MACsec operating mechanism
Operating mechanism for client-oriented mode
Figure 159 illustrates how MACsec operates in client-oriented mode.
Figure 158: MACsec interactive process in client-oriented mode
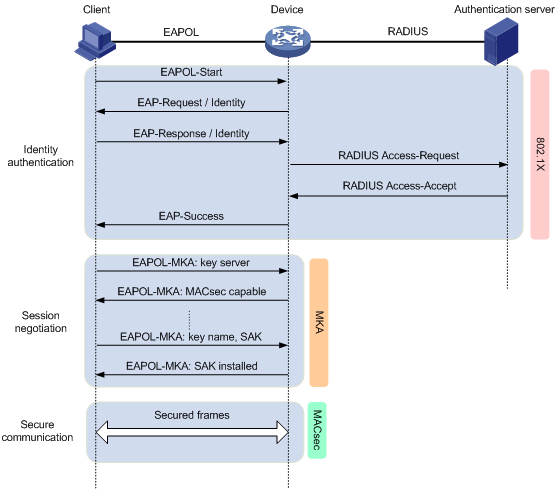
The following shows the MACsec process:
After the client passes 802.1X authentication, the RADIUS server distributes the generated CAK to the client and the access device.
After receiving the CAK, the client and the access device exchange EAPOL-MKA packets.
The client and the access device exchange the MACsec capability and required parameters for session establishment. The parameters include MKA key server priority and MACsec desire.
During the negotiation process, the access device automatically becomes the key server. The key server generates an SAK from the CAK for packet encryption, and it distributes the SAK to the client.
The client and the access device use the SAK to encrypt packets, and they send and receive the encrypted packets in secure channels.
When the access device receives a logoff request from the client, it immediately removes the associated secure session from the port. The remove operation prevents an unauthorized client from using the secure session established by the previous authorized client to access the network.
The MKA protocol also defines a session keepalive timer. If one participant does not receive any MKA packets from the peer after the timer expires, the participant removes the established secure session. The keepalive time is 6 seconds.
Operating mechanism for device-oriented mode
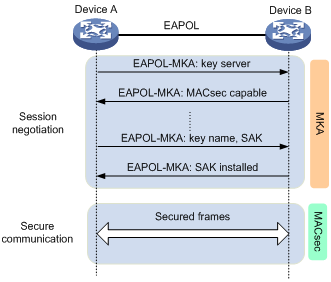
As shown in Figure 160, the devices use the configured preshared keys to start the session negotiation.
In this mode, the session negotiation, secure communication, and session termination processes are the same as the processes in client-oriented mode. However, MACsec performs a key server selection in this mode. The port with higher MKA key server priority becomes the key server, which is responsible for the generation and distribution of SAKs.
Figure 159: MACsec interactive process in device-oriented mode