Password authentication enabled Stelnet client configuration example
Network requirements
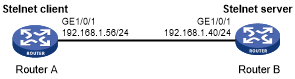
As shown in Figure 161:
Router B acts as the Stelnet server and uses password authentication.
The username and password of the client are saved on Router B.
Establish an Stelnet connection between Router A and Router B, so you can log in to Router B as a network administrator to configure and manage Router B.
Figure 156: Network diagram
Configuration procedure
Configure the Stelnet server:
# Generate RSA key pairs.
<RouterB> system-view [RouterB] public-key local create rsa The range of public key modulus is (512 ~ 2048). If the key modulus is greater than 512, it will take a few minutes. Press CTRL+C to abort. Input the modulus length [default = 1024]: Generating Keys... ........................++++++ ...................++++++ ..++++++++ ............++++++++ Create the key pair successfully.
# Generate a DSA key pair.
[RouterB] public-key local create dsa The range of public key modulus is (512 ~ 2048). If the key modulus is greater than 512, it will take a few minutes. Press CTRL+C to abort. Input the modulus length [default = 1024]: Generating Keys... .++++++++++++++++++++++++++++++++++++++++++++++++++* ........+......+.....+......................................+ ...+.................+..........+...+ Create the key pair successfully.
# Generate an ECDSA key pair.
[RouterB] public-key local create ecdsa secp256r1 Generating Keys... . Create the key pair successfully.
# Enable the Stelnet server.
[RouterB] ssh server enable
# Assign an IP address to interface GigabitEthernet 1/0/1. The Stelnet client uses this address as the destination address for SSH connection.
[RouterB] interface gigabitethernet 1/0/1 [RouterB-GigabitEthernet1/0/1] ip address 192.168.1.40 255.255.255.0 [RouterB-GigabitEthernet1/0/1] quit
# Set the authentication mode to AAA for the user lines.
[RouterB] line vty 0 63 [RouterB-line-vty0-63] authentication-mode scheme [RouterB-line-vty0-63] quit
# Create a local device management user named client001.
[RouterB] local-user client001 class manage
# Set the password to aabbcc in plain text for local user client001.
[RouterB-luser-manage-client001] password simple aabbcc
# Authorize local user client001 to use the SSH service.
[RouterB-luser-manage-client001] service-type ssh
# Assign the network-admin user role to local user client001.
[RouterB-luser-manage-client001] authorization-attribute user-role network-admin [RouterB-luser-manage-client001] quit
# Create an SSH user named client001. Specify the service type as stelnet and the authentication method as password for the user.
[RouterB] ssh user client001 service-type stelnet authentication-type password
Establish a connection to the Stelnet server:
# Assign an IP address to interface GigabitEthernet 1/0/1.
<RouterA> system-views [RouterA] interface gigabitethernet 1/0/1 [RouterA-GigabitEthernet1/0/1] ip address 192.168.1.56 255.255.255.0 [RouterA-GigabitEthernet1/0/1] quit [RouterA] quit
Before establishing a connection to the server, you can configure the server's host public key on the client to authenticate the server.
To configure the server's host public key on the client, perform the following tasks:
# Use the display public-key local dsa public command on the server to display the server's host public key. (Details not shown.)
# Enter public key view of the client and copy the host public key of the server to the client.
[RouterA] public-key peer key1 Enter public key view. Return to system view with "peer-public-key end" command. [RouterA-pkey-public-key-key1] 308201B73082012C06072A8648CE3804013082011F0281810 0D757262C4584C44C211F18BD96E5F0 [RouterA-pkey-public-key-key1]61C4F0A423F7FE6B6B85B34CEF72CE14A0D3A5222FE08CECE 65BE6C265854889DC1EDBD13EC8B274 [RouterA-pkey-public-key-key1]DA9F75BA26CCB987723602787E922BA84421F22C3C89CB9B0 6FD60FE01941DDD77FE6B12893DA76E [RouterA-pkey-public-key-key1]EBC1D128D97F0678D7722B5341C8506F358214B16A2FAC4B3 68950387811C7DA33021500C773218C [RouterA-pkey-public-key-key1]737EC8EE993B4F2DED30F48EDACE915F0281810082269009E 14EC474BAF2932E69D3B1F18517AD95 [RouterA-pkey-public-key-key1]94184CCDFCEAE96EC4D5EF93133E84B47093C52B20CD35D02 492B3959EC6499625BC4FA5082E22C5 [RouterA-pkey-public-key-key1]B374E16DD00132CE71B020217091AC717B612391C76C1FB2E 88317C1BD8171D41ECB83E210C03CC9 [RouterA-pkey-public-key-key1]B32E810561C21621C73D6DAAC028F4B1585DA7F42519718CC 9B09EEF0381840002818000AF995917 [RouterA-pkey-public-key-key1]E1E570A3F6B1C2411948B3B4FFA256699B3BF871221CC9C5D F257523777D033BEE77FC378145F2AD [RouterA-pkey-public-key-key1]D716D7DB9FCABB4ADBF6FB4FDB0CA25C761B308EF53009F71 01F7C62621216D5A572C379A32AC290 [RouterA-pkey-public-key-key1]E55B394A217DA38B65B77F0185C8DB8095522D1EF044B465E 8716261214A5A3B493E866991113B2D [RouterA-pkey-public-key-key1]485348 [RouterA-pkey-public-key-key1] peer-public-key end [RouterA] quit
# Establish an SSH connection to the server, and specify the host public key of the server as key1.
<RouterA> ssh2 192.168.1.40 public-key key1 Username: client001 Press CTRL+C to abort. Connecting to 192.168.1.40 port 22. client001@192.168.1.40's password: Enter a character ~ and a dot to abort. ****************************************************************************** * Copyright (c) 2010-2016 Hewlett Packard Enterprise Development LP * * Without the owner's prior written consent, * * no decompiling or reverse-engineering shall be allowed. * ****************************************************************************** <RouterB>
After you enter the correct password, you log in to Router B successfully.
If the client does not have the server's host public key, you must confirm the access to the server. Enter y to access the server and save the server's host public key on the client.
<RouterA> ssh2 192.168.1.40 Username: client001 Press CTRL+C to abort. Connecting to 192.168.1.40 port 22. The server is not authenticated. Continue? [Y/N]:y Do you want to save the server public key? [Y/N]:y client001@192.168.1.40's password: Enter a character ~ and a dot to abort. ****************************************************************************** * Copyright (c) 2010-2016 Hewlett Packard Enterprise Development LP * * Without the owner's prior written consent, * * no decompiling or reverse-engineering shall be allowed. * ****************************************************************************** <RouterB>
After you enter the correct password, you can access Router B successfully. At the next connection attempt, the client authenticates the server by using the saved server's host public key on the client.