HTTP client verification
The HTTP client verification feature protects HTTP servers against HTTP flood attacks. It is configured on the device where packets from the HTTP clients to the HTTP servers pass through. A device with HTTP client verification feature configured is called an HTTP client authenticator.
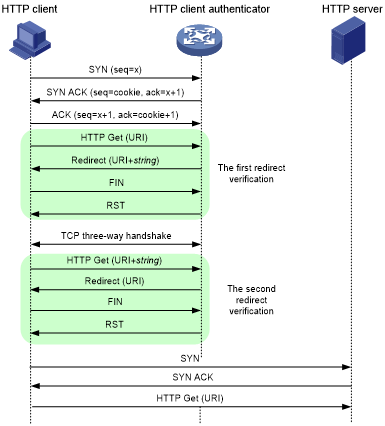
As shown in Figure 187, the HTTP client verification functions as follows:
Upon receiving a SYN packet destined for a protected HTTP server, the HTTP client authenticator performs TCP client verification in SYN cookie mode. If the client passes the TCP client verification, a TCP connection is established between the client and the authenticator. For more information about TCP client verification, see "TCP client verification."
When the authenticator receives an HTTP Get packet from the client, it performs the first redirect verification. The authenticator records the client information and responds with an HTTP Redirect packet. The HTTP Redirect packet contains a redirect URI and requires the client to terminate the TCP connection.
After receiving the HTTP Redirect packet, the client terminates the TCP connection and then establishes a new TCP connection with the authenticator.
When the authenticator receives the HTTP Get packet, it performs the second redirection verification. The authenticator verifies the following information:
The client has passed the first redirection verification.
The URI in the HTTP Get packet is the redirect URI.
If the client passes the second redirection verification, the authenticator adds its IP address to the trusted IP list, and responds a Redirect packet. The Redirect packet contains the URI that the client originally carried and requires the client to terminate the TCP connection.
The authenticator directly forwards the trusted client's subsequent packets to the server.
Figure 182: HTTP client verification process