NTP security
To improve time synchronization security, NTP provides the access control and authentication functions.
NTP access control
You can control NTP access by using an ACL. The access rights are in the following order, from the least restrictive to the most restrictive:
Peer—Allows time requests and NTP control queries (such as alarms, authentication status, and time server information) and allows the local device to synchronize itself to a peer device.
Server—Allows time requests and NTP control queries, but does not allow the local device to synchronize itself to a peer device.
Synchronization—Allows only time requests from a system whose address passes the access list criteria.
Query—Allows only NTP control queries from a peer device to the local device.
When the device receives an NTP request, it matches the request with the access rights in the order from the least restrictive to the most restrictive: peer, server, synchronization, and query.
If no NTP access control is configured, the peer access right applies.
If the IP address of the peer device matches a permit statement in an ACL, the access right is granted to the peer device. If a deny statement or no ACL is matched, no access right is granted.
If no ACL is specified for an access right or the ACL specified for the access right is not created, the access right is not granted.
If none of the ACLs specified for the access rights are created, the peer access right applies.
If none of the ACLs specified for the access rights contain rules, no access right is granted.
This feature provides minimal security for a system running NTP. A more secure method is NTP authentication.
NTP authentication
Use this feature to authenticate the NTP messages for security purposes. If an NTP message passes authentication, the device can receive it and get time synchronization information. If not, the device discards the message. This function makes sure the device does not synchronize to an unauthorized time server.
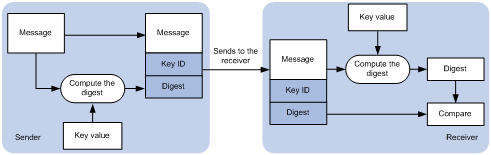
Figure 34: NTP authentication
As shown in Figure 34, NTP authentication works as follows:
The sender uses the MD5 algorithm to calculate the NTP message according to the key identified by a key ID. Then it sends the calculated digest together with the NTP message and key ID to the receiver.
Upon receiving the message, the receiver performs the following actions:
Finds the key according to the key ID in the message.
Uses the MD5 algorithm to calculate the digest.
Compares the digest with the digest contained in the NTP message.
If they are different, the receiver discards the message.
If they are the same and an NTP session is not required to be created, the receiver responds to the message. For information about NTP sessions, see "Configuring the maximum number of dynamic associations."
If they are the same and an NTP session is to be created, the local device determines whether the sender is allowed to use the authentication ID after the NTP session is established. If the sender is allowed to use the authentication ID, the receiver accepts the message. If the sender is not allowed to use the authentication ID, the receiver discards the message.
If they are the same and an NTP session has been created, the local device determines whether the sender is allowed to use the authentication ID. If the sender is allowed to use the authentication ID, the receiver accepts the message. If the sender is not allowed to use the authentication ID, the receiver discards the message.