LDAP
The Lightweight Directory Access Protocol (LDAP) provides standard multiplatform directory service. LDAP was developed on the basis of the X.500 protocol. It improves the following functions of X.500:
Read/write interactive access.
Browse.
Search.
LDAP is suitable for storing data that does not often change. The protocol is used to store user information. For example, LDAP server software Active Directory Server is used in Microsoft Windows operating systems. The software stores the user information and user group information for user login authentication and authorization.
LDAP directory service
LDAP uses directories to maintain the organization information, personnel information, and resource information. The directories are organized in a tree structure and include entries. An entry is a set of attributes with distinguished names (DNs). The attributes are used to store information such as usernames, passwords, emails, computer names, and phone numbers.
LDAP uses a client/server model, and all directory information is stored in the LDAP server. Commonly used LDAP server products include Microsoft Active Directory Server, IBM Tivoli Directory Server, and Sun ONE Directory Server.
LDAP authentication and authorization
AAA can use LDAP to provide authentication and authorization services for users. LDAP defines a set of operations to implement its functions. The main operations for authentication and authorization are the bind operation and search operation.
The bind operation allows an LDAP client to perform the following operations:
Establish a connection with the LDAP server.
Obtain the access rights to the LDAP server.
Check the validity of user information.
The search operation constructs search conditions and obtains the directory resource information of the LDAP server.
In LDAP authentication, the client completes the following tasks:
Uses the LDAP server administrator DN to bind with the LDAP server. After the binding is created, the client establishes a connection to the server and obtains the right to search.
Constructs search conditions by using the username in the authentication information of a user. The specified root directory of the server is searched and a user DN list is generated.
Binds with the LDAP server by using each user DN and password. If a binding is created, the user is considered legal.
In LDAP authorization, the client performs the same tasks as in LDAP authentication. When the client constructs search conditions, it obtains both authorization information and the user DN list.
Basic LDAP authentication process
The following example illustrates the basic LDAP authentication process for a Telnet user.
Figure 7: Basic LDAP authentication process for a Telnet user
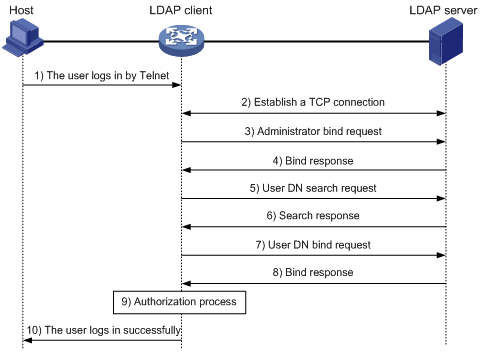
The following shows the basic LDAP authentication process:
A Telnet user initiates a connection request and sends the username and password to the LDAP client.
After receiving the request, the LDAP client establishes a TCP connection with the LDAP server.
To obtain the right to search, the LDAP client uses the administrator DN and password to send an administrator bind request to the LDAP server.
The LDAP server processes the request. If the bind operation is successful, the LDAP server sends an acknowledgment to the LDAP client.
The LDAP client sends a user DN search request with the username of the Telnet user to the LDAP server.
After receiving the request, the LDAP server searches for the user DN by the base DN, search scope, and filtering conditions. If a match is found, the LDAP server sends a response to notify the LDAP client of the successful search. There might be one or more user DNs found.
The LDAP client uses the obtained user DN and the entered user password as parameters to send a user DN bind request to the LDAP server. The server will check whether the user password is correct.
The LDAP server processes the request, and sends a response to notify the LDAP client of the bind operation result. If the bind operation fails, the LDAP client uses another obtained user DN as the parameter to send a user DN bind request to the LDAP server. This process continues until a DN is bound successfully or all DNs fail to be bound. If all user DNs fail to be bound, the LDAP client notifies the user of the login failure and denies the user's access request.
The LDAP client saves the user DN that has been bound and exchanges authorization packets with the authorization server.
If LDAP authorization is used, see the authorization process shown in Figure 8.
If another method is expected for authorization, the authorization process of that method applies.
After successful authorization, the LDAP client notifies the user of the successful login.
Basic LDAP authorization process
The following example illustrates the basic LDAP authorization process for a Telnet user.
Figure 8: Basic LDAP authorization process for a Telnet user
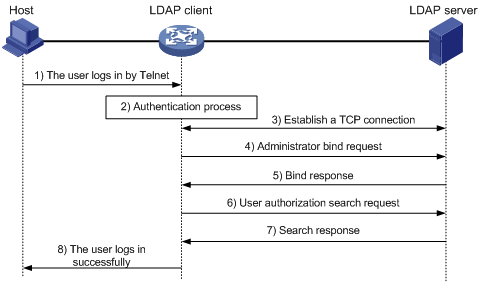
The following shows the basic LDAP authorization process:
A Telnet user initiates a connection request and sends the username and password to the device. The device will act as the LDAP client during authorization.
After receiving the request, the device exchanges authentication packets with the authentication server for the user:
If LDAP authentication is used, see the authentication process shown in Figure 7.
If the device (the LDAP client) uses the same LDAP server for authentication and authorization, skip to step 6.
If the device (the LDAP client) uses different LDAP servers for authentication and authorization, skip to step 4.
If another authentication method is used, the authentication process of that method applies. The device acts as the LDAP client. Skip to step 3.
The LDAP client establishes a TCP connection with the LDAP authorization server.
To obtain the right to search, the LDAP client uses the administrator DN and password to send an administrator bind request to the LDAP server.
The LDAP server processes the request. If the bind operation is successful, the LDAP server sends an acknowledgment to the LDAP client.
The LDAP client sends an authorization search request with the username of the Telnet user to the LDAP server. If the user uses the same LDAP server for authentication and authorization, the client sends the request with the saved user DN of the Telnet user to the LDAP server.
After receiving the request, the LDAP server searches for the user information by the base DN, search scope, filtering conditions, and LDAP attributes. If a match is found, the LDAP server sends a response to notify the LDAP client of the successful search.
After successful authorization, the LDAP client notifies the user of the successful login.