Configuring IPsec RRI
Network requirements
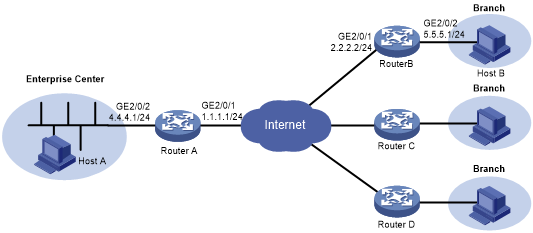
As shown in Figure 137, branches access the enterprise center through an IPsec VPN.
Configure the IPsec VPN as follows:
Configure an IPsec tunnel between Router A and each branch gateway (Router B, Router C, and Router D) to protect traffic between subnets 4.4.4.0/24 and 5.5.5.0/24.
Configure the tunnels to use the security protocol ESP, the encryption algorithm DES, and the authentication algorithm SHA1-HMAC-96. Use IKE for IPsec SA negotiation.
Configure IKE proposal to use pre-shared key authentication method, the encryption algorithm 3DES, and the authentication algorithm HMAC-SHA1.
Configure IPsec RRI on Router A to automatically create static routes to the branches based on the established IPsec SAs.
Figure 132: Network diagram
Configuration procedure
Assign IPv4 addresses to the interfaces on the routers according to Figure 137. (Details not shown.)
Configure Router A:
# Create an IPsec transform set named tran1, and specify ESP as the security protocol, DES as the encryption algorithm, and HMAC-SHA-1-96 as the authentication algorithm.
<RouterA> system-view [RouterA] ipsec transform-set tran1 [RouterA-ipsec-transform-set-tran1] encapsulation-mode tunnel [RouterA-ipsec-transform-set-tran1] protocol esp [RouterA-ipsec-transform-set-tran1] esp encryption-algorithm des [RouterA-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [RouterA-ipsec-transform-set-tran1] quit
# Create an IPsec policy template named temp1. Specify the IPsec transform set tran1 for the IPsec policy template.
[RouterA] ipsec policy-template temp1 1 [RouterA-ipsec-policy-template-temp1-1] transform-set tran1
# Enable IPsec RRI, set the preference to 100 and the tag to 1000 for the static routes created by IPsec RRI.
[RouterA-ipsec-policy-template-temp1-1] reverse-route dynamic [RouterA-ipsec-policy-template-temp1-1] reverse-route preference 100 [RouterA-ipsec-policy-template-temp1-1] reverse-route tag 1000 [RouterA-ipsec-policy-template-temp1-1] quit
# Create an IKE-based IPsec policy entry by using IPsec policy template temp1. Specify the policy name as map1 and set the sequence number to 10.
[RouterA] ipsec policy map1 10 isakmp template temp1
# Create an IKE proposal named 1, and specify 3DES as the encryption algorithm, HMAC-SHA1 as the authentication algorithm, and pre-share as the authentication method.
[RouterA] ike proposal 1 [RouterA-ike-proposal-1] encryption-algorithm 3des-cbc [RouterA-ike-proposal-1] authentication-algorithm sha [RouterA-ike-proposal-1] authentication-method pre-share [RouterA-ike-proposal-1] quit
# Create an IKE keychain named key1 and specify 123 in plain text as the pre-shared key to be used with the remote peer at 2.2.2.2.
[RouterA] ike keychain key1 [RouterA-ike-keychain-key1] pre-shared-key address 2.2.2.2 key simple 123 [RouterA-ike-keychain-key1] quit
# Apply the IPsec policy map1 to interface GigabitEthernet 2/0/1.
[RouterA] interface gigabitethernet 2/0/1 [RouterA-GigabitEthernet2/0/1] ipsec apply policy map1 [RouterA-GigabitEthernet2/0/1] quit
Configure Router B:
# Create an IPsec transform set named tran1, and specify ESP as the security protocol, DES as the encryption algorithm, and HMAC-SHA-1-96 as the authentication algorithm.
