Authentication and authorization of 802.1X users by the device as a RADIUS server
Network requirements
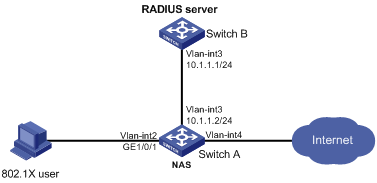
As shown inFigure 28, Switch B acts as the RADIUS server for authentication and authorization of 802.1X users connected to the NAS (Switch A).
Configure the switches to meet the following requirements:
Perform 802.1X authentication on GigabitEthernet 1/0/1 of the NAS.
The shared key is expert and the authentication port is 1812.
Exclude domain names from the usernames sent to the RADIUS server.
The user name for 802.1X authentication is dot1x.
After the user passes authentication, the RADIUS server authorizes VLAN 4 to the NAS port that the user is connecting to.
Figure 27: Network diagram
Configuration procedure
Configure interfaces and VLANs, so the host promptly obtains a new IP address to access resources in the authorized VLAN after passing authentication. (Details not shown.)
Configure the NAS:
Configure a RADIUS scheme:
# Configure a RADIUS scheme named rad and enter RADIUS scheme view.
<SwitchA> system-view [SwitchA] radius scheme rad
# Specify the primary authentication server with IP address 10.1.1.1 and set the shared key to expert in plaintext form.
[SwitchA-radius-rad] primary authentication 10.1.1.1 key simple expert
# Exclude domain names from the usernames sent to the RADIUS server.
[SwitchA-radius-rad] user-name-format without-domain [SwitchA-radius-rad] quit
Configure an authentication domain:
# Create an ISP domain named bbb and enter ISP domain view.
[SwitchA] domain bbb
# Configure the ISP domain to use RADIUS scheme rad for authentication and authorization of LAN users and not to perform accounting for LAN users.
[SwitchA-isp-bbb] authentication lan-access radius-scheme rad [SwitchA-isp-bbb] authorization lan-access radius-scheme rad [SwitchA-isp-bbb] accounting lan-access none [SwitchA-isp-bbb] quit
Configure 802.1X authentication:
# Enable 802.1X for GigabitEthernet 1/0/1.
[SwitchA] interface gigabitethernet 1/0/1 [SwitchA-GigabitEthernet1/0/1] dot1x
# Specify bbb as the mandatory authentication domain for 802.1X users on the interface.
[SwitchA-GigabitEthernet1/0/1] dot1x mandatory-domain bbb [SwitchA-GigabitEthernet1/0/1] quit
# Enable 802.1X globally.
[SwitchA] dot1x
Configure the RADIUS server:
# Create a network access user named dot1x.
<SwitchB> system-view [SwitchB] local-user dot1x class network
# Configure the password as 123456 in plaintext form.
[SwitchB-luser-network-dot1x] password simple 123456
# Configure VLAN 4 as the authorization VLAN.
[SwitchB-luser-network-dot1x] authorization-attribute vlan 4 [SwitchB-luser-network-dot1x] quit
# Configure the IP address of the RADIUS client as 10.1.1.2 and the shared key as expert in plaintext form.
[SwitchB] radius-server client ip 10.1.1.2 key simple expert
# Activate the RADIUS server configuration.
[SwitchB] radius-server activate
Verifying the configuration
On the RADIUS server, display the activated RADIUS clients and users.
[SwitchB] display radius-server active-client Total 1 RADIUS clients. Client IP: 10.1.1.2 [SwitchB] display radius-server active-user dot1x Total 1 RADIUS users matched. Username: dot1x Description: Not configured Authorization attributes: VLAN ID: 4 ACL number: Not configured Validity period: Expiration time: Not configuredOn the host, use the dot1x user for 802.1X authentication.
If the user host runs the Windows built-in 802.1X client, configure the network connection properties as follows:
Click the Authentication tab of the properties window.
Select the Enable IEEE 802.1X authentication for this network option.
Select MD5 challenge as the EAP type.
Click OK.
If the user host runs the iNode client, no advanced authentication options are required.
The user passes authentication after entering the correct user name and password on the authentication page or the iNode client.
On the NAS, verify that the RADIUS server assigns the user access port to VLAN 4 after the user passes authentication. (Details not shown.)
On the NAS, display online 802.1X user information.
[SwitchA] display dot1x connection