Configuring IPsec tunnel interface-based IPsec for IPv4 packets
Network requirements
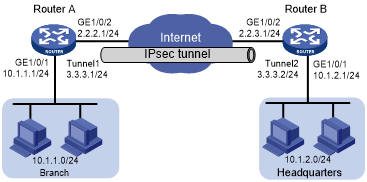
As shown in Figure 138, the branch accesses the Internet through dial-up and uses dynamic IP addresses. The headquarters uses fixed IP addresses to access the Internet.
Configure IPsec tunnel interface-based IPsec to protect the traffic between the branch (10.1.1.0/24) and the headquarters (10.1.2.0/24). This IPsec implementation ensures that the IPsec configuration of the headquarters remains stable despite of the changes of the branch subnet.
Figure 133: Network diagram
Configuration procedure
Configure routing to make sure Router A and Router B can reach each other through IPv4. (Details not shown.)
Configure IP addresses for the interfaces on Router A and Router B. (Details not shown.)
Configure Router A:
# Create an IKE keychain named abc.
<RouterA> system-view [RouterA] ike keychain abc
# Configure 123456TESTplat&! in plain text as the pre-shared key to be used with the remote peer at 2.2.3.1.
[RouterA-ike-keychain-abc] pre-shared-key address 2.2.3.1 255.255.255.0 key simple 123456TESTplat&! [RouterA-ike-keychain-abc] quit
# Create an IKE profile named abc.
[RouterA] ike profile abc
# Specify IKE keychain abc for the IKE profile.
[RouterA-ike-profile-abc] keychain abc
# Configure the local ID with the identity type as IP address and the value as 2.2.2.1.
[RouterA-ike-profile-abc] local-identity address 2.2.2.1
# Configure a peer ID with the identity type as IP address and the value as 2.2.3.1/24.
[RouterA-ike-profile-abc] match remote identity address 2.2.3.1 24
# Set the IKE phase-1 negotiation mode to aggressive.
[RouterA-ike-profile-abc] exchange-mode aggressive [RouterA-ike-profile-abc] quit
# Create an IPsec transform set named abc.
[RouterA] ipsec transform-set abc
# Specify the encryption algorithm as AES-CBC-128.
[RouterA-ipsec-transform-set-abc] esp encryption-algorithm aes-cbc-128
# Specify the authentication algorithm as SHA1.
[RouterA-ipsec-transform-set-abc] esp authentication-algorithm sha1 [RouterA-ipsec-transform-set-abc] quit
# Create an IKE-based IPsec profile named abc.
[RouterA] ipsec profile abc isakmp
# Specify IPsec transform set abc for the IPsec profile.
[RouterA-ipsec-profile-isakmp-abc] transform-set abc
# Specify IKE profile abc for the IPsec profile.
[RouterA-ipsec-profile-isakmp-abc] ike-profile abc [RouterA-ipsec-profile-isakmp-abc] quit
# Create IPsec/IPv4 tunnel interface Tunnel1.
[RouterA] interface tunnel 1 mode ipsec
# Configure an IP address for the tunnel interface.
[RouterA-Tunnel1] ip address 3.3.3.1 255.255.255.0
# Configure the source address of the tunnel interface as the IP address of GE 1/0/2 on Router A.
[RouterA-Tunnel1] source 2.2.2.1
# Configure the destination address of the tunnel interface as the IP address of GE 1/0/2 on Router B.
[RouterA-Tunnel1] destination 2.2.3.1
# Apply IPsec profile abc to the tunnel interface.
[RouterA-Tunnel1] tunnel protection ipsec profile abc [RouterA-Tunnel1] quit
# Configure a static route from Router A to Router B through the tunnel interface.
[RouterA] ip route-static 10.1.2.0 255.255.255.0 tunnel 1
Configure Router B:
# Create an IKE keychain named abc.
<RouterB> system-view [RouterB] ike keychain abc
# Configure 123456TESTplat&! in plain text as the pre-shared key to be used with the remote peer at 2.2.2.1.
[RouterB-ike-keychain-abc] pre-shared-key address 2.2.2.1 255.255.255.0 key simple 123456TESTplat&! [RouterB-ike-keychain-abc] quit
# Create an IKE profile named abc.
[RouterB] ike profile abc
# Specify IKE keychain abc for the IKE profile.
[RouterB-ike-profile-abc] keychain abc
# Configure the local ID with the identity type as IP address and the value as 2.2.3.1.
[RouterB-ike-profile-abc] local-identity address 2.2.3.1
# Configure a peer ID with the identity type as IP address and the value as 2.2.2.1/24.
[RouterB-ike-profile-abc] match remote identity address 2.2.2.1 24
# Set the IKE phase-1 negotiation mode to aggressive.
[RouterB-ike-profile-abc] exchange-mode aggressive [RouterB-ike-profile-abc] quit
