Interface-based HTTP client verification configuration example
Network requirements
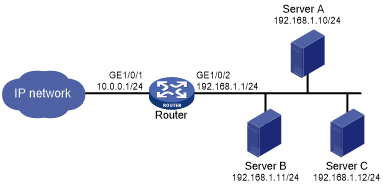
As shown in Figure 195, configure HTTP client verification on the router to protect internal servers against HTTP flood attacks.
Figure 190: Network diagram
Configuration procedure
# Configure IP addresses for the interfaces on the router. (Details not shown.)
# Create attack defense policy a1.
<Router> system-view [Router] attack-defense policy a1
# Enable global HTTP flood attack detection.
[Router-attack-defense-policy-a1] http-flood detect non-specific
# Set the global threshold to 10000 for triggering HTTP flood attack prevention.
[Router-attack-defense-policy-a1] http-flood threshold 10000
# Specify logging and client-verify as the global actions against HTTP flood attacks.
[Router-attack-defense-policy-a1] http-flood action logging client-verify [Router-attack-defense-policy-a1] quit
# Apply the attack defense policy a1 to interface GigabitEthernet 1/0/1.
[Router] interface gigabitethernet 1/0/1 [Router-GigabitEthernet1/0/1] attack-defense apply policy a1 [Router-GigabitEthernet1/0/1] quit
# Enable HTTP client verification on interface GigabitEthernet 1/0/1.
[Router] interface gigabitethernet 1/0/1 [Router-GigabitEthernet1/0/1] client-verify http enable [Router-GigabitEthernet1/0/1] quit
Verifying the configuration
# Launch an HTTP flood attack. (Details not shown.)
# Verify that the victim's IP address is added to the protected IP list for HTTP client verification.
[Router] display client-verify http protected ip IP address VPN instance Port Type Requested Trusted 192.168.1.10 -- 8080 Dynamic 20 12