-
A software version for the switch has been stored on a TFTP server accessible to the switch. (The software file is typically available from the HP Switch Networking website at www.hp.com/networking/support.)
-
The switch is properly connected to your network and has already been configured with a compatible IP address and subnet mask.
Before you use the procedure, do the following:
-
Obtain the IP address of the TFTP server in which the software file has been stored.
-
If VLANs are configured on the switch, determine the name of the VLAN in which the TFTP server is operating.
-
Determine the name of the software file stored in the TFTP server for the switch (for example, E0820.swi.)
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If your TFTP server is a UNIX workstation, ensure that the case (upper or lower) that you specify for the filename is the same case as the characters in the software filenames on the server. |
|
|
Syntax
Automatically downloads a switch software file to primary or secondary flash. If you do not specify the flash destination, the TFTP download defaults to primary flash.
Example
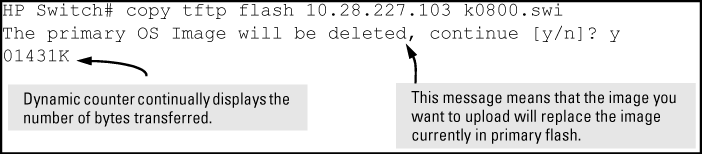
To download a switch software file named k0800.swi from a TFTP server with the IP address of 10.28.227.103 to primary flash:
-
When the switch finishes downloading the software file from the server, it displays this progress message:
-
When the download finishes, you must reboot the switch to implement the newly downloaded software image. To do so, use one of the following commands:
Syntax
Boots from the selected flash.
Syntax
Boots from the flash image and startup-config file. A switch covered in this guide (with multiple configuration files), also uses the current startup-config file.
-
To confirm that the software downloaded correctly, execute
show systemand check the Firmware revision line.
For information on primary and secondary flash memory and the boot commands, see the Basic Operation Guide.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: If you use |
|
|
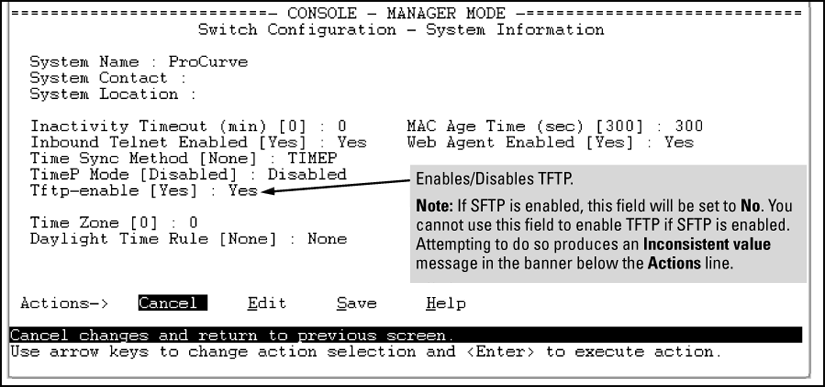
TFTP is enabled by default on the switch. If TFTP operation has been disabled, you can re-enable it by specifying TFTP client or server functionality with the following command.
Syntax
Syntax
For switches that have a separate out-of-band management port, the listen parameter in a server configuration allows you to specify whether transfers take place through the out-of-band management (oobm) interface, the data interface, or both.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: To disable all TFTP client or server operation on the switch except for the auto-TFTP feature, enter the When IP SSH file transfer is used to enable SCP and SFTP functionality on the switch, this disables TFTP client and server functionality. Once ip ssh file transfer is enabled, TFTP and auto-TFTP cannot be re-enabled from the CLI. When TFTP is disabled, instances of TFTP in the CLI The For information on how to configure TFTP file transfers on an IPv6 network, see theIPv6 Configuration Guide. |
|
|
Operation notes
TFTP at the switch is allows for extensive use of scripts on various customer environments. Such environs, like FW, configurations, backups, and restores all use the TFTP network service.
-
Users are allowed to re-enable TFTP and make both TFTP and SFTP work in parallel.
