Certificate import and export configuration example
Network requirements
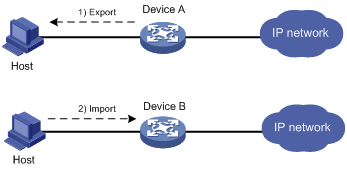
As shown in Figure 89, Device B will replace Device A in the network. PKI domain exportdomain on Device A has two local certificates containing the private key and one CA certificate. To make sure the certificates are still valid after Device B replaces Device A, copy the certificates on Device A to Device B as follows:
Export the certificates in PKI domain exportdomain on Device A to .pem certificate files.
During the export, encrypt the private key in the local certificates using 3DES_CBC with the password 11111.
Transfer the certificate files from Device A to Device B through the FTP host.
Import the certificate files to PKI domain importdomain on Device B.
Figure 88: Network diagram
Configuration procedure
Export the certificates on Device A:
# Export the CA certificate to a .pem file.
<DeviceA> system-view [DeviceA] pki export domain exportdomain pem ca filename pkicachain.pem
# Export the local certificate to a file named pkilocal.pem in PEM format, and use 3DES_CBC to encrypt the private key with the password 111111.
[DeviceA] pki export domain exportdomain pem local 3des-cbc 111111 filename pkilocal.pem
Now, Device A has three certificate files in PEM format:
A CA certificate file named pkicachain.pem.
A local certificate file named pkilocal.pem-signature, which contains the private key for signature.
A local certificate file named pkilocal.pem-encryption, which contains the private key for encryption.
# Display the local certificate file pkilocal.pem-signature.
[DeviceA] quit <DeviceA> more pkicachain.pem-sign Bag Attributes friendlyName: localKeyID: 90 C6 DC 1D 20 49 4F 24 70 F5 17 17 20 2B 9E AC 20 F3 99 89 subject=/C=CN/O=OpenCA Labs/OU=Users/CN=subsign 11 issuer=/C=CN/L=shangdi/ST=pukras/O=OpenCA Labs/OU=docm/CN=subca1 -----BEGIN CERTIFICATE----- MIIEgjCCA2qgAwIBAgILAJgsebpejZc5UwAwDQYJKoZIhvcNAQELBQAwZjELMAkG … -----END CERTIFICATE----- Bag Attributes friendlyName: localKeyID: 90 C6 DC 1D 20 49 4F 24 70 F5 17 17 20 2B 9E AC 20 F3 99 89 Key Attributes: <No Attributes> -----BEGIN ENCRYPTED PRIVATE KEY----- MIICxjBABgkqhkiG9w0BBQ0wMzAbBgkqhkiG9w0BBQwwDgQIZtjSjfslJCoCAggA … -----END ENCRYPTED PRIVATE KEY-----# Display the local certificate file pkilocal.pem-encryption.
<DeviceA> more pkicachain.pem-encr Bag Attributes friendlyName: localKeyID: D5 DF 29 28 C8 B9 D9 49 6C B5 44 4B C2 BC 66 75 FE D6 6C C8 subject=/C=CN/O=OpenCA Labs/OU=Users/CN=subencr 11 issuer=/C=CN/L=shangdi/ST=pukras/O=OpenCA Labs/OU=docm/CN=subca1 -----BEGIN CERTIFICATE----- MIIEUDCCAzigAwIBAgIKCHxnAVyzWhIPLzANBgkqhkiG9w0BAQsFADBmMQswCQYD … -----END CERTIFICATE----- Bag Attributes friendlyName: localKeyID: D5 DF 29 28 C8 B9 D9 49 6C B5 44 4B C2 BC 66 75 FE D6 6C C8 Key Attributes: <No Attributes> -----BEGIN ENCRYPTED PRIVATE KEY----- MIICxjBABgkqhkiG9w0BBQ0wMzAbBgkqhkiG9w0BBQwwDgQI7H0mb4O7/GACAggA … -----END ENCRYPTED PRIVATE KEY-----Download the certificate files pkicachain.pem, pkilocal.pem-sign, and pkilocal.pem-encr from Device A to the host through FTP. (Details not shown.)
Upload the certificate files pkicachain.pem, pkilocal.pem-sign, and pkilocal.pem-encr from the host to Device B through FTP. (Details not shown.)
