Web authentication process
Figure 165: Web authentication process
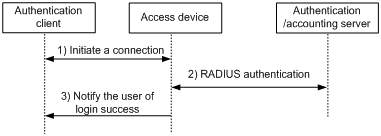
The Web authentication process is as follows:
An unauthetnicated user sends an HTTP request. When the access device receives the HTTP request on a Layer 2 Ethernet interface enabled with Web authentication, it redirects the request to the Web authentication page. The user enters the username and password on the Web authentication page.
If the user requests the Web authentication page or free Web resources, the access device permits the request. No Web authentication is performed.
The access device and the AAA server exchange RADIUS packets to authenticate the user.
If the user passes RADIUS authentication, the local portal Web server pushes a login success page to the authentication client.
If the user fails RADIUS authentication, the local portal Web server pushes a login failure page to the authentication client.
Authorization VLAN
Web authentication uses VLANs authorized by the AAA server or the access device to control network resource access of authenticated users.
After a user passes Web authentication, the AAA server or the access device authorizes the user to access a VLAN. The access device then adds the user to the authorized VLAN and generates a MAC VLAN entry on the user access interface. If the authorized VLAN does not exist on the access device, the access device first creates the VLAN. The access interface allows the packets from the VLAN to pass, with the VLAN tag stripped.
The initial VLAN and the authorized VLAN of a user might be on different subnets. A user can access the resources in the authorized VLAN only when the IP address of the client is on the same subnet as the authorized VLAN. Therefore, a user might need to update the IP address of the client after the user is assigned to the authorized VLAN.
Auth-Fail VLAN
An Auth-Fail VLAN is a VLAN assigned to users who fail authentication. The Auth-Fail VLAN provides network resources such as the patch server, virus definitions server, client software server, and anti-virus software server to the users. The users can use these resources to upgrade their client software or other programs.
Web authentication supports Auth-Fail VLAN on an interface that performs MAC-based access control. If a user on the interface fails authentication, the access devices creates a MAC VLAN entry based on the MAC address of the user and adds the user to the Auth-Fail VLAN. Then, the user can access the portal-free IP resources in the Auth-Fail VLAN. All HTTP requests to non-portal-free IP resources will be redirected to the authentication page. If the user passes authentication, the access device adds the user to the authorized VLAN (if any) or return the user to the initial VLAN of the interface. If the user fails the authentication, the access device keeps the user in the Auth-Fail VLAN.
The initial VLAN and the Auth-Fail VLAN of a user might be on different subnets. A user can access the resources in the authorized VLAN only when the IP address of the client is on the same subnet as the authorized VLAN. Therefore, a user might need to update the IP address of the client after the user is assigned to the authorized VLAN.
Authorization ACL
Web authentication uses ACLs authorized by the AAA server or the access device to control user access to network resources and limit user access rights. When a user passes authentication, the AAA server and the access device assigns an authorization ACL to the access interface of the user. The access device filters traffic from the user on the access interface according to the authorized ACL.
You must configure the authorized ACLs on the access device if you specify authorization ACLs on the authentication server.
To change the access control criteria for the user, you can specify a different authorization ACL on the authentication server or change rules in the authorized ACL on the access device.