-
SFTP support for database of DSNOOPv4, v6 and DHCP Server are also available. To provide a secure way to transfer the database, the SFTP option has been added where the respective database can also be transferred to a SFTP Server.
The auto-tftp command lets you configure the switch to download software automatically from a TFTP server.
At switch startup, the auto-TFTP feature automatically downloads a specified software image to the switch from a specified TFTP server and then reboots the switch. To implement the process, you must first reboot the switch using one of the following methods:
Syntax
By default, auto-TFTP is disabled. This command configures the switch to automatically download the specified software file from the TFTP server at the specified IP address. The file is downloaded into primary flash memory at switch startup; the switch then automatically reboots from primary flash.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: To enable auto-TFTP to copy a software image to primary flash memory, the version number of the downloaded software file (for example, K_14_01.swi) must be different from the version number currently in the primary flash image. The current TFTP client status (enabled or disabled) does not affect auto-TFTP operation. (See Enabling TFTP.) Completion of the auto-TFTP process may require several minutes while the switch executes the TFTP transfer to primary flash and then reboots again. |
|
|
The no form of the command disables auto-TFTP operation by deleting the auto-tftp entry from the startup configuration.
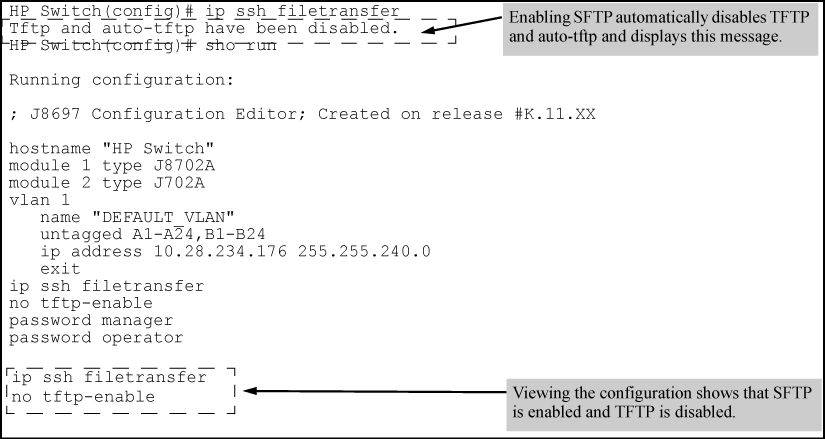
The no auto-tftp command does not affect the current TFTP-enabled configuration on the switch. However, entering the ip ssh filetransfer command automatically disables both auto-tftp and tftp operation.
Note that the menu interface accesses only the primary flash.
-
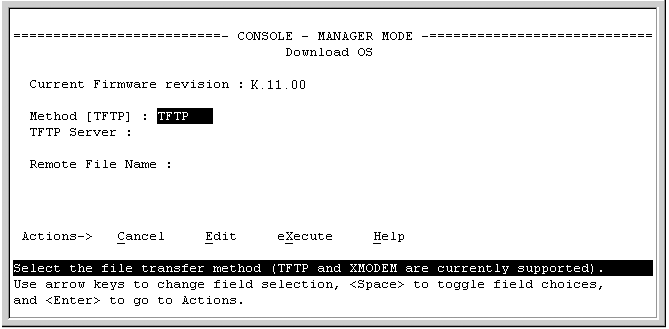
In the console Main Menu, select Download OS to display the screen in Download OS (software) screen (default values). (The term "OS" or "operating system" refers to the switch software):
-
In the TFTP Server field, enter the IP address of the TFTP server in which the software file has been stored.
-
In the Remote File Name field, enter the name of the software file (if you are using a UNIX system, remember that the filename is case-sensitive.)
-
Press [Enter], then [X] (for eXecute) to begin the software download.