Import the certificate files to Device B:
# Disable CRL checking. (You can configure CRL checking as required. This example assumes CRL checking is not required.)
<DeviceB> system-view [DeviceB] pki domain importdomain [DeviceB-pki-domain-importdomain] undo crl check enable
# Specify the RSA key pair for signature as sign, and the RSA key pair for encryption as encr for certificate request.
[DeviceB-pki-domain-importdomain] public-key rsa signature name sign encryption name encr [DeviceB-pki-domain-importdomain] quit
# Import the CA certificate file pkicachain.pem in PEM format to the PKI domain.
[DeviceB] pki import domain importdomain pem ca filename pkicachain.pem
# Import the local certificate file pkilocal.pem-signature in PEM format to the PKI domain. The certificate file contains a key pair.
[DeviceB] pki import domain importdomain pem local filename pkilocal.pem-signature Please input the password:******
# Import the local certificate file pkilocal.pem-encryption in PEM format to the PKI domain. The certificate file contains a key pair.
[DeviceB] pki import domain importdomain pem local filename pkilocal.pem-encryption Please input the password:******
# Display the imported local certificate information on Device B.
[DeviceB] display pki certificate domain importdomain local Certificate: Data: Version: 3 (0x2) Serial Number: 98:2c:79:ba:5e:8d:97:39:53:00 Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, L=shangdi, ST=pukras, O=OpenCA Labs, OU=docm, CN=subca1 Validity Not Before: May 26 05:56:49 2011 GMT Not After : Nov 22 05:56:49 2012 GMT Subject: C=CN, O=OpenCA Labs, OU=Users, CN=subsign 11 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (1024 bit) Modulus: 00:9f:6e:2f:f6:cb:3d:08:19:9a:4a:ac:b4:ac:63: ce:8d:6a:4c:3a:30:19:3c:14:ff:a9:50:04:f5:00: ee:a3:aa:03:cb:b3:49:c4:f8:ae:55:ee:43:93:69: 6c:bf:0d:8c:f4:4e:ca:69:e5:3f:37:5c:83:ea:83: ad:16:b8:99:37:cb:86:10:6b:a0:4d:03:95:06:42: ef:ef:0d:4e:53:08:0a:c9:29:dd:94:28:02:6e:e2: 9b:87:c1:38:2d:a4:90:a2:13:5f:a4:e3:24:d3:2c: bf:98:db:a7:c2:36:e2:86:90:55:c7:8c:c5:ea:12: 01:31:69:bf:e3:91:71:ec:21 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Cert Type: SSL Client, S/MIME X509v3 Key Usage: Digital Signature, Non Repudiation X509v3 Extended Key Usage: TLS Web Client Authentication, E-mail Protection, Microsoft Smartcardlogin Netscape Comment: User Certificate of OpenCA Labs X509v3 Subject Key Identifier: AA:45:54:29:5A:50:2B:89:AB:06:E5:BD:0D:07:8C:D9:79:35:B1:F5 X509v3 Authority Key Identifier: keyid:70:54:40:61:71:31:02:06:8C:62:11:0A:CC:A5:DB:0E:7E:74:DE:DD X509v3 Subject Alternative Name: email:subsign@docm.com X509v3 Issuer Alternative Name: DNS:subca1@docm.com, DNS:, IP Address:1.1.2.2, IP Address:2.2.1.1 Authority Information Access: CA Issuers - URI:http://titan/pki/pub/cacert/cacert.crt OCSP - URI:http://titan:2560/ 1.3.6.1.5.5.7.48.12 - URI:http://titan:830/ X509v3 CRL Distribution Points: Full Name: URI:http://192.168.40.130/pki/pub/crl/cacrl.crl Signature Algorithm: sha256WithRSAEncryption 18:e7:39:9a:ad:84:64:7b:a3:85:62:49:e5:c9:12:56:a6:d2: 46:91:53:8e:84:ba:4a:0a:6f:28:b9:43:bc:e7:b0:ca:9e:d4: 