# Create an IPsec transform set named abc.
[RouterB] ipsec transform-set abc
# Specify the encryption algorithm as AES-CBC-128.
[RouterB-ipsec-transform-set-abc] esp encryption-algorithm aes-cbc-128
# Specify the authentication algorithm as SHA1.
[RouterB-ipsec-transform-set-abc] esp authentication-algorithm sha1 [RouterB-ipsec-transform-set-abc] quit
# Create an IKE-based IPsec profile named abc.
[RouterB] ipsec profile abc isakmp
# Specify IPsec transform set abc for the IPsec profile.
[RouterB-ipsec-profile-isakmp-abc] transform-set abc
# Specify IKE profile abc for the IPsec profile.
[RouterB-ipsec-profile-isakmp-abc] ike-profile abc [RouterB-ipsec-profile-isakmp-abc] quit
# Create IPsec/IPv4 tunnel interface Tunnel1.
[RouterB] interface tunnel 1 mode ipsec
# Configure an IP address for the tunnel interface.
[RouterB-Tunnel1] ip address 3.3.3.2 255.255.255.0
# Configure the source address of the tunnel interface as the IP address of GE 1/0/2 on Router B.
[RouterB-Tunnel1] source 2.2.3.1
# Configure the destination address of the tunnel interface as the IP address of GE 1/0/2 on Router A.
[RouterB-Tunnel1] destination 2.2.2.1
# Apply IPsec profile abc to the tunnel interface.
[RouterB-Tunnel1] tunnel protection ipsec profile abc [RouterB-Tunnel1] quit
# Configure a static route from Router B to Router A through the tunnel interface.
[RouterB] ip route-static 10.1.1.0 255.255.255.0 tunnel 1
Verifying the configuration
After the configuration is completed, Router A will automatically initiate IKE negotiation with Router B. After IKE negotiation succeeds, the tunnel interface links will become up. After IPsec SAs are established, traffic between the branch and the headquarters will be IPsec protected. This example uses Router A to verify the configuration.
# Display brief IP configuration for interfaces on Router A.
<RouterA> display ip interface brief *down: administratively down (s): spoofing (l): loopback Interface Physical Protocol IP Address Description GE1/0/1 up up 10.1.1.1 -- GE1/0/2 up up 2.2.2.1 -- Tun1 up up 3.3.3.1 --
# Display tunnel interface information on Router A.
<RouterA> display interface Tunnel 1 Tunnel1 Current state: UP Line protocol state: UP Description: Tunnel1 Interface Bandwidth: 64 kbps Maximum transmission unit: 1444 Internet address: 3.3.3.1/24 (primary) Tunnel source 2.2.2.1 (GigabitEthernet0/0), destination 2.2.3.1 Tunnel TTL 255 Tunnel protocol/transport IPsec/IP Output queue - Urgent queuing: Size/Length/Discards 0/100/0 Output queue - Protocol queuing: Size/Length/Discards 0/500/0 Output queue - FIFO queuing: Size/Length/Discards 0/75/0 Last clearing of counters: Never Last 300 seconds input rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec Last 300 seconds output rate: 0 bytes/sec, 0 bits/sec, 0 packets/sec Input: 0 packets, 0 bytes, 0 drops Output: 0 packets, 0 bytes, 0 drops
# Display IPsec SAs on Router A.
<RouterA> display ipsec sa
-------------------------------
Interface: Tunnel1
-------------------------------
-----------------------------
IPsec profile: abc
Mode: ISAKMP
-----------------------------
Tunnel id: 0
Encapsulation mode: tunnel
Perfect forward secrecy:
Path MTU: 1388
Tunnel:
local address: 2.2.2.1
remote address: 2.2.3.1
Flow:
sour addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
dest addr: 0.0.0.0/0.0.0.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 2701952073 (0xa10c8449)
Connection ID: 4294967296
Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3180
Max received sequence-number: 0
Anti-replay check enable: Y
Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N
Status: Active
[Outbound ESP SAs]
SPI: 3607077598 (0xd6ffa2de)
Connection ID: 12884901889
Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-MD5
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3180
Max sent sequence-number: 0
UDP encapsulation used for NAT traversal: N
Status: Active
# Verify that a private IP address in the branch subnet can ping a private IP address in the headquarters subnet successfully.
<RouterA> ping -a 10.1.1.1 10.1.2.1 Ping 10.1.2.1 (10.1.2.1) from 10.1.1.1: 56 data bytes, press CTRL_C to break 56 bytes from 10.1.2.1: icmp_seq=0 ttl=255 time=1.000 ms 56 bytes from 10.1.2.1: icmp_seq=1 ttl=255 time=1.000 ms 56 bytes from 10.1.2.1: icmp_seq=2 ttl=255 time=0.000 ms 56 bytes from 10.1.2.1: icmp_seq=3 ttl=255 time=1.000 ms 56 bytes from 10.1.2.1: icmp_seq=4 ttl=255 time=0.000 ms --- Ping statistics for 10.1.2.1 --- 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss round-trip min/avg/max/std-dev = 0.000/0.600/1.000/0.490 ms