up to the maximum number of authenticated clients allowed on the port. Also, a RADIUS-assigned ACL for a given client's traffic can be assigned regardless of whether other ACLs assigned to the same port are statically configured on the switch.
A RADIUS-assigned ACL filters IP traffic entering the switch from the client whose authentication caused the ACL assignment. Filter criteria is based on:
-
Destination address
-
IPv4 or IPv6 traffic type (such as TCP and UDP traffic)
Implementing the feature requires:
-
RADIUS authentication using the 802.1X, web-based authentication, or MAC authentication available on the switch to provide client authentication services
-
Configuring one or more ACLs on a RADIUS server (instead of the switch), and assigning each ACL to the username/password pair or MAC address of the client(s) you want the ACLs to support
Using RADIUS to dynamically apply ACLs to clients on edge ports enables the switch to filter IP traffic coming from outside the network, thus removing unwanted IP traffic as soon as possible and helping to improve system performance. Also, applying RADIUS-assigned ACLs to the network edge is likely to be less complex than configuring static port and VLAN-based ACLs in the network core to filter unwanted IP traffic that could have been filtered at the edge.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: A RADIUS-assigned ACL filters inbound IP traffic on a given port from the client whose authentication triggered the ACL assignment to the port. A RADIUS-assigned ACL can be applied regardless of whether IP traffic on the port is already being filtered by other, static ACLs that are already assigned. Simultaneous ACL activity supported per-port lists the supported per-port ACL assignment capacity. ACLs enhance network security by blocking selected IP traffic, and can serve as one aspect of network security. However, because ACLs do not protect from malicious manipulation of data carried in IP packet transmissions, they should not be relied upon for a complete edge security solution. Depending on the ACL configuration in the RADIUS server, the ACLs described in this section filter either IPv4 traffic only or both IPv4 and IPv6 traffic. These ACLs do not filter non-IP traffic such as AppleTalk and IPX. |
|
|
Simultaneous ACL activity supported per-port[1]
| ACL type | Function | IPv4 | IPv6 |
|---|---|---|---|
| Port ACL | Static ACL assignment to filter inbound IP traffic on a specific port. | 1 | 1 |
| RADIUS-assigned ACL | Dynamic ACL assignment to filter inbound IP traffic from a specific client on a given port. | 1-32[a] | 1-32[a] |
|
[a] One per authenticated client, up to a maximum of 32 clients per-port for 802.1X, web-based authentication, and MAC-Authentication methods combined. |
|||
Contrasting dynamic (RADIUS-assigned) and static ACLs highlights several key differences between the static ACLs configurable on switch VLANs and ports, and the dynamic ACLs that can be assigned by a RADIUS server to filter IP traffic from individual clients.
Contrasting dynamic (RADIUS-assigned) and static ACLs
| RADIUS-assigned ACLs | Static port and VLAN ACLs | ||||||
|---|---|---|---|---|---|---|---|
| Configured in client accounts on a RADIUS server. | Configured on switch ports and VLANs. | ||||||
| Designed for use on the edge of the network where filtering of IP traffic entering the switch from individual, authenticated clients is most important and where clients with differing access requirements are likely to use the same port. | Designed for use where the filtering needs focus on static configurations covering:
|
||||||
| Implementation requires client authentication. | Client authentication not a factor. | ||||||
| Identified by the credentials (username/password pair or the MAC address) of the specific client the ACL is intended to service. | Identified by a number in the range of 1-199 or an alphanumeric name. | ||||||
| Supports dynamic assignment to filter only the IP traffic entering the switch from an authenticated client on the port to which the client is connected. (IPv6 traffic can be switched; IPv4 traffic can be routed or switched. For either IP traffic family, includes traffic having a DA on the switch itself.) | Supports static assignments to filter:
|
||||||
| When the authenticated client session ends, the switch removes the RADIUS-assigned ACL from the client port. | Remains statically assigned to the port or VLAN. | ||||||
|
Allows one RADIUS-assigned ACL per authenticated client on a port. (Each such ACL filters traffic from a different, authenticated client.)
