Client-oriented MACsec configuration example (host as client)
Network requirements
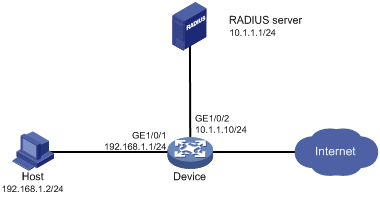
As shown in Figure 161, the host accesses the network through GigabitEthernet 1/0/1. The device performs RADIUS-based 802.1X authentication for the host to control user access to the Internet.
To ensure secure communication between the host and device, perform the following tasks on the device:
Enable MACsec desire, and configure MKA to negotiate SAKs for packet encryption.
Set the MACsec confidentiality offset to 30 bytes.
Enable MACsec replay protection, and set the replay protection window size to 100.
Set the MACsec validation mode to strict.
Figure 160: Network diagram
Configuration procedure
Configure the RADIUS server to provide authentication, authorization, and accounting services. Add a user account for the host. (Details not shown.)
Configure IP addresses for the Ethernet ports. (Details not shown.)
Configure AAA:
# Enter system view.
<Device> system-view
# Configure RADIUS scheme radius1.
[Device] radius scheme radius1 [Device-radius-radius1] primary authentication 10.1.1.1 [Device-radius-radius1] primary accounting 10.1.1.1 [Device-radius-radius1] key authentication simple name [Device-radius-radius1] key accounting simple money [Device-radius-radius1] user-name-format without-domain [Device-radius-radius1] quit
# Configure authentication domain bbb for 802.1X users.
[Device] domain bbb [Device-isp-bbb] authentication lan-access radius-scheme radius1 [Device-isp-bbb] authorization lan-access radius-scheme radius1 [Device-isp-bbb] accounting lan-access radius-scheme radius1 [Device-isp-bbb] quit
Configure 802.1X:
# Enable 802.1X on GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1 [Device-GigabitEthernet1/0/1] dot1x
# Implement port-based access control on GigabitEthernet 1/0/1.
[Device-GigabitEthernet1/0/1] dot1x port-method portbased
# Specify bbb as the mandatory authentication domain for 802.1X users on GigabitEthernet 1/0/1.
[Device-GigabitEthernet1/0/1] dot1x mandatory-domain bbb [Device-GigabitEthernet1/0/1] quit
# Enable 802.1X globally, and sets the device to relay EAP packets.
[Device] dot1x [Device] dot1x authentication-method eap
Configure MACsec:
# Create an MKA policy named pls.
[Device] mka policy pls
# Set the MACsec confidentiality offset to 30 bytes.
[Device-mka-policy-pls] confidentiality-offset 30
# Enable MACsec replay protection.
[Device-mka-policy-pls] replay-protection enable
# Set the MACsec replay protection window size to 100.
[Device-mka-policy-pls] replay-protection window-size 100
# Set the MACsec validation mode to strict.
[Device-mka-policy-pls] validation mode strict [Device-mka-policy-pls] quit
# Apply the MKA policy to GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1 [Device-GigabitEthernet1/0/1] mka apply policy pls
# Configure MACsec desire and enable MKA on GigabitEthernet 1/0/1.
[Device-GigabitEthernet1/0/1] macsec desire [Device-GigabitEthernet1/0/1] mka enable [Device-GigabitEthernet1/0/1] quit
Verifying the configuration
# Display MACsec information on GigabitEthernet 1/0/1.
[Device] display macsec interface gigabitethernet 1/0/1 verbose
Interface GigabitEthernet1/0/1
Protect frames : Yes
Active MKA policy : pls
Replay protection : Enabled
Replay window size : 100 frames
Confidentiality offset : 30 bytes
Validation mode : Strict
Included SCI : No
SCI conflict : No
Cipher suite : GCM-AES-128
Transmit secure channel:
SCI : 00E00100000A0006
Elapsed time: 00h:02m:07s
Current SA : AN 0 PN 1
Receive secure channels:
SCI : 00E0020000000106
Elapsed time: 00h:02m:03s
Current SA : AN 0 LPN 1
Previous SA : AN N/A LPN N/A
# Display MKA session information on GigabitEthernet 1/0/1 after a user logs in.
[Device] display mka session interface gigabitethernet 1/0/1 verbose
Interface GigabitEthernet1/0/1
Tx-SCI : 00E00100000A0006
Priority : 0
Capability: 3
CKN for participant: 1234
Key server : Yes
MI (MN) : A1E0D2897596817209CD2307 (2509)
Live peers : 1
Potential peers : 0
Principal actor : Yes
MKA session status : Secured
Confidentiality offset: 30 bytes
Current SAK status : Rx & Tx
Current SAK AN : 0
Current SAK KI (KN) : A1E0D2897596817209CD230700000002 (2)
Previous SAK status : N/A
Previous SAK AN : N/A
Previous SAK KI (KN) : N/A
Live peer list:
MI MN Priority Capability Rx-SCI
B2CAF896C9BFE2ABFB135E63 2512 0 3 00E0020000000106