Client-oriented MACsec configuration example (device as client)
Network requirements
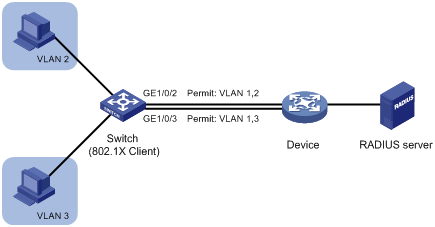
As shown in Figure 162:
The switch connects to the device through trunk ports GigabitEthernet 1/0/2 and GigabitEthernet 1/0/3.
The device acts as an access device. You cannot configure a preshared key on the device for MKA negotiation and packet encryption.
The RADIUS server acts as an 802.1X authentication server.
To secure data between the switch and the device by MACsec, perform the following tasks on the switch:
Enable MACsec desire, and configure MKA to negotiate SAKs for packet encryption.
Configure the 802.1X client feature, so that the switch acts as an 802.1X client and can use 802.1X-generated CAKs for MAcsec.
Figure 161: Network diagram
Configuration procedure
Configure IP addresses for the Ethernet ports. Make sure the switch, the device, and the RADIUS server can reach one another. (Details not shown.)
Configure the access device. (Details not shown.)
Configuration on the access device varies by manufacturer. For information about device configuration, see the corresponding product manual. This part illustrates only the switch configuration, and for information about 802.1X client commands, see Security Command Reference.
Configure the RADIUS server to provide authentication, authorization, and accounting services. Add user accounts. (Details not shown.)
Configure the switch:
# Create VLAN 2.
<Switch> system-view [Switch] vlan 2 [Switch-vlan2] quit
# Configure GigabitEthernet 1/0/2 as a trunk port, and assign the port to VLAN 2.
[Switch] interface gigabitethernet 1/0/2 [Switch-GigabitEthernet1/0/2] port link-type trunk [Switch-GigabitEthernet1/0/2] port trunk permit vlan 2
# Configure the 802.1X client username as aaaa, and set the password to 123456 in plaintext form on GigabitEthernet 1/0/2.
[Switch-GigabitEthernet1/0/2] dot1x supplicant username aaaa [Switch-GigabitEthernet1/0/2] dot1x supplicant password simple 123456
# Specify TTLS-GTC as the 802.1X client EAP authentication method on GigabitEthernet 1/0/2.
[Switch-GigabitEthernet1/0/2] dot1x supplicant eap-method ttls-gtc
# Specify MAC address 1-1-1 for 802.1X client authentication on GigabitEthernet 1/0/2.
[Switch-GigabitEthernet1/0/2] dot1x supplicant mac-address 1-1-1
# Enable the 802.1X client feature on GigabitEthernet 1/0/2.
[Switch-GigabitEthernet1/0/2] dot1x supplicant enable
# Configure MACsec desire and enable MKA on GigabitEthernet 1/0/2.
[Switch-GigabitEthernet1/0/2] macsec desire [Switch-GigabitEthernet1/0/2] mka enable [Switch-GigabitEthernet1/0/2] quit
# Create VLAN 3.
[Switch] vlan 3 [Switch-vlan3] quit
# Configure GigabitEthernet 1/0/3 as a trunk port, and assign the port to VLAN 3.
[Switch] interface gigabitethernet 1/0/3 [Switch-GigabitEthernet1/0/3] port link-type trunk [Switch-GigabitEthernet1/0/3] port trunk permit vlan 3
# Configure the 802.1X client username as bbbb, and set the password to 654321 in plaintext form on GigabitEthernet 1/0/3.