|
Simultaneously supports all of the following static assignments affecting a given port:
|
||||||
| Supports IPv6 ACLs and IPv4 extended ACLs. “IPv6 Access Control Lists (ACLs)” in the IPv6 Configuration Guide for your switch. | Supports IPv6 ACLs and standard and extended IPv4 ACLs. | ||||||
|
A given RADIUS-assigned ACL operates on a port to filter only the IP traffic entering the switch from the authenticated client corresponding to that ACL, and does not filter IP traffic inbound from other authenticated clients. (The traffic source is not a configurable setting.) |
A static port ACL can be applied on a port to filters either IPv4 or IPv6 traffic entering the switch through that port. |
||||||
| Requires client authentication by a RADIUS server configured to dynamically assign an ACL to a client on a switch port, based on client credentials. | No client authentication requirement. | ||||||
| ACEs allow a counter (cnt) option that causes a counter to increment when there is a packet match. |
The Also, ACEs allow a |
A RADIUS-assigned ACL configured on a RADIUS server is identified and invoked by the unique credentials (username/password pair or a client MAC address) of the specific client the ACL is intended to service. Where the username/password pair is the selection criteria, the corresponding ACL can also be used for a group of clients that all require the same ACL policy and use the same username/password pair. Where the client MAC address is the selection criteria, only the client having that MAC address can use the corresponding ACL. When a RADIUS server authenticates a client, it also assigns the ACL configured with that client's credentials to the client's port. The ACL then filters the client's inbound IP traffic and denies (drops) any such traffic that is not explicitly permitted by the ACL.
-
If the filter rule used for a RADIUS-based ACL is one of the options that specifies only IPv4 traffic, then the ACL will implicitly deny any inbound IPv6 traffic from the authenticated client.
-
If the filter rule used for a RADIUS-based ACL is the option for specifying both IPv4 and IPv6 traffic, then the ACL filter both IP traffic types according to the ACEs included in the RADIUS-assigned ACL.
When the client session ends, the switch removes the RADIUS-assigned ACL from the client port.
When multiple clients supported by the same RADIUS server use the same credentials, they will all be serviced by different instances of the same ACL. (The actual IP traffic inbound from any client on the switch carries a source MAC address unique to that client. The RADIUS-assigned ACL uses this MAC address to identify the traffic to be filtered.)
These steps suggest a process for using RADIUS-assigned ACLs to establish access policies for client IP traffic.
-
Determine the polices you want to enforce for authenticated client traffic inbound on the switch.
-
Plan ACLs to execute traffic policies:
-
Apply ACLs on a per-client basis where individual clients need different traffic policies or where each client must have a different username/password pair or will authenticate using MAC authentication.
-
Apply ACLs on a client group basis where all clients in a given group can use the same traffic policy and the same username/password pair.
-
-
Configure the ACLs on a RADIUS server accessible to the intended clients.
-
Configure the switch to use the desired RADIUS server and to support the desired client authentication scheme. Options include 802.1X, web-based authentication, or MAC authentication. (Note that the switch supports the option of simultaneously using 802.1X with either web-based or MAC authentication.)
-
Test client access on the network to ensure that your RADIUS-assigned ACL application is properly enforcing your policies.
For further information common to all IPv4 or IPv6 ACL applications, see the IPv4 Configuration Guide or IPv6 Configuration Guide for your switch.
Packet-filtering in an applied ACL is sequential, from the first ACE in the ACL to the implicit deny any any following the last explicit ACE. This operation is the same regardless of whether the ACL is applied dynamically from a RADIUS server or statically in the switch configuration.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: ACLs can enhance network security by blocking selected IP traffic, and can serve as one aspect of maintaining network security. However, because ACLs do not provide user or device authentication, or protection from malicious manipulation of data carried in IP packet transmissions, they should not be relied upon for a complete security solution. |
|
|
-
Relating a client to a RADIUS-assigned ACL: A RADIUS-assigned ACL for a particular client must be configured in the RADIUS server under the authentication credentials the server should expect for that client. If the client must authenticate using 802.1X and/or web-based authentication, the username/password pair forms the credential set. If authentication is through MAC Authentication, then the client MAC address forms the credential set. See Configuring an ACL in a RADIUS server.
-
Multiple clients using the same username/password pair: Multiple clients using the same username/password pair will use duplicate instances of the same ACL.
-
Limits for ACEs in RADIUS-assigned ACLs: The switch supports up to 80 characters in a single ACE. Exceeding this limit causes the related client authentication to fail.
-
Effect of other, statically configured ACLs: Suppose that port B1 belongs to VLAN "Y" and has a RADIUS-assigned ACL to filter inbound traffic from an authenticated client. Port B1 is also configured with IPv4 and IPv6 static port ACLs, and VLAN "Y" is statically configured with IPv4 and IPv6 VACLs.
