Overview
MAC-forced forwarding (MFF) implements Layer 2 isolation and Layer 3 communication between hosts in the same broadcast domain.
An MFF-enabled device intercepts ARP requests and returns the MAC address of a gateway (or server) to the senders. In this way, the senders are forced to send packets to the gateway for traffic monitoring and attack prevention.
![[NOTE: ]](images/note.png) | NOTE: MFF does not support VRRPE for a gateway. | |
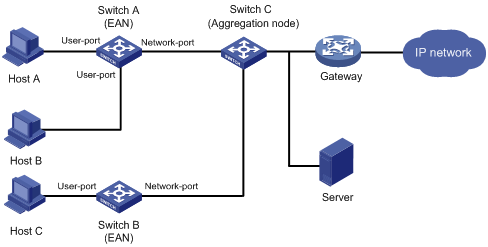
As shown in Figure 152, hosts are connected to Switch C through Switch A and Switch B, which are called Ethernet access nodes (EANs). The MFF-enabled EANs forward packets from hosts to the gateway for further forwarding. The hosts are isolated at Layer 2, but they can communicate at Layer 3.
An MFF-enabled device and a host cannot ping each other.
Figure 151: Network diagram for MFF
MFF works with any of the following features to implement traffic filtering and Layer 2 isolation on the EANs:
DHCP snooping (see Layer 3—IP Services Configuration Guide).
ARP snooping (see Layer 3—IP Services Configuration Guide).
IP source guard (see "Configuring IP source guard).
ARP detection (see "Configuring ARP attack protection").
VLAN mapping (see Layer 2—LAN Switching Configuration Guide).
![[NOTE: ]](images/note.png) | NOTE: When MFF works with static IP source guard bindings, you must configure VLAN IDs in the static bindings. Otherwise, IP packets allowed by IP source guard are permitted even if their destination MAC addresses are not the MAC address of the gateway. | |