Ensuring that DHCPv6 clients obtain IPv6 addresses from authorized DHCPv6 servers
If DHCPv6 clients obtain invalid IPv6 addresses and network configuration parameters from an unauthorized DHCP server, they will be unable to communicate normally with other network devices. With DHCPv6 snooping, the ports of a device can be configured as trusted or untrusted to make sure that the clients obtain IPv6 addresses only from authorized DHCPv6 servers.
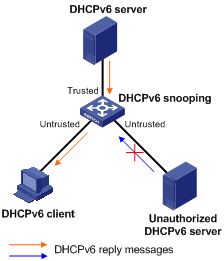
Trusted—A trusted port forwards DHCPv6 messages normally.
Untrusted—An untrusted port discards reply messages from any DHCPv6 server.
Figure 72: Trusted and untrusted ports
A DHCPv6 snooping device's port that is connected to an authorized DHCPv6 server, DHCPv6 relay agent, or another DHCPv6 snooping device should be configured as a trusted port. The trusted port forwards reply messages from the authorized DHCPv6 server. Other ports are configured as untrusted so that they do not forward reply messages from any DHCPv6 servers. This ensures that the DHCPv6 client can obtain an IPv6 address from the authorized DHCPv6 server only.
As shown in Figure 72, configure the port that connects to the DHCPv6 server as a trusted port, and other ports as untrusted.