The following information provides general guidelines for configuring a RADIUS server to specify RADIUS-assigned ACLs. It also provides an example configuration for a FreeRADIUS server application. To configure services on a specific RADIUS server application, see the documentation provided with that application.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: This application requires a RADIUS server having an IPv4 address. Clients can be dual-stack, IPv4-only or IPv6-only. |
|
|
A RADIUS-assigned ACL configuration in a RADIUS server includes the following elements:
-
Nas-Filter-Rule attributes: standard and vendor-specific
-
ACL configuration, entered in the server, and associated with specific username/password or MAC address criteria, and comprised of ACEs entered in the server
A RADIUS-assigned ACL includes:
-
One or more explicit
permitand/ordenyACEs -
An implicit
deny in ip from any to anyACE automatically applied after the last operator-created ACE
Nas-filter-rule attribute options
| Service | Control Method and Operating Notes | ||||||
|---|---|---|---|---|---|---|---|
|
ACLs applied to client traffic inbound to the switch Assigns a RADIUS-configured ACL to filter inbound packets received from a specific client authenticated on a switch port. |
Standard Attribute: 92 This is the preferred attribute for use in RADIUS-assigned ACLs to configure ACEs to filter IPv4 and IPv6 traffic. Entry for IPv4-Only ACE To Filter Client Traffic: Nas-filter-Rule="< permit or deny ACE > "(Standard Attribute 92)For example: Nas-filter-Rule=permit in tcp from any to any Entries for IPv4/IPv6 ACE To Filter Client Traffic:
For example: HP-Nas-Rules-IPv6=1Nas-filter-Rule="permit in tcp from any to any"
|
||||||
|
Used with the Nas-filter-Rule attribute described above to provide IPv6 traffic-filtering capability in an ACE. |
HP-Nas-Rules-IPv6: 63 (Vendor-Specific Attribute) When using the standard attribute (92) described above in a RADIUS-assigned ACL to support both IPv4 and IPv6 traffic inbound from an authenticated client, one instance of this VSA must be included in the ACL. Note that this attribute supports either of the following IP modes for Nas-filter-Rule ACEs:
HP vendor-specific ID: 11 VSA: 63 (string=HP-Nas-Rules-IPv6)
Setting: HP-Nas-Rules-IPv6=< 1 2 > Nas-filter-Rule "< permit or deny ACE > "
However, if you do not want both the IPv4 and IPv6 traffic of the selected type to go to their respective "any" destinations, then two ACEs with explicit destination addresses are needed. In this case, do one of the following:
For example, if you want to allow the IPv4 Telnet traffic from a client to go to any destination, but you want the IPv6 Telnet traffic from the same client to go only to a specific address or group of addresses, you will need to distinguish the separate destinations. This is done by using explicit addresses for the "any" destinations. For example: HP-Nas-Rules-IPv6=1Nas-filter-Rule="deny in tcp from any to 0.0.0.0/0 23"Nas-filter-Rule="deny in tcp from any to fe80::b1 23" The above example sends IPv4 Telnet traffic to its "any" destination, but allows IPv6 Telnet traffic only to fe80::b1 23.To reverse this example, you would configure ACEs such as the following: HP-Nas-Rules-IPv6=1Nas-filter-Rule="deny in tcp from any to 10.10.10.1 23"Nas-filter-Rule="deny in tcp from any to ::/0 23" In cases where you do not want the selected traffic type for either IPv4 or IPv6 to go to the "any" destination, you must use two ACEs to specify the destination addresses. For example: HP-Nas-Rules-IPv6=1Nas-filter-Rule="deny in tcp from any to 10.10.10.1 23"Nas-filter-Rule="deny in tcp from any to fe80::23 23" To use the IPv6 VSA while allowing only IPv4 traffic to be filtered, you would use a configuration such as the following: HP-Nas-Rules-IPv6=2Nas-filter-Rule="permit in tcp from any to any" |
||||||
|
IPv4-only ACLs applied to client traffic inbound to the switch Assigns a RADIUS-configured IPv4 ACL to filter inbound IPv4 packets received from a specific client authenticated on a switch port. |
HP-Nas-Filter-rule (Vendor-Specific Attribute): 61 This attribute is maintained for legacy purposes (for configurations predating software release xx.15.01) to support ACEs in RADIUS-assigned ACLs capable of filtering only IPv4 traffic. However, for new or updated configurations (and any configurations supporting IPv6 traffic filtering) HP recommends using the Standard Attribute (92) described earlier in this table instead of the HP-Nas-filter-Rule attribute described here. HP vendor-specific ID: 11 VSA: 61 (string=HP-Nas-Filter-Rule Setting: HP-Nas-filter-Rule="<
|
The following information describes ACE syntax configuration options in a RADIUS server.
