You can store and view the following security settings in the running-config file associated with the current software image. The security settings that can be saved to a configuration file are:
-
Local manager and operator passwords and user names.
-
SNMP security credentials, including SNMPv1 community names and SNMPv3 user names, authentication, and privacy settings.
-
802.1X port-access passwords and user names.
-
TACACS+ encryption keys.
-
RADIUS shared secret (encryption) keys.
-
Public keys of SSH-enabled management stations that are used by the switch to authenticate SSH clients that try to connect to the switch.
The information saved to the running-config file when the include-credentials command is entered includes:
nameis an alphanumeric string for the user name assigned to the manager or operator.
<hash type>indicates the type of hash algorithm used: SHA-1 or plain text.
<pass hash>is the SHA-1 authentication protocol’s hash of the password or clear ASCII text.
For example, a manager user name and password can be stored in a runningconfig file as follows:
Use the write memory command to save the password configurations in the startup-config file. The passwords take effect when the switch boots with the software version associated with that configuration file.
|
|
|
![[CAUTION: ]](images/caution.gif) |
CAUTION: If a startup configuration file includes other security credentials, but does not contain a manager or operator password, the switch will not have password protection and can be accessed through Telnet or the serial port of the switch with full manager privileges. |
|
|
The password command has the following options:
Syntax
Set or clear a local user name/password for a given access level.
You can enter a manager, operator, or 802.1X port-access password in clear ASCII text or hashed format. However, manager and operator passwords are displayed and saved in a configuration file only in hashed format; port-access passwords are displayed and saved only as plain ASCII text.
-
For more information about configuring local manager and operator passwords,Configuring Username and Password Security.
-
For more information about configuring a port-access password for 802.1X client authentication. See802.1X Port-based access control.
SNMPv1 community names and write-access settings, and SNMPv3 user names continue to be saved in the running configuration file even when you enter the include-credentials command.
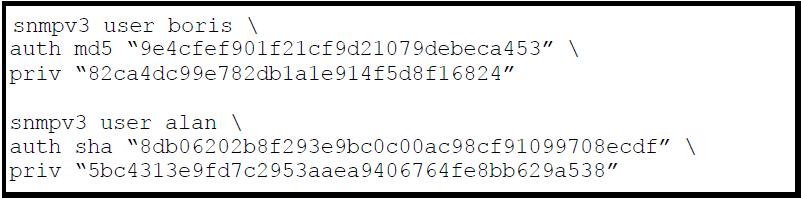
In addition, the following SNMPv3 security parameters are also saved:
The following example shows the additional security credentials for SNMPv3 users that can be saved in a running-config file.
Although you can enter an SNMPv3 authentication or privacy password in either clear ASCII text or the SHA-1 hash of the password, the password is displayed and saved in a configuration file only in hashed format, see Example of security credentials saved in the running-config.
See “Configuring for Network Management Applications” in the Management and Configuration Guide for your switch for more information about the configuration of SNMP security parameters.
802.1X authenticator (port access) credentials can be stored in a configuration file. 802.1X authenticator credentials are used by a port to authenticate supplicants requesting a point-to-point connection to the switch. 802.1X supplicant credentials are used by the switch to establish a point-to-point connection to a port on another 802.1X-aware switch. Only 802.1X authenticator credentials are stored in a configuration file.
The local password configured with the password command is no longer accepted as an 802.1X authenticator credential. A new configuration command password port-access is introduced to configure the local operator user name and password used as 802.1X authentication credentials for access to the switch.
The password port-access values are now configured separately from the manager and operator passwords configured with the password manager and password operator commands and used for management access to the switch.
After you enter the complete password port-access command syntax, the password is set. You are not prompted to enter the password a second time.
You can use TACACS+ servers to authenticate users who request access to a switch through Telnet (remote) or console (local) sessions. TACACS+ uses an authentication hierarchy consisting of:
When you configure TACACS+, the switch first tries to contact a designated TACACS+ server for authentication services. If the switch fails to connect to any TACACS+ server, it defaults to its own locally assigned passwords for authentication control if it has been configured to do so.
For improved security, you can configure a global or server-specific encryption key that encrypts data in TACACS+ packets transmitted between a switch and a RADIUS server during authentication sessions. The key configured on the switch must match the encryption key configured in each TACACS+ server application. (The encryption key is sometimes referred to as “shared secret” or “secret” key.)
TACACS+ shared secret (encryption) keys can be saved in a configuration file by entering this command:
The option <keystring> is the encryption key (in clear text) used for secure communication with all or a specific RADIUS server.
You can use RADIUS servers as the primary authentication method for users who request access to a switch through Telnet, SSH, console, or port access (802.1X). The shared secret key is a text string used to encrypt data in RADIUS packets transmitted between a switch and a RADIUS server during authentication sessions. Both the switch and the server have a copy of the key; the key is never transmitted across the network.
RADIUS shared secret (encryption) keys can be saved in a configuration file by entering this command:
HP Switch(config)# radius-server key<keystring>
The option <keystring> is the encryption key (in clear text) used for secure communication with all or a specific RADIUS server.