[RouterB] ipsec transform-set tran1 [RouterB-ipsec-transform-set-tran1] encapsulation-mode tunnel [RouterB-ipsec-transform-set-tran1] protocol esp [RouterB-ipsec-transform-set-tran1] esp encryption-algorithm des [RouterB-ipsec-transform-set-tran1] esp authentication-algorithm sha1 [RouterB-ipsec-transform-set-tran1] quit
# Configure IPv4 advanced ACL 3000 to identify traffic from subnet 5.5.5.0/24 to subnet 4.4.4.0/24.
[RouterB] acl advanced 3000 [RouterB-acl-ipv4-adv-3000] rule permit ip source 5.5.5.0 0.0.0.255 destination 4.4.4.0 0.0.0.255 [RouterB-acl-ipv4-adv-3000] quit
# Create an IKE-based IPsec policy entry. Specify the policy name as map1 and set the sequence number to 10. Specify the transform set tran1 and ACL 3000, and specify the remote IP address for the tunnel as 1.1.1.1.
[RouterB] ipsec policy map1 10 isakmp [RouterB-ipsec-policy-isakmp-map1-10] transform-set tran1 [RouterB-ipsec-policy-isakmp-map1-10] security acl 3000 [RouterB-ipsec-policy-isakmp-map1-10] remote-address 1.1.1.1 [RouterB-ipsec-policy-isakmp-map1-10] quit
# Create an IKE proposal named 1, and specify 3DES as the encryption algorithm, HMAC-SHA1 as the authentication algorithm, and pre-share as the authentication method.
[RouterB] ike proposal 1 [RouterB-ike-proposal-1] encryption-algorithm 3des-cbc [RouterB-ike-proposal-1] authentication-algorithm sha [RouterB-ike-proposal-1] authentication-method pre-share [RouterB-ike-proposal-1] quit
# Create an IKE keychain named key1 and specify 123 in plain text as the pre-shared key to be used with the remote peer at 1.1.1.1.
[RouterB] ike keychain key1 [RouterB-ike-keychain-key1] pre-shared-key address 1.1.1.1 key simple 123 [RouterB-ike-keychain-key1] quit
# Apply the IPsec policy map1 to interface GigabitEthernet 2/0/1.
[RouterB] interface gigabitethernet 2/0/1 [RouterB-GigabitEthernet2/0/1] ipsec apply policy map1 [RouterB-GigabitEthernet2/0/1] quit
Make sure Router B has a route to the peer private network, with the outgoing interface as GigabitEthernet 2/0/1.
Configure Router C and Router D in the same way Router B is configured.
Verifying the configuration
Verify that IPsec RRI can automatically create a static route from Router A to Router B:
# Initiate a connection from subnet 5.5.5.0/24 to subnet 4.4.4.0/24. IKE negotiation is triggered to establish IPsec SAs between Router A and Router B. (Details not shown.)
# Verify that IPsec SAs are established on Router A.
[RouterA] display ipsec sa ------------------------------- Interface: GigabitEthernet2/0/1 ------------------------------- ----------------------------- IPsec policy: map1 Sequence number: 10 Mode: Template ----------------------------- Tunnel id: 0 Encapsulation mode: tunnel Perfect forward secrecy: Inside VRF: Path MTU: 1463 Tunnel: local address: 1.1.1.1 remote address: 2.2.2.2 Flow: sour addr: 4.4.4.0/255.255.255.0 port: 0 protocol: ip dest addr: 5.5.5.0/255.255.255.0 port: 0 protocol: ip [Inbound ESP SAs] SPI: 1014286405 (0x3c74c845) Connection ID: 1 Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-SHA1 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3590 Max received sequence-number: 4 Anti-replay check enable: Y Anti-replay window size: 64 UDP encapsulation used for nat traversal: N Status: Active [Outbound ESP SAs] SPI: 4011716027 (0xef1dedbb) Connection ID: 2 Transform set: ESP-ENCRYPT-DES-CBC ESP-AUTH-SHA1 SA duration (kilobytes/sec): 1843200/3600 SA remaining duration (kilobytes/sec): 1843199/3590 Max sent sequence-number: 4 UDP encapsulation used for nat traversal: N Status: Active# Verify that IPsec RRI has created a static route to reach Router B.
[RouterA] display ip routing-table verbose
Verify that Router A can automatically create static routes to Router C and Router D in the same way that you verify the IPsec RRI feature by using Router A and Router B. (Details not shown.)