| ACE syntax (standard attribute-92) |
|
| IPv6 VSA for standard attribute |
|
| ACE syntax (legacy VSA-61) |
|
|
Nas-filter-Rule = : Standard attribute for filtering inbound IPv4 traffic from an authenticated client. When used without the HP VSA option (below) for filtering inbound IPv6 traffic from the client, drops the IPv6 traffic. See also Nas-filter-rule attribute options. |
|
|
[ HP-Nas-Rules-IPv6=< 1 | 2 >]: HP VSA used in an ACL intended to filter IPv6 traffic. Settings include:
This VSA must be present in an ACL where the Nas-filter-Rule= attribute is intended to filter inbound IPv6 traffic from an authenticated client. See also Nas-filter-rule attribute options. |
|
|
HP-Nas-filter-Rule= : Legacy HP VSA for filtering inbound IPv4 traffic only from an authenticated client. Drops inbound IPv6 traffic from the client. See also Nas-filter-rule attribute options. |
|
|
Must be used to enclose and identify a complete permit or deny ACE syntax statement. For example: Nas-filter-Rule="deny in tcp from any to 0.0.0.0/0 23" |
|
|
Specifies whether to forward or drop the identified IP traffic type from the authenticated client. (For information on explicitly permitting or denying all inbound IP traffic from an authenticated client, or for implicitly denying all such IP traffic not already permitted or denied, see Configuration notes.) |
|
|
in Required keyword specifying that the ACL applies only to the traffic inbound from the authenticated client. |
|
|
Options for specifying the type of traffic to filter. |
|
|
ip Applies the ACE to all IP traffic from the authenticated client. |
|
|
ip-protocol-value This option applies the ACE to the type of IP traffic specified by either a protocol number or by tcp , udp ,icmp,or (for IPv4-only) igmp. The range of protocol numbers is 0-255. (Protocol numbers are defined in RFC 2780. For a complete listing, see "Protocol Registries" on the Web site of the Internet Assigned Numbers Authority at ( www.iana.com). Some examples of protocol numbers include: |
|
|
1=ICMP 2=IGMP (IPv4 only) 6=TCP 17=UDP 41=IPv6 |
|
|
from any Required keywords specifying the (authenticated) client source. (Note that a RADIUS-assigned ACL assigned to a port filters only the inbound traffic having a source MAC address that matches the MAC address of the client whose authentication invoked the ACL assignment.) |
|
|
to Required destination keyword. |
|
any
|
|
|
host <ipv4-addr> Specifies a single destination IPv4 address. |
|
|
<ipv4-addr/<mask > Specifies a series of contiguous destination addresses or all destination addresses in a subnet. The |
|
|
host <ipv6-addr> Specifies a single destination IPv6 address. Note: Filtering IPv6 traffic requires the Standard Attribute(Nas-Filter-Rule)with the HP-Nas-Rules-IPv6 VSA set to 1. See Nas-filter-rule attribute options. |
|
|
<ipv6-addr/<prefix> Specifies a series of contiguous destination addresses or all destination addresses in a subnet. The |
|
[tcp/udp-port|tcp/udp-port-range]
Optional TCP or UDP port specifier. Used when the ACE is intended to filter client TCP or UDP traffic with one or more specific TCP or UDP destination port numbers. You can specify port numbers as individual values and/or ranges. For example, the following ACE shows two ways to deny any UDP traffic from an authenticated client that has a DA of any address and a UDP destination port of 135, 137-139, or 445: deny in udp from any to any 135, 137-139, 445 deny in 17 from any to any 135, 137-139, 445 |
|
[icmp-type|icmpv6-type]
Optional ICMP type specifier. This can be either a keyword or an ICMP type number. For a listing of numbers and types, see ICMP type numbers and keywords. |
|
[cnt]
Optional counter specifier for a RADIUS-assigned ACE. When used, the counter increments each time there is a "match" with the ACE. This option does not require that you configure the switch for RADIUS accounting. |
The Standard attribute (92), when used in an ACL without the HP-Nas-Rules-IPv6 VSA, filters IPv4 traffic inbound from the authenticated client. (Any IPv6 traffic inbound from the client is dropped.) This example illustrates configuring RADIUS-assigned IPv4 ACL support on FreeRADIUS using the standard attribute for two different client identification methods (username/password and MAC address).
