Designing secure applications |
Understanding how the controller handles authentication
The HPE VAN SDN Controller uses OpenStack Keystone to provide token-based authentication. This security mechanism:
Provides user authentication.
Completely isolates the security mechanism from the underlying REST API.
Exposes a REST API to allow any authentication server that implements this REST API to be hosted elsewhere (outside the SDN controller).
This security mechanism does not:
Provide authorization. Your SDN application must provide authorization functions.
Support filtering functions such as black-listing or rate-limiting.
To achieve isolation of security aspects from the API, authentication information is encapsulated by a token that a user receives by presenting his/her credentials to an authentication server. The user then uses this token (via the RESTful API header X-Auth-Token) in any API call that requires authentication. The token is validated by an Authentication Filter that fronts the requested API resource.
Upon successful authentication, requests are forwarded to the RESTful APIs with the authentication information such as:
User ID
User name
User roles
Expiration Date
Upon unsuccessful authentication (either no token or invalid token), it is up to the application to deny or allow access to its resource. This flexibility allows the application to implement its own authorization mechanism, such as ACL-based or even allow anonymous operations on certain resources.
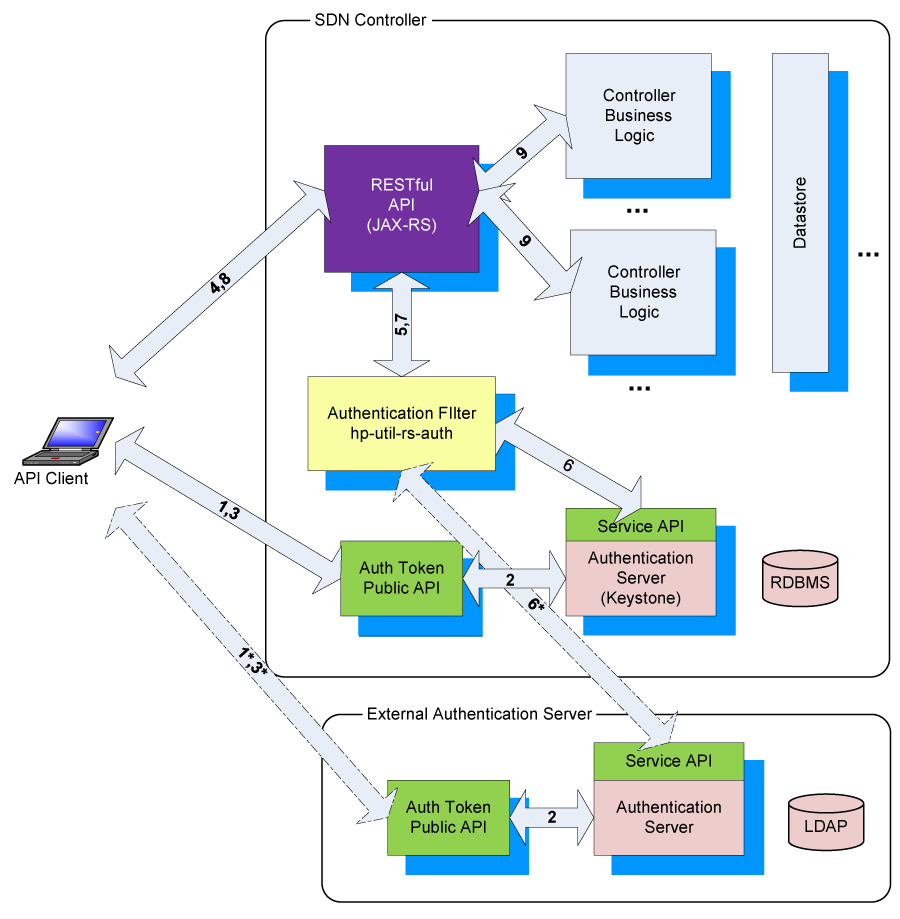
The flow of token-based authentication in the HPE VAN SDN Controller can be summarized as illustrated in Token-based authentication flow.
API Client presents credentials (username/password) to the AuthToken REST API.
Authentication is performed by the authentication server.
The HPE VAN SDN Controller supports a local Keystone-based authentication server, but the authentication server can also be hosted elsewhere by the customer (and can be integrated with an enterprise directory such as LDAP for example), as long as it implements the AuthToken REST API. The external authentication server use-case is shown by the dotted-line interactions.
The authentication server returns the token to the API client.
The API client includes this token in the X-Auth-Token header when making a request to the HPE VAN SDN Controller’s RESTful API.
The token is intercepted by the Authentication Filter (Servlet Filter).
The Authentication Filter validates the token with the authentication server via a different AuthToken REST API.
The Authentication Filter returns the validation status back to the REST API.
If the validation is unsuccessful (no token or invalid token), the HPE VAN SDN Controller returns status 401 (Unauthorized) back to the API Client.
If the validation is successful, the API Client’s HPE VAN SDN Controller REST API request is invoked and the business logic related to the request is executed.
To isolate services and applications from Keystone specifics, two different authentication service APIs (AuthToken REST API's) are published:
Public API (/auth):
Create token. This accepts username/password credentials and return back a unique token with some expiration.
Service API:
Revoke token. This revokes a given token.
Validate token. This validates a given token and returns back the appropriate principal's information.
Authentication services have been split into these two APIs to limit sensitive services (Service API) to only authorized clients.
Getting an authorization token:
To get an authorization token using the controller RSdoc, see Getting an authorization token using RSdoc.
To get an authorization token using curl commands, see Getting an authorization token using a curl command.