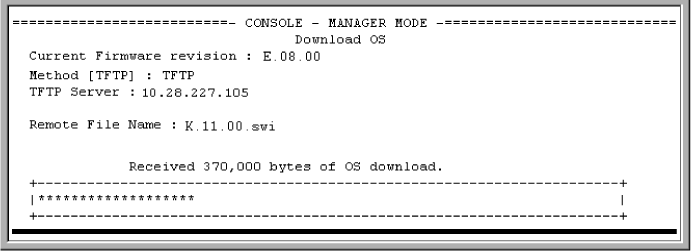
The screen shown in Download OS (software) screen during a download appears:
A "progress" bar indicates the progress of the download. When the entire software file has been received, all activity on the switch halts and you will see Validating and writing system software to FLASH...
-
After the primary flash memory is updated with the new software, you must reboot the switch to implement the newly downloaded software. Return to the Main Menu and press [6] (for Reboot Switch.)
Continue reboot of system? : No
Press the space bar once to change No to Yes, then press [Enter] to begin the reboot.
![[NOTE: ]](images/note.gif)
NOTE: When you use the menu interface to download a switch software, the new image is always stored in primary flash. Also, using the
Reboot Switchcommand in the Main Menu always reboots the switch from primary flash. Rebooting the switch from the CLI provides more options. See the Basic Operation Guide.
-
After you reboot the switch, confirm that the software downloaded correctly:
Using the ip ssh filetransfer command to enable SFTP automatically disables TFTP and auto-TFTP (if either or both are enabled), as shown in Example of switch configuration with SFTP enabled.
If you enable SFTP and then later disable it, TFTP and auto-TFTP remain disabled unless they are explicitly re-enabled.
-
The TFTP feature is enabled by default, and can be enabled or disabled through the CLI, the Menu interface (see Using the Menu interface to disable TFTP), or an SNMP application. Auto-TFTP is disabled by default and must be configured through the CLI.
-
While SFTP is enabled, TFTP and auto-TFTP cannot be enabled from the CLI. Attempting to enable either non-secure TFTP option while SFTP is enabled produces one of the following messages in the CLI:
Similarly, while SFTP is enabled, TFTP cannot be enabled using an SNMP management application. Attempting to do so generates an "inconsistent value" message. (An SNMP management application cannot be used to enable or disable auto-TFTP.)
-
To enable SFTP by using an SNMP management application, you must first disable TFTP and, if configured, auto-TFTP on the switch. You can use either an SNMP application or the CLI to disable TFTP, but you must use the CLI to disable auto-TFTP. The following CLI commands disable TFTP and auto-TFTP on the switch.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: As a matter of policy, administrators should not enable the SSH V1-only or the SSH V1-or-V2 advertisement modes. SSHv1 is supported on only some legacy switches (such as the HP Switch Series 2500 switches.) |
|
|
Once you have confirmed that you have enabled an SSH session (with the show ip ssh command), enter ip ssh filetransfer so that SCP and/or SFTP can run. You can then open your third-party software client application to begin using the SCP or SFTP commands to safely transfer files or issue commands to the switch.
Switch memory allows up to ten public keys. This means the authentication and encryption keys you use for your third-party client SCP/SFTP software can differ from the keys you use for the SSH session, even though both SCP and SFTP use a secure SSH tunnel.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: SSH authentication is mutually exclusive with RADIUS servers. |
|
|
Some clients, such as PSCP (PuTTY SCP), automatically compare switch host keys for you. Other clients require you to manually copy and paste keys to the $HOME/.ssh/known_hosts file. Whatever SCP/SFTP software tool you use, after installing the client software you must verify that the switch host keys are available to the client.
Because the third-party software utilities you may use for SCP/SFTP vary, you should refer to the documentation provided with the utility you select before performing this process.
-
When an SFTP client connects, the switch provides a file system displaying all of its available files and folders. No file or directory creation is permitted by the user. Files may be only uploaded or downloaded, according to the permissions mask. All of the necessary files the switch needs are already in place on the switch. You do not need to (nor can you) create new files.
-
The switch supports one SFTP session or one SCP session at a time.