Secure Shell version 2 (SSHv2) is used by HP switches to provide remote access to SSH-enabled management stations. Although SSH provides Telnetlike functions, unlike Telnet, SSH provides encrypted, two-way authenticated transactions. SSH client public-key authentication is one of the types of authentication used.
Client public-key authentication uses one or more public keys (from clients) that must be stored on the switch. Only a client with a private key that matches a public key stored on the switch can gain access at the manager or operator level. For more information about how to configure and use SSH public keys to authenticate SSH clients that try to connect to the switch.
The SSH security credential that is stored in the running configuration file is configured with the ip ssh public-key command used to authenticate SSH clients for manager or operator access, along with the hashed content of each SSH client public key.
Syntax
ip ssh public-key <manager|operator>keystringSet a key for public-key authentication.
manager
Allows manager-level access using SSH public-key authentication.
operator
Allows operator-level access using SSH public-key authentication.
keystring
A legal SSHv2 (RSA or DSA) public key. The text string for the public key must be a single quoted token. If the keystring contains double-quotes, it can be quoted with single quotes (
'keystring'). The following restrictions for a keystring apply.
A keystring cannot contain both single and double quotes.
A keystring cannot have extra characters, such as a blank space or a new line. However, to improve readability, you can add a backlash at the end of each line.
NOTE: The
ip ssh public-keycommand allows you to configure only one SSH client public key at a time. Theip ssh public-keycommand behavior includes an implicit append that never overwrites existing public-key configurations on a running switch.If you download a software configuration file that contains SSH client publickey configurations, the downloaded public keys overwrite any existing keys, as happens with any other configured values.
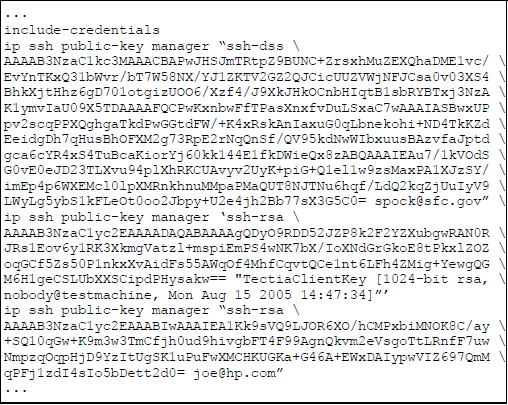
To display the SSH public-key configurations (72 characters per line) stored in a configuration file, enter the show config or show running-config command. The following example shows the SSH public keys configured for manager access, along with the hashed content of each SSH client public key stored in a configuration file.
If a switch configuration contains multiple SSH client public keys, each public key is saved as a separate entry in the configuration file. You can configure up to 10 SSH client public keys on a switch.
The following restrictions apply when you enable security credentials to be stored in the running configuration with the include-credentials command:
-
The private keys of an SSH host cannot be stored in the running configuration. Only the public keys used to authenticate SSH clients can be stored. An SSH host's private key is only stored internally, for example, on the switch or on an SSH client device.
-
SNMPv3 security credentials saved to a configuration file on a switch cannot be used after downloading the file on a different switch. The SNMPv3 security replaceables in the file are only supported when loaded on the same switch for which they were configured. This is because when SNMPv3 security credentials are saved to a configuration file, they are saved with the engine ID of the switch as shown here:
snmpv3 engine-id 00:00:00:0b:00:00:08:00:09:01:10:01
If you download a configuration file with saved SNMPv3 security credentials on a switch, when the switch loads the file with the current software version the SNMPv3 engine ID value in the downloaded file must match the engine ID of the switch in order for the SNMPv3 users to be configured with the authentication and privacy passwords in the file. (To display the engine ID of a switch, enter the show snmpv3 engine-id command. To configure authentication and privacy passwords for SNMPv3 users, enter the snmpv3 user command.)
If the engine ID in the saved SNMPv3 security settings in a downloaded configuration file does not match the engine ID of the switch:
-
The SNMPv3 users are configured, but without the authentication and privacy passwords. You must manually configure these passwords on the switch before the users can have SNMPv3 access with the privileges you want.
-
Only the
snmpv3 user<user_name> credentials from the SNMPv3 settings in a downloaded configuration file are loaded on the switch, for example:snmpv3 user boris
snmpv3 user alan
-
You can store 802.1X authenticator (port access) credentials in a configuration file. However, 802.1X supplicant credentials cannot be stored.
-
The local operator
passwordconfigured with thepasswordcommand is no longer accepted as an 802.1X authenticator credential. A new configuration commandpassword port-accessis introduced to configure the user name and password used as 802.1X authentication credentials for access to the switch. You can store thepassword port-accessvalues in the running configuration file by using theinclude-credentialscommand.
![[NOTE: ]](images/note.gif)
NOTE:
password port-accessvalues are configured separately from local operator user name and passwords configured with thepassword operatorcommand and used for management access to the switch. For more information about how to use thepassword port-accesscommand to configure operator passwords and user names for 802.1X authentication,Configuring Username and Password Security.