-
Enter the ACL standard attribute in the FreeRADIUS
dictionary.rfc4849file.ATTRIBUTE Nas-FILTER-Rule 92
-
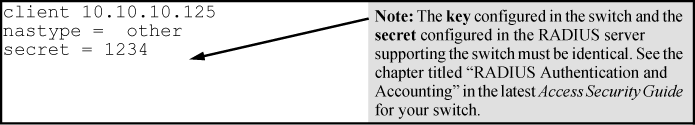
Enter the switch IP address, NAS (Network Attached Server) type, and the key used in the FreeRADIUS clients.conf file. For example, if the switch IP address is 10.10.10.125 and the key ("secret") is "1234", you would enter the following in the server's clients.conf file:
-
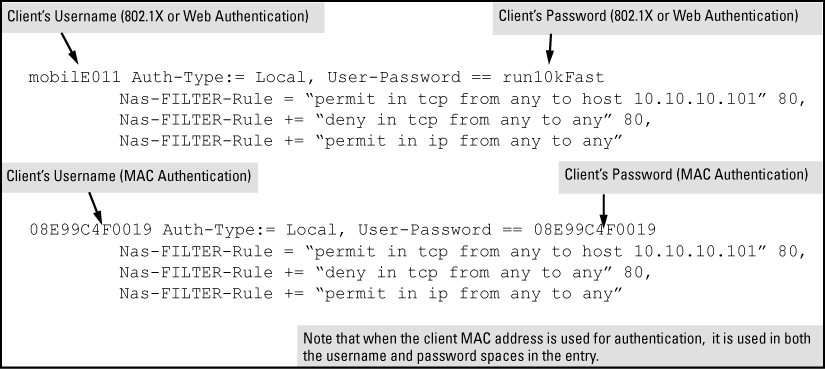
For a given client username/password pair or MAC address, create an ACL by entering one or more ACEs in the FreeRADIUS "users" file. Remember that every ACL created automatically includes an implicit
deny in ip from any to anyACE.For example, to create identical ACL support for the following:
-
Client having a username of "mobilE011" and a password of "run10kFast"
-
Client having a MAC address of 08 E9 9C 4F 00 19
The ACL in this example must achieve the following:
-
Permit http (TCP port 80) traffic from the client to the device at 10.10.10.101
-
Deny http (TCP port 80) traffic from the client to all other devices
-
Permit all other traffic from the client to all other devices
To configure the above ACL, enter the username/password and ACE information shown in Configuring the FreeRADIUS server to support ACLs for the indicated clients.
-
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: For information on syntax details for RADIUS-assigned ACLs, see Using HP VSA 63 to assign IPv6 and IPv4 ACLs (example). |
|
|
The ACL VSA HP-Nas-Rules-IPv6=1 is used in conjunction with the standard attribute (Nas-Filter-Rule) for ACL assignments filtering both IPv6 and IPv4 traffic inbound from an authenticated client. For example, to use these attributes to configure a RADIUS-assigned ACL on a FreeRADIUS server to filter both IPv6 and IPv4 ACLs, perform these steps:
-
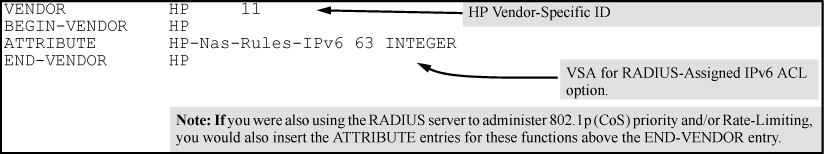
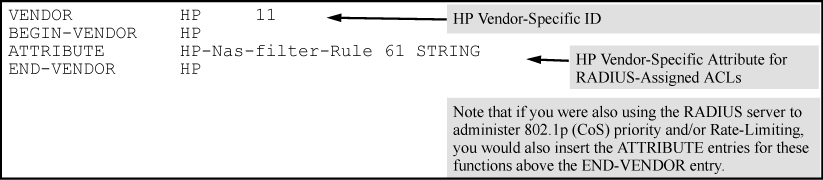
Enter the following in the FreeRADIUS
dictionary.hpfile:-
HP vendor-specific ID
-
ACL VSA for IPv6 ACLs (63)
-
HP-Nas-Rules-IPv6 VALUE setting to specify both IPv4 and IPv6 (1)
-
-
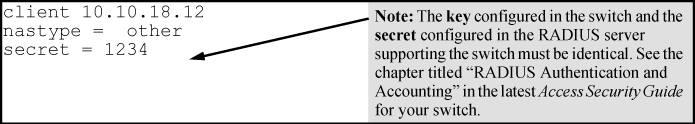
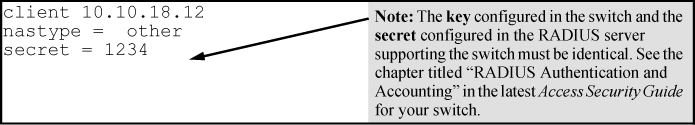
Enter the switch IPv4 address, NAS (Network Attached Server) type, and the key used in the FreeRADIUS clients.conf file. For example, if the switch IP address is 10.10.10.125 and the key ("secret") is "1234", you would enter the following in the server's clients.conf file:
-
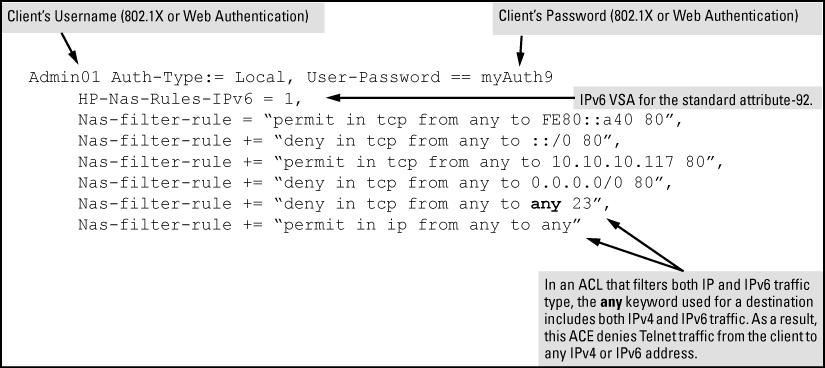
For a given client username/password pair, create an ACL by entering one or more IPv6 and IPv4 ACEs in the FreeRADIUS "users" file. Remember that the ACL created to filter both IPv4 and IPv6 traffic automatically includes an implicit deny in ip from any to any ACE at the end of the ACL in order to drop any IPv4 and IPv6 traffic that is not explicitly permitted or denied by the ACL. For example, to create ACL support for a client having a username of "Admin01" and a password of "myAuth9". The ACL in this example must achieve the following:
-
Permit http (TCP port 80) traffic from the client to the device at FE80::a40.