-
All files have read-write permission. Several SFTP commands, such as
createorremove, are not allowed and return an error message. The switch displays the following files:/ +---cfg | running-config | startup-config +---log | crash-data | crash-data-a | crash-data-b | crash-data-c | crash-data-d 8212zl only | crash-data-e " " | crash-data-f "" | crash-data-g 8212zl only | crash-data-h " " | crash-data-I "" | crash-data-J "" | crash-data-K "" | crash-data-L " " | crash-log | crash-log-a | crash-log-b | crash-log-c | crash-log-d 8212zl only | crash-log-e "" | crash-log-f "" | crash-log-g 8212zl only | crash-log-h " " | crash-log-I " " | crash-log-J " " | crash-log-K " " | crash-log-L " " | event log +---os | primary | secondary \---ssh +---mgr_keys | authorized_keys \---oper_keys | authorized_keys \---core ( this directory is not available on the 8212zl) | mm1.cor management module or management function | im_a.cor interface module ( chassis switches only) | im_b.cor interface module ( chassis switches only) | im_1.cor interface module ( chassis switches only) | port_1-24.cor core-dump for ports 1-24 ( stackable switches only) | port_25-48.cor core-dump for ports 25-48 ( stackable switches only) -
When using SFTP to copy a software image onto the switch, the command return takes only a few seconds. However, this does not mean that the transfer is complete, because the switch requires additional time (typically more than one minute) to write the image to flash in the background. To verify the file transfer has been completed, you can use the
show flashcommand or look for a confirmation message in the log, as in the following example:I 01/09/09 16:17:07 00150 update: Primary Image updated.
You can verify secure file transfer operations by checking the switch's event log, or by viewing the error messages sent by the switch that most SCP and SFTP clients print out on their console.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Messages that are sent by the switch to the client depend on the client software in use to display them on the user console. |
|
|
If an ssh connection is broken at the wrong moment (for instance, the link goes away or spanning tree brings down the link), a fatal exception occurs on the switch. If this happens, the switch gracefully exits the session and produces an Event Log message indicating the cause of failure. The following three examples show the error messages that may appear in the log, depending on the type of session that is running (SSH, SCP, or SFTP):
ssh: read error Bad file number, session aborted I 01/01/90 00:06:11 00636 ssh: sftp session from ::ffff:10.0.12.35 W 01/01/90 00:06:26 00641 ssh: sftp read error Bad file number, session aborted I 01/01/90 00:09:54 00637 ssh: scp session from ::ffff:10.0.12.35 W 01/ 01/90 ssh: scp read error Bad file number, session aborted
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: The |
|
|
If you attempt to start an SCP (or SFTP) session while a flash write is in progress, the switch does not allow the SCP or SFTP session to start. Depending on the client software in use, the following error message may appear on the client console:
This next example shows the error message that may appear on the client console if a new SCP (or SFTP) session is started from a client before the previous client session has been closed (the switch requires approximately ten seconds to timeout the previous session):
The switch's USB port (labeled as Auxiliary Port) allows the use of a USB flash drive for copying configuration files to and from the switch. Beginning with software release K_12_XX or later, copy commands that used either tftp or xmodem now include an additional option for usb as a source or destination for file transfers.
Operating rules and restrictions on USB usage are:
-
Unformatted USB flash drives must first be formatted on a PC (Windows FAT format.) For devices with multiple partitions, only the first partition is supported. Devices with secure partitions are not supported.
-
If they already exist on the device, subdirectories are supported. When specifying a
filename, you must enter either the individual file name (if at the root) or the full path name (for example, /subdir/filename.) -
To view the contents of a USB flash drive, use the
dircommand. This lists all files and directories at the root. To view the contents of a directory, you must specify the subdirectory name (that is,dir subdirectory.) -
The USB port supports connection to a single USB device. USB hubs to add more ports are not supported.
|
|
|
![[NOTE: ]](images/note.gif) |
NOTE: Some USB flash drives may not be supported on your switch. Consult the latest Release Notes for information on supported devices. |
|
|