Example: Configuring basic triple authentication
Network configuration
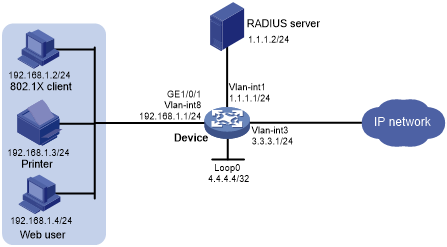
As shown in Figure 92, the terminals are connected to the device to access the IP network. Configure triple authentication on the device's Layer 2 interface that connects to the terminals. A terminal passing one of the three authentication methods, 802.1X authentication, Web authentication, and MAC authentication, can access the IP network.
Assign IP addresses on subnet 192.168.1.0/24 to the terminals.
Use the remote RADIUS server to perform authentication, authorization, and accounting. Configure the device to send usernames carrying no ISP domain names to the RADIUS server.
Configure the local Web authentication server on the device to use listening IP address 4.4.4.4. Configure the device to send a default authentication page to the Web user and forward authentication data by using HTTP.
Figure 92: Network diagram
Procedure
Make sure that the terminals, the server, and the device can reach each other. (Details not shown.)
Configure the RADIUS server to provide normal authentication, authorization, and accounting for users. In this example, configure the following on the RADIUS server:
An 802.1X user with username userdot.
A Web authentication user with username userpt.
A MAC authentication user with a username and password both being the MAC address of the printer f07d6870725f.
Configure Web authentication:
# Configure VLANs and IP addresses for the VLAN interfaces, and add ports to specific VLANs. (Details not shown.)
# Edit authentication pages, compress the pages to a .zip file named abc, and upload the .zip file to the device by FTP. (Details not shown.)
# Configure the local Web server to use HTTP. Configure file abc.zip as the default authentication page file of the local Web server.
<Device> system-view [Device] portal local-web-server http [Device-portal-local-websvr-http] default-logon-page abc.zip [Device-portal-local-websvr-http] quit
# Configure the IP address of interface loopback 0 as 4.4.4.4.
[Device] interface loopback 0 [Device-LoopBack0] ip address 4.4.4.4 32 [Device-LoopBack0] quit
# Create a Web authentication server named webserver and enter its view.
[Device] web-auth server webserver
# Configure the redirection URL for the Web authentication server as http://4.4.4.4/portal/.
[Device-web-auth-server-webserver] url http://4.4.4.4/portal/
# Set the IP address and port number of Web authentication server to 4.4.4.4 and 80.
[Device-web-auth-server-webserver] ip 4.4.4.4 port 80 [Device-web-auth-server-webserver] quit
# Enable Web authentication on , and specify the Web authentication server webserver for the port.
[Device] interface [Device–] web-auth enable apply server webserver [Device–] quit
Configure 802.1X authentication:
# Enable 802.1X authentication globally.
[Device] dot1x
# Enable 802.1X authentication (MAC-based access control required) on .
[Device] interface [Device–] dot1x port-method macbased [Device–] dot1x [Device–] quit
Configure MAC authentication:
# Enable MAC authentication globally.
[Device] mac-authentication
# Enable MAC authentication on .
[Device] interface [Device–] mac-authentication [Device–] quit
Configure a RADIUS scheme:
# Create a RADIUS scheme named rs1.
[Device] radius scheme rs1
# Specify the primary authentication and accounting servers and keys.
[Device-radius-rs1] primary authentication 1.1.1.2 [Device-radius-rs1] primary accounting 1.1.1.2 [Device-radius-rs1] key authentication simple radius [Device-radius-rs1] key accounting simple radius
# Specify usernames sent to the RADIUS server to carry no domain names.
[Device-radius-rs1] user-name-format without-domain [Device-radius-rs1] quit
Configure an ISP domain:
# Create an ISP domain named triple.
[Device] domain triple
# Configure the domain to use RADIUS scheme rs1 for authentication, authorization and accounting of LAN access users.
[Device-isp-triple] authentication lan-access radius-scheme rs1 [Device-isp-triple] authorization lan-access radius-scheme rs1 [Device-isp-triple] accounting lan-access radius-scheme rs1 [Device-isp-triple] quit
# Configure domain triple as the default domain. If a username entered by a user includes no ISP domain name, the AAA method of the default domain is used.
[Device] domain default enable triple
Verifying the configuration
Verify that the Web user can pass Web authentication.
# On the Web user terminal, use a Web browser to access an external network and then enter the correct username and password on the authentication page http://4.4.4.4/portal/logon.html. (Details not shown.)
# Display information about online Web authentication users.
[Device] display web-auth user Total online web-auth users: 1 User Name: localuser MAC address: acf1-df6c-f9ad Access interface: Initial VLAN: 1 Authorization VLAN: N/A Authorization ACL ID: N/A Authorization user profile: N/A
Verify that the printer can pass MAC authentication.
# Connect the printer to the network. (Details not shown.)
# Display information about online MAC authentication users.
Total connections: 1 Slot ID: 1 User MAC address: f07d-6870-725f Access interface: Username: f07d6870725f User access state: Successful Authentication domain: triple Initial VLAN: 14 Authorization untagged VLAN: 14 Authorization tagged VLAN: N/A Authorization VSI: N/A Authorization ACL ID: N/A Authorization user profile: N/A Authorization URL: N/A Termination action: Default Session timeout period: N/A Online from: 2015/01/04 18:01:43 Online duration: 0h 0m 2s
Verify that the 802.1X client can pass 802.1X authentication.
# On the 802.1X client, initiate 802.1X authentication and then enter the correct username and password. (Details not shown.)
# Display information about online 802.1X users.
Total connections: 1 Slot ID: 1 User MAC address: 7446-a091-84fe Access interface: Username: userdot User access state: Successful Authentication domain: triple IPv4 address: 192.168.1.2 Authentication method: CHAP Initial VLAN: 14 Authorization untagged VLAN: 14 Authorization tagged VLAN list: N/A Authorization VSI: N/A Authorization ACL ID: N/A Authorization user profile: N/A Authorization URL: N/A Termination action: Default Session timeout period: N/A Online from: 2015/01/04 18:13:01 Online duration: 0h 0m 14s