-
Deny http (TCP port 80) traffic from the client to all other IPv6 addresses.
-
Permit http (TCP port 80) traffic from the client to the device at 10.10.10.117.
-
Deny http (TCP port 80) traffic from the client to all other IPv4 addresses.
-
Deny Telnet (TCP port 23) traffic from the client to any IPv4 or IPv6 addresses.
-
Permit all other IPv4 and IPv6 traffic from the client to all other devices.
To configure the above ACL, enter the username/password and ACE information, as shown in this example:
-
This release continues to support the HP VSA 61 vendor-specific method of earlier releases for enabling RADIUS-based IPv4 ACL assignments on the switch. The recommended use of this option is to support legacy ACL configurations that rely on VSA 61. HP recommends using the standard attribute (92) for new, RADIUS-based IPv4 ACLs, see Nas-filter-rule options, and Using the standard attribute in an IPv4 ACL (example).
This example uses the HP VSA attribute 61 for configuring RADIUS-assigned IPv4 ACL support on FreeRADIUS for two different client identification methods (username/password and MAC address).
-
Enter the HP vendor-specific ID and the ACL VSA in the FreeRADIUS dictionary file:
-
Enter the switch IPv4 address, NAS (Network Attached Server) type, and the key used in the FreeRADIUS
clients.conffile. For example, if the switch IP address is 10.10.10.125 and the key ("secret") is "1234", you would enter the following in the server'sclients.conffile: -
For a given client username/password pair, create an ACL by entering one or more IPv4 ACEs in the FreeRADIUS "users" file. Remember that the ACL created to filter IPv4 traffic automatically includes an implicit
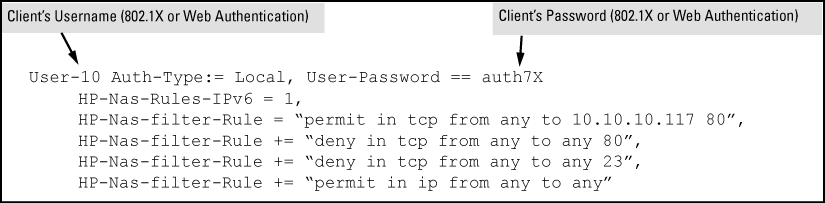
deny in ip from anyto any ACE (for IPv4). For example, to create ACL support for a client having a username of "User-10" and a password of "auth7X". The ACL in this example must achieve the following:-
Permit http (TCP port 80) traffic from the client to the device at 10.10.10.117.
-
Deny http (TCP port 80) traffic from the client to all other IPv4 addresses.
-
Deny Telnet (TCP port 23) traffic from the client to any IPv4 address.
-
Permit all other IPv4 traffic from the client to all other devices.
To configure the above ACL, you would enter the username/password and ACE information shown in Configuring a FreeRADIUS server to filter IPv4 traffic for a client with the correct credentials into the FreeRADIUS "users"file.
-
This option for ending a RADIUS-assigned ACL permits all of the client's inbound IPv4 and IPv6 traffic not previously permitted or denied.
Nas-filter-Rule += permit in ip from any to any HP-Nas-Rules-IPv6=1
See Nas-filter-rule attribute options for information on the above attributes.
Any of the following three options for ending a RADIUS-assigned ACL explicitly permit all of the client's inbound IPv4 traffic not previously permitted or denied. These options also deny any of the client's IPv6 traffic not previously permitted or denied.
