Configuration example
Network requirements
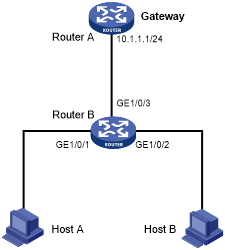
As shown in Figure 207, Host B launches gateway spoofing attacks to Router B. As a result, traffic that Router B intends to send to Router A is sent to Host B.
Configure Router B to block such attacks.
Figure 202: Network diagram
Configuration procedure
# Configure ARP gateway protection on Router B.
<RouterB> system-view [RouterB] interface gigabitethernet 1/0/1 [RouterB-GigabitEthernet1/0/1] arp filter source 10.1.1.1 [RouterB-GigabitEthernet1/0/1] quit [RouterB] interface gigabitethernet 1/0/2 [RouterB-GigabitEthernet1/0/2] arp filter source 10.1.1.1
Verifying the configuration
# Verify that GigabitEthernet 1/0/1 and GigabitEthernet 1/0/2 discard the incoming ARP packets whose sender IP address is the IP address of the gateway.