[Switch-GigabitEthernet1/0/3] dot1x supplicant username bbbb [Switch-GigabitEthernet1/0/3] dot1x supplicant password simple 654321
# Specify TTLS-GTC as the 802.1X client EAP authentication method on GigabitEthernet 1/0/3.
[Switch-GigabitEthernet1/0/3] dot1x supplicant eap-method ttls-gtc
# Specify MAC address 1-1-2 for 802.1X client authentication on GigabitEthernet 1/0/3.
[Switch-GigabitEthernet1/0/3] dot1x supplicant mac-address 1-1-2
# Enable the 802.1X client feature on GigabitEthernet 1/0/3.
[Switch-GigabitEthernet1/0/3] dot1x supplicant enable
# Configure MACsec desire and enable MKA on GigabitEthernet 1/0/3.
[Switch-GigabitEthernet1/0/3] macsec desire [Switch-GigabitEthernet1/0/3] mka enable [Switch-GigabitEthernet1/0/3] quit
Verifying the configuration
# Display MACsec information on GigabitEthernet 1/0/2.
[Switch] display macsec interface gigabitethernet 1/0/2 verbose
Interface GigabitEthernet1/0/2
Protect frames : Yes
Replay protection : Enabled
Replay window size : 0 frames
Confidentiality offset : 0 bytes
Validation mode : Check
Included SCI : No
SCI conflict : No
Cipher suite : GCM-AES-128
Transmit secure channel:
SCI : 00E00100000A0006
Elapsed time: 00h:02m:07s
Current SA : AN 0 PN 1
Receive secure channels:
SCI : 00E0020000000106
Elapsed time: 00h:02m:03s
Current SA : AN 0 LPN 1
Previous SA : AN N/A LPN N/A
# Display MACsec information on GigabitEthernet 1/0/3.
[Switch] display macsec interface gigabitethernet 1/0/3 verbose
Interface GigabitEthernet1/0/3
Protect frames : Yes
Replay protection : Enabled
Replay window size : 0 frames
Confidentiality offset : 0 bytes
Validation mode : Check
Included SCI : No
SCI conflict : No
Cipher suite : GCM-AES-128
Transmit secure channel:
SCI : A087100801000103
Elapsed time: 00h:00m:55s
Current SA : AN 0 PN 1
Receive secure channels:
SCI : A0872B3602000003
Elapsed time: 00h:00m:52s
Current SA : AN 0 LPN 1
Previous SA : AN N/A LPN N/A
# Display MKA session information on GigabitEthernet 1/0/2 after 802.1X client user aaaa comes online.
[Switch] display mka session interface gigabitethernet 1/0/2 verbose Interface GigabitEthernet1/0/2 Tx-SCI : 00E00100000A0006 Priority : 0 Capability: 3 CKN for participant: 1234 Key server : No MI (MN) : A1E0D2897596817209CD2307 (2509) Live peers : 1 Potential peers : 0 Principal actor : Yes MKA session status : Secured Confidentiality offset: 0 bytes Current SAK status : Rx & Tx Current SAK AN : 0 Current SAK KI (KN) : A1E0D2897596817209CD230700000002 (2) Previous SAK status : N/A Previous SAK AN : N/A Previous SAK KI (KN) : N/A Live peer list: MI MN Priority Capability Rx-SCI B2CAF896C9BFE2ABFB135E63 2512 0 3 00E0020000000106
# Display MKA session information on GigabitEthernet 1/0/3 after 802.1X client user bbbb comes online.
[Switch] display mka session interface gigabitethernet 1/0/3 verbose
Interface GigabitEthernet1/0/3
Tx-SCI : A087100801000103
Priority : 0
Capability: 3
CKN for participant: 7B8784F16F85ED8F9D0130AA9B93D0F0
Key server : No
MI (MN) : D3F6D374598C8FD1F1819D6C (78)
Live peers : 1
Potential peers : 0
Principal actor : Yes
MKA session status : Secured
Confidentiality offset: 0 bytes
Current SAK status : Rx & Tx
Current SAK AN : 0
Current SAK KI (KN) : FCA71854FCAE51398EC2DA7900000001 (1)
Previous SAK status : N/A
Previous SAK AN : N/A
Previous SAK KI (KN) : N/A
Live peer list:
MI MN Priority Capability Rx-SCI
FCA71854FCAE51398EC2DA79 71 0 3 A0872B3602000003