1f:d2:6f:48:c4:b9:ba:c5:69:4d:90:f3:15:c4:4e:4b:1e:ef: 2b:1b:2d:cb:47:1e:60:a9:0f:81:dc:f2:65:6b:5f:7a:e2:36: 29:5d:d4:52:32:ef:87:50:7c:9f:30:4a:83:de:98:8b:6a:c9: 3e:9d:54:ee:61:a4:26:f3:9a:40:8f:a6:6b:2b:06:53:df:b6: 5f:67:5e:34:c8:c3:b5:9b:30:ee:01:b5:a9:51:f9:b1:29:37: 02:1a:05:02:e7:cc:1c:fe:73:d3:3e:fa:7e:91:63:da:1d:f1: db:28:6b:6c:94:84:ad:fc:63:1b:ba:53:af:b3:5d:eb:08:b3: 5b:d7:22:3a:86:c3:97:ef:ac:25:eb:4a:60:f8:2b:a3:3b:da: 5d:6f:a5:cf:cb:5a:0b:c5:2b:45:b7:3e:6e:39:e9:d9:66:6d: ef:d3:a0:f6:2a:2d:86:a3:01:c4:94:09:c0:99:ce:22:19:84: 2b:f0:db:3e:1e:18:fb:df:56:cb:6f:a2:56:35:0d:39:94:34: 6d:19:1d:46:d7:bf:1a:86:22:78:87:3e:67:fe:4b:ed:37:3d: d6:0a:1c:0b Certificate: Data: Version: 3 (0x2) Serial Number: 08:7c:67:01:5c:b3:5a:12:0f:2f Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, L=shangdi, ST=pukras, O=OpenCA Labs, OU=docm, CN=subca1 Validity Not Before: May 26 05:58:26 2011 GMT Not After : Nov 22 05:58:26 2012 GMT Subject: C=CN, O=OpenCA Labs, OU=Users, CN=subencr 11 Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (1024 bit) Modulus: 00:db:26:13:d3:d1:a4:af:11:f3:6d:37:cf:d0:d4: 48:50:4e:0f:7d:54:76:ed:50:28:c6:71:d4:48:ae: 4d:e7:3d:23:78:70:63:18:33:f6:94:98:aa:fa:f6: 62:ed:8a:50:c6:fd:2e:f4:20:0c:14:f7:54:88:36: 2f:e6:e2:88:3f:c2:88:1d:bf:8d:9f:45:6c:5a:f5: 94:71:f3:10:e9:ec:81:00:28:60:a9:02:bb:35:8b: bf:85:75:6f:24:ab:26:de:47:6c:ba:1d:ee:0d:35: 75:58:10:e5:e8:55:d1:43:ae:85:f8:ff:75:81:03: 8c:2e:00:d1:e9:a4:5b:18:39 Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Cert Type: SSL Server X509v3 Key Usage: Key Encipherment, Data Encipherment Netscape Comment: VPN Server of OpenCA Labs X509v3 Subject Key Identifier: CC:96:03:2F:FC:74:74:45:61:38:1F:48:C0:E8:AA:18:24:F0:2B:AB X509v3 Authority Key Identifier: keyid:70:54:40:61:71:31:02:06:8C:62:11:0A:CC:A5:DB:0E:7E:74:DE:DD X509v3 Subject Alternative Name: email:subencr@docm.com X509v3 Issuer Alternative Name: DNS:subca1@docm.com, DNS:, IP Address:1.1.2.2, IP Address:2.2.1.1 Authority Information Access: CA Issuers - URI:http://titan/pki/pub/cacert/cacert.crt OCSP - URI:http://titan:2560/ 1.3.6.1.5.5.7.48.12 - URI:http://titan:830/ X509v3 CRL Distribution Points: Full Name: URI:http://192.168.40.130/pki/pub/crl/cacrl.crl Signature Algorithm: sha256WithRSAEncryption 53:69:66:5f:93:f0:2f:8c:54:24:8f:a2:f2:f1:29:fa:15:16: 90:71:e2:98:e3:5c:c6:e3:d4:5f:7a:f6:a9:4f:a2:7f:ca:af: c4:c8:c7:2c:c0:51:0a:45:d4:56:e2:81:30:41:be:9f:67:a1: 23:a6:09:50:99:a1:40:5f:44:6f:be:ff:00:67:9d:64:98:fb: 72:77:9e:fd:f2:4c:3a:b2:43:d8:50:5c:48:08:e7:77:df:fb: 25:9f:4a:ea:de:37:1e:fb:bc:42:12:0a:98:11:f2:d9:5b:60: bc:59:72:04:48:59:cc:50:39:a5:40:12:ff:9d:d0:69:3a:5e: 3a:09:5a:79:e0:54:67:a0:32:df:bf:72:a0:74:63:f9:05:6f: 5e:28:d2:e8:65:49:e6:c7:b5:48:7d:95:47:46:c1:61:5a:29: 90:65:45:4a:88:96:e4:88:bd:59:25:44:3f:61:c6:b1:08:5b: 86:d2:4f:61:4c:20:38:1c:f4:a1:0b:ea:65:87:7d:1c:22:be: b6:17:17:8a:5a:0f:35:4c:b8:b3:73:03:03:63:b1:fc:c4:f5: e9:6e:7c:11:e8:17:5a:fb:39:e7:33:93:5b:2b:54:72:57:72: 5e:78:d6:97:ef:b8:d8:6d:0c:05:28:ea:81:3a:06:a0:2e:c3: 79:05:cd:c3
To display detailed information about the CA certificate, use the display pki certificate domain command.