(Using this attribute to permit IPv4 traffic from the client while denying any IPv6 traffic from the client assumes that
HP-Nas-Rules-IPv6=1does not exist elsewhere in the ACL. See Nas-filter-rule attribute options for more onHP-Nas-Rules-IPv6.)
Any of the following three options for ending a RADIUS-assigned ACL explicitly deny all of the client's inbound IPv4 and IPv6 traffic not previously permitted or denied.
For any packet being filtered by a RADIUS-assigned ACL, there will always be a match. That is, any packet that does not have a match with an explicit permit or deny ACE in the list will match with the implicit deny any any ACE automatically included at the end of the ACL. That is, a RADIUS-assigned ACL includes an implicit deny in ip from any to any ACE at the end of the ACL to deny any IPv4 and IPv6 traffic not previously permitted or denied.
An ACL configured in a RADIUS server is identified by the authentication credentials of the client or group of clients the ACL is designed to support. When a client authenticates with credentials associated with a particular ACL, the switch applies that ACL to the switch port the client is using. To enable the switch to forward a client's credentials to the RADIUS server, you must first configure RADIUS operation and an authentication method on the switch.
-
Configure RADIUS operation on the switch:
Syntax:
This command configures the IPv4 address and encryption key of a RADIUS server. The server should be accessible to the switch and configured to support authentication requests from clients using the switch to access the network.
-
Configure RADIUS network accounting on the switch (optional).
You can also view ACL counter hits using either of the following commands:
![[NOTE: ]](images/note.gif)
NOTE: See the documentation provided with your RADIUS server for information on how the server receives and manages network accounting information, and how to perform any configuration steps necessary to enable the server to support network accounting data from the switch.
-
Configure an authentication method. Options include 802.1X, web-based authentication, and MAC authentication. You can configure 802.1X, web-based authentication, and/or MAC authentication to operate simultaneously on the same ports.
Syntax:
These commands configure 802.1X port-based access control on the switch, and activates this feature on the specified ports. For more on 802.1X configuration and operation, see User authentication methods.
Syntax:
This command configures MAC authentication on the switch and activates this feature on the specified ports. For more on MAC authentication, see Web and MAC Authentication.
Syntax:
This command configures web-based authentication on the switch and activates this feature on the specified ports. For more on web-based authentication, see Web and MAC Authentication.
These commands output data indicating the current ACL activity imposed per-port by RADIUS server responses to client authentication.
Syntax:
For the specified ports, this command lists:
Whether the ACL for the indicated client is configured to filter IPv4 traffic only, or both IPv4 and IPv6 traffic. See Nas-filter-rule attribute options for more on this topic.
The explicit ACEs, switch port, and client MAC address for each ACL dynamically assigned by a RADIUS server as a response to client authentication.
If
cnt(counter) is included in an ACE, then the output includes the current number of inbound packet matches the switch has detected in the current session for that ACE, see ACE syntax in RADIUS servers.
NOTE: If there are no ACLs currently assigned to any port in
<, executing this command returns only the system prompt. If a client authenticates but the server does not return a RADIUS-assigned ACL to the client port, then the server does not have a valid ACL configured and assigned to that client's authentication credentials.port-list>
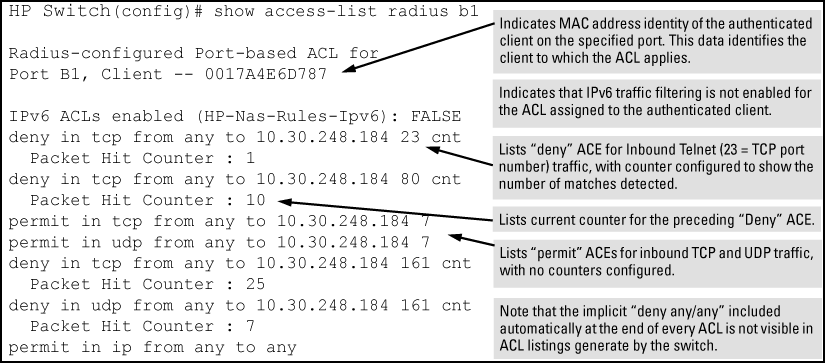
Example:
The following output shows that a RADIUS server has assigned an ACL to port B1 to filter inbound traffic from an authenticated client identified by a MAC address of 00-17-A4-E6-D7-87.
