Saving security logs into the security log file
Network requirements
Save security logs into the security log file Flash:/securitylog/seclog.log every one hour.
Only the security log administrator can view the contents of the security log file. No other users cannot view, copy, or rename the security log file.
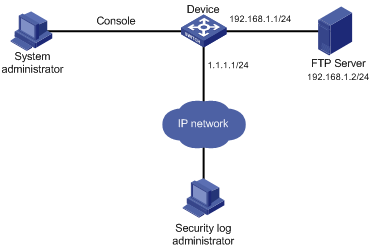
Figure 22: Network diagram
Configuration considerations
The configuration in this example includes two parts:
Log in to the device as the system administrator:
Enable saving the security logs into the security log file and set the saving interval to one hour.
Create a local user seclog with the password 123123123123, and authorize this user as the security log administrator. That is, use the authorization-attribute command to set the user privilege level to 3 and specify the user role as security audit. In addition, specify the service types that the user can use by using service-type.
Set the authentication mode to scheme for the user logging in to the device, and make sure only the local user that has passed the AAA local authentication can view and perform operations on the security log file.
Log in to the device as the security log administrator:
Set the directory for saving the security log file to Flash:/securitylog/seclog.log.
View the contents of the security log file to learn the security status of the device.
Configuration procedure
Configuration performed by the system administrator:
# Enable saving security logs into the security log file and set the saving interval to one hour.
<Sysname> system-view [Sysname] info-center security-logfile enable [Sysname] info-center security-logfile frequency 3600
# Create a local user seclog, and configure the password for the user as 123123123123.
[Sysname] local-user seclog New local user added. [Sysname-luser-seclog] password simple 123123123123
# Authorize the user to manage the security log file.
[Sysname-luser-seclog] authorization-attribute level 3 user-role security-audit
# Authorize the user to use SSH, Telnet, and terminal services.
[Sysname-luser-seclog] service-type ssh telnet terminal [Sysname-luser-seclog] quit
# According to the network plan, the user logs in to the device through SSH or Telnet, so configure the authentication mode of the VTY user interface as scheme.
[Sysname] display user-interface vty ? INTEGER<0-15> Specify one user terminal interface
The output shows that the device supports sixteen VTY user interfaces, which are numbered 0 through 15.
[Sysname] user-interface vty 0 15 [Sysname-ui-vty0-15] authentication-mode scheme [Sysname-ui-vty0-15] quit
Configuration performed by the security log administrator:
# Log in to the device as user seclog.
C:/> telnet 1.1.1.1 ****************************************************************************** * Copyright (c) 2010-2013 Hewlett-Packard Development Company, L.P. * * Without the owner's prior written consent, * * no decompiling or reverse-engineering shall be allowed. * ****************************************************************************** Login authentication Username:seclog Password: <Sysname>
# Display the summary of the security log file.
<Sysname> display security-logfile summary Security-log is enabled. Security-log file size quota: 1MB Security-log file directory: flash:/seclog Alarm-threshold: 80% Current usage: 0% Writing frequency: 1 hour 0 min 0 sec
The output shows that the directory for saving the security log file is flash:/seclog.
# Change the directory where the security log file is saved to Flash:/securitylog.
<Sysname> mkdir securitylog . %Created dir flash:/securitylog. <Sysname> info-center security-logfile switch-directory flash:/securitylog/
# Display the contents of the security log file buffer.
<Sysname> display security-logfile buffer %@175 Nov 2 17:02:53:766 2011 Sysname SHELL/4/LOGOUT: Trap 1.3.6.1.4.1.25506.2.2.1.1.3.0.2: logout from Console %@176 Nov 2 17:02:53:766 2011 Sysname SHELL/5/SHELL_LOGOUT:Console logged out from aux0.
The content of other logs is not shown.
The preceding information indicates that there is still new content in the buffer that has not been saved into the security log file.
# Manually save the contents of the security log file buffer into the security log file.
<Sysname> security-logfile save Info: Save all the contents in the security log buffer into file flash:/securitylog/seclog.log successfully.
# Display the contents of the security log file.
<Sysname> more securitylog/seclog.log %@157 Nov 2 16:12:01:750 2011 Sysname SHELL/4/LOGIN: Trap 1.3.6.1.4.1.25506.2.2.1.1.3.0.1: login from Console %@158 Nov 2 16:12:01:750 2011 Sysname SHELL/5/SHELL_LOGIN:Console logged in from aux0.
The content of other logs is not shown.