Syntax:
For ports in < configured for authentication, this command shows the details of the RADIUS-assigned features listed below that are active as the result of a client authentication. (Ports in port-list>< that are not configured for authentication are not listed.)port-list>
Client Base Details:
|
Indicates whether there is an authenticated client session active on the port. Options include |
|
|
During an authenticated session, shows the user name of the authenticated client. If the client is not authenticated, this field is empty. |
|
|
Shows the authenticated client's IP address, if available. Requires DHCP snooping enabled on the switch. When "n/a" appears in the field, the switch has not been able to acquire the client's IP address. Note: Where the client IP address is available to the switch, it can take a minute or longer for the switch to learn the address. For more on this topic, see Configuring RADIUS accounting. |
|
|
For an unauthenticated session, indicates the elapsed time in seconds since the client was detected on the port. For an authenticated session, this indicates the elapsed time in seconds since the client was authenticated on the port. |
|
|
During an authenticated session, shows the MAC address of the authenticated client. |
Access Policy Details:
|
Indicates the 802.1p priority assigned by the RADIUS server for traffic inbound on the port from an authenticated client. The field shows an eight-digit value where all digits show the same, assigned 802.1p number. For example, if the assigned 802.1p value is 5, then this field shows |
|
|
VLAN ID (VID) of the untagged VLAN currently supporting the authenticated connection. |
|
|
VLAN IDs (VIDs) of any tagged VLANs currently supporting the authenticated connection. |
|
|
Lists the explicit ACEs in the ACL assigned to the port for the authenticated client. Includes the ACE "Hit Count" (matches) for ACEs configured with the |
|
|
Indicates the ingress rate-limit assigned by the RADIUS server to the port for traffic inbound from the authenticated client. If there is no ingress rate-limit assigned, then |
|
|
Indicates the egress rate-limit assigned by the RADIUS server to the port for traffic outbound to the authenticated client. If there is no egress rate-limit assigned, then |
Output showing current RADIUS-applied features
HP Switch(config)# show port-access web-based clients 10 detailed
Port Access Web-Based Client Status Detailed
Client Base Details :
Port : 9
Session Status : authenticated Session Time(sec) : 5
Username : acluser1 MAC Address : 0017a4-e6d787
IP : n/a
Access Policy Details :
COS Map : 77777777 In Limit Kbps : 1000
Untagged VLAN : 10 Out Limit Kbps : Not Set
Tagged VLANs : 20
RADIUS-ACL List :
deny in 23 from any to 10.0.8.1/24 23 CNT
Hit Count: 1
permit in 1 from any to 10.0.10.1/24 CNT
Hit Count: 112
deny in udp from any to any 67-68 CNT
Hit Count: 7
permit in ip from any to any CNT
Hit Count: 125
ICMP type numbers and keywords
| IPv4 ICMP | IPv6 ICMP | ||
|---|---|---|---|
| # | Keyword | # | Keyword |
| 0 | echo reply | 1 | destination unreachable |
| 3 | destination unreachable | 2 | packet too big |
| 4 | source quench | 3 | time exceeded |
| 5 | redirect | 4 | parameter problem |
| 8 | echo request | 128 | echo request |
| 9 | router advertisement | 129 | echo reply |
| 10 | router solicitation | 130 | multicast listener query |
| 11 | time-to-live exceeded | 131 | multicast listener reply |
| 12 | IP header bad | 132 | multicast listener done |
| 13 | timestamp request | 133 | router solicitation |
| 14 | timestamp reply | 134 | router advertisement |
| 15 | information request | 135 | neighbor solicitation |
| 16 | information reply | 136 | neighbor advertisement |
| 17 | address mask request | 137 | redirect message |
| 18 | address mask reply | 138 | router renumbering |
| 139 | icmp node information query | ||
| 140 | icmp node information response | ||
| 141 | inverse neighbor discovery solicitation message | ||
| 142 | inverse neighbor discovery advertisement message | ||
| 143 | version 2 multicast listener report | ||
| 144 | home agent address discovery request message | ||
| 145 | home agent address discovery reply message | ||
| 146 | mobile prefix solicitation | ||
| 147 | mobile prefix advertisement | ||
| 148 | certification path solicitation message | ||
| 149 | certification path advertisement message | ||
| 151 | multicast router advertisement | ||
| 152 | multicast router solicitation | ||
| 153 | multicast router termination | ||
-
An IPv6 ACE has been received on a port and either the
HP-Nas-Rules-IPv6attribute is missing orHP-Nas-Rules-IPv6=2is configured. See Nas-filter-rule attribute options for more on this attribute.
Currently active, RADIUS-based authentication sessions (including HP IDM client sessions) using RADIUS-assigned ACLs share internal switch resources with several other features. The switch provides ample resources for all features. However, if the internal resources do become fully subscribed, new RADIUS-based sessions using RADIUS-assigned ACLs cannot be authenticated until the necessary resources are released from other applications.
-
For information on determining the current resource availability and usage, see “Monitoring Resources" in the Management and Configuration Guide for your switch.
-
For a summary of ACL resource limits, see the topics covering scalability in the latest Management and Configuration Guide for your switch.